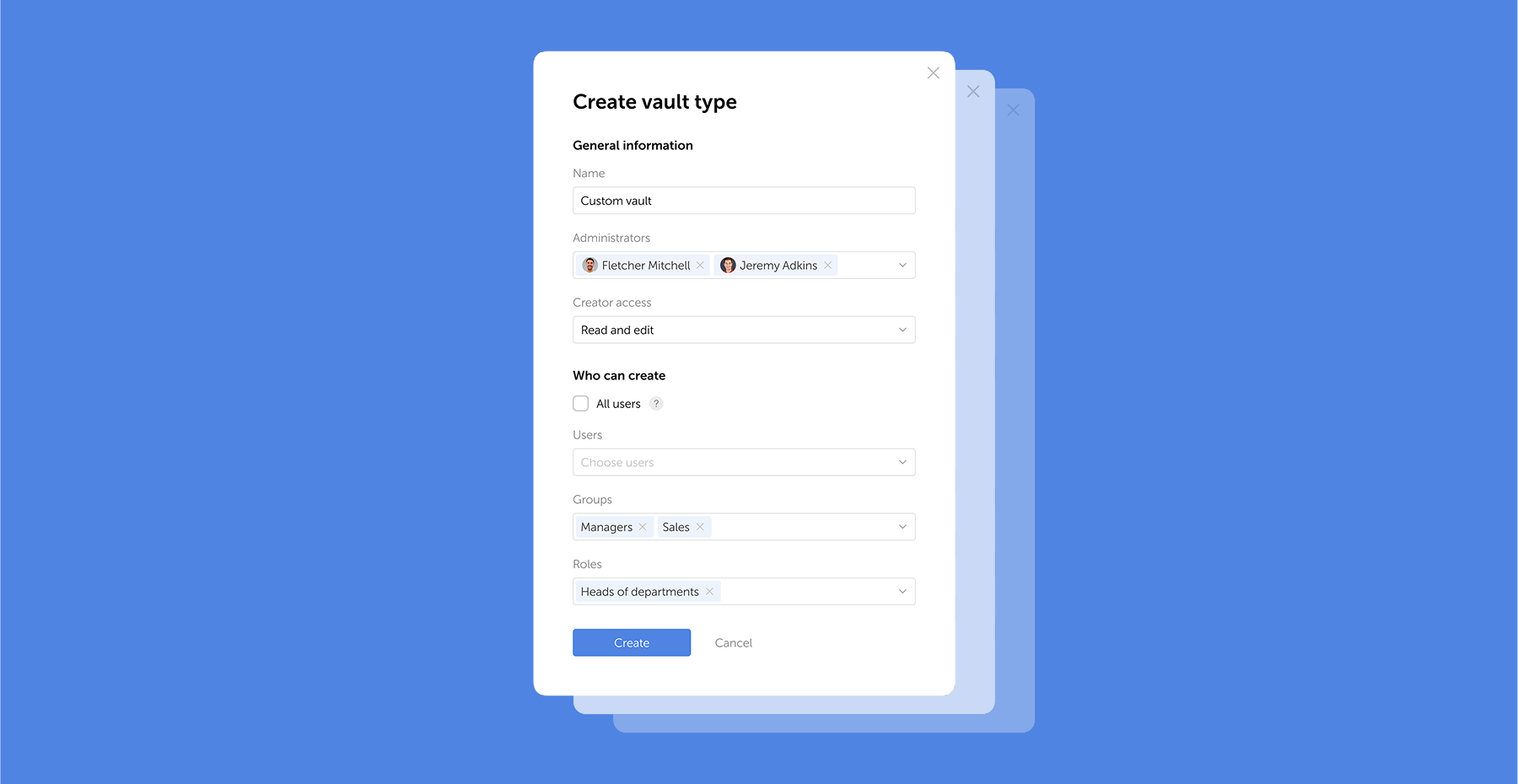
DevOps pipelines run on secrets — API keys, tokens, and certificates move through automated CI/CD workflows at high velocity without human oversight. Securing this machine-to-machine access requires a dedicated secrets management strategy built for automation. As infrastructure scales, protecting these credentials becomes essential for continuous, secure delivery.
According to Verizon’s 2025 DBIR, credential abuse accounts for 22% of initial access vectors, and stolen credentials are involved in 88% of basic web application attacks. IBM’s 2025 report puts the global average breach cost at $4.44M with a 241-day lifecycle. For breaches caused by compromised credentials, the average is $4.67M and 246 days.
Key takeaways:
- Secrets encompass API keys, OAuth tokens, Secure Shell keys, and certificates
- Centralized storage with automated rotation prevents theft
- Regulatory compliance, like GDPR, PCI-DSS, and HIPAA, requires proper management
Unlike traditional password tools, DevOps secrets management focuses on machine authentication at scale. It secures credentials in encrypted vaults, injects them into authorized services, rotates them automatically, and maintains audit logs to ensure compliance.
The risks of poor secrets management
In 2024, GitHub's security scans uncovered 39 million exposed secrets across public repositories. Developers had embedded credentials directly in code, a practice that persists because Git preserves complete history. Even "deleted" secrets remain accessible. The problem compounds through secret sprawl.
Critical risks:
- Repository history preserves hardcoded secrets indefinitely
- Scattered secrets eliminate usage visibility
- Extended credential lifespans widen attack windows
- Compliance gaps trigger compliance violations
Common challenges in DevOps secrets management
In dynamic DevOps environments, secrets frequently move across automated systems, creating challenges:
- Secret sprawl. Credentials end up in repositories, config files, environment variables, and notes, making tracking difficult.
