Most of us have heard of torrents, and have likely also used torrents to download movies, books, music, TV shows, games, and so on. But, you’ve probably still got one question that remains unanswered — what are they? BitTorrent is well-known as a technology for piracy, although its genius isn’t limited to that. It's a useful, decentralized peer-to-peer protocol that outperforms other protocols in many different ways.
In this article, we’ll break it down to be as simple as possible while also explaining several terms that might pass you by every day.
Why do I need BitTorrent?
When you download data from the internet, most of the time, your computer connects to the webserver and immediately downloads the data from a certain server. This is how the cohort of online traffic operates. Even though we have fancy technologies to reroute this traffic through many different servers, there’s still a bottleneck in terms of the maximum speed that may be provided to the end-user. But what if you know someone who already has the file that you need, wouldn’t it be better to AirDrop it, instead of uploading it to a server, and then downloading it once again? Well, that’s what Bram Cohen created his BitTorrent protocol for.
How does BitTorrent work?
BitTorrent is effectively a peer-to-peer protocol, which means that computers in a BitTorrent ‘swarm’ (a collection of computers downloading and uploading the same torrent) exchange data without the use of a central server.
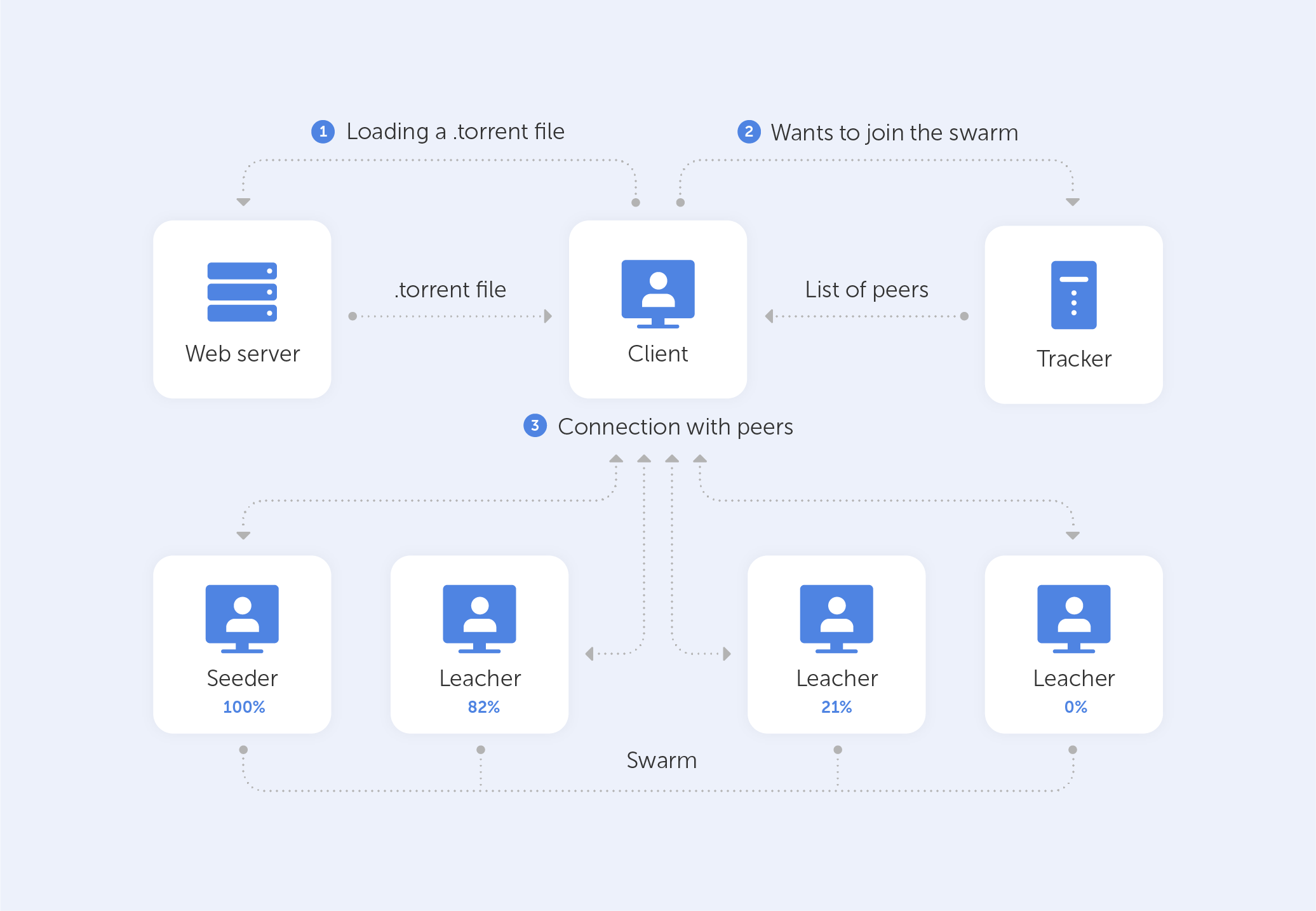
A machine traditionally joins a BitTorrent swarm by loading a .torrent file onto a BitTorrent client. The BitTorrent client communicates with a ‘tracker’ defined in the .torrent file. The tracker is a dedicated server that keeps track of the computers that are linked to it. The tracker exchanges IP addresses with other BitTorrent clients in the swarm, allowing them to communicate with one another. That’s exactly why it is called a ‘tracker’ — it tracks the participants of any given communicative endeavour.
