
2023 was characterized by an evolving array of cyber threats and a significantly broadened spectrum of digital vulnerabilities, pushing organizations to reassess and strengthen their cybersecurity infrastructures. Despite a widespread yearning for a break from the relentless tide of phishing, ransomware, and credential stuffing incidents, cybercriminals are gearing up to use their proven strategies from this period to orchestrate even more intricate and damaging campaigns in 2024. It’s become increasingly imperative for those in the cybersecurity realm to forecast and brace for the predominant challenges and trends that will define the cybersecurity landscape in 2024.
The following are key prognostications intended to serve as vital strategic insights for IT and cybersecurity professionals, aiding them in effectively prioritizing their efforts to navigate and mitigate the rapidly evolving threat landscape
Compromised credentials
The ongoing reliance on traditional usernames and passwords for access control and authentication has perpetuated the issue of compromised credentials. This has been a consistent weak spot, often exploited in cyberattacks. Detailed analyses of data breaches repeatedly pinpoint compromised credentials as a principal attack vector. Intriguingly, a study by the Identity Defined Security Alliance (IDSA) highlights that identity-related cyberattacks are both widespread (with 94% of respondents experiencing such attacks) and largely preventable (with a 99% prevention rate). Despite these alarming statistics, a significant number of organizations remain underprepared, lacking crucial identity-related security measures. This is particularly concerning given the rise of non-human identities stemming from digital transformations, such as in DevOps, cloud computing, and IoT (Internet of Things). Therefore, the expectation for 2024 is a continued emphasis on enhancing identity security, with organizations encouraged to intensify their implementation of Zero Trust models and decrease their dependency on traditional password-based systems.
Ransomware
Ransomware has proven to be a lucrative venture for cybercriminals, who exploit vulnerabilities within organizations to execute devastating attacks. Examples of these include high-profile breaches involving entities like the Kansas Court System, Yamaha Motors, and Western Digital. The emergence of Ransomware-as-a-Service has simplified the process of launching such attacks. Over the past year, ransomware tactics have evolved into complex extortion schemes, involving not just data encryption but also data exfiltration and threats of public disclosure if ransoms aren't paid. This trend was exemplified by the Alphv/BlackCat ransomware group's SEC complaint against MeridianLink. With new SEC disclosure regulations mandating prompt reporting of major cybersecurity incidents, such tactics are expected to gain even more traction. Therefore, enterprises are advised to enhance their ransomware preparedness, with a specific focus on the recovery of endpoints and essential infrastructure like Active Directory.
Hacktivism amidst global conflicts
The intersection of global conflicts and the upcoming 2024 Presidential elections in the United States is expected to create a fertile environment for hacktivism. Hacktivists, often self-identified as defenders of free speech, may seek to disrupt the controlled flow of information during times of conflict or elections by exposing sensitive data or initiating cyberattacks. This could lead to a blurring of lines between state-sponsored hacking and independent hacktivist activities. The role of hacktivists in influencing public opinion through various cyber operations, including the potential use of deepfake technologies, is expected to be significant in 2024.
Vulnerability management
In response to the increasing exploitation of zero-day vulnerabilities by cyber adversaries, the White House's National Cybersecurity Strategy, released in March 2023, has redirected focus towards organizations' responsibility to secure their software. This strategy underscores the importance of comprehensive vulnerability management, which involves identifying, assessing, prioritizing, and mitigating security vulnerabilities. This increased emphasis on liability for independent software vendors is anticipated to drive technological advancements in vulnerability management tools and bring renewed attention to this critical aspect of cybersecurity.
Transformation in security awareness training
The realm of security awareness training is poised for a significant transformation in 2024. With the widespread adoption of generative artificial intelligence in the sphere of cyber threats, traditional training methods are becoming obsolete. Future training programs are expected to integrate continuous breach and attack simulations (BAS) to test and enhance the effectiveness of user-focused controls. These programs will also likely focus on equipping software developers with secure coding practices to preemptively address vulnerabilities.
Conclusion
In summary, the year 2024 emphasizes the crucial need for a delicate balance between robust cybersecurity measures and the resilience to adapt to cyber threats. As IT and security professionals prepare for the challenges ahead, prioritizing the continuous visibility, protection, and management of the entire digital attack surface is paramount. Protecting mission-critical assets and developing the capability to anticipate, withstand, recover from, and adapt to various cyberattacks will remain at the forefront of effective organizational cybersecurity strategies.
Five cybersecurity predictions for 2024
Of course, losing access to your Google or Gmail account is going to be upsetting. If you've forgotten your password, or if someone has hacked into your account and changed it, Google provides a list of actions that you may take to regain access to your account. Indeed, they may come in handy at times, but the methods of password recovery for Google accounts tend to change from time to time and relying on them as a fallback is never a good idea.
Not only have we provided all the necessary links in the “Password recovery” section down below for those who have lost access to certain accounts, but we’ll today be focusing on what can be done to ensure you never lose access to your account again. Here are some things to consider:
Regularly backup your data
If you have a current backup of your data, it will be less of a blow if you ever lose access to your account. Takeout is the name Google has given to the feature that allows you to download your data. You may download all of the data from all of your Google applications, or just part of the data from some of them. You might even decide to download the data from a single app, such as Gmail, from your Google account.
For each sort of data, the download formats are different. For example, MBOX files may be imported to Gmail or most other email services and applications.
Keep your old passwords
Keep a copy of your old passwords in case you forget your current one. Google uses this method to verify your identity if you ever lose your password. In the event that you haven't updated your password in a while, you may not be able to recall your old password. It's a good idea to maintain a copy of your previous Google passwords in a secure place when you change your password.
When using a password manager such as Passwork, you can keep track of your previous passwords. Because of that, we strongly recommend using one. When you establish a new password on an app or website, most password managers only allow you to update the current entry; however, with a password manager, you may create a new password and then go back and change the name of the old one to something like "Gmail — old password". By the way, this is also a problem with Apple Keychain — when you change your password, it asks whether you would like to update your old password. You’ll obviously press “Update”, and bam, your previous password is lost in the void. So keep an eye on that.
Why is this important? Well, as we’ve hinted at, Google asks you to enter the previous password in some cases as a fallback plan.
Fill in the recovery info
Google provides you with many ways to recover your password:
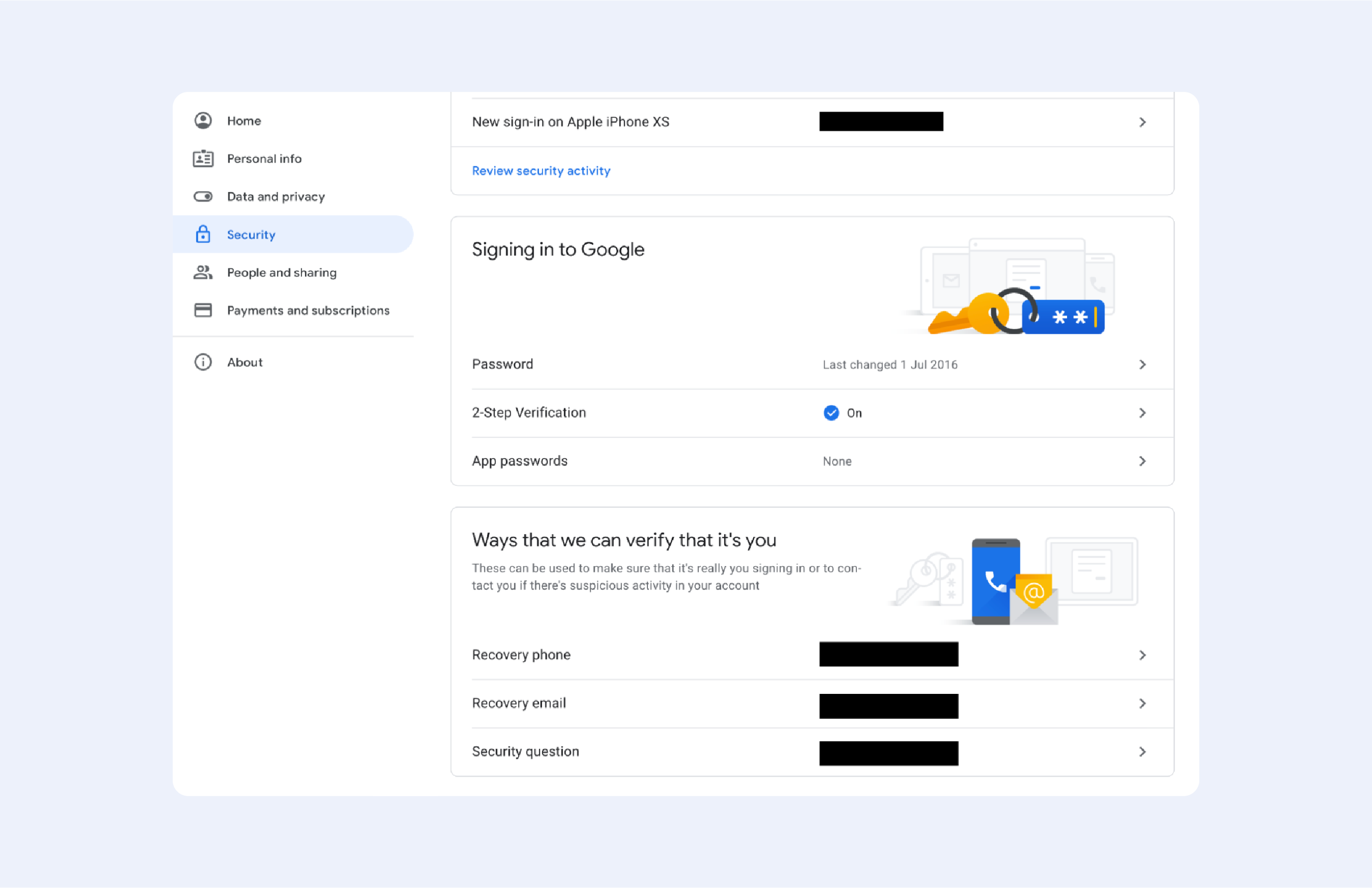
- Go to your Google account and choose "Security" from the left-hand column
- Scroll all the way down to "Ways that we can verify that it’s you"
- Fill them in
- PROFIT
Now, Google will use those options to recover your password when needed, or just to verify it’s you when weird login behaviour is detected. Among all the options, the ‘Recovery phone’ is the most convenient one — trust me, you’ll forget that ‘Security Question’ in just a few days. ‘Recovery email’, to be honest, isn't secure enough — we, Earthlings, tend to use weak passwords, so your account might be compromised if a hacker manages to guess your ‘NicknameDateOFBirth’ password.
Remember the day you registered
If everything else fails, Google may ask you to provide an estimated date of when you created the account. The best way to get this date is by searching for a Gmail welcome email.
To locate the welcome email, go to the ‘All Mail’ folder on your computer (to see it, you may need to click ‘More’ to expand the folders). You may also hover your cursor over the page information in the upper right-hand corner and choose ‘Oldest’.
This will move the email you received first to the top of the list. If, on the other hand, you imported non-Gmail emails into your inbox from before 2004, the welcome email will not appear at the top of the inbox hierarchy. Also, if you haven’t imported all of your emails, you’ll encounter some problems.
The email may also be found by searching for "welcome," "Gmail team," "gmail-noreply@google.com," or "googlecommunityteam-noreply@google.com," among other similar words and phrases.
However, when I personally tried it, I couldn't find it. This is because I delete all the mail on my account once a year. For people like myself, there’s a weird hack — your POP settings might show the date on which you created your Gmail account.
To access them, click the gear icon in the top right-hand corner, select See all settings, then click Forwarding and POP/IMAP.
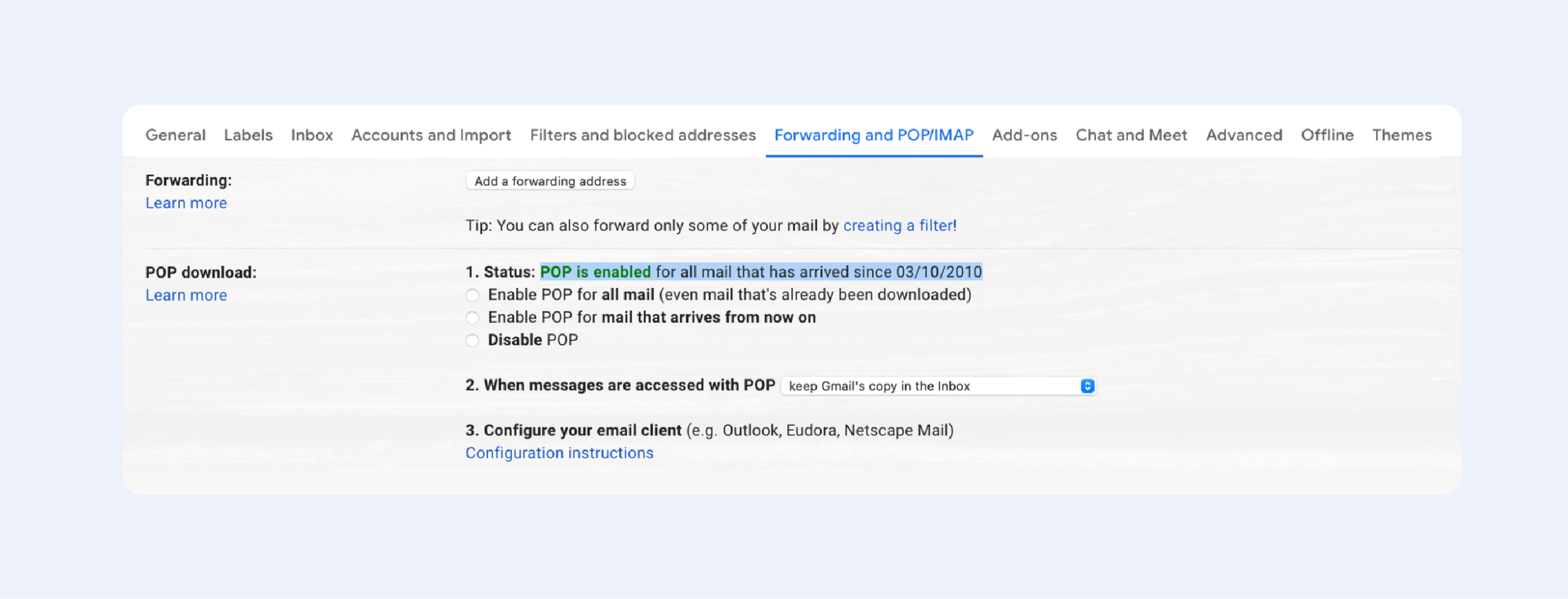
Look for the Status line in the POP download section. If you're fortunate, you'll come upon the following information:
“Status: POP is enabled for all mail that has arrived since [Here is your date]”
Important:
If you’ve ever changed your POP settings, the date on which you created your Gmail account won’t be shown.
Password recovery
There’s only one place where you can recover your password — it’s this “Google Recovery” page. Everything else is likely phishing scams. The only other alternative option, in case of an adversary like losing your password, is the “Can’t sign into your Google Account” page.
