Wearable technology has become increasingly popular in recent years, with devices like the Apple Watch, Fitbit, and Xiaomi gaining significant market share. These devices offer a wide range of features, from tracking fitness goals to monitoring health data and staying connected with the digital world. However, with the rise of wearable tech, concerns have been raised about how secure these devices are and whether they put user data at risk.
Challenges
The types of data that wearable tech collects vary from device to device. Some devices, such as fitness trackers, collect basic health data such as heart rate and activity level. Other devices, such as smartwatches, can collect more sensitive data such as location, messages, and emails. This data is typically stored on the device and synced to the cloud, making it accessible from any device that the user is logged into.
One of the most significant concerns with wearable tech is the security of this data. If the device or cloud storage is not properly secured, the data could be accessed by hackers who could use it for malicious purposes. For example, hackers could use location data to track users' movements or steal their identity by accessing their personal information.
To protect user data, most wearable tech companies implement security measures. For example, the Apple Watch uses encryption to protect data stored on the device, and it requires a passcode or biometric authentication to access the device. Similarly, Fitbit and Xiaomi use encryption to protect user data and offer security features such as two-factor authentication.
Despite these measures, data breaches in wearable tech have unfortunately become more common in recent years, highlighting the need for continued vigilance when it comes to security measures. For example, in 