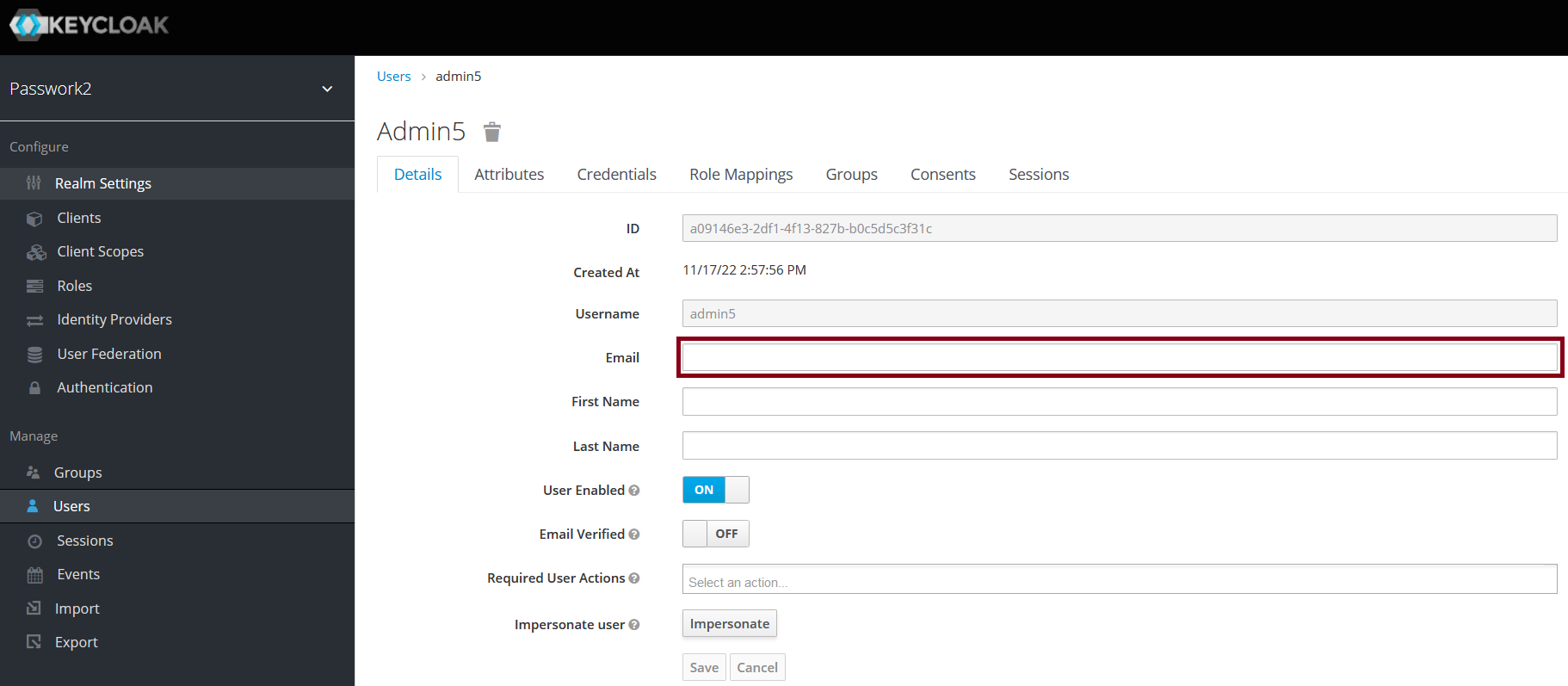
Configuring SSO with Keycloak
Before performing SSO configuration, make sure that the value of the domain parameter in the config.ini configuration file is the current domain name of the Passwork server.
This is necessary so that IDP can download the https://<your-passwork>/sso/metadata file from your server. Your server must be configured to run over HTTPS protocol.