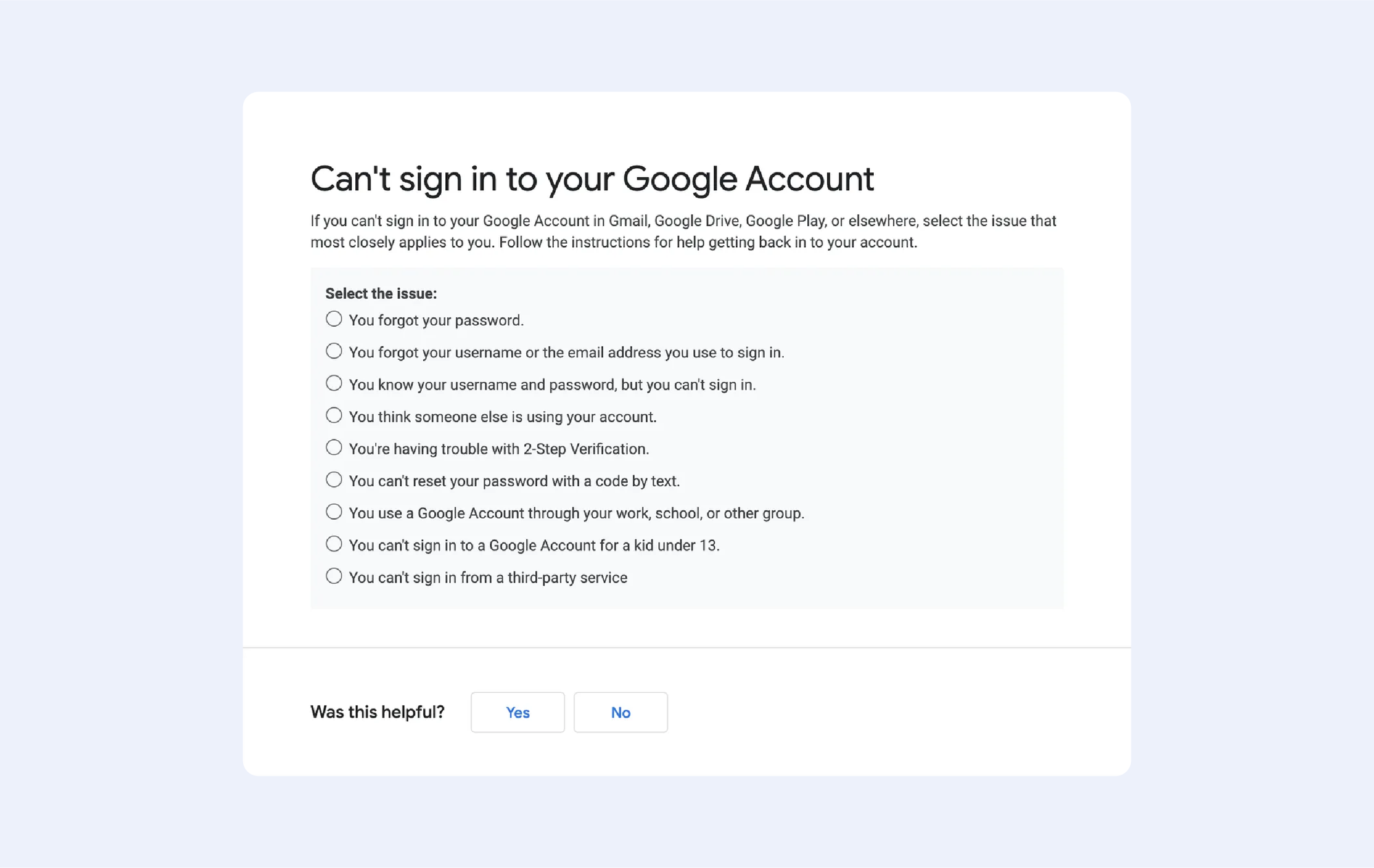
Basically, you should follow the instructions on screen and pray to Google's mothership that hope shall be restored.
If your prayers haven’t been heard, and all pages cycle through a loop with a “Please try again” message, visit the “Tips to complete account recovery steps” page — it helped me several times to understand exactly what Google wants from me.
The last page you can visit, if everything else fails, is “Create a replacement Google Account”.
Conclusion
If you have important data stored on any cloud: Gmail, Google Drive, Docs, etc. — back them up using offline storage. Use two-factor authentication to always keep your mobile phone as a recovery option. Keep hold of your password change history and remember the date you registered your account.
I forgot my GMail password!
If you’ve ever set up a wireless router on your own, you’ve probably heard of WPS. You might come across this term in the router’s configuration menus or see it on the backside of your router — but do you know what WPS actually means and how it works? If you can’t answer these questions yourself, then you’re in the right place.

What is WPS?
WPS stands for WiFi Protected Setup. It’s effectively a wireless network security standard that speeds up and simplifies the process of connecting your device with a router. It helps to do it quickly without entering a Wi-Fi password. To enable WPS you should find a tactile button located on the backside of your router or switch it on in the configurations menu of the router. When you turn it on, WPS mode allows you to connect your various devices to your router using the WPS password, also known as the WPA-PSA key.
In fact, WPS is not responsible for the Wi-Fi connection at all. It’s designed solely to send the connection data between the router and the wireless device. Remember, that’s an important distinction.
WPS was an idea of the nonprofit ‘Wi-Fi Alliance’. The alliance is effectively an association of the largest companies that create computers and Wi-Fi devices. More than 600 members take part, including companies such as Microsoft, Samsung, and Intel. Alliance was founded in 1999 to promote Wi-Fi technologies and certificate Wi-Fi products around the world. This standard was created in 2007 to simplify the connection process and since that time, most Wi-Fi systems around the world have adopted it.
How does WPS work?
If you want to connect your wireless device, you have to know the password to the Wi-Fi network. This process isn’t difficult but it takes some time to get the essential data. WPS makes it easier and a bit quicker.
There are some different ways to do it. First of all, WPS can be a workaround for connecting to Wi-Fi without a password. To do so, you should hit the WPS button on your router to enable device detection. Then, take your device and choose the network you need to connect to. The connection will be immediately available and the system won’t ask you to enter the password.
Some wireless electronic equipment like printers also has a WPS button that can be used to make rapid connections. All you have to do is to push both buttons, on the device and on the router, to get access to the wireless network. You don’t need to enter any data here, as the WPS delivers the password automatically. Also, that device will be able to connect to the same Wi-Fi router without pushing WPS buttons in the future as the password will be remembered.
The other option requires one to use the eight-digit PIN code. When WPS is enabled on a router, a PIN code is produced automatically. The WPS PIN can be found on the WPS setup page. Some devices that lack a WPS button will require the PIN. If you enter the wireless network, they verify themselves and connect to it.
The last option also can be done by using that eight-digit PIN. Some devices do not have the WPS button but also support WPS, so they will produce a client PIN that will be used by the router to connect the device to the network. You should just enter the PIN in the settings of your router to get access.
Unfortunately, methods that require using a PIN code don’t have any benefits in the speed of the connection process. You spend the same amount of time entering the router’s password and the WPS PIN, so you should just choose the way that’s more comfortable for you.
Which devices work with WPS?
WPS is supported by a wide range of devices, most commonly, wireless routers. However, you can also find a WPS button on wireless printers, Wi-Fi Range Extenders and Repeaters, which commonly provide WPS capabilities as well. Finally, the WPS functionality is available on a few higher-end laptops, tablets, smartphones, and 2-in-1 devices, where it’s usually implemented via software rather than physical buttons.
What are the advantages and disadvantages of WPS?
Despite the fact that WPS is embedded in most Wi-Fi equipment, the benefit of this standard is still a controversial issue. Some professionals opt for using it as it makes the connection to the router easier and quicker while others opt against it as WPS mitigates the security of the connection process.
Advantages:
1. It's quick, especially if both the router and the client device have the WPS button.
2. It's simple and requires no technical knowledge. There is no more primitive way of connecting Wi-Fi than pressing the WPS button on both the router and the client device.
3. Support is relatively strong. WPS is supported by all routers and most networking devices. WPS can also be used to establish rapid Wi-Fi network connections on the most common operating systems like Windows, Android, and Linux.
Disadvantages:
1. It isn't really safe. WPS connections using PINs appear to be particularly sensitive to brute-force attacks. A successful WPS attack allows an attacker to obtain access to your Wi-Fi network, and disabling WPS is the only viable remedy.
2. WPS can be used by anyone who has physical access to the router. So any person who is aware of the router’s location can connect it without your permission.
3. WPS is not supported by Apple. You can't connect to Wi-Fi using WPS if you have a Mac, an iPhone, or an iPad. This is because Apple has determined that WPS is insufficiently secure, and thus WPS isn’t not supported by any of the devices.
Conclusion
As we’ve found out, the WPS network’s security standard has both benefits and limitations. On the one hand, it helps us to avoid remembering the Wi-Fi password and connect quickly. On the other hand, WPS is not secure enough to foster user confidence across the board. So, it’s up to you to decide on using WPS or not. In any case, you can disable the function at any time you want by simply switching off the WPS button.
WPS – What is it, and how does it work?

In Passwork 6.3, we have implemented numerous changes that significantly improve organization management efficiency, provide more flexible user permission settings, and increase security:
- Administrative rights
- Hidden vaults
- Improved private vaults
- Improved settings interface
Administrative rights
Available with the Advanced license
Now there is no need to make users administrators in order to grant them specific administrative rights. This option is a response to one of the most frequent requests from our customers.
Administrators can grant only those rights or permissions that are necessary for users to fulfill their duties and flexibly customize access to settings sections and manage Passwork. For instance, you can grant employees the right to create and edit new users, view the history of user activity, track settings changes, while restricting access to organization vaults and System settings.
You can configure additional rights on the Administrative rights tab in User management. There are four settings sections to flexibly customize Passwork for your business:
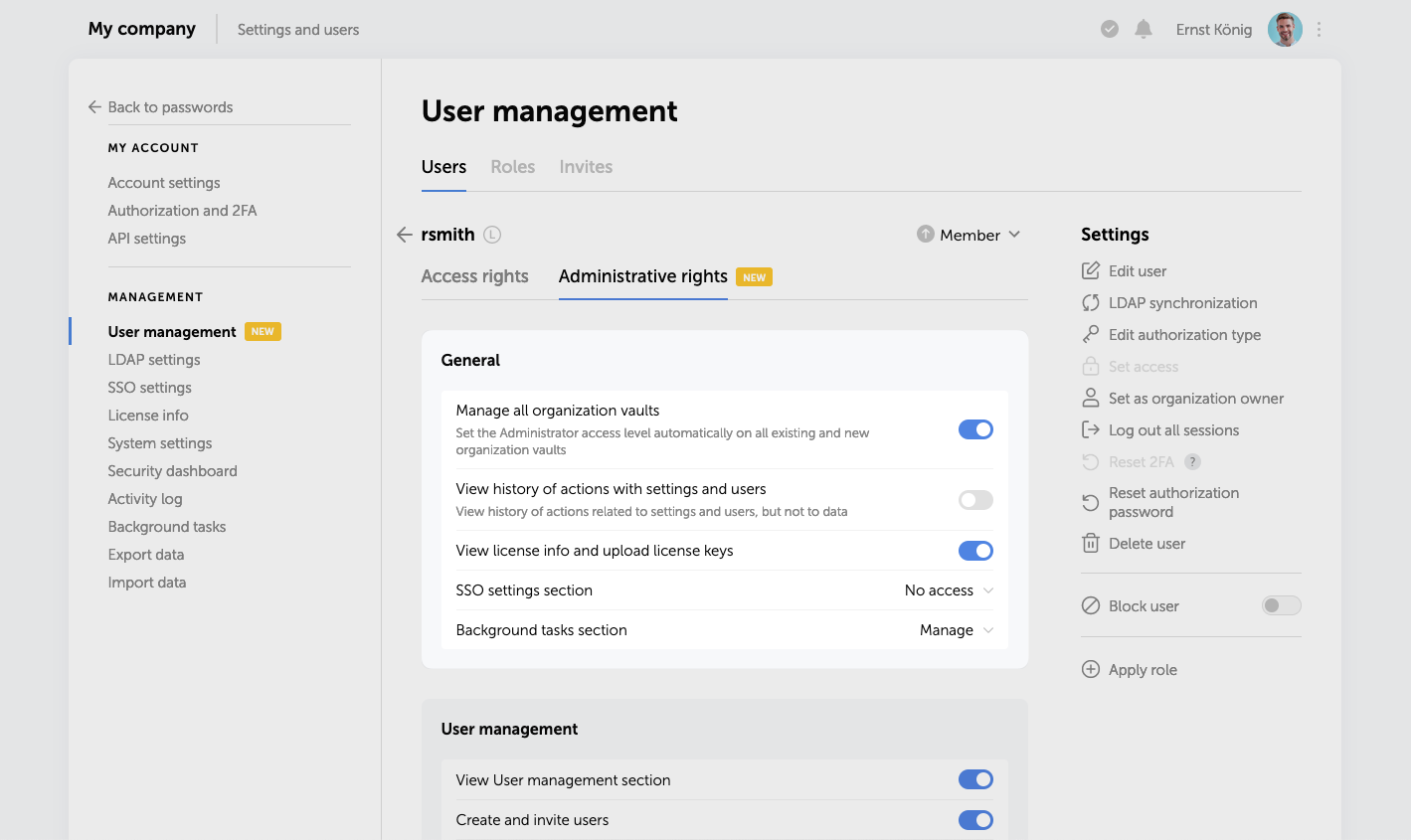
General
In this section, you can grant users access rights to manage all existing and new organization vaults, view the history of actions with settings and users, access license info and upload license keys, view and modify the parameters of SSO settings and Background tasks.
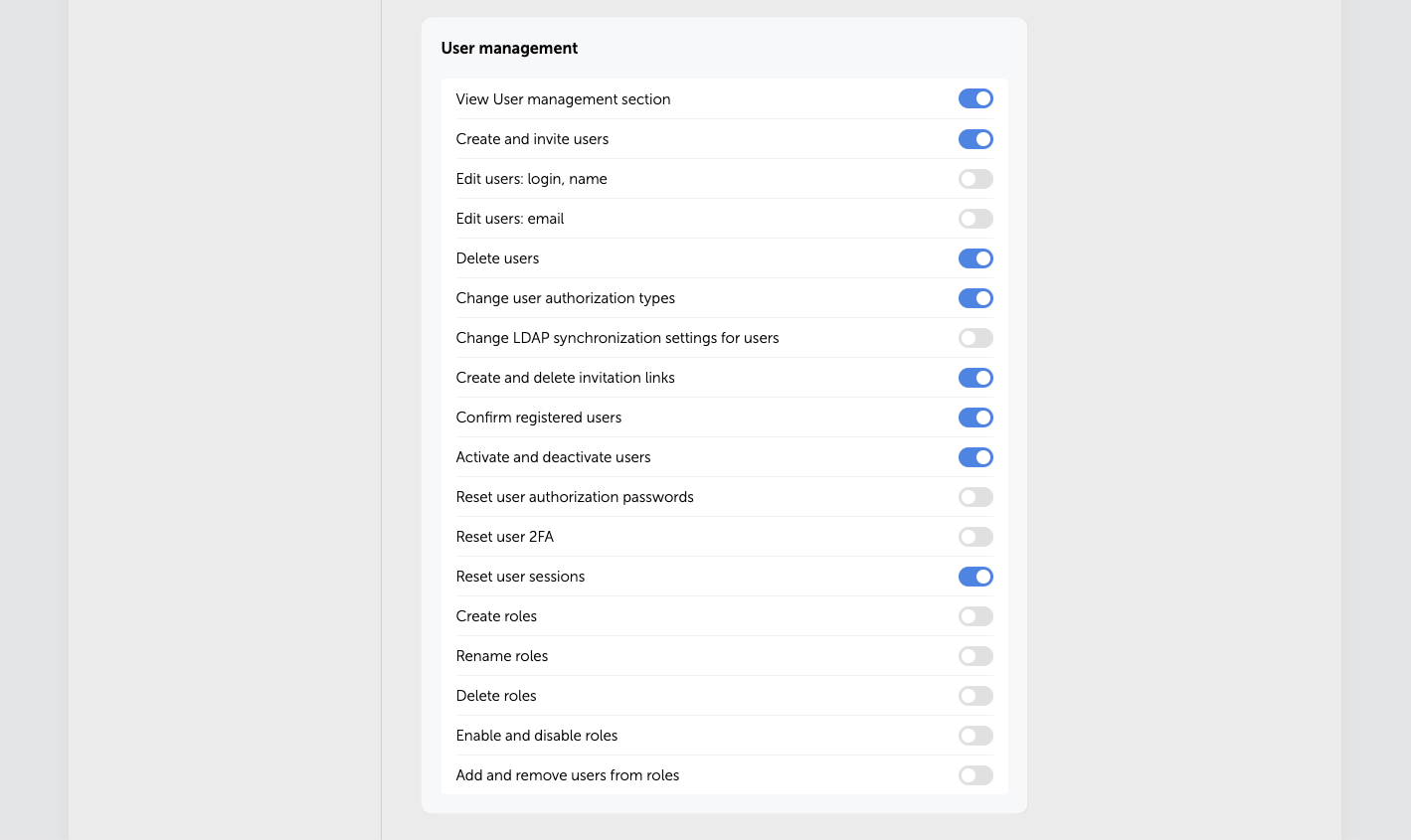
User management
In this section, you can grant users access rights to view and modify User management parameters. This includes performing any necessary actions with users and roles, such as creating, deleting, and editing users, changing their authorization type and sending invitations.