2017, researchers discovered a vulnerability in the Bluetooth communication protocol used by many wearable devices. This vulnerability, known as BlueBorne, allowed hackers to take control of devices and steal sensitive data.
In 2019, it was discovered that several popular fitness apps had inadvertently exposed sensitive user data. The apps, which were used in conjunction with wearable fitness trackers, had failed to properly secure user data, leaving information like usernames, passwords, and exercise routines vulnerable to attack.
Another example of a wearable tech data breach occurred in 2018 when hackers stole sensitive data from the Polar fitness app. The data, which included location data, was collected by the app's users and stored on Polar's servers. However, the servers were not properly secured, allowing hackers to access the data and track the movements of military personnel and intelligence agents in sensitive locations.
How to protect your data and privacy?
To protect your data and privacy when using wearable tech, there are several steps you can take. Firstly, always use strong, unique passwords for your wearable tech accounts, and consider using a password manager to help generate and manage these passwords.
Secondly, ensure that your device's software is always up-to-date with the latest security patches and updates. This will help to protect against known vulnerabilities and ensure that any new security features are in place.
Thirdly, be aware of the data that your wearable tech is collecting and where it is being stored. Check the privacy policy of your device and app to understand how your data is being used and shared. If you are concerned about your privacy, consider disabling certain features or opting out of data sharing.
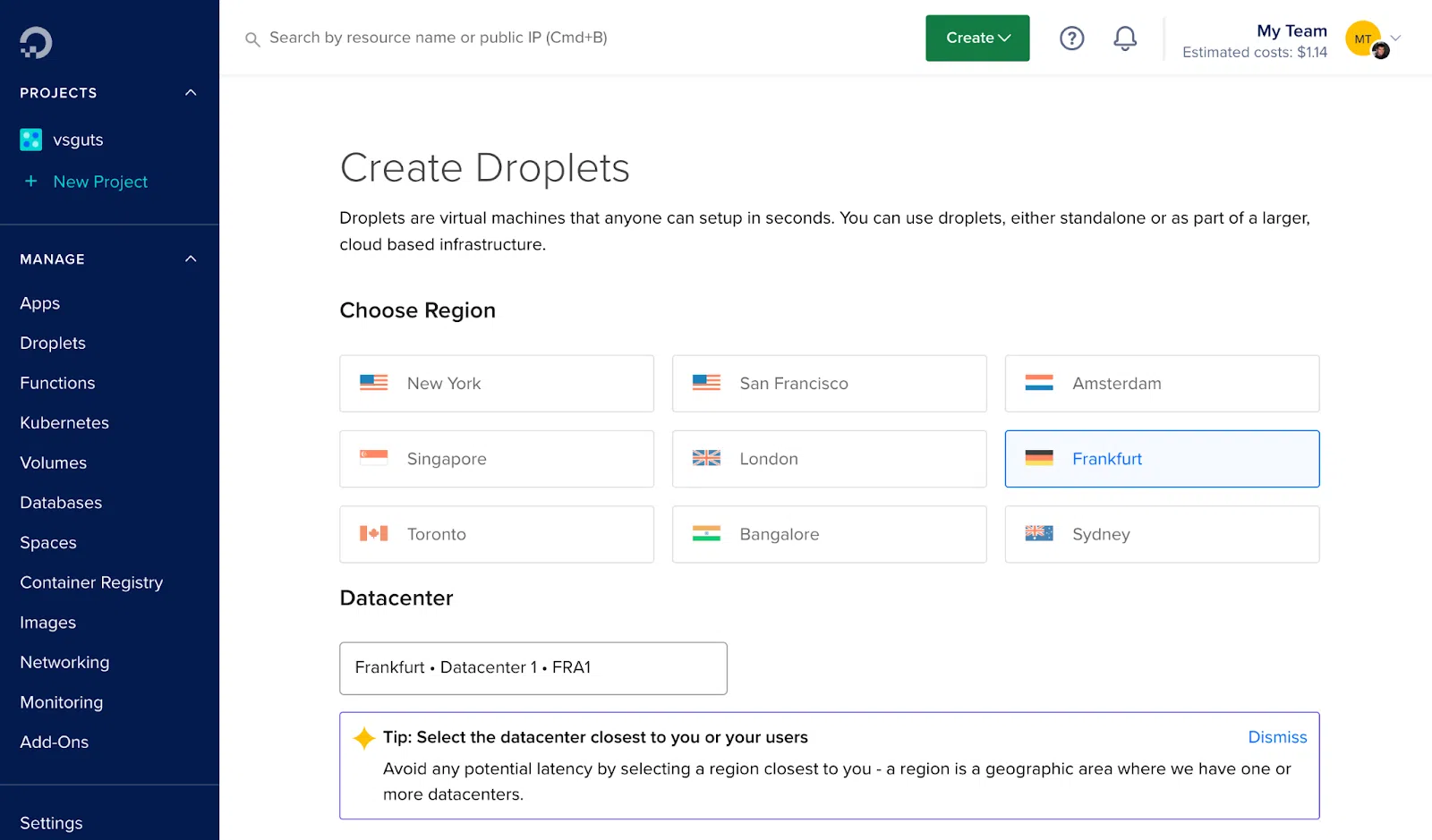