- Credential rotation. Regularly updating secrets is essential, but it often leads to deployment failures when overlooked.
- Multi-cloud complexity. Each cloud provider uses unique tools and access controls, leading to fragmented and risky duplication of secrets.
Security measures can slow deployments, pushing developers to hardcode credentials to save time. Solutions like Jenkins, GitHub Actions, and GitLab CI address this by injecting secrets at runtime, ensuring they exist only during deployment. Automated retrieval eliminates delays while maintaining security.
Hybrid and multi-cloud setups scatter secrets across various platforms, each with different access controls. For example, database passwords may reside on one cloud, API keys on another, and certificates on-premise. Without consistent access management, integration becomes complex and error-prone.
Real-world examples of secret exposure incidents
A 2024 U.S. Treasury breach traced to leaked API keys let attackers bypass security. CVE-2025-30066 showed compromised GitHub Actions leaking credentials into logs. Notable incidents affected major enterprises, many involving OAuth tokens.
96% of exposed GitHub tokens had write permissions, meaning attackers could potentially modify repositories rather than only read data. Cloud account compromises originate from exposed credentials: attackers scan GitHub, GitLab, and Bitbucket for API keys granting cloud access.
These data breaches share common patterns: credentials stored where they shouldn't be and valid longer than necessary. Prevention requires centralized storage and automated rotation working together.
DevOps secrets management best practices
Centralized management forms the foundation of secure DevOps environments. Store all credentials in dedicated vaults with AES-256 at-rest encryption. Set up automated rotation policies to expire and replace credentials on schedule, maintaining complete audit logs for compliance. In line with industry standards, OWASP guidance emphasizes standardizing approaches.
Core practices:
- Centralize secrets in dedicated vaults
- Encrypt using AES-256 or stronger
- Automate rotation policies
- Apply zero trust and least privilege
- Maintain complete audit logs
To effectively implement zero-trust and least-privilege principles, organizations should shrink their attack surface by verifying every access request and restricting permissions to role requirements through Role-based access control (RBAC). Identity management systems like Active Directory (AD) or LDAP can enforce these policies, supplemented with multi-factor authentication (MFA) and just-in-time, single-use credentials.
Hardcoded secrets should not be present in the codebase; instead, environment variables or direct vault integrations should be used for runtime access. To prevent credentials from entering repository history, organizations can implement pre-commit hooks with tools like Gitleaks or Talisman. Proper .gitignore configuration is also essential to exclude sensitive files.
Finding and removing hardcoded secrets:
- Scan Git repositories with automated detection tools
- Implement pre-commit hooks blocking secrets before commits
- Use environment variables for runtime credential access
- Rotate discovered passwords and credentials immediately
- Educate developers on secure handling practices
Handling secrets in code repositories
Before Git commits are complete, pre-commit hooks scan for exposed credentials. For continuous monitoring, GitHub, GitLab, and Bitbucket provide native detection that alerts when credentials appear. GitGuardian monitors repositories continuously and catches secrets that bypass initial checks.
In the .gitignore configuration, exclude files containing secrets. Developer education matters equally: private repositories provide insufficient protection — anyone with access can read them.
Pre-commit hook configuration for Gitleaks
#!/bin/bash
# Save as .git/hooks/pre-commit
gitleaks protect --staged --verbose
if [ $? -ne 0 ]; then
echo "! Gitleaks detected secrets"
echo "Remove secrets and retry"
exit 1
fi
Best secrets management tools for DevOps 2026
For teams using a single cloud, native tools simplify operations. For example, AWS Secrets Manager automates credential rotation and integrates with access controls. Setup is quick, taking hours instead of weeks. However, this convenience comes with the downside of being locked into one provider.
In multi-cloud environments, managing secrets becomes fragmented. Credentials for Amazon, Microsoft, and Google services are stored in separate vaults, requiring different integration codes for each platform. Tools like HashiCorp Vault solve this by supporting multiple clouds, but they require specialized expertise to manage.
When managing both employee passwords and application secrets, organizations often use separate tools. This duplication increases costs and complexity, and Passwork handles both.
Developers should also configure .gitignore to exclude files with sensitive data and understand that private repositories alone don’t guarantee security — anyone with access can view their contents.
Open-source vs. commercial solutions
Some secrets management platforms offer both open-source and enterprise versions. Open-source solutions attract teams with transparent code, community support, and no licensing costs. In contrast, enterprise platforms provide dedicated support, compliance certifications, and advanced monitoring.
SaaS deployment removes the need for infrastructure management but adds third-party dependencies. Total costs include not just licensing fees, but also operational expenses.
5 criteria that actually matter when choosing a tool
Start with documented requirements. How many secrets need management, hundreds or thousands?
Evaluation criteria:
- Integration with existing CI/CD tools
- Scalability supporting growth
- Compliance certifications matching requirements
- Deployment flexibility balancing control and operations
- Total cost, including infrastructure and staff time
Managing passwords and DevOps secrets in a single system reduces overhead and improves cost efficiency. Unified role-based access controls simplify administration and mirror your organizational structure.
On-premise deployment keeps all credentials securely within your infrastructure — giving you complete control over sensitive data. The solution integrates seamlessly with Active Directory, LDAP, and SSO protocols.