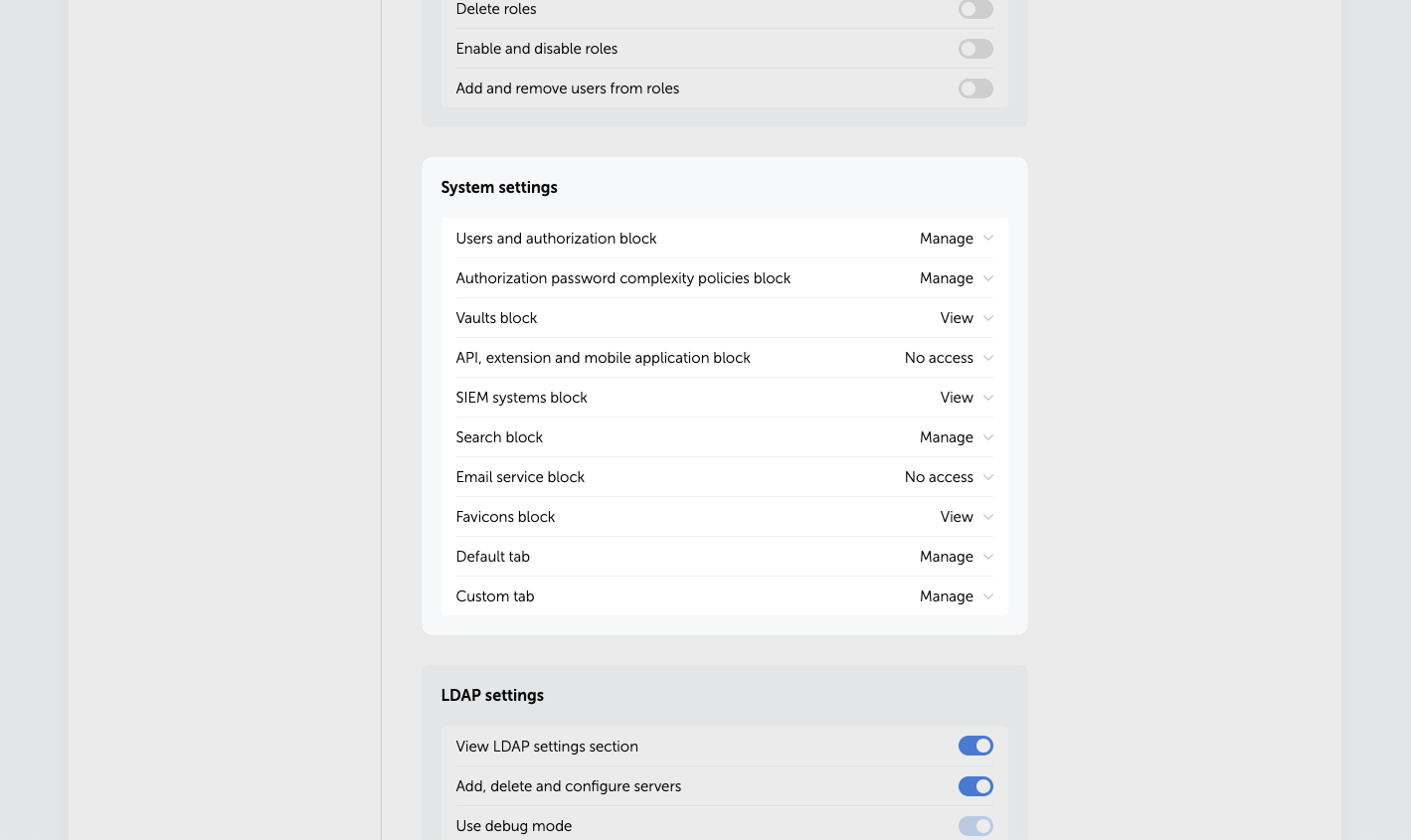
System settings
In this section of settings, you can grant users the right to view and modify specific groups of System settings.
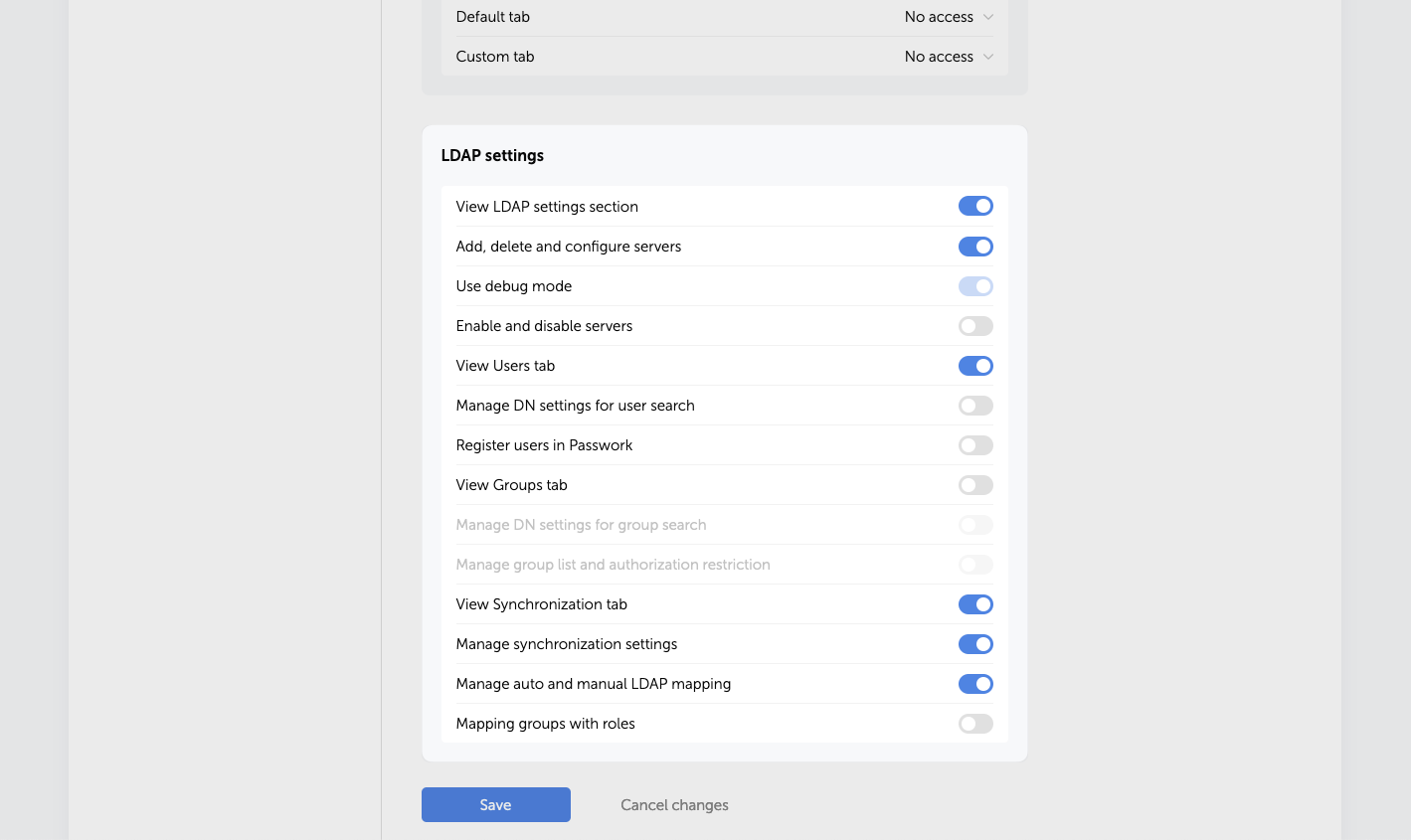
LDAP settings
In this section, you can grant users the right to view and modify LDAP parameters which include adding and deleting servers, registering new users, managing group lists, viewing and configuring synchronization settings.
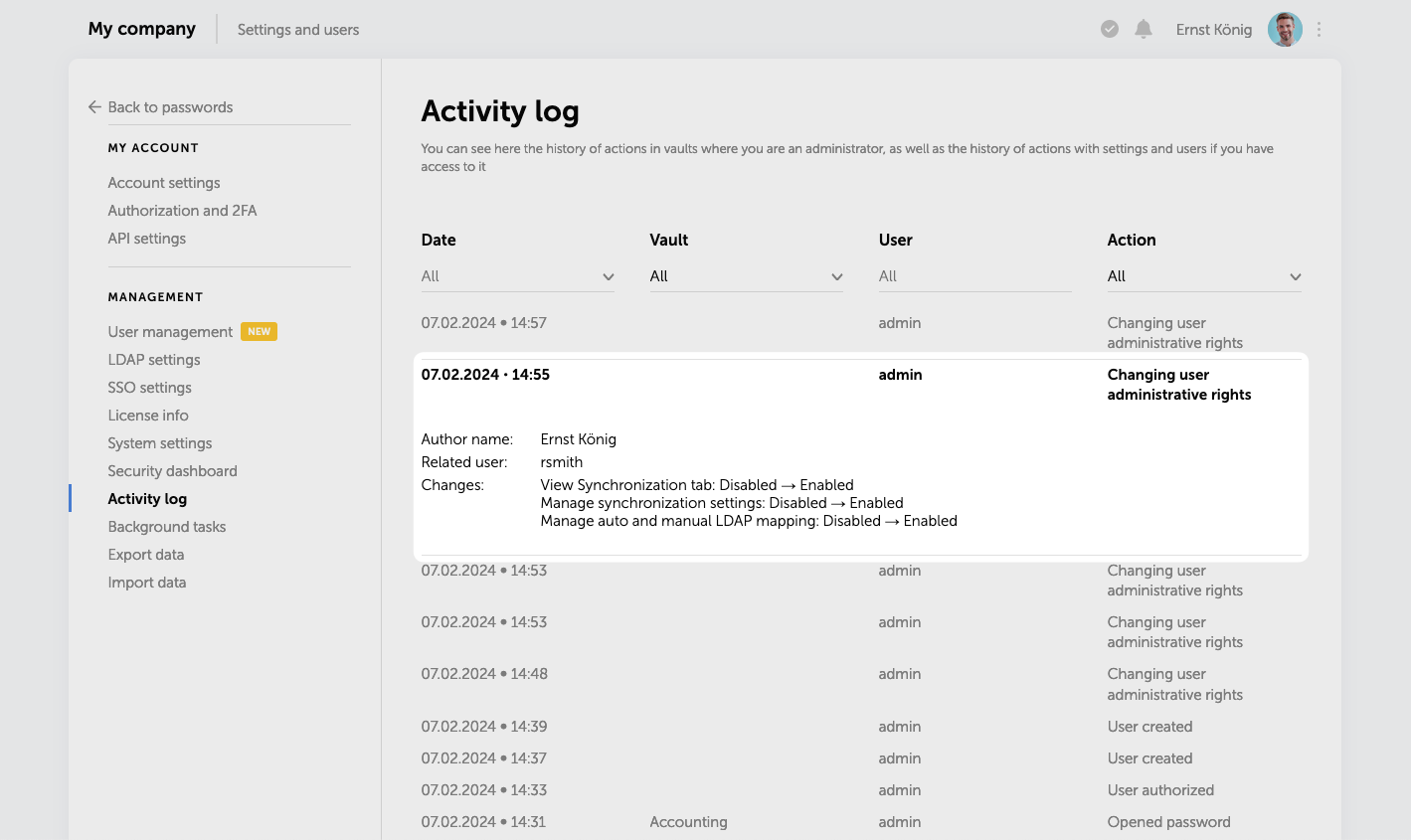
Activity log
The event of changing user administrative rights has been added to the Activity log. All changes are now recorded in the Activity log, that includes the users who initiated such changes as well as each setting that was modified with its previous and current values.
Interface improvements
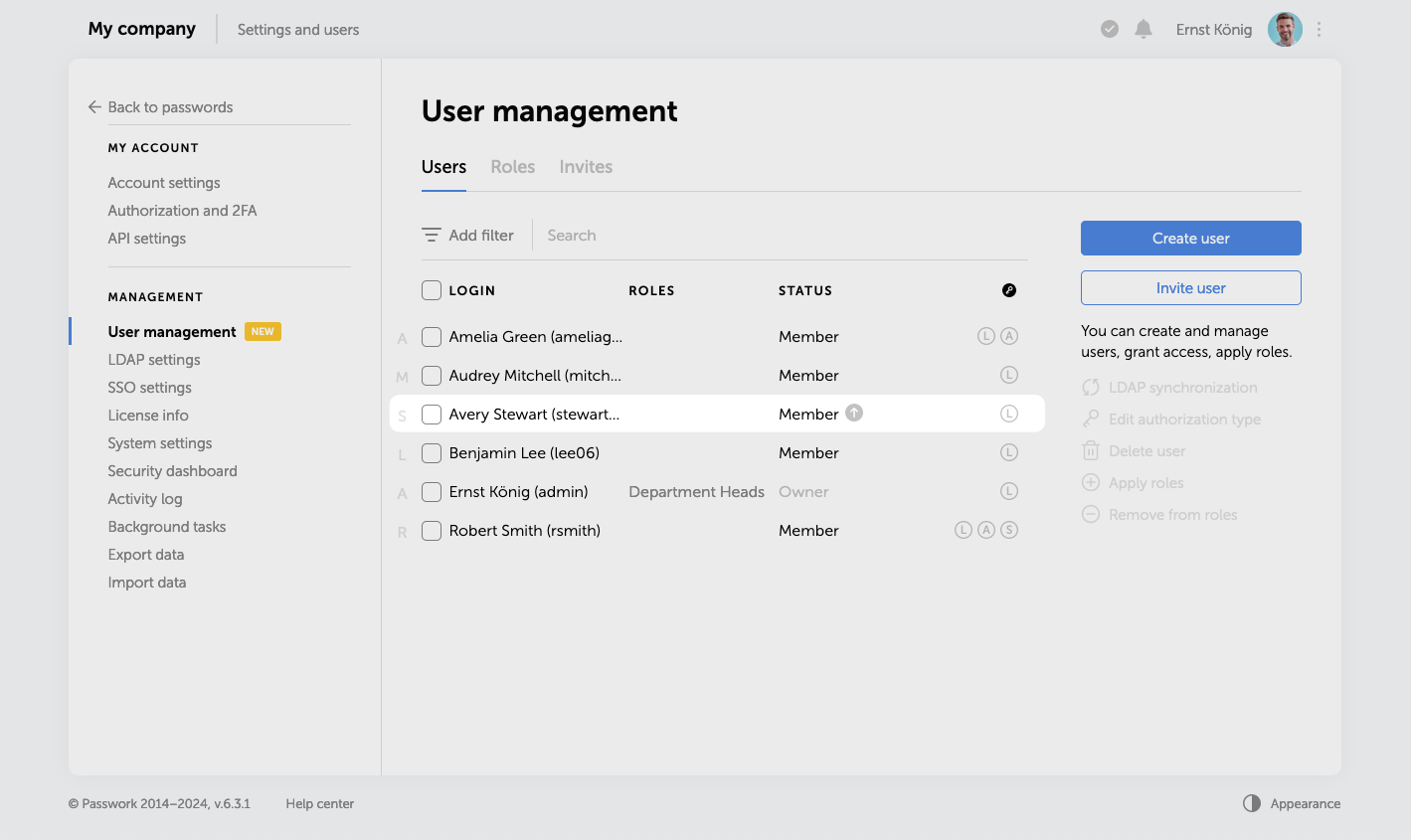
Users with additional administrative rights are marked with a special icon next to their user status.
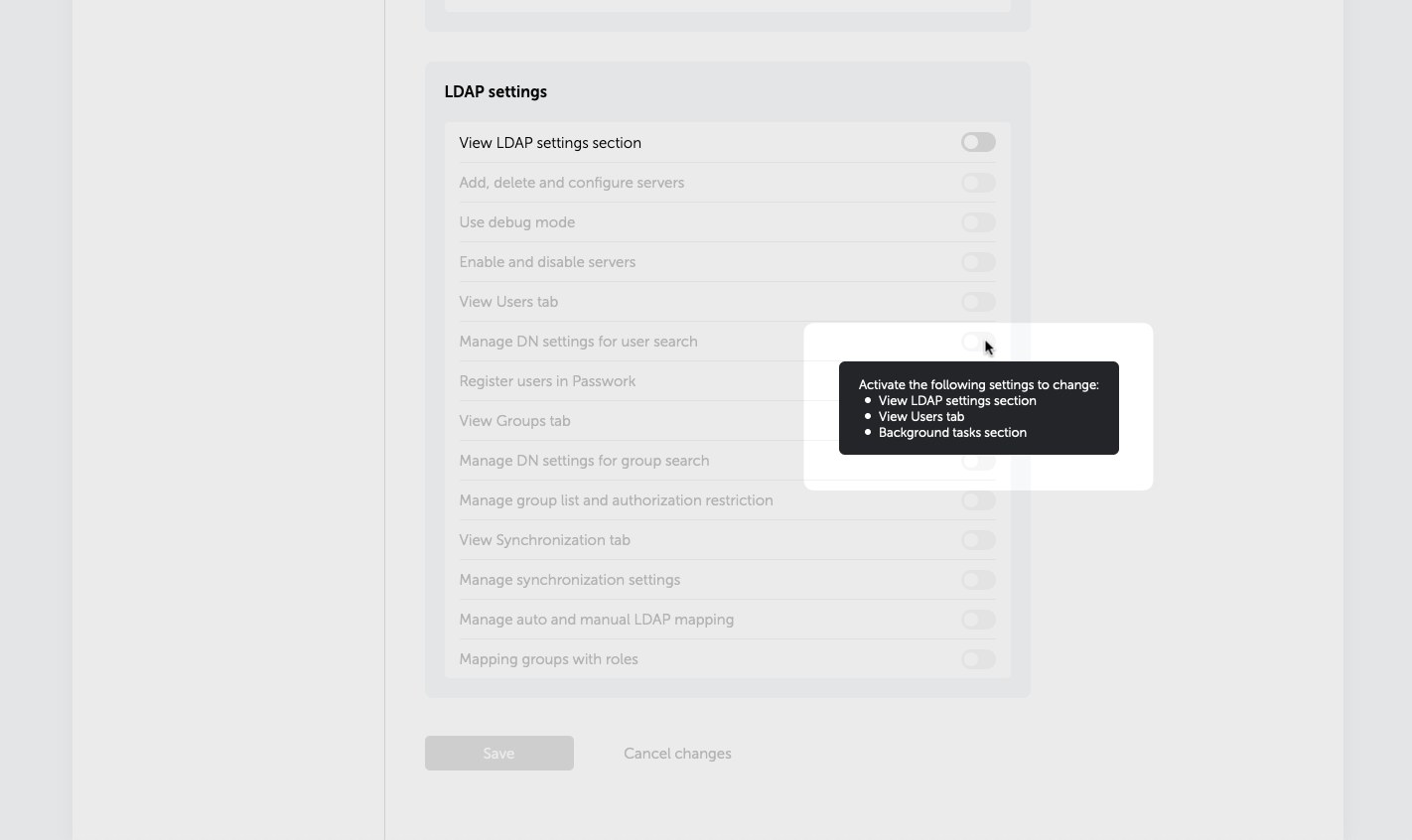
Some items remain unavailable until the necessary settings have been activated. When hovering your cursor over such items, a tooltip with information regarding dependent settings will be displayed.