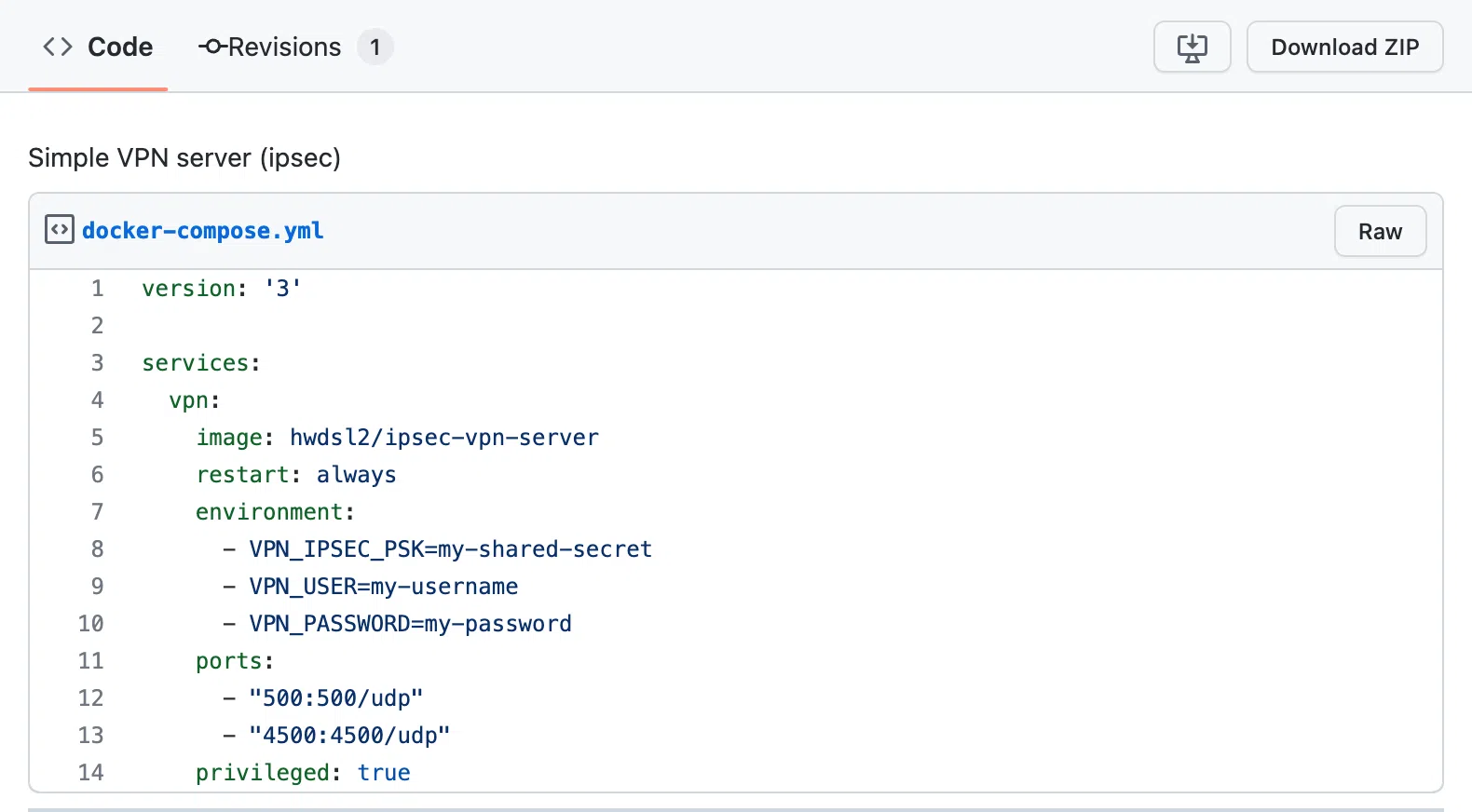
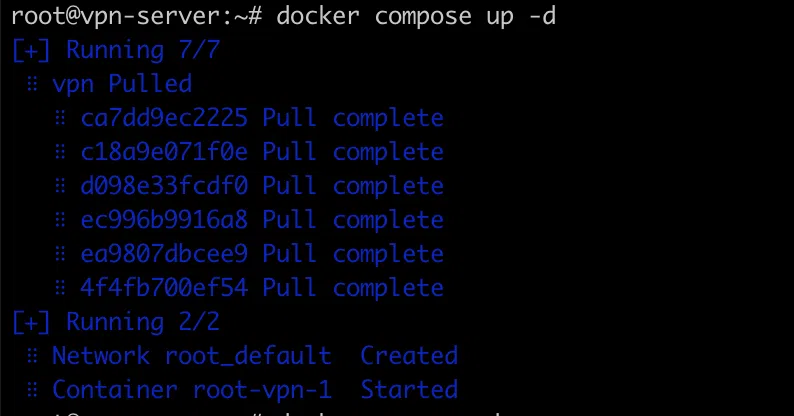
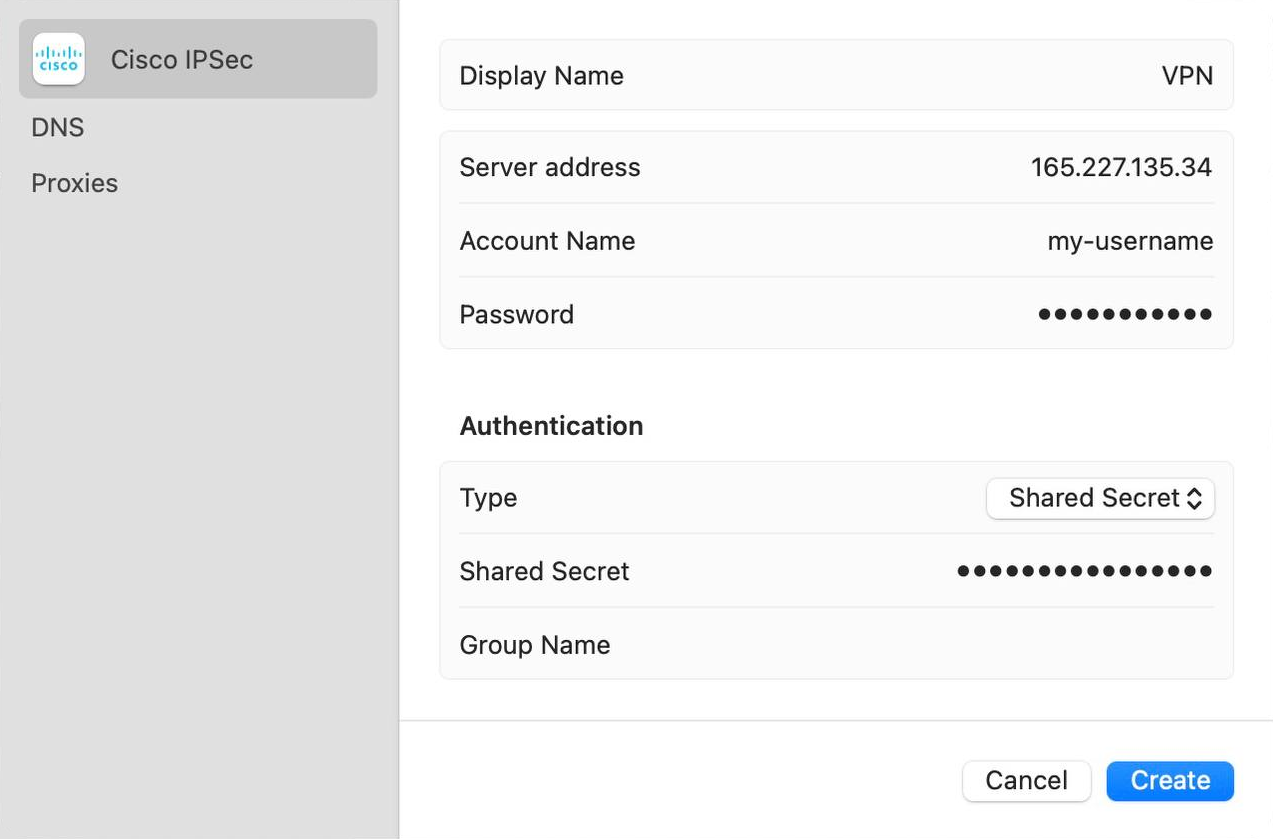
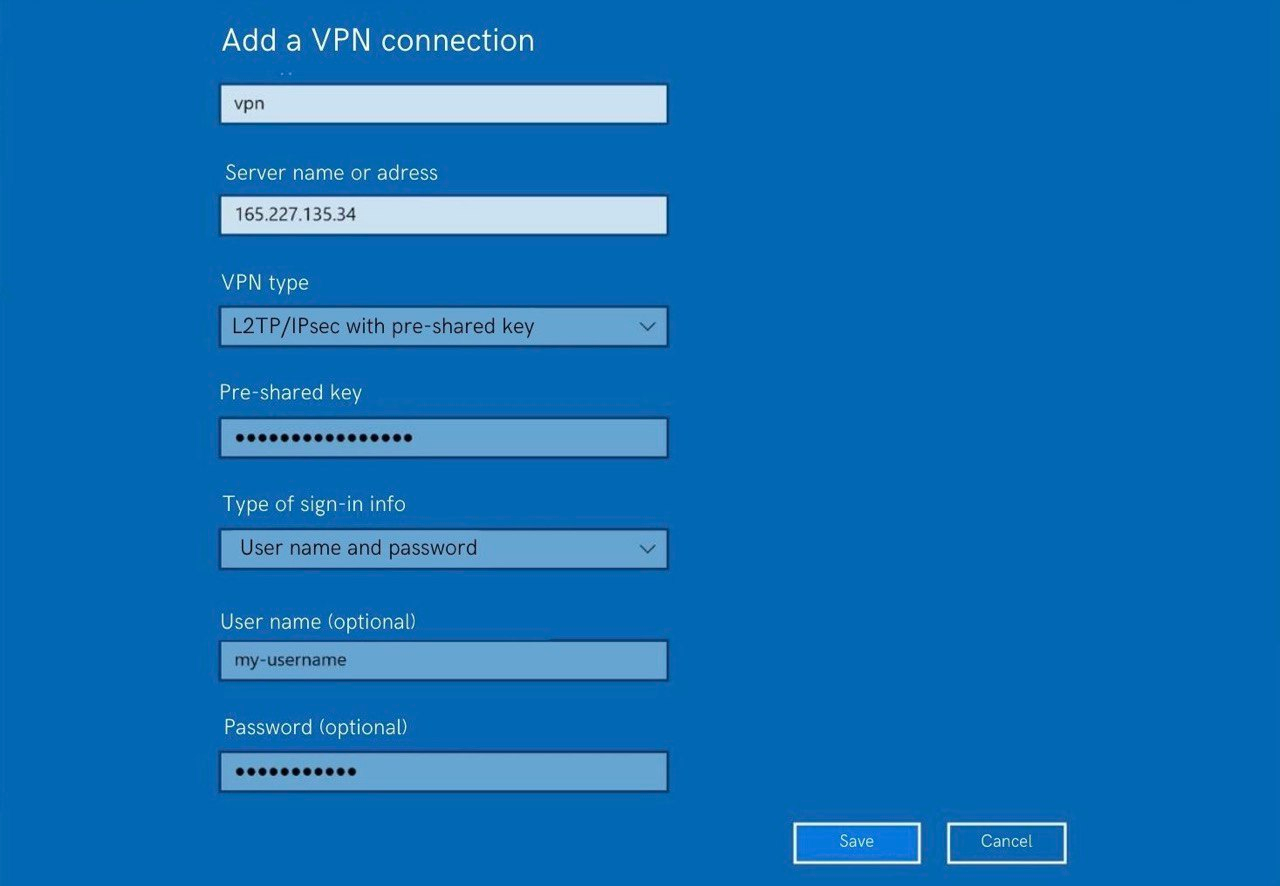
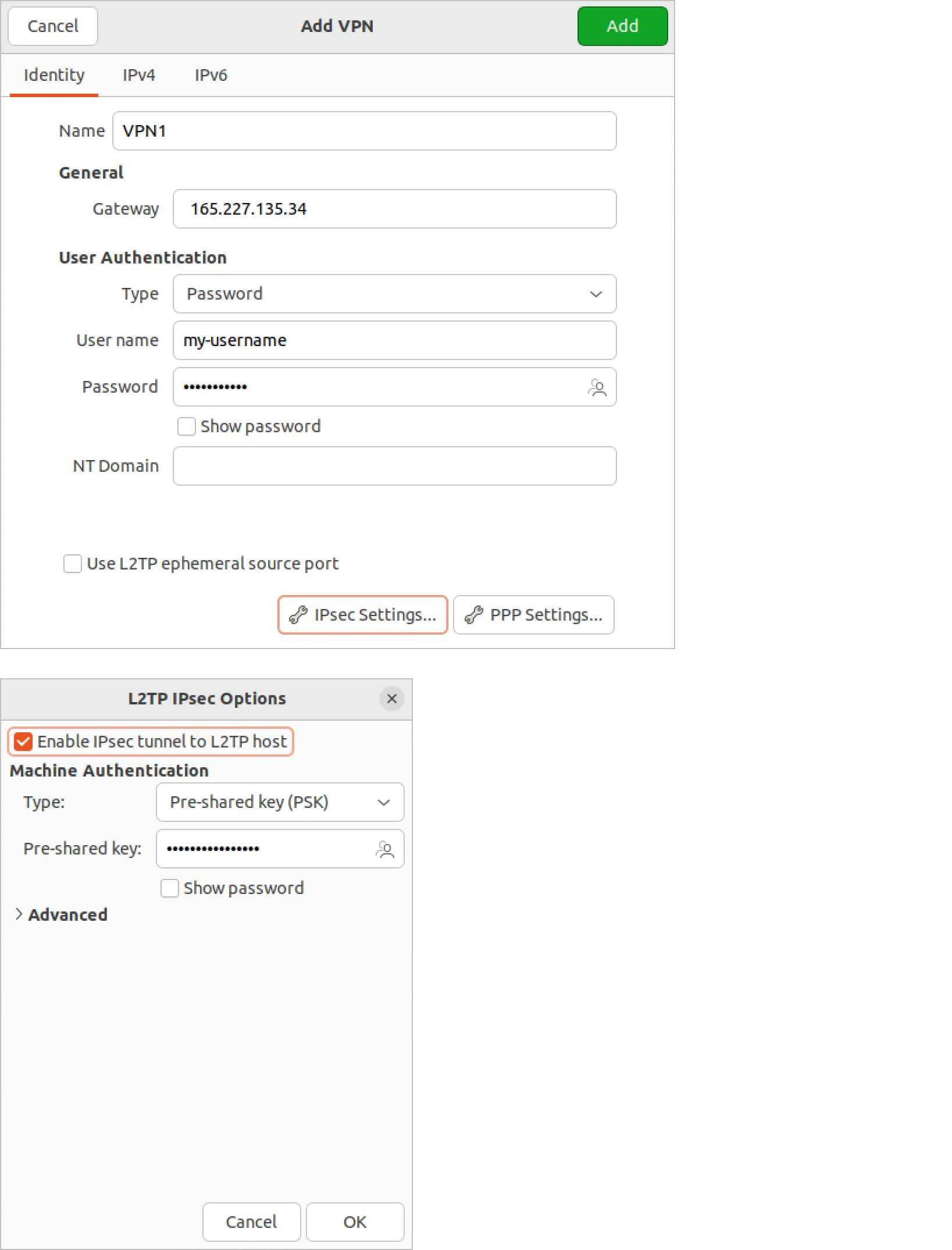
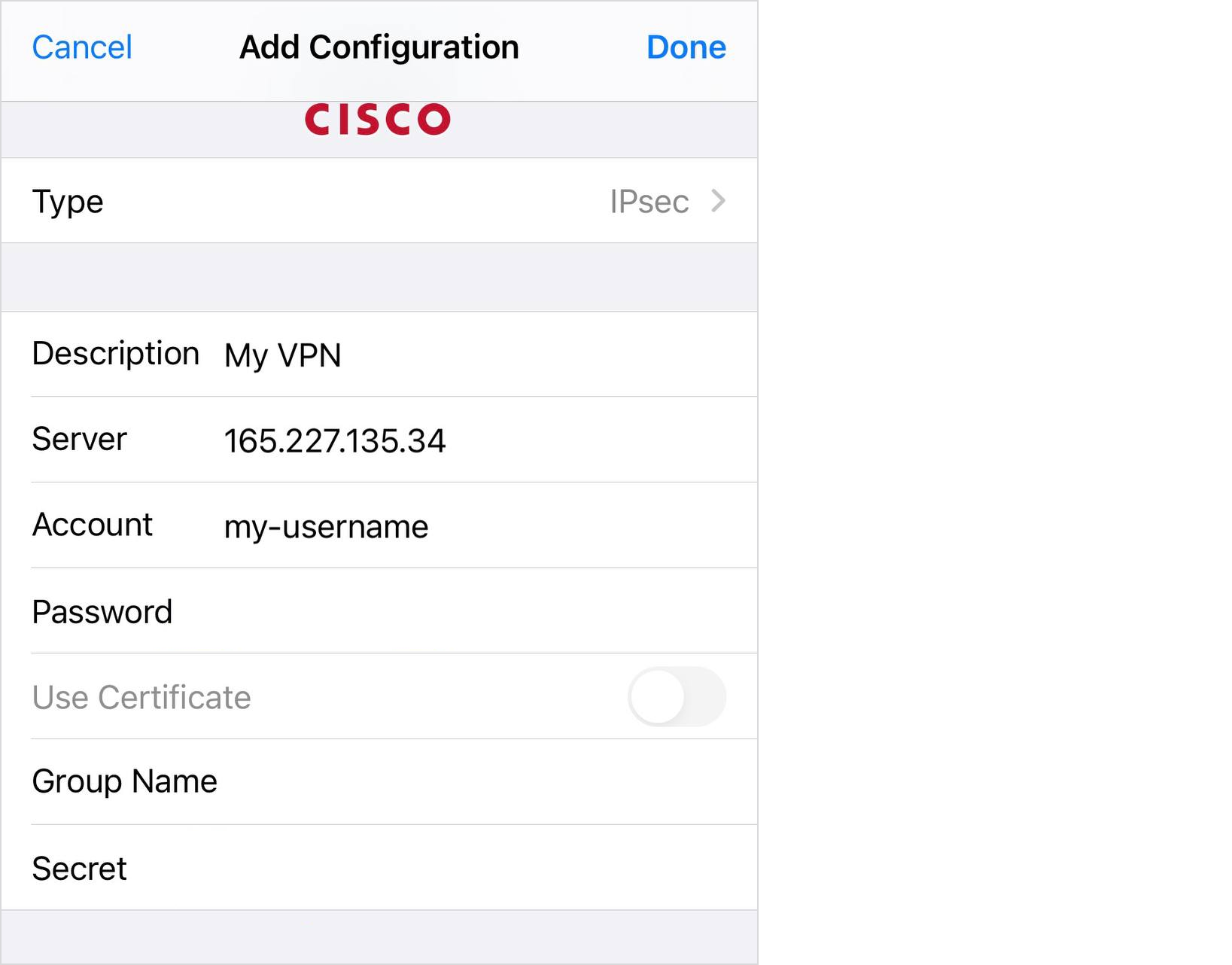
Then, consider using a VPN (Virtual Private Network) to protect your online activities when using wearable tech. A VPN encrypts your internet connection, making it more difficult for hackers to intercept your data. VPNs are particularly useful when using public Wi-Fi, which is often unsecured and vulnerable to hacking.
Lastly, it's essential to know how to identify potential threats and scams that may target wearable tech users. This can include phishing emails or fake apps that may trick users into disclosing their personal information or installing malware on their devices.
Wearable tech in the workplace