How to automate secrets management in DevOps
Automation replaces manual updates with scheduled credential rotation. CI/CD pipelines, such as Jenkins, GitHub Actions, and GitLab CI, connect directly to secret platforms via APIs for runtime delivery.
The standard integration flow is secure: runners authenticate with short-lived tokens, retrieve secrets, and inject them as environment variables. Credentials never persist in pipeline definitions or logs.
image: passwork-cli:latest
pipelines:
default:
- step:
name: Deploy with secured credentials
script:
# Get database credentials from Passwork and run database migrations
- passwork-cli exec --password-id "db_credentials" \
python manage.py migrate
# Get API keys from Passwork and run deployment script
- passwork-cli exec --password-id "api_keys,deploy_keys" \
./scripts/deploy.sh
# Notify the team with a direct API call
- passwork-cli api --method POST \
--endpoint "v1/inbox/messages" \
--params '{"recipient":"devops","message":"Deployment completed successfully"}'
services:
- docker
definitions:
services:
docker:
memory: 2048
Regular replacement of secrets reduces exposure windows. Modern secrets platforms generate dynamic credentials on demand through configurable time-to-live (TTL) values. Cloud-native tools automate rotation for their respective services. Different assets require distinct rotation strategies — API keys rotate differently than TLS/SSL certificates or database passwords.
Graceful refresh mechanisms allow applications to retrieve updated credentials without restarts. When requests arrive, vaults create unique credentials valid for that specific session. After disconnection, automatic revocation follows.
Upon compromise detection, revocation processes activate immediately. Rotation should occur when compromise is detected or suspected, or during security incidents.
Building a secrets management strategy
Successful implementation requires strategic planning beyond tool selection. Strategy covers organizational change management, phased rollout, and success metrics.
Organizations must gain stakeholder buy-in from development, security, and infrastructure teams. Phased implementation starts with non-production environments, proves the approach, then expands.
Implementation phases:
- Assessment. Inventory existing secrets, identify security gaps, and document current workflows.
- Planning. Select tools, define policies, establish rotation schedules, and configure access controls.
- Pilot. Deploy to non-production environments, train teams, and refine processes.
- Rollout. Expand to production systems gradually, migrate existing secrets, and monitor adoption.
- Optimization. Tune policies, automate workflows, and measure success metrics.
What a secrets policy must cover
Formal security policies document secrets management requirements and establish governance. Policies should define what constitutes a secret, specify approved storage locations, establish rotation schedules, and outline incident response procedures.
Compliance requirements from GDPR, PCI-DSS, HIPAA, ISO 27001, and SOC 2 mandate specific controls: audit logging, encryption standards, and access restrictions. Involve security, development, and operations teams to craft the proper strategy.
Training and adoption
Technology alone can't secure credentials. Special training for teams should cover the risks of hard-coded credentials, proper tool use, and secure practices. DevSecOps culture integrates security naturally into workflows.
Monitoring and auditing secret usage
For anomaly detection and compliance demonstration, visibility into secret access becomes critical. In every audit entry, details should include who accessed which secrets, when, from which systems, and whether access succeeded.
These logs flow into security analytics platforms. Through Splunk and ELK Stack, teams analyze access patterns. Cloud-native tools integrate with their respective provider monitoring services.
From all sources, SIEM systems aggregate logs, then apply rules and machine learning to detect anomalies.
How to catch credential misuse before it becomes a breach
Between sensitivity and alert fatigue, security alerting finds balance. Through SIEM platforms, rules catch suspicious activities: access from unusual locations, high-value secret retrieval outside business hours, and multiple failed authentications. For baseline deviations, anomaly detection identifies patterns.
With Prometheus, Datadog, and PagerDuty integration, alerts reach teams immediately. Through our advanced admin tools, granular monitoring comes with customizable alerts and compliance reporting built in.
Frequently Asked Questions

What is DevOps secrets management, and why is it important?
DevOps secrets management securely stores, distributes, rotates, and audits credentials like API keys and tokens. Proper management prevents unauthorized access and maintains GDPR and PCI-DSS compliance.
What are the best practices for managing DevOps secrets and credentials?
Core practices include centralizing secrets in vaults, implementing automated rotation, applying zero trust and least privilege, eliminating hardcoded credentials, and maintaining audit logs.
How do you securely manage secrets in your CI/CD pipeline?
Integrate secrets management tools with Jenkins, GitHub Actions, and GitLab CI. Inject secrets at runtime as environment variables. Authenticate pipeline runners using short-lived tokens.
What tools are recommended for DevOps secrets management in 2026?
Cloud-native tools suit single-cloud environments but create vendor lock-in. Cross-platform solutions offer multi-cloud support but require operational expertise. Passwork combines password and secrets management with on-premise deployment and unified credential management.
How do you implement a centralized vault for DevOps secrets?
Select a platform based on integration needs, compliance requirements, and deployment preferences. Configure role-based access controls, establish rotation policies, and implement audit logging.
What are the security risks of improper secrets management?
GitHub detected 39 million leaked secrets in 2024. Risks include data breaches, compliance violations, and secret sprawl.
How do you avoid hardcoding secrets in your applications and infrastructure?
Store secrets in vaults and inject at runtime through environment variables. Use detection tools for continuous monitoring.
How should secrets be managed across multi-cloud environments?
Adopt unified platforms that work consistently across all cloud providers. We provide on-premise and cloud deployment flexibility, letting teams control sensitive secrets.