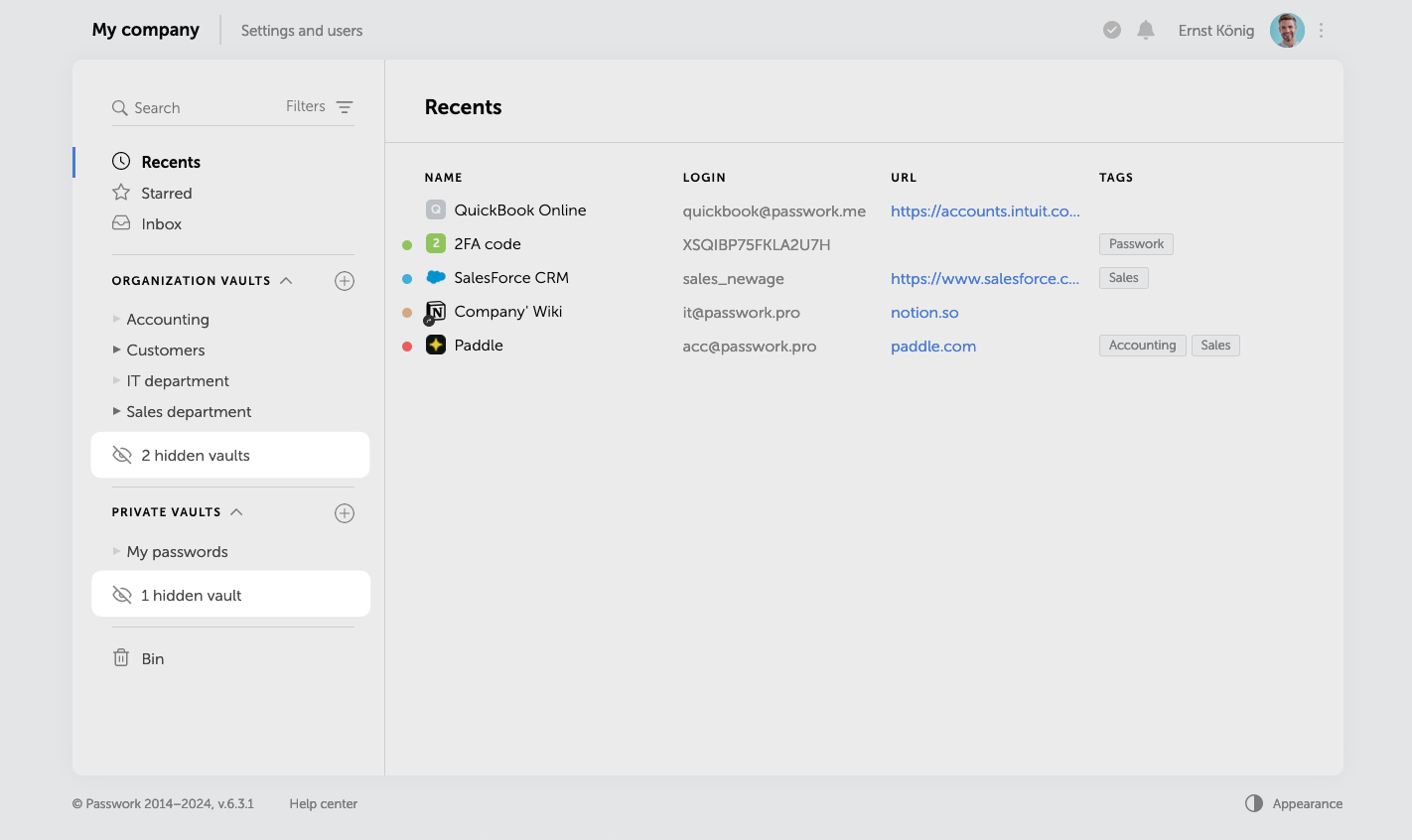
Hidden vaults
In the previous versions of Passwork only organization administrators were able to hide vaults. Also, only organization vaults could be hidden. In this new version, all users can hide any vaults. Hiding makes vaults invisible only to the users who choose to do it and does not affect others.
Hidden vault management is now carried out in a new window, which is available directly from the list of vaults. You can view the list of all available vaults and customize their visibility there.
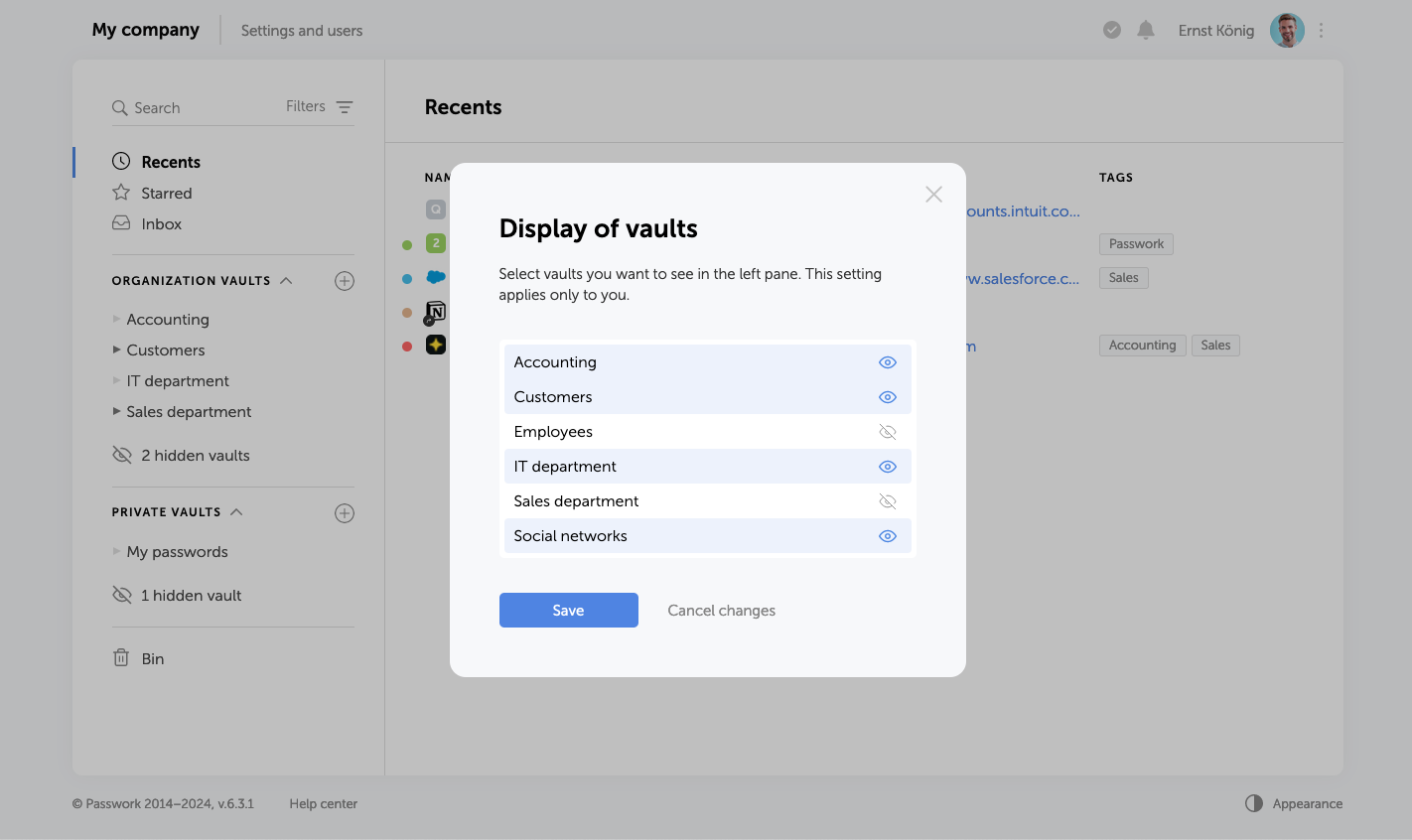
Private vault improvements
Displaying private vaults in User management
Besides hiding private vaults, employees with User management access can now see all vaults which they administer (including private vaults). The new feature which makes it possible to add users to private vaults has also been added to User management.

Logging of events in private vaults
Private vault administrators can view all events related to their vaults in the Activity log.
Other changes
- Fixed an issue which prevented users from changing their temporary master password
- Fixed an issue which prevented users from setting the minimum length for authorization and master passwords
- Fixed an issue in User management which made administrator self-deletion possible
- Minor improvements to the settings interface
Introducing Passwork 6.3
Self-signed certificates are widely used in testing environments and they are excellent alternatives to purchasing and renewing yearly certifications.
That is of course if you know how and, more importantly, when to use them. Remember, that A self-signed certificate is not signed by a publicly trusted Certificate Authority (CA). Self-signed certificates are considered different from traditional CA certificates that are signed and issued by a CA because self-signed certificates are created, issued, and signed by the company or developer who is responsible for the website or software associated with the certificate.
You are probably reading this article because for some reason, you need to create a self-signed certificate with Windows. So, we’ve tried to outline the easiest ways to do that. This article is up-to-date as of December 2021. By the way, we’re referring to Windows 10 for all the following tutorials. As far as we know, the processes for Windows 11 are identical.
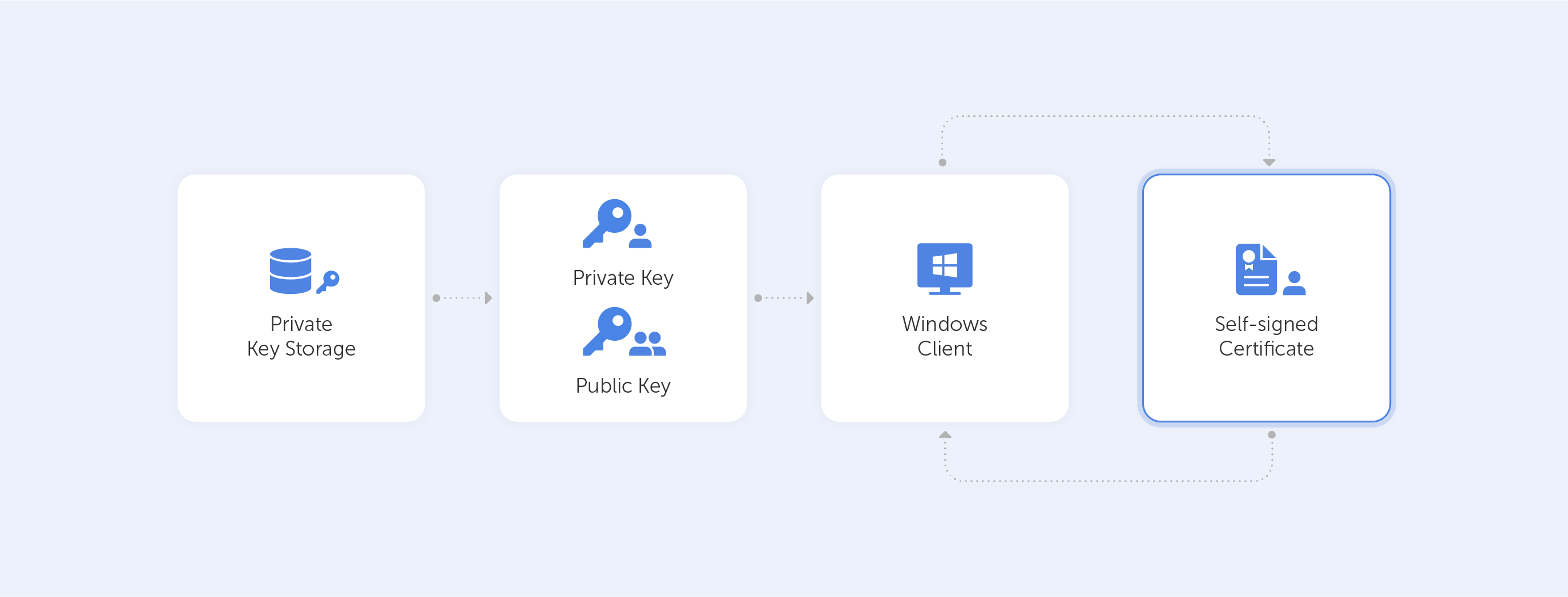
So what are our options?
Using Let’s Encrypt.
These guys offer free CA certificates with various SAN and wildcard support. The certificate is only good for 90 days, but they do give an automated renewal method. This is a great alternative for a quick proof-of-concept. Other options would require more typing, for sure.
But this option works only if you want to generate a certificate for your website. The best way to start is by going to Getting Started, the instructions thereafter are very easy to follow.