Example parameter in config.ini: domain = https://passwork.example.com
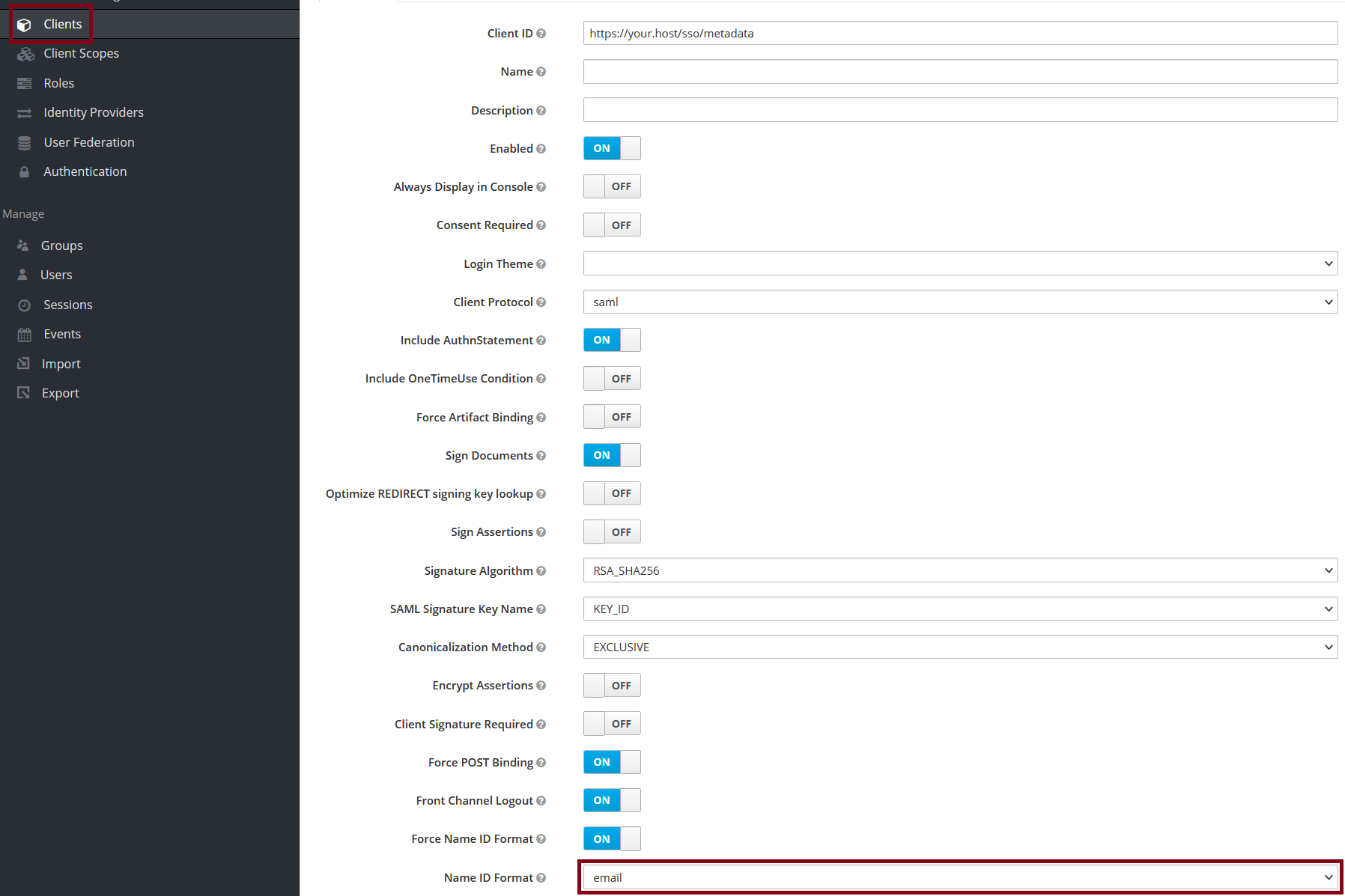
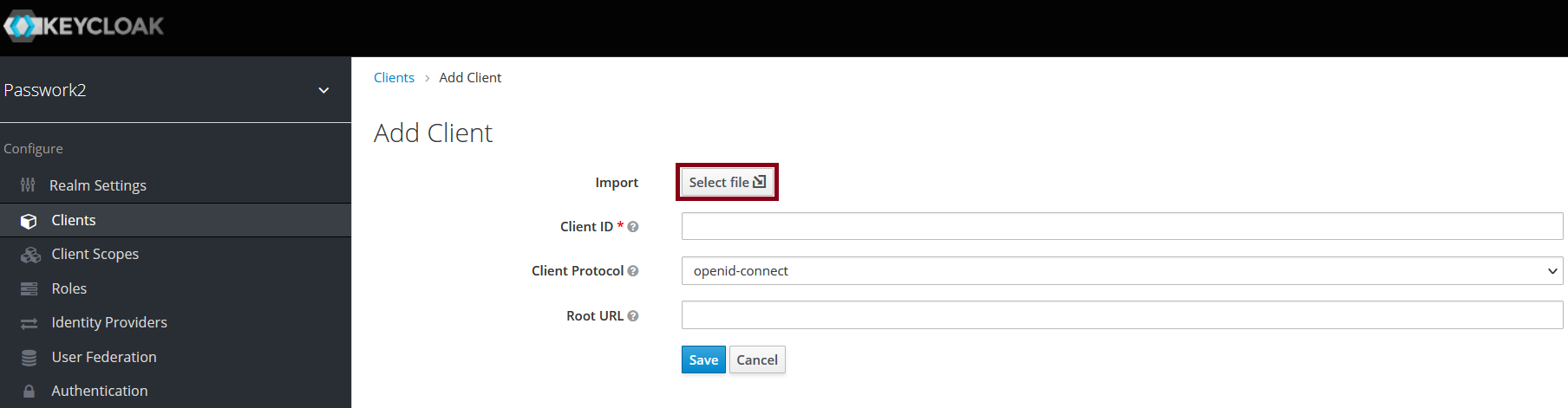
Go to the Clients and click Create
keycloack.json
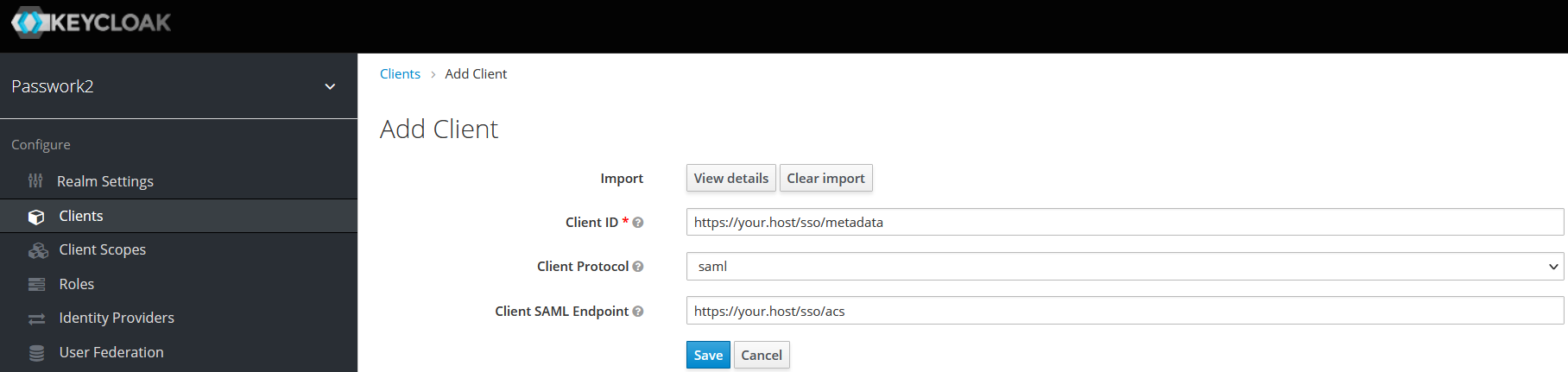
Download the keycloack.json with example settings and change the following values to match your host address
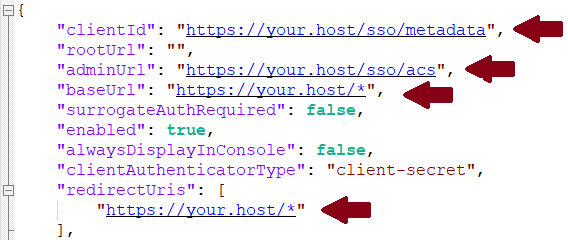
Import the export file on the Add client page
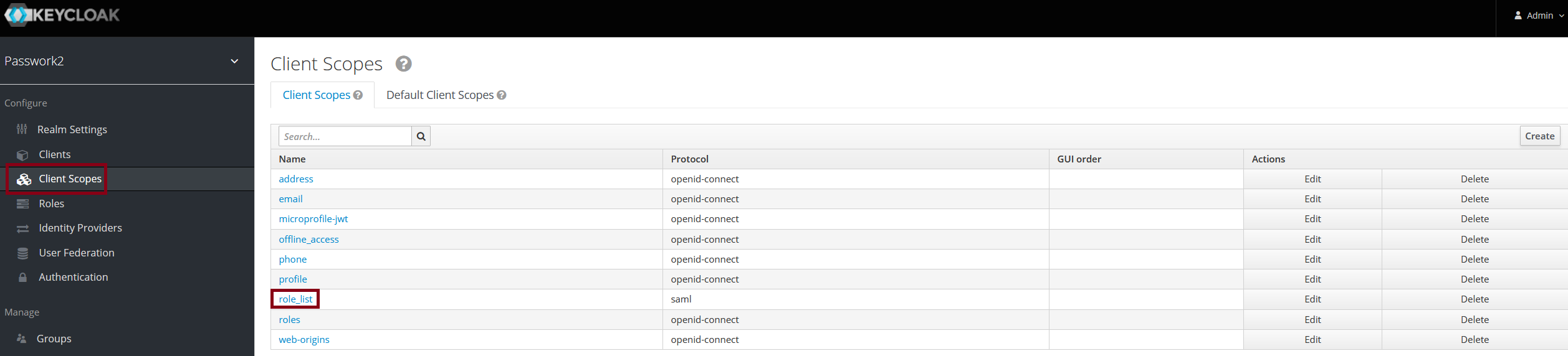
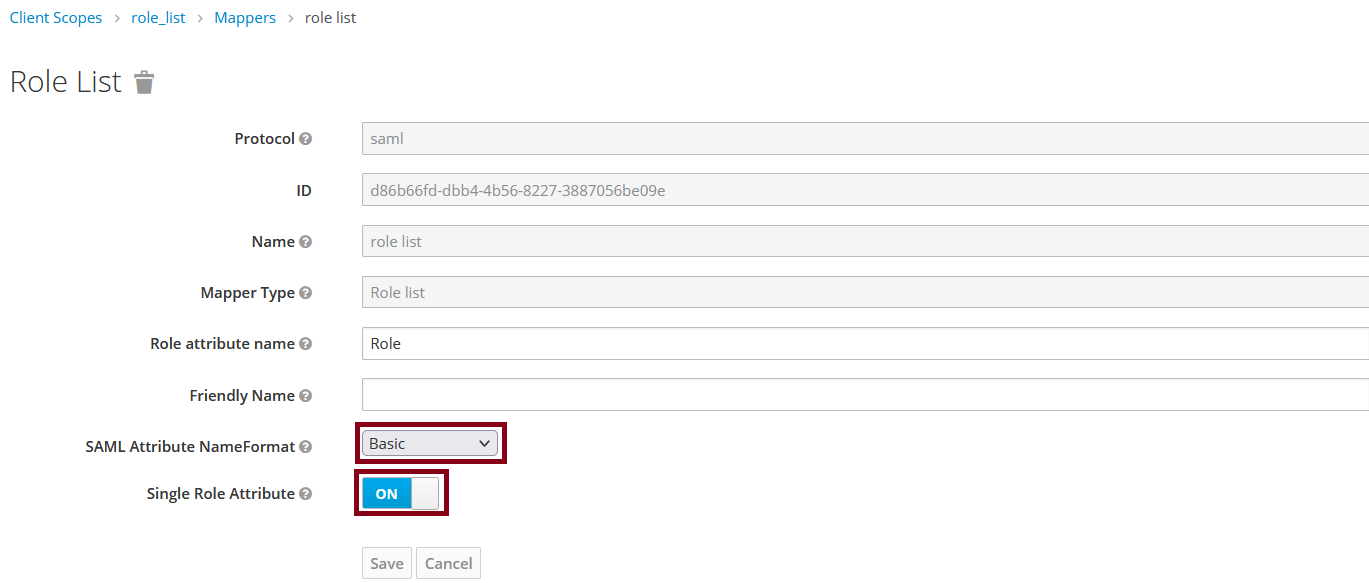