How do you rotate secrets regularly without disrupting services?
Implement automated rotation through platforms that support graceful updates. Applications need refresh mechanisms to retrieve updated credentials without restarts.
How to manage DevOps secrets and credentials in 2026
DevOps secrets management best practices for 2026: secure API keys, tokens, and certificates in CI/CD pipelines. Explore top tools, automation strategies, and how Passwork helps protect secrets at scale.

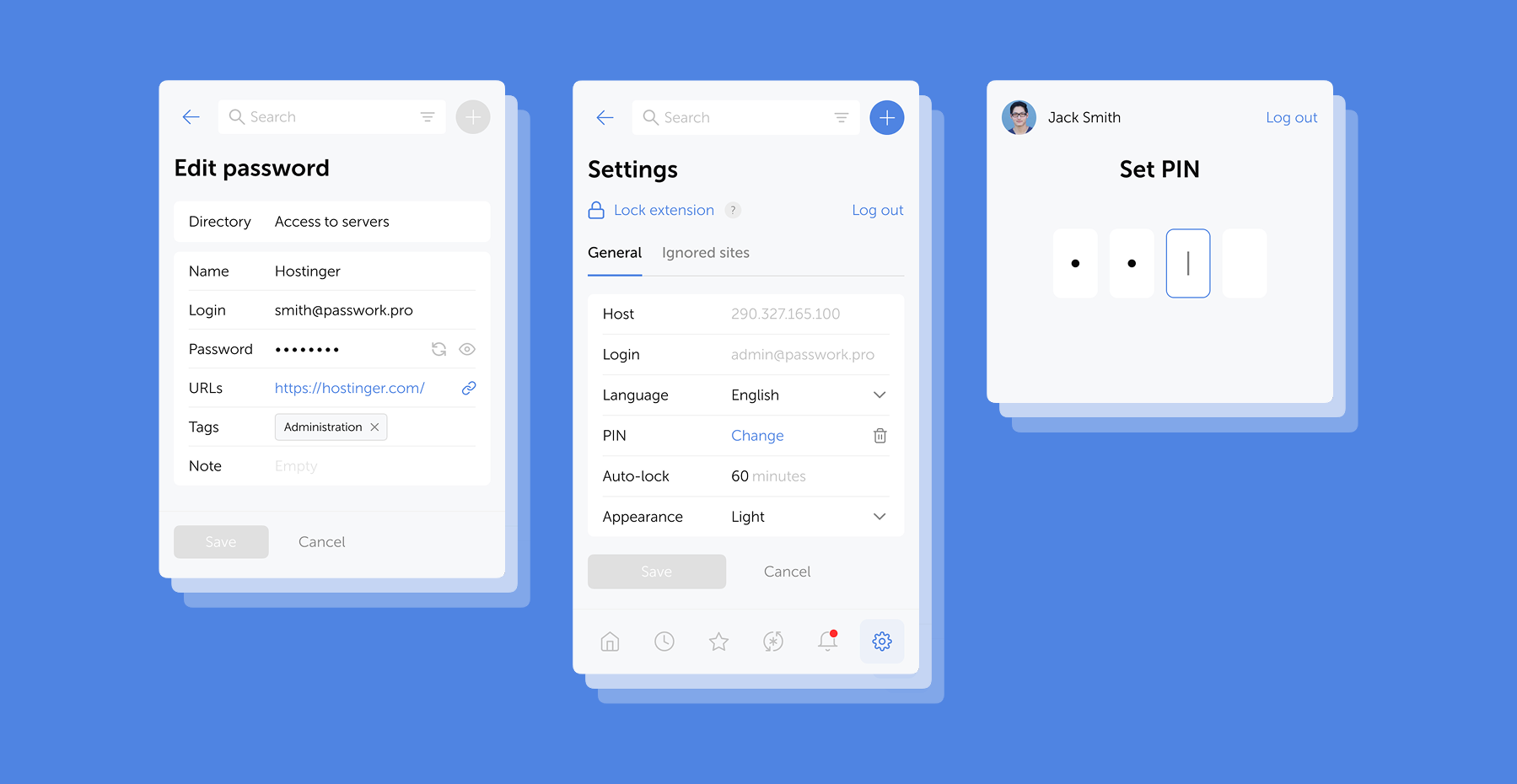
The latest release introduces additional access controls for the desktop app and adds several UI improvements and fixes.
Desktop app access control
Passwork administrators can now manage access to the desktop app. The Account section in role settings includes two new parameters that allow you to enable or disable the desktop client and restrict its download from the web version.