Other one-click option:
We’ve reviewed different online services that allow you to easily generate self-signed certificates. We’ve sorted them from one-click to advanced, and the first one is:
Just enter your domain name — and you are ready to go:
Fill out the following fields:
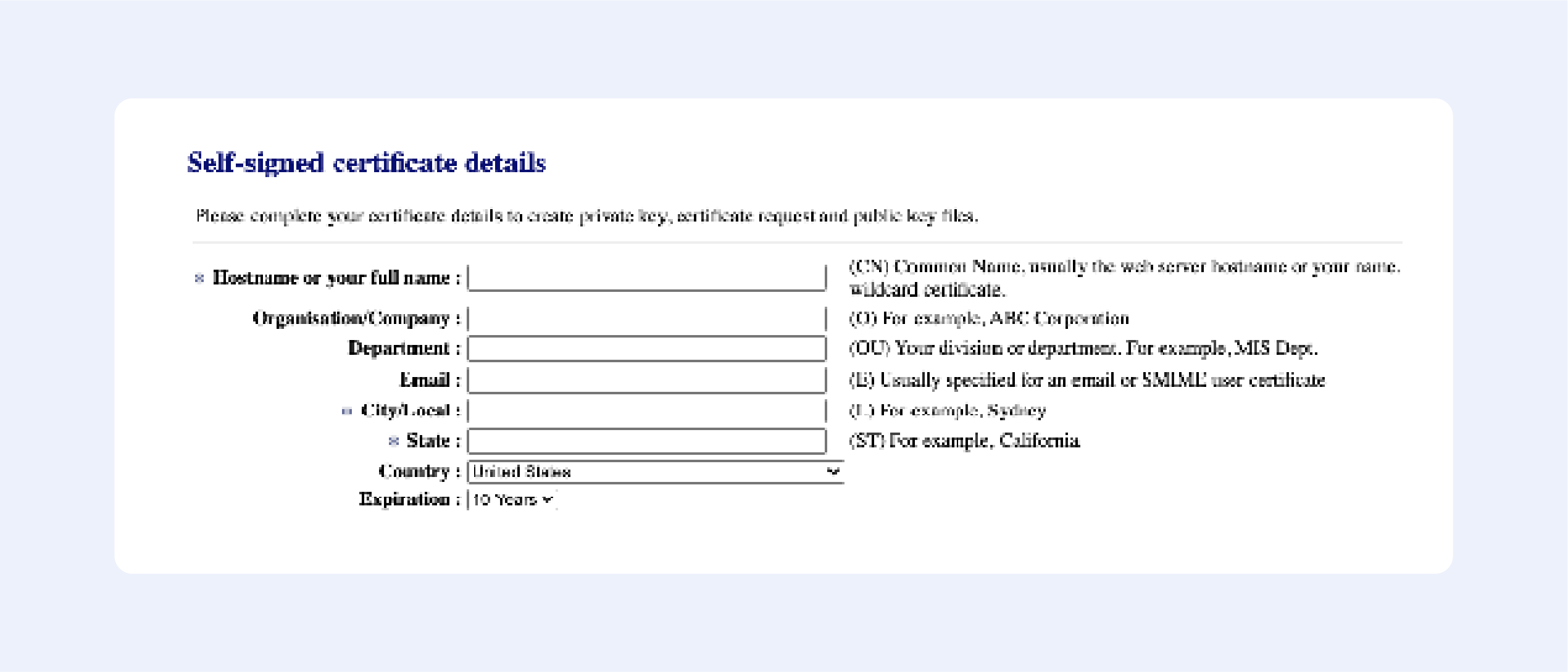
Press “Next”, then confirm your details, and get your certificate:
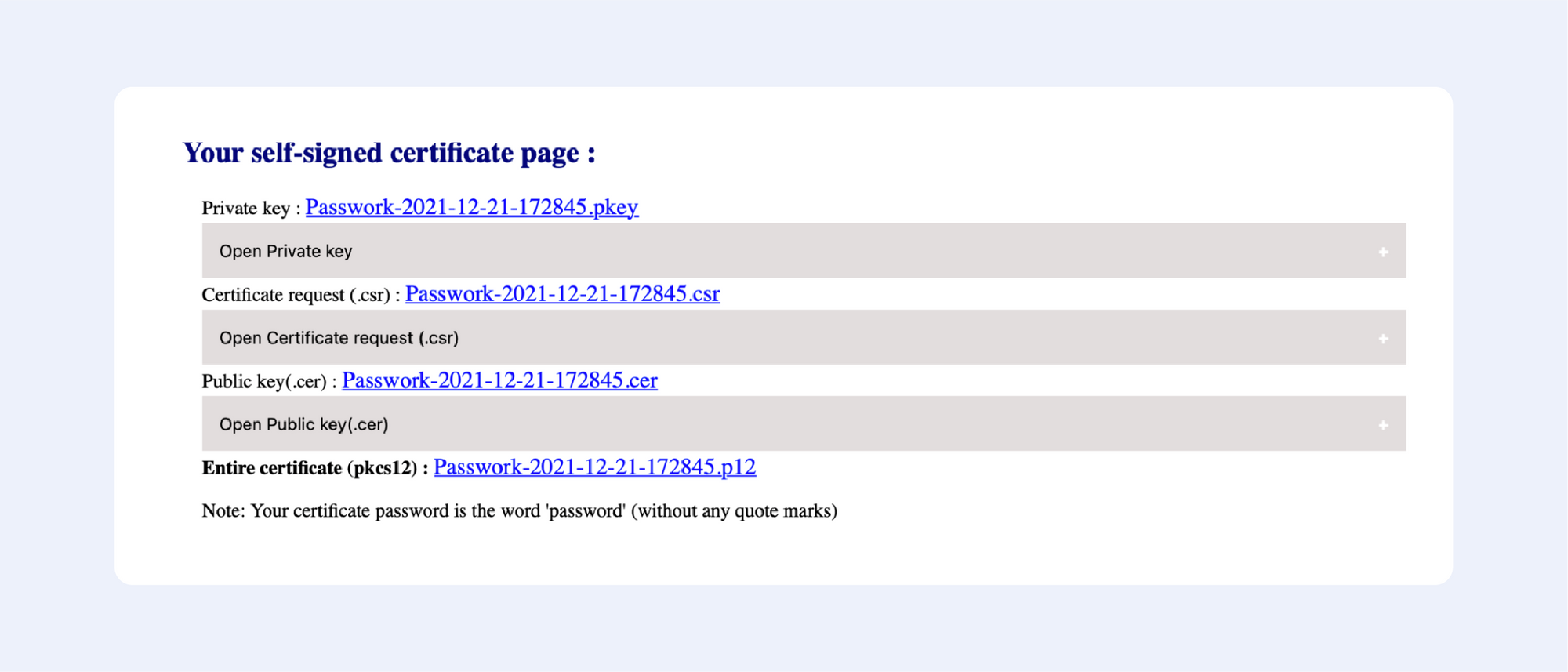
It’s that easy!
Among the online services that allow you to generate self-signed certificates, this one is the most advanced; just look at all available options to choose from:
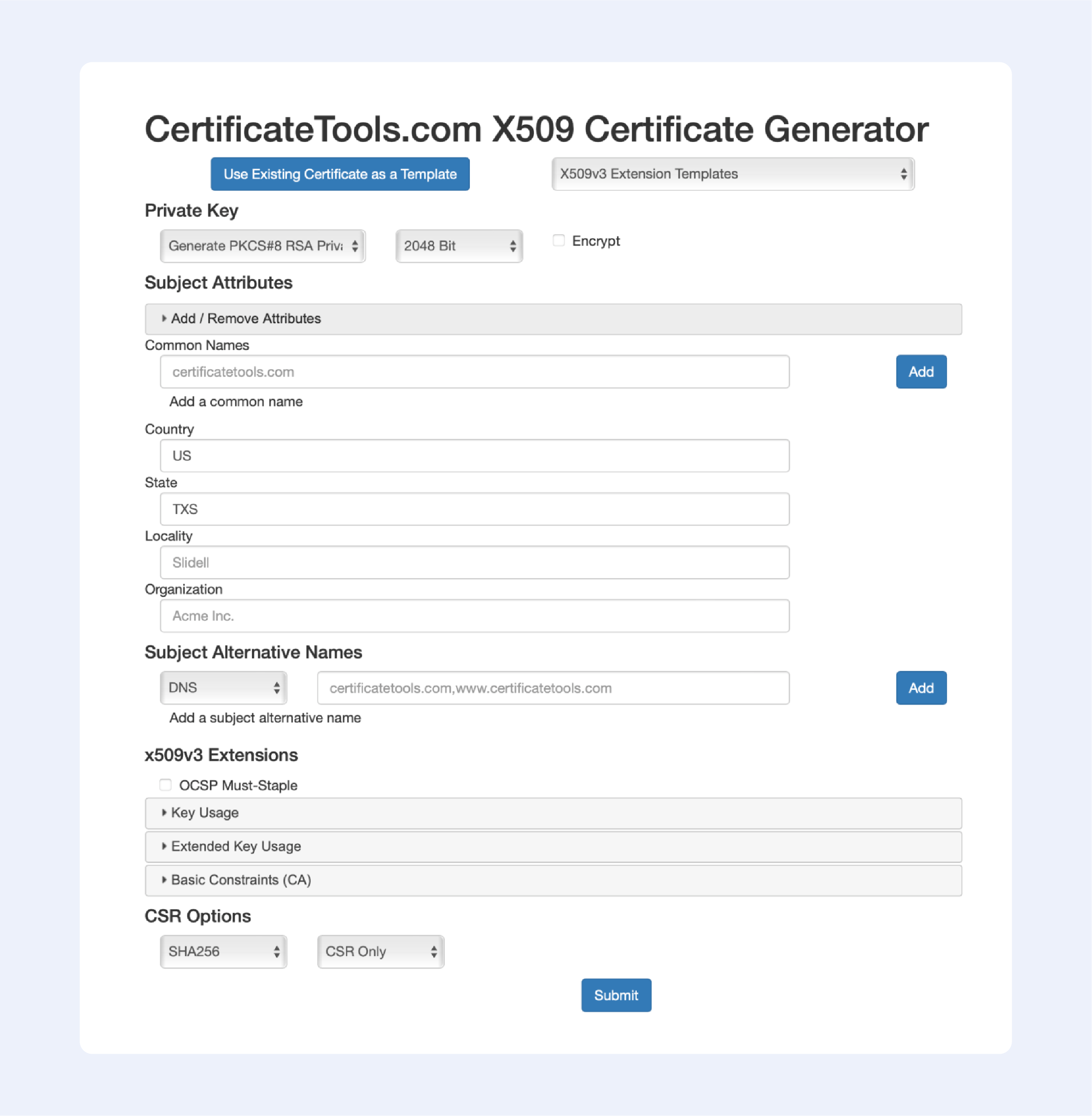
Now let’s continue with offline solutions, that are a bit more advanced:
PowerShell 4.0
1. Press the Windows key, type Powershell. Right-click on PowerShell and select Run as Administrator.
2. Run the New-SelfsignedCertificate command, as shown below.
$cert = New-SelfSignedCertificate -certstorelocation
cert:localmachinemy -dnsname passwork.com3. This will add the certificate to the locater store on your PC. Replace passwork.com with your domain name in the above command.
4. Next, create a password for your export file:
$pwd = ConvertTo-SecureString -String ‘password!’ -Force -AsPlainText5. Replace password with your own password.
6. Enter the following command to export the self-signed certificate:
$path = 'cert:localMachinemy' + $cert.thumbprint
Export-PfxCertificate -cert $path -FilePath
c:tempcert.pfx -Password $pwd7. In the above command, replace c:temp with the directory where you want to export the file.
8. Import the exported file and deploy it for your project.
Use OpenSSL
1. Download the latest OpenSSL windows installer from a third-party source;
2. Run the installer. OpenSSL requires Microsoft Visual C++ to run. The installer will prompt you to install Visual C++ if it is already not installed;
3. Click Yes to install;
4. Run the OpenSSL installer again and select the installation directory;
5. Click Next;
6. Open Command Prompt and type OpenSSL to get an OpenSSL prompt.
The next step would be to generate a public/private key file pair.
1. Open Command Prompt and create a new directory on your C drive:
C: >cd Test2. Now go to the new directory:
C: Test>3. Now you need to type the path of the OpenSSL install directory followed by the RSA key algorithm:
C: Test>c:opensslbinopenssl genrsa -out privkey.pem 40964. Run the following command to split the generated file into separate private and public key files:
C: Test>c:opensslbinopenssl ssh-keygen -t rsa -b 4096 -f privkey.pemOnce you have the public/private key generated, follow the next set of steps to create a self-signed certificate file on Windows.
1. Go to the directory that you created earlier for the public/private key file:
C: Test>2. Enter the path of the OpenSSL install directory, followed by the self-signed certificate algorithm:
C: Test>c:opensslbinopenssl req -new -x509 -key privkey.pem -out cacert.pem -days 1093. Follow the on-screen instructions;
4. You need to enter information about your organization, region, and contact details to create a self-signed certificate.
We also have a detailed article on OpenSSL – it contains more in-depth instructions on generating self-signed certificates.
Using IIS
This is one of those hidden features that very few people know about.
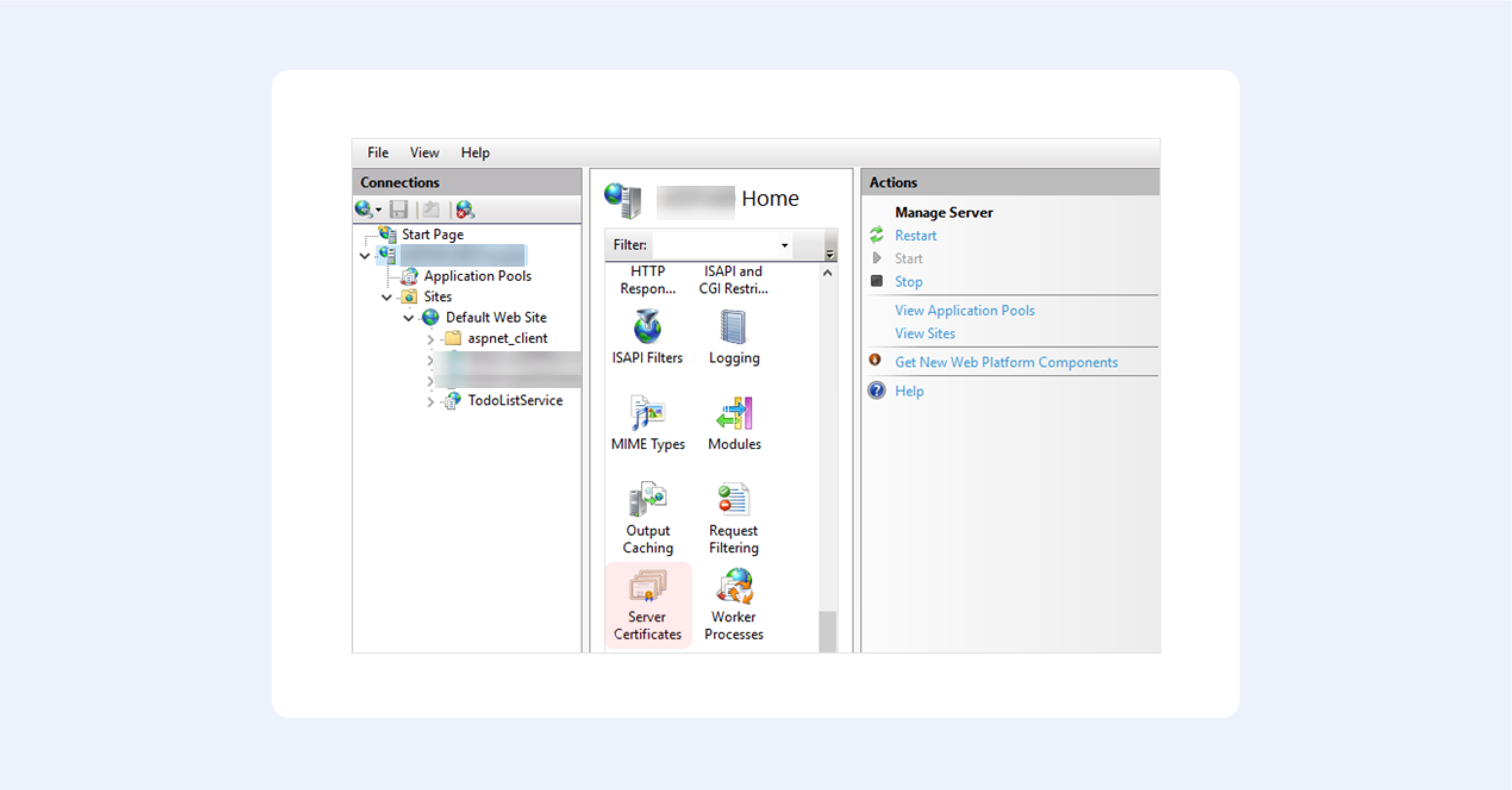
1. From the top-level in IIS Manager, select “Server Certificates”;
2. Then click the “Create” button on the right;
3. This will create a self-signed certificate, valid for a year with a private key. It will only work for “localhost”.
We hope this fruit bowl of options provides you with some choice in the matter. Creating your own self-signed certificate nowadays is trivial, but only until you begin to understand how they really work.
Our option of choice is, of course, OpenSSL — after all, it is an industry-standard.
7 ways to create self-signed certificates on Windows
Are you having trouble remembering your passwords or accessing your account? Perhaps you’re stressing out that you may have been hacked? Well, in any case, restoring your Facebook account utilising reliable Facebook account recovery solutions shall be covered by this article, so buckle up!
In order to regain access to your Facebook account, you can use one of several automated methods. Many are based on the information you provided when you set up your account, which isn’t helpful if you can’t remember the most important piece of information you provided when you set up the account — your password. Also, some information will be out of date, like your recovery phone number or your active email address.
And even if all methods listed below fail, we’ve got an alternative for you right at the very bottom of the article.
Firstly, make sure that you aren't still logged into Facebook somewhere else!
Android and iOS Facebook apps, as well as mobile browsers may all be used to access the site, so you might be logged in on them.
If you are logged in, you can ‘recover’ your account by simply changing the password, and it can be done without a confirmation reset code!
But if you are not logged into Facebook on other devices or browsers — try Facebook's Default Account Recovery Methods.
If at all feasible, log into your Facebook account using the same internet connection and computer or phone that you've used on a regular basis in the past. If Facebook detects your network and device, you may be able to reset your password without having to provide any extra information to Facebook. But first and foremost, you must authenticate your account.
Find and recover your account by providing contact information
The best option is to directly go to the Facebook Recovery Page.
To sign in, enter an email address or phone number that you previously associated with your Facebook profile. When looking for a phone number, test it both with and without your country code, for example, 1, +1, or 001 for the United States; all three variants should work just fine. Even if it doesn't explicitly say so, you may use your Facebook credentials to log in — instead of your mobile number or email.