Go to Client scopes and click role_list
In the Mappers tab, select role_list
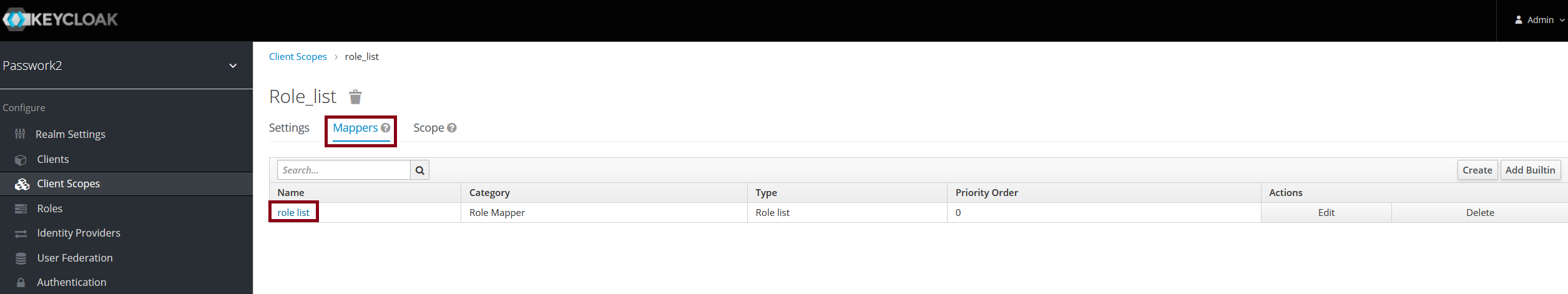
Set the SAML Attribute NameFormat parameter to Basic and enable Single Role Attribute
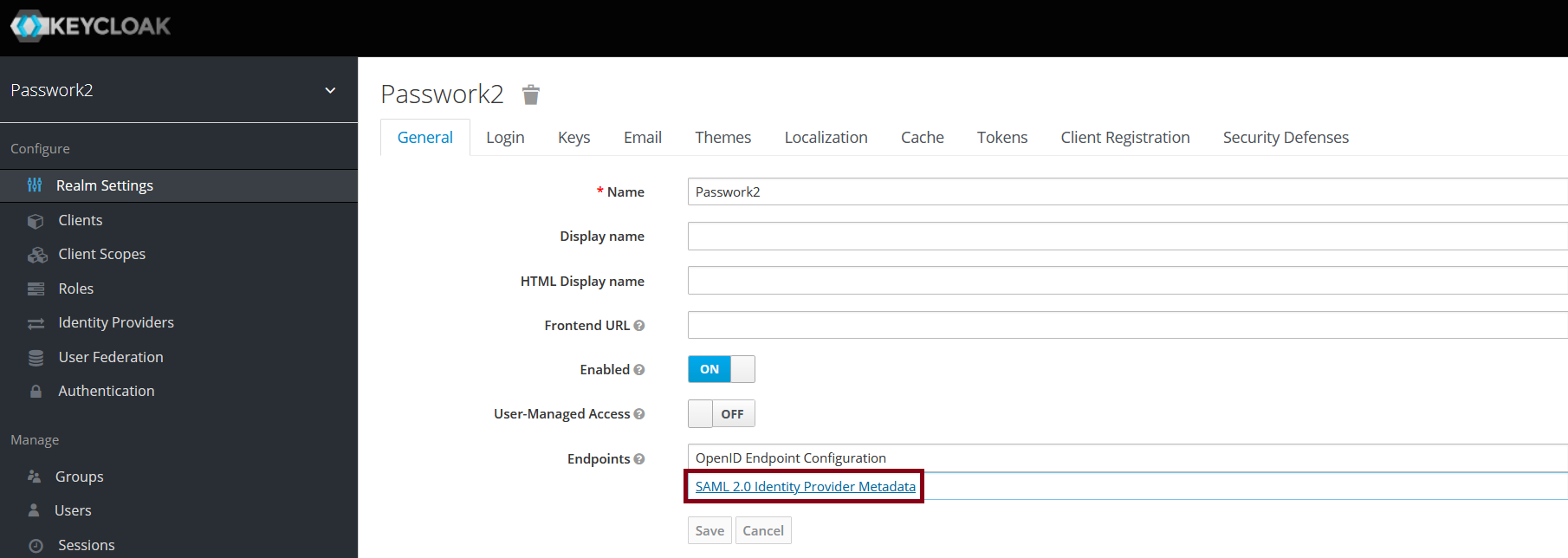
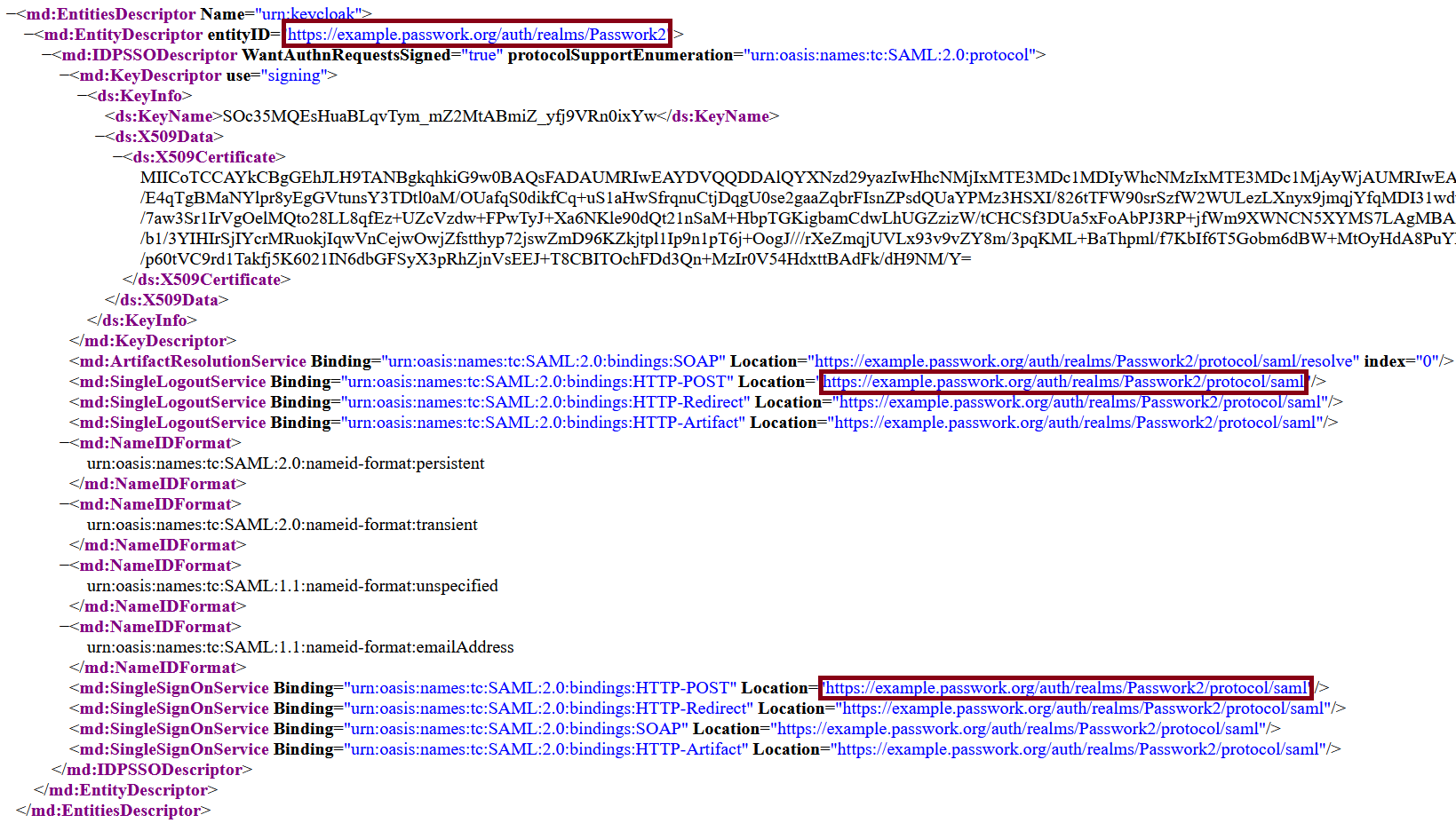
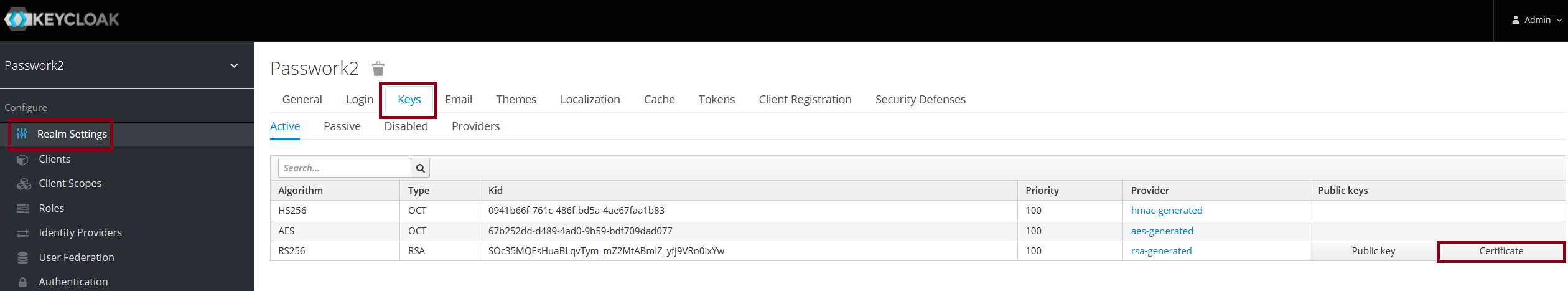
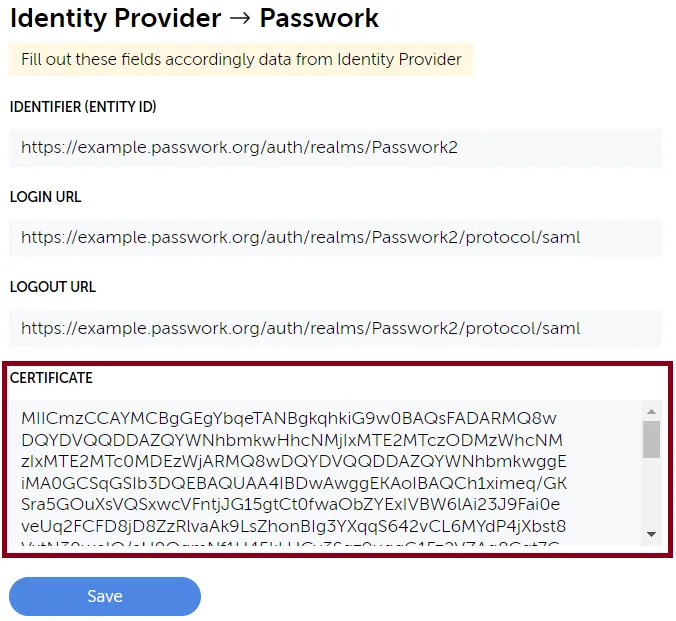
Open the Realm settings, copy the required values, and add them to the SSO configuration interface in Passwork
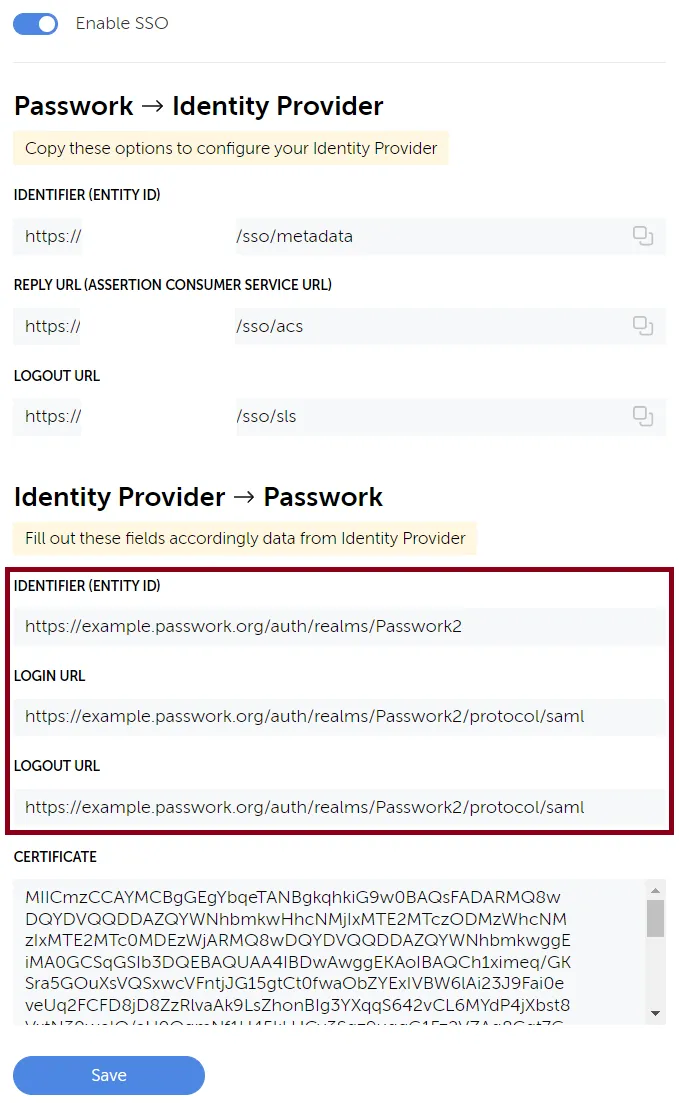