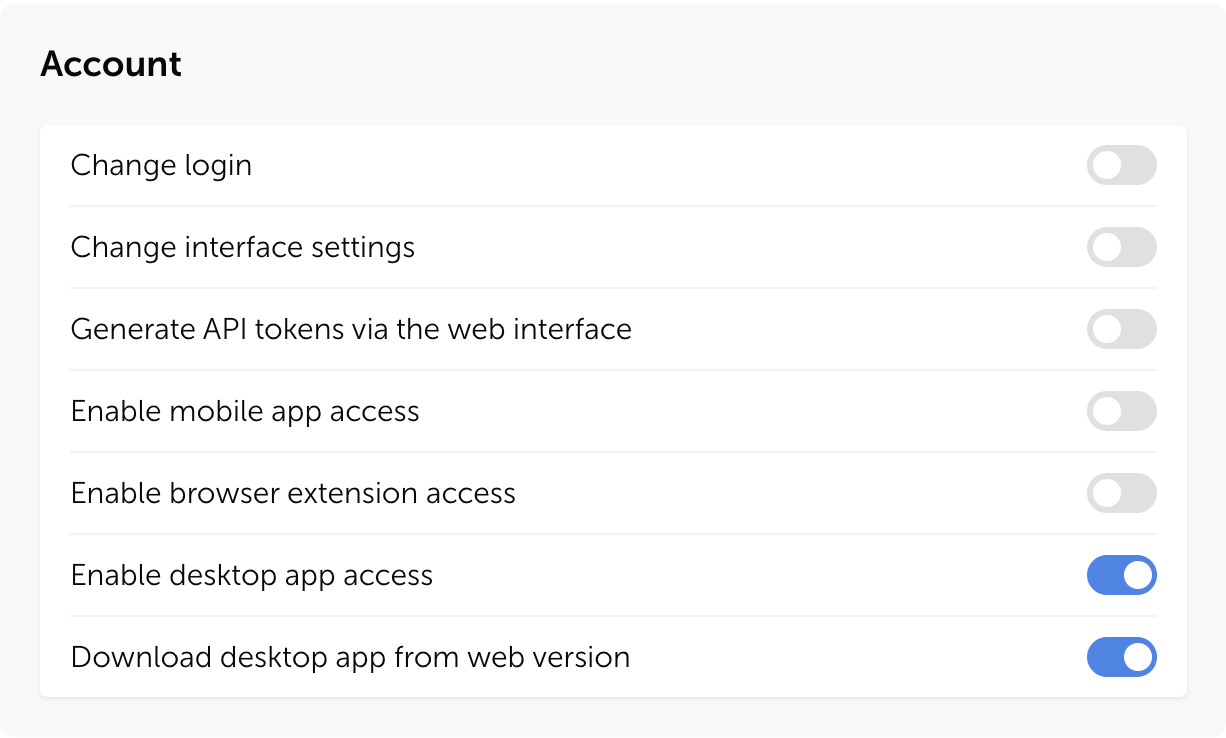
Apply these permissions via role settings under Settings and users → Roles → Select role → Account.
Improvements
- Added the option to copy URL directly from the Copy to clipboard context menu
- Added automatic master password migration for users upgrading from Passwork 5.3 and earlier versions
- Minor UI improvements
Bug fixes
- Fixed an issue where folder names displayed incorrectly in the import window when using the dark theme
- Fixed browser back and forward navigation between passwords in Recents, Favorites, and Inbox
- Fixed an issue where account settings for the Owner role failed to save after a page refresh
- Fixed the display of some system notifications
- Fixed an avatar upload failure
Desktop app 1.2.0
- Fixed an issue where the macOS app required manual confirmation in Privacy & Security settings on first launch
- Fixed an issue causing incorrect session termination
- Fixed an issue in Vault settings where the Save and Cancel buttons in the All vaults tab could overlap other elements during scrolling
- Fixed the incorrect app icon displayed in the Windows taskbar preview


Passwork 7.5.2 release
The latest release introduces additional access controls for the desktop app and adds several UI improvements and fixes.

Outdated password practices, such as memorizing credentials or enforcing complex rules, consistently fail against today's threats. The Verizon Data Breach Investigations 2025 Report reveals that compromised credentials remain the leading cause of security incidents, with 22% of hacking-related breaches leveraging stolen or weak passwords.
Credential stuffing accounts for up to 19% of daily authentication attempts in enterprise environments. At $4.4 million per incident, the average breach cost reported by IBM in 2025 shows what's at stake.
The evolution of password management
Over the past decade, password management has fundamentally changed. We have moved away from frustrating, outdated practices like mandatory monthly password changes. Today, frameworks like NIST SP 800-63 guide organizations toward a more practical approach: longer passphrases and multi-factor authentication (MFA).
Security used to rely on complexity for its sake. Modern policies focus on resilience against real-world threats. A long, memorable passphrase is now far more effective than a short password packed with arbitrary special characters. Because long passphrases are harder to crack using brute-force methods, and their convenience helps users avoid unsafe practices like writing down their passwords.
Core password management
Password management relies on secure passwords, password managers, and MFA. Password policies adhere to NIST SP 800-63 standard by emphasizing the use of strong passwords and the adoption of multifactor authentication (MFA). These policies effectively address the most common entry points attackers use. This approach ensures that credential storage complies with audit and regulatory requirements.
Password managers make it easier to store complex passwords and help organizations maintain consistent credential policies. They also include built-in MFA support, providing an additional layer of verification. As a result, even if a password is compromised, the account remains protected.
Implications and benefits for enterprises:
- Password managers are important for secure credential storage
- Multi-factor authentication (MFA) provides an additional layer of protection
- Password policies help maintain secure password hygiene across systems
- Password strength is a defense against attacks like credential stuffing
Creating reliable passwords
Secure passwords defend against brute-force attacks, but length matters more than complexity. For accounts without MFA, NIST SP 800-63B sets the minimum password length to 8 characters, and with MFA to 15 characters.
Composition rules (uppercase, numbers, symbols) are now explicitly forbidden — they lead to predictable patterns like "P@ssw0rd567". Instead, encourage passphrases. Random word combinations like "correct-horse-battery-staple" are harder to crack than short complex strings.
