Adding server
Server name and Primary host
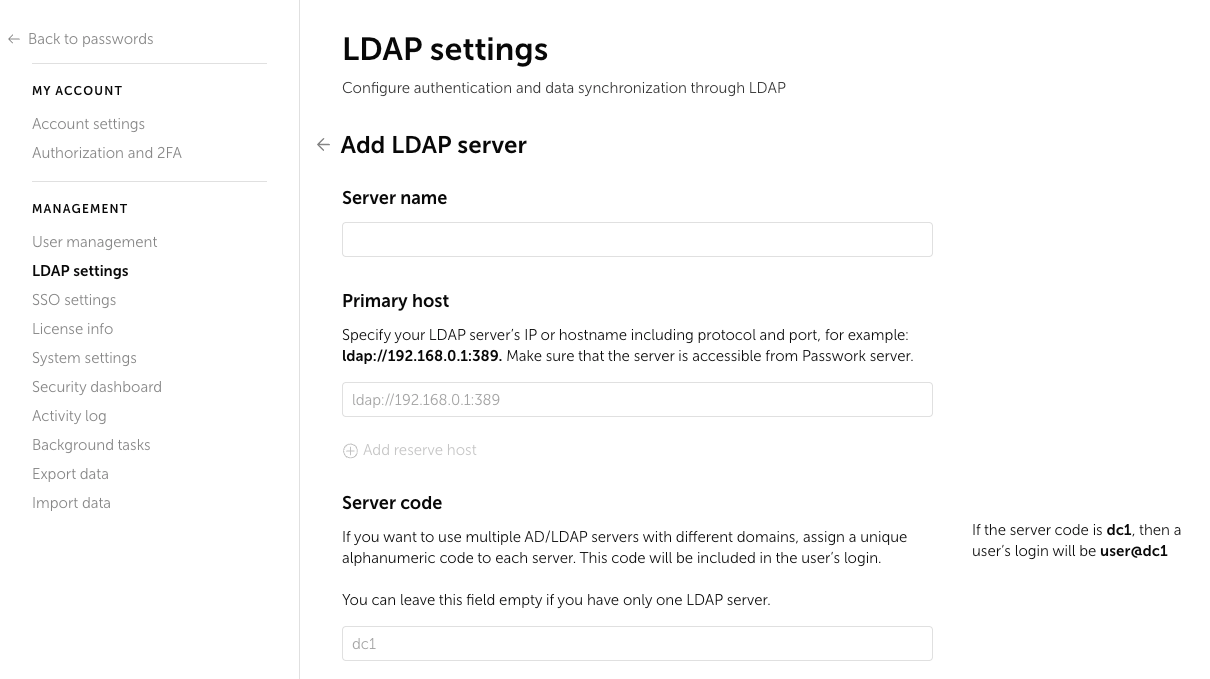
In the Server Name field, enter the name under which the LDAP server will be displayed in Passwork.
In the Primary Host section, specify the address of the LDAP server. You must provide the full address, including protocol and port.
Example:
ldap://192.168.0.1:389
If there is a backup LDAP server, its address can also be specified in Passwork settings. In case the primary LDAP server fails, Passwork will automatically make the backup server primary and direct all DN requests to it until the issues with the primary LDAP server are resolved.
If a secure protocol LDAPS is used, then instead of the IP address, specify the CN (Common Name):
Example:
ldaps://dc01.passwork.local:636
More details about configuring and using LDAPS
Server code
If you need to specify multiple LDAP servers, you must specify a server code for each of them.
Server Code is a unique alphanumeric code that becomes part of the user's login. Passwork reads the server code from the user's login and performs authorization using the LDAP server whose code was specified in the login.
You can leave this field empty if only one LDAP server is used and users without a code will use this server for authorization.
For example, if the server code is dc1, then the user's login in Passwork will be user@dc1. When authorizing in Passwork, the user will enter the login user@dc1, Passwork will extract the server code dc1, find it in the database, and connect to this LDAP server.
If the user enters a login without @, for example, user, Passwork will look for an LDAP server without a code and try to connect to it.
Example:
| Login | Server Code | Login in Passwork |
|---|---|---|
user | none | user |
user | passwork.local | [email protected] |
user | passwork | user@passwork |
Service account
Specify the login and password of the Service Account that has rights to work with users.
Passwork stores this data in encrypted form: the saved password can be changed but cannot be viewed.
The dropdown list allows you to select the attribute name by which the user's login for authorization in Passwork is formed:
- If the LDAP server uses Windows, select samaccountname
- If the LDAP server runs on Linux family OS, select uid
If the LDAP server is configured so that user logins are not stored in the default attribute, you need to specify the attribute name manually.
You can check the correctness of the entered data by clicking Test
Authorization
Passwork allows configuring user authorization using the service account.
Service account
Passwork authorizes using the service account, then searches for the user by login and tries to authorize using the login and password.
Authorization via the service account consists of the following steps:
- On the authorization page, the user enters their credentials, such as username and password.
- The Passwork server uses the service account to find the user with that login in LDAP and obtain their DN.
- The Passwork server sends a bind request to the LDAP server with the found user DN and their password.
- The LDAP server verifies the entered credentials against the data stored in its database.
- If the entered credentials are correct and match the data on the LDAP server, the LDAP server returns confirmation of successful authentication to the Passwork server.
- The Passwork server receives confirmation of successful authentication from the LDAP server and grants the user access to the system.
User attribute mapping
To use LDAP attributes as the user's email and full name in Passwork, specify the names of these attributes.
User email
The default LDAP attribute is mail, example:
mail: [email protected]
If another attribute is used for email in LDAP (for example, userPrincipalName), it must be specified.
User full name
The full name can be stored in different attributes depending on LDAP server settings:
displaynamenmcncommonnamename
Example:
displayName: Ivan Petrov
If LDAP does not use displayName, you can specify another suitable attribute from the list or a custom one.
User groups
The memberOf attribute contains a list of groups the user belongs to. This is a key element for:
- Access control based on groups;
- Assigning Groups during mapping;
- Restricting login to Passwork by groups.
Example:
memberOf: CN=Admins,OU=Groups,DC=example,DC=com
memberOf: CN=IT,OU=Departments,DC=example,DC=com
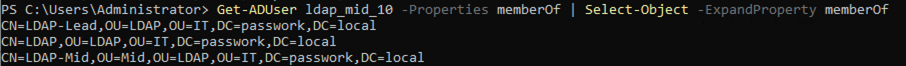
In most configurations, the memberOf parameter is suitable by default. Changing this value is required only if the LDAP schema uses a different attribute. Before changing, it is recommended to ensure the presence of such an attribute and its correct operation.