Once connected, a BitTorrent client downloads tiny chunks of the torrent's contents, in fact, as much as it can. As soon as the BitTorrent’s client has any data downloaded, it may start uploading it to other BitTorrent clients in the swarm. As a result, everyone who downloads a torrent is also uploading the same torrent — all the pieces that a user has at the moment. This increases the download speed for everyone. When 10,000 users download the same file, the central server is not overburdened. Instead, each downloader shares their upload capacity with other downloaders, ensuring that the torrent remains as fast as possible.
Importantly, BitTorrent clients never download files directly from the tracker. The tracker simply participates in the torrent by keeping track of the BitTorrent clients that are connected to the swarm, not by downloading or uploading data.
‘Seeds’, ‘Peers’, and ‘Leeches’
If you're a torrent user, you've probably come across the words ‘seeds’, ‘peers’, and ‘leeches’. Let's take a look at what these terms actually mean.
The seed is the user who has already downloaded the entire file and is now sharing it with peers while not downloading any parts of the file from others. To download a torrent, one seeder – who has a full copy of all the files in the torrent — must first join the swarm so that other users may download the data. If a torrent has no seeders, it cannot be downloaded since no connected user possesses the entire file.
Leechers or peers are people who are simultaneously downloading and uploading — so, the vast majority, basically. In the BitTorrent world, people who give more — get more. In other words, the BitTorrent client prefers to send data to clients who contribute more upload bandwidth rather than sending data to clients who upload at a very slow speed.
This improves download rates for the whole swarm and compensates those who donate more upload bandwidth.
Moreover, we bet you encountered times when the file you wished to download via the torrent network wasn’t very popular, resulting in low speeds, or no download at all. This could have resulted, for example, because all the seed users were offline. It’s good to know that our ability, as highly-evolved primates, to create new technologies is limitless. Indeed, as a result, we did manage to mitigate the aforementioned, to an extent.
Magnet links
Apart from the .torrent file, you might be familiar with something called ‘magnet links’.
A magnet link includes a unique identifier, different data based on the torrent's exact nature, and, most significantly, a cryptographic hash of the torrent’s contents. And that’s really cool because you can search for different torrents that lead to the same file. Now, a magnet link uses that identifier to ‘attract’ all torrents that can help download those files, meaning more seeders, meaning more peers, meaning greater speeds and stability! All this fancy technology is done by what is called the DHT protocol, and according to its specification, "each peer effectively becomes a tracker." This implies that BitTorrent’s clients no longer require a centralized server to manage a swarm. Rather, BitTorrent evolves into a completely decentralized peer-to-peer file-sharing system.
Does this have applications outside of PirateBay?
Of course. Here are just some examples:
- To deliver updates for games, including World of Warcraft, StarCraft II, and Diablo 3, Blizzard uses a special BitTorrent client. This enhances everyone's downloads by allowing users to share their upload bandwidth with others, utilizing idle bandwidth ensuring quicker downloads for everyone;
- Wikileaks released files using BitTorrent, which relieved the tremendous strain on their systems;
- BitTorrent is used by Linux distributions to help disseminate ISO disc images.
Is it safe?
A big problem is that virus-ridden pirated content makes up a concerning chunk of all available torrents nowadays; that’s a huge threat to your security for obvious reasons. However, the biggest problem with torrents is that all BitTorrent users may see the ISP addresses of all users as well as the data they send. And of course, copyright holders, the police, advertising organizations, and hackers frequently monitor this data. Because of this, it’s critical for torrent users to maintain total online security by utilizing internet security software and installing operating system updates as soon as they become available. Encrypting an internet connection and masking the IP address with a virtual private network (VPN) also helps, but not to a full extent. So the short answer is — it’s not very safe.
In the end, downloading via BitTorrent is worth it, most of the time, especially when it comes to big files. While lacking in security, BitTorrent is the Web2 version of Web3 that we’re all allowed to try right now, as long as it doesn’t infringe on copyright laws.