Characteristics of secure passwords:
- Length: at least 12 characters
- Complexity: random letters, numbers, symbols
- Memorability: use passphrases
The role of password managers
Behind the scenes, enterprise password managers handle encryption and authentication in addition to credential storage. With zero-knowledge architecture, the data stays encrypted on your device, and the provider never sees it. When selecting the right solution, it’s important to focus on key features that ensure security and adaptability: strong encryption, flexible deployment (cloud or on-premise), and built-in MFA support.
Some compliance and security policies call for keeping data behind a company's own firewall. For these organizations, on-premise deployment is a hard requirement. Passwork supports both cloud and on-premise, so you can choose what fits your infrastructure.
Multi-factor authentication: Security multiplier
MFA remains necessary for account protection — the DBIR treats it as a baseline. Yet the report also warns against complacency. Token theft, adversary-in-the-middle attacks, where an attacker intercepts communication between the user and the server, and SIM swapping are already identified as MFA bypass techniques in the 2025 dataset, and these threats are expected to become even more prevalent in the future.
Phishing-resistant methods like FIDO2 / WebAuthn offer stronger defense by binding credentials cryptographically to specific domains and devices.
Steps to implement MFA across common platforms:
- Enable MFA for all user accounts
- Choose your MFA method (SMS, app, or hardware token)
- Integrate with existing identity management systems (AD / LDAP / SSO)
- Set up recovery options for lost authentication factors
- Educate users on MFA use and benefits
Avoiding password reuse and its dangers
Credential stuffing exploits password reuse at scale. Credentials leaking from one site often lead attackers to test them across others, where they succeed in 0.2–2% of attempts. With billions of stolen credentials available, attackers can compromise thousands of accounts.
Password managers solve this — they generate unique passwords for every account. If a breach occurs on one platform, it remains contained and cannot spread to other systems.
Key practices to prevent password reuse:
- Use unique passwords for all accounts
- Store them securely in a password manager
- Regularly update password policies
When you evaluate password managers, deployment flexibility matters. For organizations with compliance requirements or existing infrastructure, it can be a deciding factor. Both cloud and on-premise options are available for testing in a demo environment that matches your actual setup.
Enterprise password management best practices

At the organizational level, password management has to account for team hierarchies, distributed infrastructure, and compliance rules. Centralized management, policy enforcement, and integration with existing systems reduce the risk of credential-related breaches. For privileged accounts, this extends to privileged access management (PAM) controls, limiting who can access critical systems and how.
Given the moderate to high implementation complexity (3-6 months), organizations should set realistic expectations. A successful enterprise-level strategy includes the use of password managers with multi-factor authentication, alongside solid password policies that follow current security standards.
Implementing centralized password management solutions
Before you select an enterprise password management system, evaluate deployment options: cloud, on-premises, or both, against your organization's size, security needs, and compliance rules.
A centralized platform applies password policies consistently across all users and removes the risk of employees skipping rules or using unapproved workarounds. For secure credential management, pair your password manager with multi-factor authentication.
Password policies that balance security and usability
Without proactive monitoring, suspicious login patterns can go unnoticed for weeks or months. To detect credential stuffing, which the Verizon DBIR identifies as an increasingly prevalent attack type, security teams rely on behavioral analysis and rate limiting. For brute-force attacks, account lockout policies act as the primary countermeasure.
To block brute force attacks, security teams rely on account lockout and rate limiting. By establishing baseline login patterns and setting deviation alerts, organizations can spot anomalies early. Regular reviews of password policies against actual login data reveal where rules create friction without adding security. Quick responses to emerging risks keep systems protected.
Advanced strategies beyond passwords
Passwordless authentication replaces traditional passwords with more secure methods. Instead of typed credentials, WebAuthn uses biometrics or security tokens. Because credentials never leave the device, phishing and credential theft no longer apply.
According to NIST SP 800-63B, hardware-bound implementations, such as FIDO2 security keys, can meet AAL3, the highest authenticator assurance level. Synced passkeys satisfy AAL2 requirements.
Beyond eliminating passwords, these methods improve user experience and align with NIST's push for stronger authentication. Organizations should keep MFA in place during the transition. MFA continues to protect accounts while passwordless adoption scales across the organization.
The path to passwordless authentication
With WebAuthn, biometrics or security tokens replace passwords using public-key cryptography. When paired with hardware-bound keys, this method meets NIST highest assurance level (AAL3) for identity verification. All major browsers support WebAuthn today, though implementation complexity varies. A gradual approach works best: start with MFA for layered security, then introduce passwordless authentication step by step.
Recommended steps for transitioning to passwordless authentication:
- Assess the current MFA implementation. Verify that MFA is configured to provide an extra layer of protection.
- Integrate WebAuthn. Implement WebAuthn, use biometrics or security tokens.
- Educate users. Prepare your team with proper training on the new authentication methods.
- Update security policies. Revise security policies to reflect the technology integration.
- Monitor and evaluate. Continuously track and evaluate the effectiveness of passwordless authentication.
Operational metrics for password management
Without clear metrics, password management stays invisible to leadership. Tracking specific indicators helps demonstrate their value across the organization. Start with these metrics: help desk ticket volume for password resets, MFA adoption rates, time to detect anomalous login attempts, and password reuse rates per department.
Beyond operational metrics, security standards like GDPR, HIPAA, and PCI DSS require organizations to verify compliance through audit trails — something centralized password management automatically provides. Regular reporting on these metrics turns security from a cost center into a documented, accountable program.