In the Realm settings, go to the Keys tab, click on Certificate, and copy its value into the corresponding field in the SSO settings in Passwork
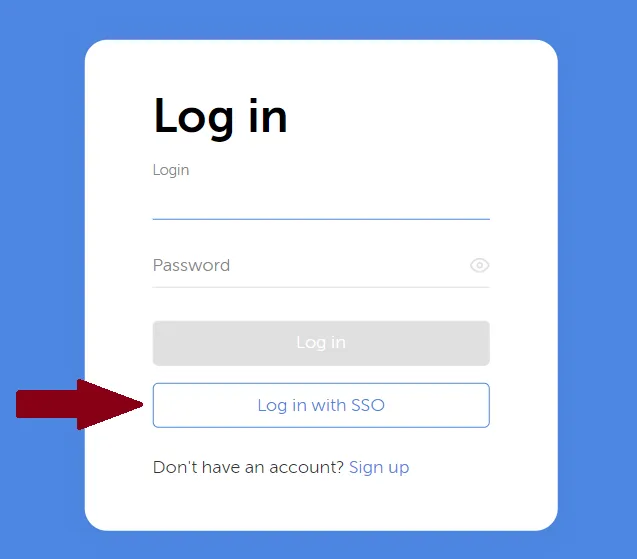
Click the Log in with SSO on the Passwork login page and try to log in to test it
Errors and their descriptions
In case of errors, they will be recorded in the PHP log
1. The response from SSO cannot be correctly decrypted because the certificate fingerprint has been copied incorrectly or is the fingerprint of an incorrect certificate.