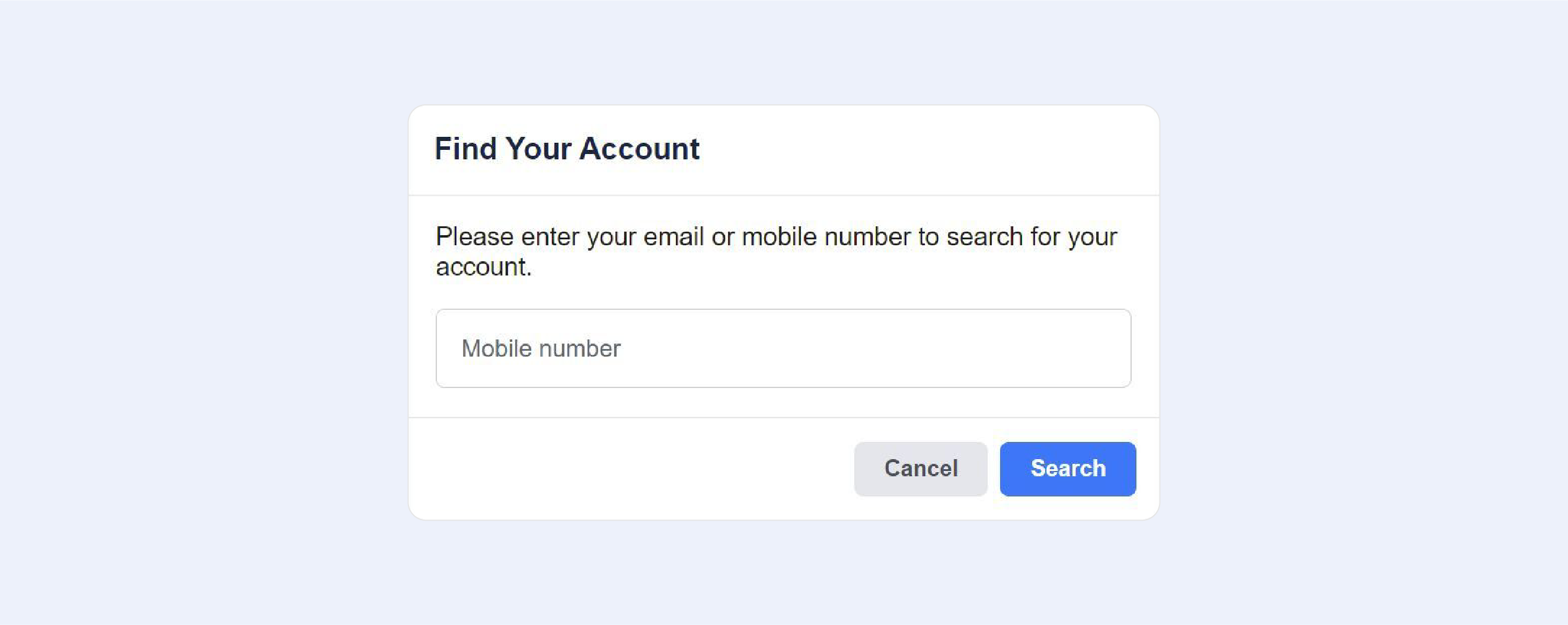
Your profile will be summarised once you have successfully identified your account, as seen in the screenshot below. Please double-check that this is indeed your account and that you still have access to the email address or phone number mentioned before proceeding. The option of choosing between email or phone recovery may still be available to you.
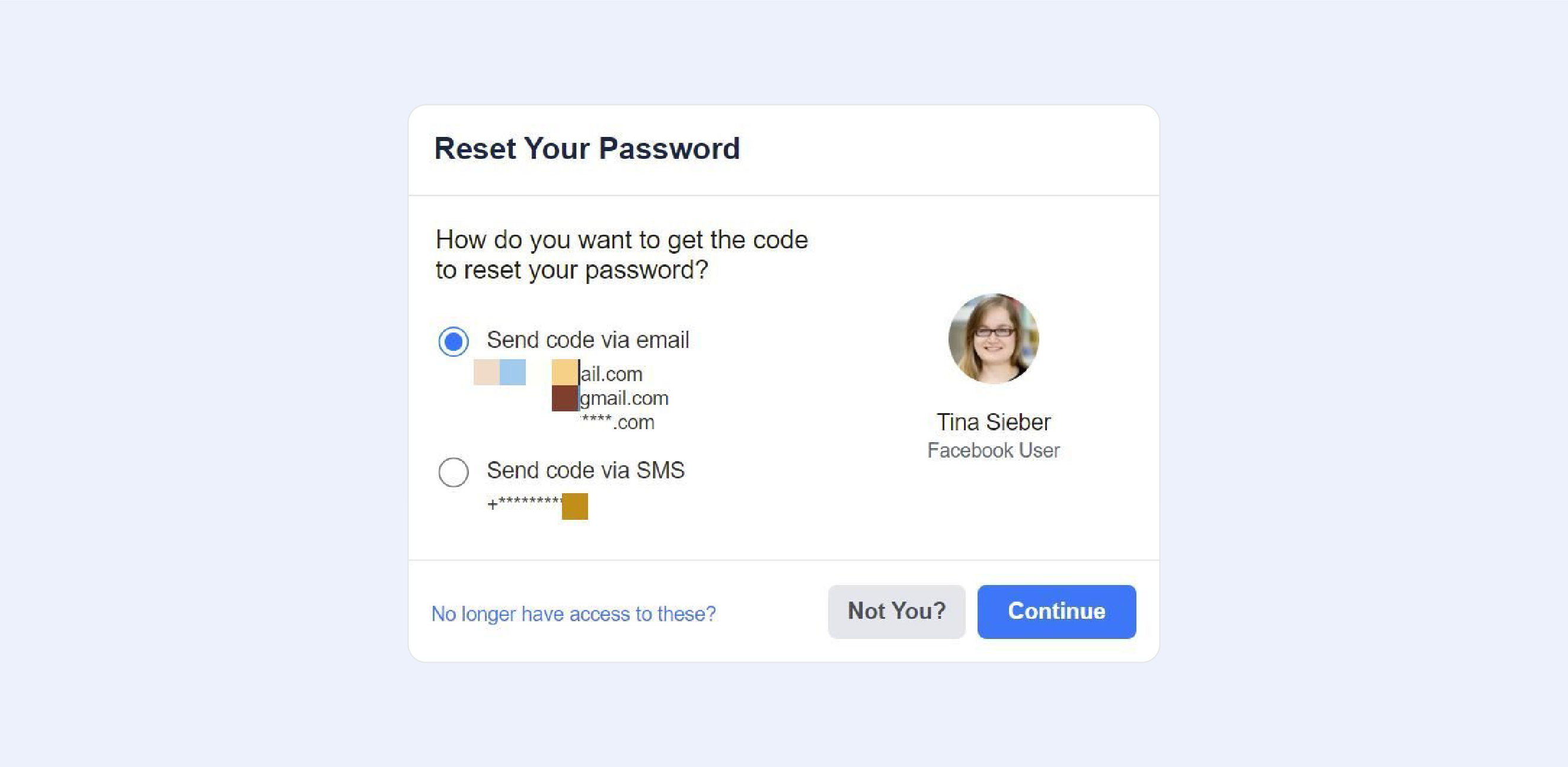
If everything appears to be in order with the contact information that Facebook has on file for you, though, click Continue. A security code will be sent to you by Facebook.
Retrieve the code from your email or phone (depending on whatever method you used), input it, and rejoice in the knowledge that you have regained access to your Facebook profile.
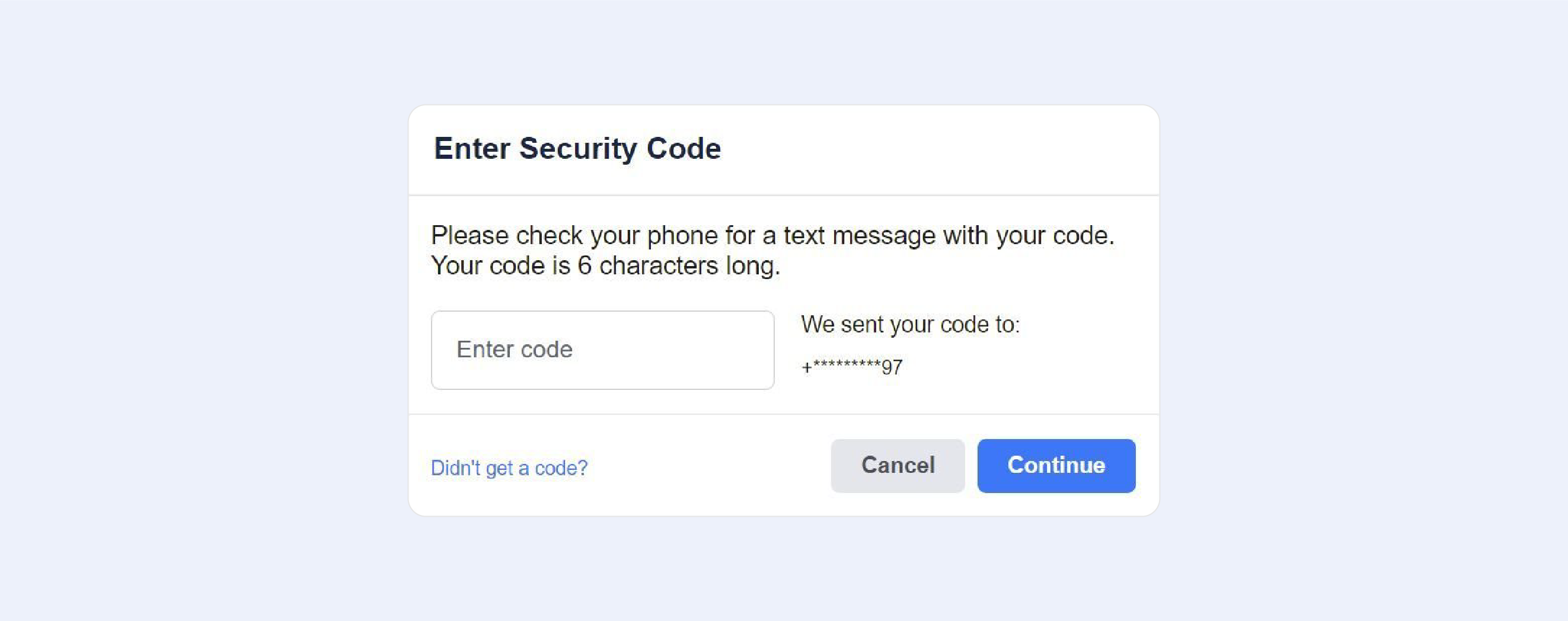
At this point, you have the option of creating a new password, which we highly advise you to do.
If you don't receive the code via email, check your spam folder, or make sure you can receive text messages from unknown senders if the code doesn't arrive to your mobile.
If you are still unable to receive the code, choose Didn't get a code? from the drop-down menu. You can return to the previous screen by clicking the X in the bottom-left corner of the Enter Security Code box.
Maybe you'll get lucky and discover that you don't, in fact, have access to the account at all!
Log back into your Facebook account
You should immediately reset your password and update your contact information if you have regained access to your Facebook account after a suspected hijacking.
To keep your Facebook account safe, follow two simple rules. Don't forget to get rid of any email addresses or phone numbers that you no longer have access to. Also, enable two-factor authentication on all of your social media accounts in order to prevent a loss of access in the future.
Don’t forget, the Facebook Help Community is a great place to find answers to your issues.
If all else fails, creating a new Facebook profile might not be as bad as you think
Over the past few years, we've received a large number of letters from users who were unable to regain access to their Facebook accounts, despite following each and every one of the instructions listed above.
Typically, their contact information was out of date, the recovery codes offered by Facebook were ineffective, or the corporation never responded to their request for identification verification. And at that point, you’re pretty much out of options.
You have to accept the fact that you must move on. Even though it's painful, you must learn from your mistakes and register a new user account.
Always include legitimate contact details, don’t forget to up the security on your Facebook account, and completely re-create your profile from the ground up. Despite the inconvenience, it’s a better option than doing nothing. Not to mention, you won’t have any of those embarrassing old photos, and you can only add people as friends that really matter to you now.
How to recover your Facebook account

In Passwork 6.2 we have introduced a range of features aimed at enhancing your security and convenience:
- Bin
- Protection against accidental removal of vault
- Protection against 2FA brute force
- Accelerated synchronization with LDAP
- Improved API settings
- Bug fixes in role management
Bin
Now, when deleting folders and passwords, they will be moved to the Bin. If needed, they can be restored while preserving previously set access permissions. Vaults are deleted without being moved to the Bin — they can only be restored from a backup.
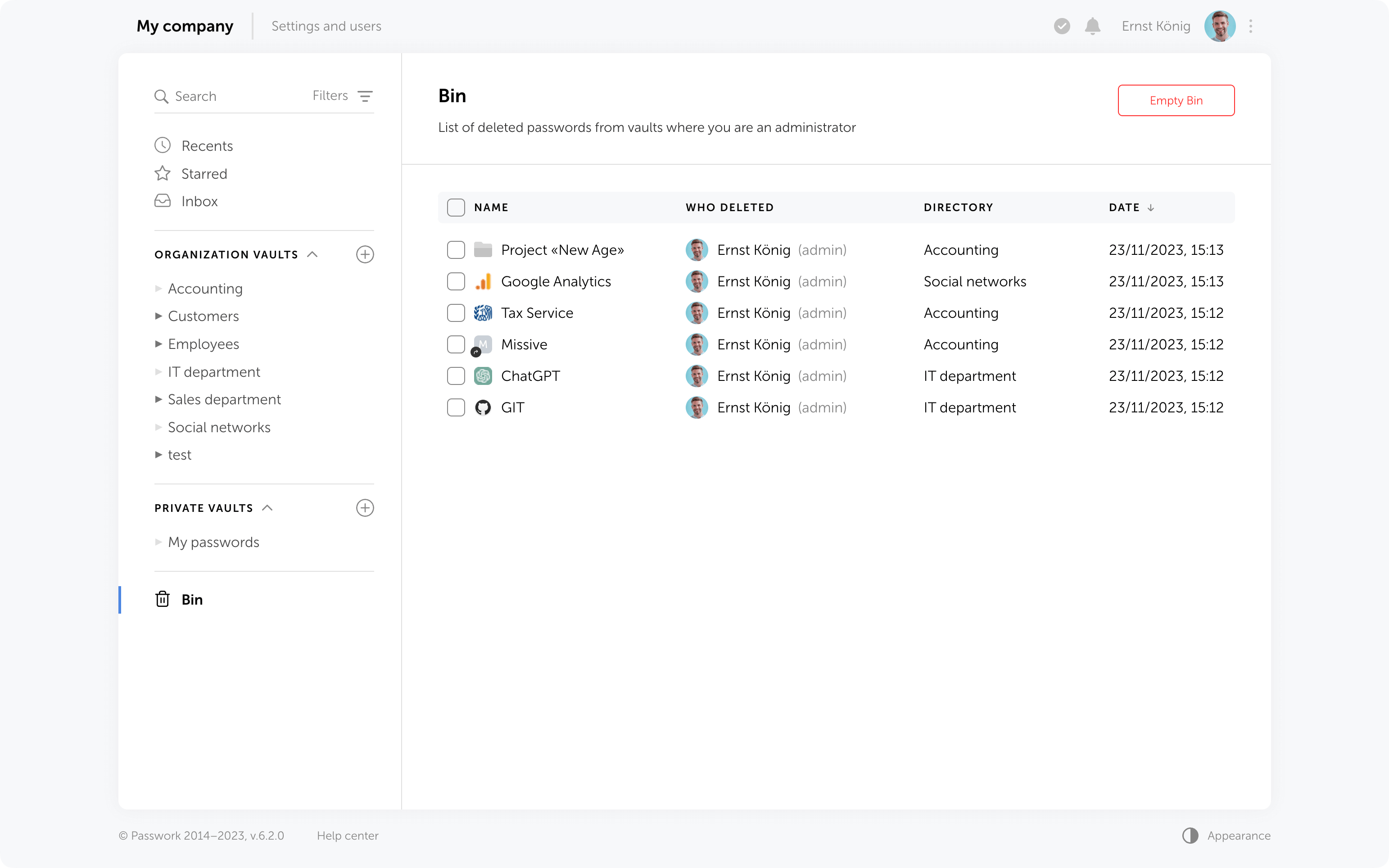
Who can view deleted passwords and folders in the Bin?
Inside the bin users can see the deleted items from those vaults in which they are administrators. For instance, an employee who is not an administrator of organization vaults will only see the deleted passwords and folders from his personal vaults when opening the Bin.
In addition to object names, the Bin also displays the usernames of people who deleted data. You can also see the initial directory name and the deletion date.
Object restoration
Objects from the Bin can be restored to their initial directory if it has not been deleted or moved. Alternatively, you can choose any other directory where you have edit and higher access levels.
When restoring deleted folders to their initial directories, user and role access levels will also be restored exactly as they were previously manually set in these folders. Other access permissions will be set based on the current permissions in the initial directory.
When restoring folders to a directory different from the initial, access levels will always depend on the current permissions in the selected directory.