Another important consideration when it comes to wearable tech security is the role of wearable tech in the workplace. Wearable tech is increasingly being used in workplace environments, where it can offer benefits like tracking employee productivity and health. However, it is essential to ensure that wearable tech devices used in the workplace are properly secured and that sensitive workplace data is not put at risk.
Organizations can take several steps to protect workplace data when using wearable tech.
Firstly, companies should develop a clear policy on the use of wearable tech in the workplace, outlining the acceptable use of these devices and the security measures that should be in place.
Secondly, companies should invest in secure wearable tech devices that offer robust security features, such as encryption and two-factor authentication. This will help to protect sensitive workplace data from unauthorized access and reduce the risk of data breaches.
Thirdly, organizations should provide training for employees on how to use wearable tech devices securely. This could include information on the importance of using strong passwords, keeping devices up-to-date with the latest security patches and updates, and being aware of potential security threats.
Finally, companies should implement monitoring and control measures to ensure that wearable tech devices used in the workplace are being used appropriately and that sensitive data is not being put at risk.
Conclusion
Overall, wearable tech devices offer many benefits for both individuals and organizations, but it is essential to take steps to protect data and privacy. By following the best practices outlined above, individuals and companies can minimize the risks associated with using wearable tech devices and enjoy the many benefits that these innovative devices offer.