Building a culture of password security
Cybercrime increasingly targets human behavior. Technical controls alone cannot close this gap. Across the organization, strong password habits reduce risk more than any single tool.
Long-term adoption depends on combining sound password practices with security awareness. Employees need to understand why MFA matters and how to spot phishing attempts. When security becomes part of the daily workflow, adoption follows naturally.
Transfer your remaining subscription period and enjoy 20% off your first renewal.
Frequently Asked Questions

What are the important password management best practices for 2026?
For 2026, password management practices include using unique passwords for every account, leveraging password managers for secure storage, and implementing multi-factor authentication (MFA) for added protection. Organizations should adopt a centralized password policy and maintain security awareness to protect against threats, such as credential stuffing.
How do password managers improve security compared to manual password management?
Password managers improve security by storing encrypted credentials, generating secure passwords, and preventing password reuse. Unlike manual management, password managers automate password updates and integrate with multi-factor authentication (MFA), boosting overall security and minimizing human error, which can lead to breaches.
Why is implementing multi-factor authentication important for password security?
Implementing multi-factor authentication (MFA) adds an important layer of security by requiring users to provide more than just a password. Even if passwords are compromised, MFA protects accounts by validating identity through additional verification methods such as security tokens or biometric authentication, reducing the risk of unauthorized access.
How should organizations balance security requirements with user experience in password management?
Organizations should implement user-friendly password policies that encourage reliable passwords while integrating multi-factor authentication to improve security without complicating the user experience. Password managers simplify password management, so users can follow protocols without sacrificing convenience. Balancing usability and security is needed for compliance and user adoption.
What are the risks of password reuse, and how can they be mitigated?
Password reuse increases the risk of credential stuffing attacks, where attackers use compromised credentials to gain unauthorized access to multiple accounts. Password managers mitigate this risk: they generate and store unique passwords for each account, prevent reuse across platforms, and limit the number of systems exposed if one credential leaks.

Password management best practices for enterprise security
Cybercrime increasingly targets human behavior. Technical controls alone cannot close this gap. Across the organization, strong password habits reduce risk more than any single tool.
In the new version, we’ve improved TOTP autofill and added error logging to the browser extension. You can now export logs directly from the service worker console and share them with our team — significantly speeding up troubleshooting.
- Improved TOTP autofill performance in the browser extension
- Added the capability to download error logs through the service worker console using the downloadErrors() command
- Fixed an issue where TOTP autofill did not work for items from the Inbox
- Fixed an issue where the extension could incorrectly prompt to save or autofill data in some forms not related to authentication
- Fixed an issue that could block extension functionality after connecting it
- Fixed an issue where notification dates could display incorrectly
- Fixed an issue preventing the extension from working in Firefox Incognito mode
- Minor bug fixes and performance improvements


Browser extension 2.0.34 release
In the new version, we’ve improved TOTP autofill and added error logging to the browser extension. You can now export logs directly from the service worker console and share them with our team — significantly speeding up troubleshooting.

Bring Your Own Device (BYOD) has transformed from a workplace trend into a business necessity. By 2026, over 82% of companies will have adopted formal BYOD policies, with more than 80% actively promoting this approach. This reflects a fundamental change in how organizations approach workplace flexibility and productivity.
The appeal is clear: employees work on devices they know, IT departments reduce hardware costs, and companies attract talent seeking flexibility. But this convenience introduces security challenges that can expose sensitive data, compromise networks, and create compliance headaches.
This guide walks you through the security landscape of BYOD — from understanding core risks to implementing frameworks that protect your organization without sacrificing employee autonomy.
Understanding BYOD and its security implications
BYOD allows employees to use personal smartphones, tablets, and laptops for work tasks. These devices access corporate email, cloud applications, internal networks, and sensitive data — all while living outside traditional IT control.
The current state of BYOD in modern workplaces
Organizations now face a reality where personal devices are integral to daily operations, not exceptions to policy.
Employees expect seamless transitions between home and office, using devices that fit their workflows. IT departments adapted by building security architectures that accommodate this flexibility rather than resist it.
Why organizations are adopting BYOD
Cost reduction drives many BYOD programs. Companies save on hardware procurement, maintenance, and replacement cycles. Employees bear the initial device cost, while organizations invest in security infrastructure and management tools.
Employee satisfaction improves when workers use familiar devices. Learning curves disappear, productivity increases, and job satisfaction rises. This matters in competitive talent markets where workplace flexibility influences hiring decisions.
Operational agility increases as employees access work resources from anywhere. Business continuity improves because workers aren't tied to corporate-owned equipment. During disruptions, operations continue with minimal interruption.
Main BYOD security challenges
- Lack of standardization. Personal devices vary in operating systems, security patch levels, and configurations, leading to inconsistent security postures.
- Visibility gaps. IT teams have difficulties monitoring device health, installed apps, and security settings, leaving blind spots in the security landscape.
- Policy enforcement challenges. Balancing security requirements with employee privacy can lead to resistance or vulnerabilities.
- Lifecycle management issues. Managing security when employees upgrade devices, switch platforms, or leave the organization requires careful planning and technical capabilities.
Key BYOD security risks and vulnerabilities
Data leakage and loss in BYOD environments
Corporate data lives alongside personal information on BYOD devices. Employees might unintentionally share confidential files through personal cloud storage, messaging apps, or email accounts. The boundary between work and personal use blurs, creating opportunities for data to escape corporate controls.