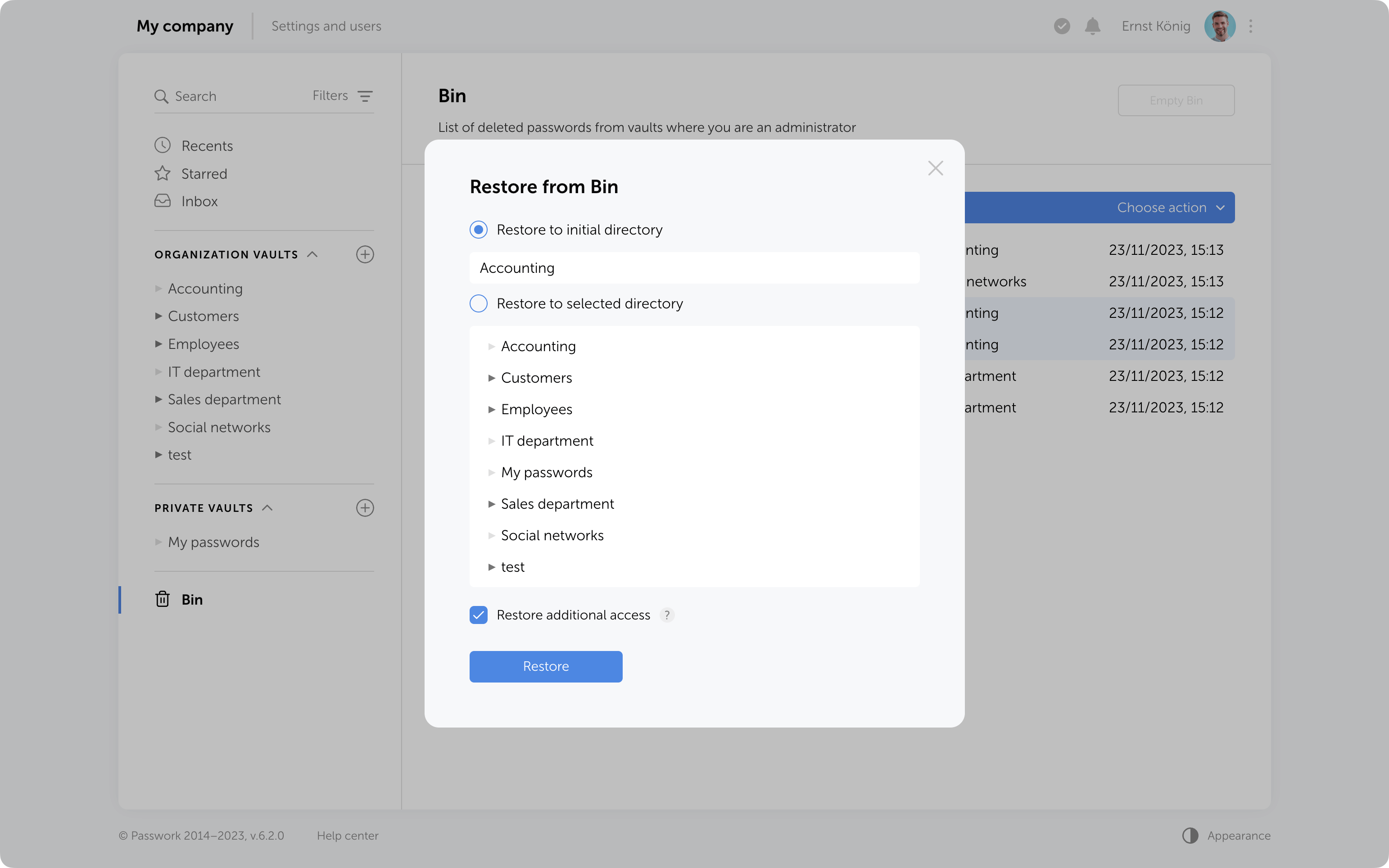
Additional access to deleted passwords
If passwords have been shared with users, moving them to the Bin will remove them from the “Inbox” section, and any shortcuts or links to these passwords will become nonfunctional.
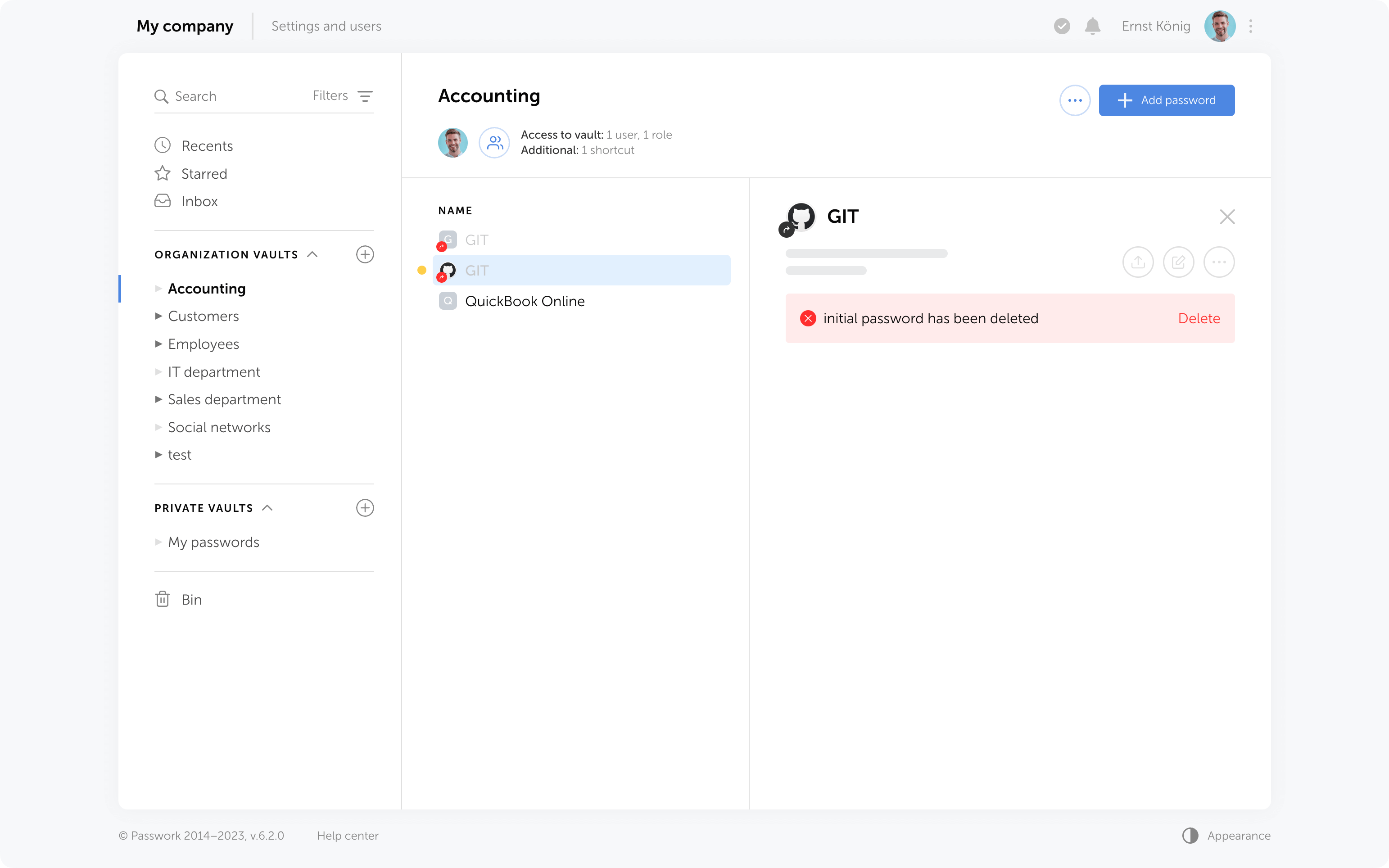
Restoring additional access
When restoring from the Bin, it is possible to regain additional access levels to passwords. Passwords that were shared with users will reappear in their “Inbox” section, access to passwords through shortcuts will be restored, and links that have not expired will become functional again.
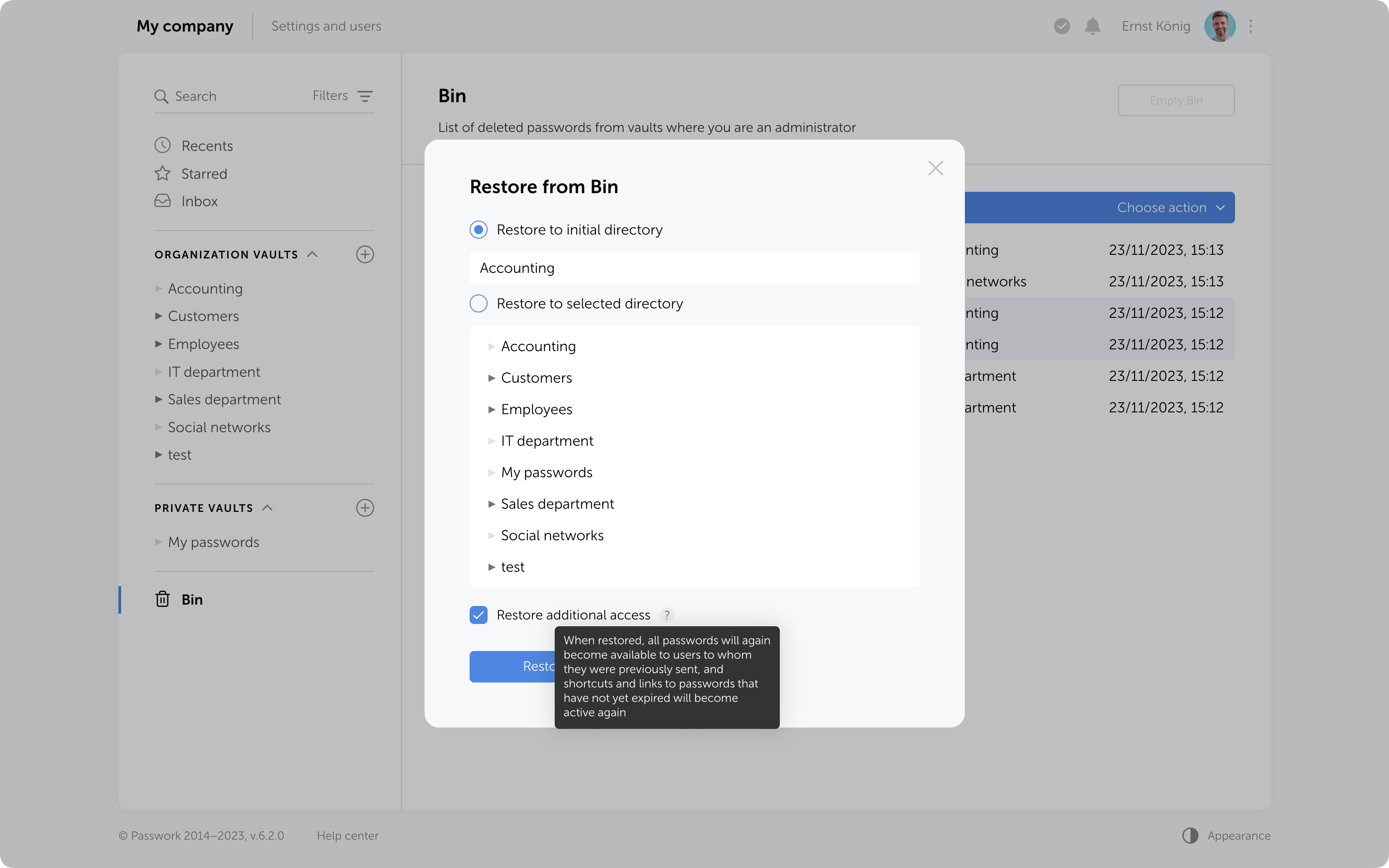
Bin cleanup
You can delete selected items from the Bin or use the "Empty Bin" button to remove all items contained inside.
It's important to note that in the Bin you only see the items which were deleted from the vaults where you are an administrator. Objects from other vaults are not visible, and clearing the Bin will not affect them.
In future, the option to configure automatic Bin cleanup will be added.
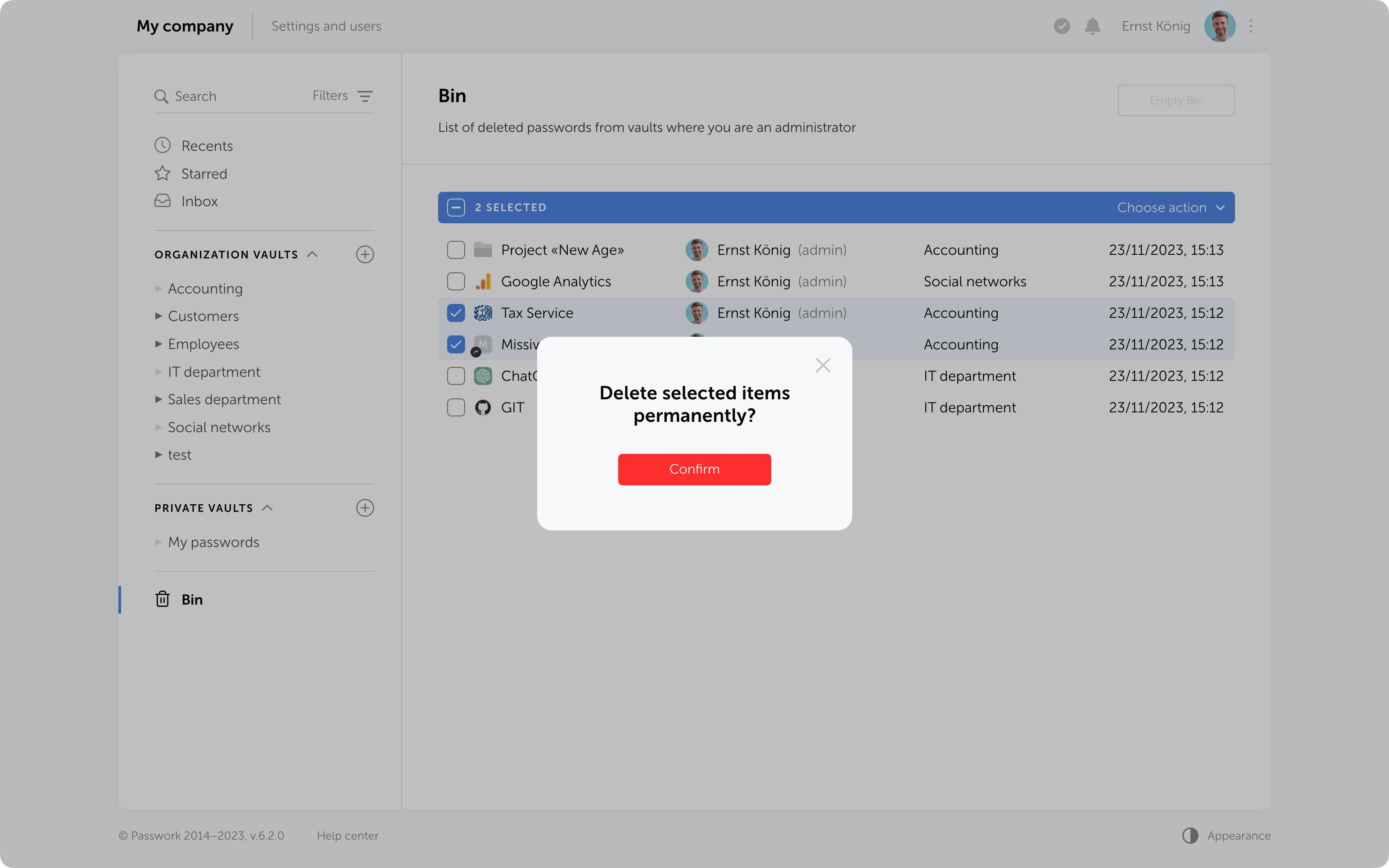
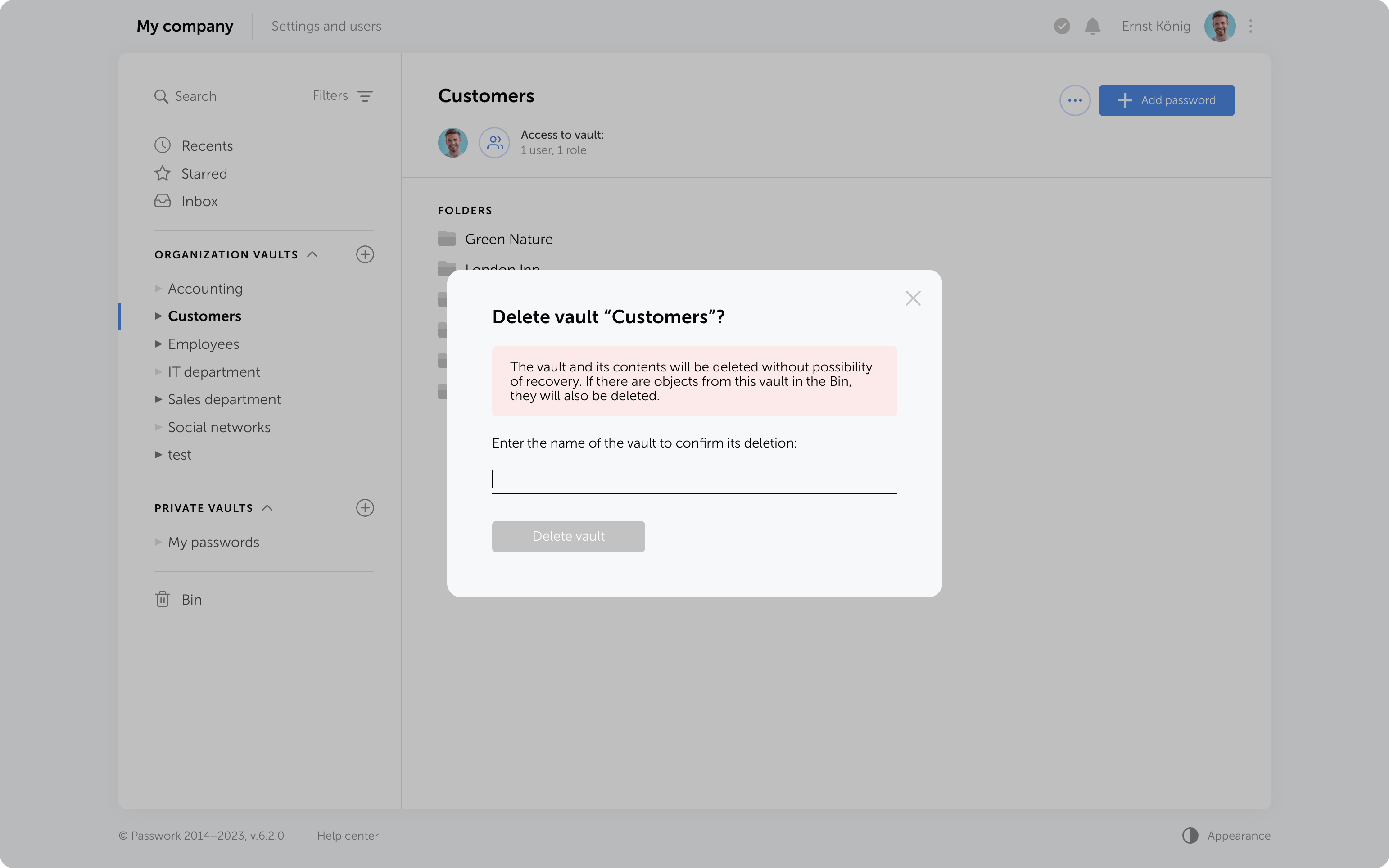
Protection against accidental removal of vault
To confirm the deletion of a vault, you now need to enter its name. It will be permanently deleted along with all the data inside. Additionally, if there are passwords or folders from this vault in the Bin, they will also be removed.