OneLogin_Saml2_Error: invalid_response LastErrorReason: Signature validation failed. SAML Response rejected in /var/www/app/modules/Admin/SSO/SsoController.php:78\nStack trace:\n#0 [internal function]: Passwork\\Modules\\Admin\\SSO\\SsoController->acsAction()\n#1 [internal function]: Phalcon\\Dispatcher\\AbstractDispatcher->callActionMethod()\n#2 [internal function]:Phalcon\\Dispatcher\\AbstractDispatcher->dispatch()\n#3 /var/www/public/index.php(91): Phalcon\\Mvc\\Application->handle()\n#4 {main}
2. The current host value in the config.ini parameter domain is specified incorrectly.
OneLogin_Saml2_Error: Invalid array settings: sp_acs_url_invalid, sp_sls_url_invalid in /var/www/app/vendors/php-saml/lib/Saml2/Settings.php:122\nStack trace:\n#0 /var/www/app/vendors/php-saml/lib/Saml2/Auth.php(152): OneLogin_Saml2_Settings->__construct()\n#1 /var/www/app/modules/Admin/SSO/SsoService.php(53): OneLogin_Saml2_Auth->__construct()\n#2 /var/www/app/modules/Admin/SSO/SsoController.php(33): Passwork\\Modules\\Admin\\SSO\\SsoService->getAuth()\n#3 [internal function]: Passwork\\Modules\\Admin\\SSO\\SsoController->loginAction()\n#4 [internal function]: Phalcon\\Dispatcher\\AbstractDispatcher->callActionMethod()\n#5 [internal function]: Phalcon\\Dispatcher\\AbstractDispatcher->dispatch()\n#6 /var/www/public/index.php(91): Phalcon\\Mvc\\Application->handle()\n#7 {main}, referer:
3. The user lacks the attribute required for authentication.
OneLogin_Saml2_Error: invalid_response LastErrorReason: The status code of the Response was not Success,was Responder -> urn:oasis:names:tc:SAML:2.0:status:InvalidNameIDPolicy in /var/www/app/modules/Admin/SSO/SsoController.php:78\nStack trace:\n#0 [internal function]:Passwork\\Modules\\Admin\\SSO\\SsoController->acsAction()\n#1 [internal function]: Phalcon\\Dispatcher\\AbstractDispatcher->callActionMethod()\n#2 [internal function]:Phalcon\\Dispatcher\\AbstractDispatcher->dispatch()\n#3 /var/www/public/index.php(91): Phalcon\\Mvc\\Application->handle()\n#4 {main}