Protection against 2FA brute force
Protection against 2FA brute-force attacks has been added. After several incorrect attempts to enter the 2FA code, the user will be temporarily locked. The number of attempts, input intervals, and the lockout time are set in the config.ini file.
Other changes
- LDAP synchronization has been accelerated
- Descriptions of parameters and minimum allowable values for API token expiration time and API refresh token expiration time have been added to the API settings section
- Automatic assignment of "Navigation" to parent folders in role management has been fixed
- The issue when a vault administrator could not add roles to a vault and manage its permissions has been fixed
- The issue with showing additional access rights to passwords when moved to another vault has been fixed
Upgrade Instructions — How to update Passwork
More information about features and prices — on the Passwork website
Introducing Passwork 6.2

Over the past decade, data has transitioned from mere information to a precious asset. Numerous enterprises thrive on data, while others crumble with its loss. Customer personal information, analytics, financial transaction records and more hold monetary value. Yes, there's an abundance of informational "clutter" around, but even amid hard-to-spot data, a skilled cybercriminal can discover a gold mine.
The acceleration of information technology is rapid, with fresh information emerging and being processed every moment. Often, companies simply lack the time to sift the "wheat" from the "chaff" and, as a result, release sensitive data, like customers' home addresses for delivery, into the open.
Most firms have mastered data collection, some have ventured into processing it, and a fewer number into analyzing it, but not all have grasped how to safeguard it. In this article, we’ll explore what qualifies as sensitive data, how to shield it, and the primary blunders made while handling sensitive data.
What sets apart ordinary data from sensitive data?
With the trend of data accumulation in the market, corporations have embraced it wholeheartedly. This opens up numerous avenues for growth, business broadening and optimization, and introducing new offerings to the market. For instance, by scrutinizing customer conduct, you can present them with the products they need at the opportune moment. Or, simply, knowing customers' birthdays, send a discount coupon as a present, encouraging a new purchase. The possibilities are myriad, and they stem from entirely diverse data types. That's why enterprises amass data even before understanding its use. It's for the just-in-case scenario.
Similarly, it's not always feasible to instantly determine the significance of data and the extent of protection required. Some opt for overcaution, storing data securely from the outset, while others leave it in public view, thus risking it. The sensitivity of data can be gauged by asking — what’s the fallout if it’s pilfered?
Two outcomes exist. Nothing occurs — the data isn't sensitive. The offender, directly or indirectly, could inflict harm on the business or customers. For instance, by pilfering personal data, like full names and phone numbers, and releasing them online, the company’s reputation takes a hit. Or, by stealing an individual’s data — their address, purchasing tendencies, and, say, date of birth, orchestrate a social engineering assault.
Sensitive data encompasses information that could potentially jeopardize its possessor. For regular folks, it’s mainly personal and financial data, medical details, relationship data, personal visuals, and data on preferences. For companies, it includes internal business records, customer and employee databases, confidential documents, market evaluations, and the like.
Recognizing sensitive data
The theft or exposure of sensitive data undermines a company's customer privacy, triggers financial setbacks, and could even threaten an organization’s security. Hence, distinguishing sensitive personal data from common data is crucial. This involves carrying out a data classification and risk assessment.
This could encompass evaluating potential damage in case of a data breach, as well as examining legal mandates for specific data types. Primarily, anything related to sensitive information and personal data should be guarded. However, the task of identifying data types doesn’t conclude here. For instance, trade secrets can be shielded under 21 orders or at your discretion, but personal data must be classified and shielded by law. Information security experts opine that to pinpoint sensitive company data, the IS division, along with representatives from various sectors — accounting, legal, HR, and marketing — should formulate guidelines to identify sensitive information. The primary focus here would be potential financial or reputational harm from information leakage. Yet, the potential threat indicator of a data breach may not always be objective. Numerous cyber incidents involving social engineering demonstrate that even seemingly harmless data about a person can be utilized to perpetrate a crime.
Key blunders in handling sensitive data
Both enterprises and users can be culpable for sensitive data leakage. On the corporate side, the usual culprit is a basic disregard for information security norms. For instance, unprotected corporate networks, operating on outdated operating systems, or absence of antivirus protection. On the user side — unawareness of cyber hygiene norms and a lack of understanding of what data might be sensitive. Common errors enabling sensitive data leakage:
• Inadequate password and account safeguards
• Lack of data categorization within the firm
• Improperly set up security systems
• Absence of data encryption
• Employees are untrained in cyber hygiene
Moreover, information is often undervalued by both corporations and individuals. For instance, a person may deem their passport information crucial but be indifferent about sharing their health information on social networks. Like any other domain of information security, elementary measures are paramount. For example, remembering updates, prompt training of staff in cyber hygiene, and employing protective software.
Conclusion
The subject of sensitive data is steadily gaining traction, as only in recent times have assailants learnt to actively exploit personal or corporate data to commit offenses. For larger and more technologically advanced companies, the issue is being addressed at a more sophisticated level, as they have not only learnt how to analyze and segment data but also how to defend it. However, there's another facet to consider - the company service users themselves. They may possess minimal awareness of the worth of their personal data and trigger leaks.
Sensitive information: distinguishing the crucial from the commonplace

Prominent enterprises have endured substantial setbacks due to security breaches within their mobile applications, underscoring the criticality of app security that is often overshadowed by server-side concerns. Contrary to popular belief, mobile apps are not mere interfaces for server data; their vulnerabilities can inflict extensive damage, not limited to a single user but potentially devastating to the business at large. This article aims to elucidate this often-overlooked risk by showcasing notable instances where mobile app vulnerabilities have led to significant financial and reputational harm.
TikTok's multi-faceted security dilemmas
The year 2020 was marked by significant scrutiny directed at TikTok, a widely used social platform. The app was caught accessing clipboard data on Apple devices without user authorization, a clear invasion of privacy that could potentially lead to the exposure of sensitive personal and professional information. The same period saw the emergence of other security loopholes that provided attackers with the capability to compromise accounts, exfiltrate personal data, or circulate harmful content. The situation was further aggravated by concerns over TikTok's alleged ties to foreign government entities. The controversy was so severe that it led to the app's prohibition in several regions and culminated in a class-action lawsuit that cost the company $92 million in settlements. This series of events underscored the imperative for app developers to meticulously govern data collection practices to safeguard user privacy.
Strava's global heatmap incident
The fitness-oriented app Strava faced its own share of controversy in 2018 when it released a global heatmap of user fitness activities. What might have been a novel idea turned sour when it inadvertently compromised the safety of military personnel by revealing their movements and even the locations of military facilities. Although Strava claimed that the map was anonymous, resourceful individuals managed to de-anonymize the data, proving that even data represented as anonymous can be reconstructed to reveal identities. This incident sparked a global debate on the security ramifications of sharing fitness tracking data through apps and the potential threats it could pose to individuals and national security.
Starbucks' mobile app compromise
In 2015, Starbucks, the global coffeehouse chain, confronted a serious breach when its mobile app fell victim to an attack. Due to inadequate authentication processes, cybercriminals managed to hijack customer accounts. This security oversight led to unauthorized access to payment details and illegal transactions, leaving customers financially vulnerable and causing a major dent in Starbucks’ corporate image.
WhatsApp and a spate of security breaches
WhatsApp, one of the most popular messaging apps worldwide, wasn't immune to security flaws. In 2019, a vulnerability was exploited to install Pegasus spyware on users' devices, leading to a significant breach of confidential information, including personal messages and call logs. Another flaw, known as "Media File Jacking," was identified, affecting both Android and iOS users. This particular vulnerability allowed cybercriminals to alter media files, replacing them with inappropriate or harmful content. A notably critical issue emerged in 2021, involving WhatsApp's group chat feature, which inadvertently exposed users to phishing and other social engineering attacks due to flawed invitation controls. These incidents collectively contributed to a substantial erosion of trust among WhatsApp users.
Clubhouse's privacy controversy
Clubhouse, the audio-based social network that gained rapid popularity, faced serious backlash when a significant vulnerability was discovered. The flaw allowed malicious actors to secretly record and broadcast live audio conversations, a blatant violation of user privacy. Furthermore, the transmission of user IDs in plain text made it possible to de-anonymize conversations, adding fuel to the growing privacy concerns. The repercussions included a severe reputational hit and heightened skepticism about the security protocols of emerging social media apps.
Signal's unexpected security flaw
Signal, an app that prides itself on security, encountered a surprising setback when a vulnerability was discovered, allowing for PIN brute-force attacks. This revelation was particularly alarming given the app's reputation for robust security, and it inevitably affected its perceived reliability.
Zoom's security and privacy scandals
Zoom, a leader in video conferencing, faced multiple issues in 2020. A vulnerability was exploited by uninvited individuals to intrude on private meetings, leading to the infamous "Zoom-bombing" incidents. Furthermore, misleading claims about the app's encryption standards led to public uproar when it was revealed that Zoom had the technical capability to access private conversations. This forced the company to revamp its encryption system on a tight schedule, incurring considerable costs.
Snapchat's ongoing security struggles
Snapchat, popular among younger demographics, has had its fair share of security woes. Various vulnerabilities allowed for account breaches and even real-time location tracking, posing a severe threat to user safety and privacy. These issues resulted in negative publicity and declining user engagement.
Uber and Airbnb's security breaches
Both Uber and Airbnb have experienced security breaches that enabled attackers to take over user accounts. These incidents, involving unauthorized rides and bookings, underlined the critical importance of robust authentication mechanisms and the potential financial and reputational damages stemming from such breaches.
Fortnite’s gaming data breach
Fortnite, a gaming sensation, hasn’t been spared from security flaws. Vulnerabilities discovered allowed attackers to hijack accounts, make unauthorized in-game purchases, and access sensitive personal data. These incidents brought to light the risks associated with online gaming platforms and the need for enhanced security measures, particularly given the young age demographic of many users.
Conclusion
In summary, it's evident that mobile app vulnerabilities are a widespread issue, often underreported or overlooked by the general populace. Users must recognize the gravity of the personal and sensitive information stored within their devices and the apps they use. It's prudent to avoid reusing passwords, to be wary of suspicious apps, and to exercise caution when sharing information online. In an era where digital threats are increasingly sophisticated, vigilance is our first line of defense.
Unveiling the giants: corporations whose flawed apps inflicted business catastrophes

In 2024, the digital finance landscape is increasingly challenged by sophisticated forms of fraud, particularly carding. This type of credit card fraud, involving the unauthorized use of stolen card information, poses significant risks to both individuals and financial institutions. This comprehensive exploration delves into the mechanisms of carding, its evolutionary trajectory in the realm of financial fraud, and the multi-faceted strategies being employed to protect bank accounts in this digitally-dominated era.
Understanding carding
Carding is a complex process initiated by the illicit acquisition of credit card information. This can occur through various methods:
• Sophisticated hacking operations that breach financial databases
• Phishing schemes designed to deceive individuals into divulging their details
• Large-scale data breaches at major retailers or financial institutions
Once fraudsters acquire this data, they test it to verify its legitimacy and then use or sell it for unauthorized transactions, often leveraging the anonymity of the dark web. The speed and stealth with which carding operations are conducted make them a particularly pernicious and challenging form of financial fraud to counteract.
The evolution of financial fraud
Financial fraud has undergone a significant transformation over the years. Initially, fraudsters employed physical methods like skimming devices on ATMs. However, the digital revolution brought about more complex and less detectable methods, including malware that captures sensitive information and sophisticated phishing operations. These digital methods necessitate equally advanced countermeasures in security and consumer awareness.
Regulatory bodies have escalated their efforts in enforcing data security standards. Financial institutions are now mandated to comply with rigorous data protection regulations, including conducting regular security audits and adhering to cybersecurity best practices. These regulations are crucial in ensuring a baseline of security across the financial sector.
Protecting bank accounts in 2024
Enhanced authentication
In response to these threats, banks have significantly enhanced their security measures. The integration of biometric verification methods, such as fingerprint and facial recognition technologies, has introduced a personalized layer of security challenging for fraudsters to replicate. Additionally, two-factor authentication (2FA), combining knowledge-based (passwords) and possession-based (a mobile device for OTPs) elements, has become a standard security practice, drastically reducing unauthorized account access.
Advanced encryption
Encryption is a cornerstone in securing data transmission. Modern banking involves sophisticated encryption protocols that cloak data during transmission, making it virtually impenetrable to interception and misuse. This ensures that even if data is captured by unauthorized entities, it remains secure and indecipherable.
AI and machine learning
The adoption of artificial intelligence and machine learning has been a game-changer in detecting and preventing fraud. These technologies analyze extensive transaction data, identifying anomalous patterns indicative of fraudulent activity. By quickly flagging these irregularities, banks can proactively address potential fraud, often before customers are aware of any risk.
Secure banking applications
The development of secure banking applications has been a focus for financial institutions. These applications come equipped with features like automatic logout after periods of inactivity, fraud alert systems, and encrypted communication channels for reporting suspicious activities. Such features empower customers to safely manage their accounts and contribute to the overall security framework.
Consumer education
Consumers are essential in safeguarding their financial information. Vigilant monitoring of account activities, cautious sharing of personal information, and using secure networks for online banking are fundamental preventive measures. Prompt reporting of any anomalies or suspicious activities to their banks is also vital in preventing the escalation of potential fraud.
Educating these consumers is pivotal in the fight against financial fraud. Banks are actively investing in campaigns to heighten awareness about safe online practices, such as recognizing phishing attempts, using secure networks for financial transactions, and the criticality of promptly reporting unusual account activities.
Conclusion
Given the dynamic nature of financial security, continuous collaboration across sectors is imperative. Financial institutions, technology companies, and law enforcement agencies must maintain open channels of communication and strategy sharing. Ongoing innovation in security technologies and consistent consumer education are critical in staying ahead of evolving threats.
As we proceed through 2024, the safeguarding of bank accounts from threats like carding requires an integrated approach. This strategy involves leveraging cutting-edge technology, enforcing strict regulatory measures, cultivating informed consumer habits, and maintaining constant vigilance. By comprehending the complexities of financial fraud and adopting comprehensive, proactive security measures, we can aim for a more secure financial environment for all participants.