Lost or stolen devices represent immediate security incidents. Without proper safeguards, anyone accessing the device gains entry to corporate resources. The risk intensifies when devices lack basic protections for example screen locks or encryption.
Malware and phishing threats targeting personal devices
Personal devices often have weaker security than corporate equipment. Employees might disable security features for convenience, install apps from untrusted sources, or ignore software updates. These behaviors create entry points for malware.
Phishing attacks exploit the personal nature of BYOD. Attackers send convincing messages to personal email or messaging apps, knowing employees use the same device for work. Once compromised, the device provides access to corporate networks and data.
Out-of-date devices and unpatched vulnerabilities
Employees control update schedules on personal devices. Critical security patches might wait days or weeks while users delay updates for convenience. During this window, known vulnerabilities remain exploitable.
Older devices present additional challenges. Manufacturers eventually stop supporting devices with security updates, leaving them permanently vulnerable. When employees continue using these devices for work, they introduce unpatched risks into your environment.
Shadow IT and unsanctioned applications
Employees install applications that solve immediate problems without considering security implications. File-sharing services, collaboration tools, and productivity apps might bypass IT approval processes entirely.
These unsanctioned applications often lack proper security controls, compliance certifications, or integration with corporate security systems. Data flows through services your security team doesn't monitor or protect.
Mixing personal and business use
One of the most common vulnerabilities in BYOD environments is credential mismanagement. Employees frequently save corporate passwords in personal browser keychains or unencrypted notes for convenience. Meanwhile, a corporate password manager lives separately on their device, featuring its own encryption, access control, and biometric protection. With Passwork, employees access company vaults through a mobile app, keeping work credentials completely separate from personal data.
Building an effective BYOD security framework
Creating a comprehensive BYOD security policy
Your BYOD policy defines acceptable use, security requirements, and responsibilities. It should address device eligibility, required security measures, acceptable applications, and data handling procedures.
Scope and eligibility sections clarify which devices qualify for BYOD programs and which roles can participate. Not every position requires BYOD access, and not every device meets minimum security standards.
Security requirements must be specific and enforceable. Define mandatory features such as encryption, screen locks, biometric authentication, and automatic updates. Specify prohibited activities such as jailbreaking or rooting devices.
Data classification guides employees in handling different information types. Clearly distinguish between public, internal, confidential, and restricted data. Define which data types are accessible via BYOD and which require corporate-owned devices.
Incident response procedures outline steps employees must take when devices are lost, stolen, or compromised. Include reporting timelines, contact information, and expectations for cooperation during investigations.
Defining device and software requirements
- Operating system requirements. Only devices with actively supported operating systems should be allowed in BYOD programs. Outdated systems must be excluded.
- Mandatory security features. Devices must include encryption, secure boot, and hardware-backed credential storage. Ensure these features are enforced by policy.
- Approved applications. Provide employees with a list of secure, approved apps and alternatives to unsanctioned tools to encourage compliance.
Technical solutions for BYOD security
Securing Network Access and Ensuring Compliance
Personal devices should not have the same network access as corporate equipment. Implement network segmentation and strict access controls so that BYOD users can only access the necessary resources. Require a VPN for remote access in order to encrypt traffic and control entry points. Continuous network monitoring should detect unusual activity and trigger alerts.
These controls also help organizations meet regulatory requirements, such as HIPAA, GDPR, and others. A robust network strategy supports data residency rules and ensures proper logging and reporting for audits, including access records and incident tracking.
Best practices for BYOD security implementation
Security policies fail without employee buy-in. Focus training on practical compliance and real-world threats:
- Onboarding first: Introduce BYOD policies, privacy boundaries, and incident reporting before employees enroll devices.
- Continuous awareness: Share relevant threat intelligence and highlight recent incidents regularly to keep security top-of-mind.
- Scenario-based learning: Train employees using industry-specific examples — like targeted phishing attempts or common social engineering tactics.
Monitoring and managing BYOD security risks
Proactive monitoring prevents minor issues from escalating into breaches:
- Continuous tracking: Monitor device compliance, flag outdated software, and identify suspicious activities in real time.
- Visibility dashboards: Track key metrics like enrollment rates, policy compliance, and OS versions across your environment.
- Automated remediation: Configure systems to automatically restrict access or notify users when devices fall out of compliance.
- Regular audits: Review access logs and test remote wipe capabilities to ensure technical controls adapt to evolving threats.
Balancing security with employee privacy
Successful BYOD programs protect corporate data while respecting personal privacy:
- Containerization: Isolate corporate data within managed containers — keeping personal information entirely outside IT visibility.
- Transparent policies: Explicitly document what data IT can access, clarifying that monitoring focuses strictly on corporate resources.
- Informed consent: Require employees to acknowledge monitoring capabilities and remote wipe scenarios before device enrollment.
Zero-trust architecture for BYOD environments
Zero-trust principles assume no device or user is inherently trustworthy. Every access request requires verification regardless of network location or previous authentication.
Multi-factor authentication (MFA) is no longer optional. It is the baseline. Biometrics, hardware tokens, and authenticator apps should work together as layered protection.
In BYOD environments, employees need secure access to corporate credentials on their personal devices. Passwork mobile apps for iOS and Android provide biometric unlock with Face ID and Touch ID, allowing users to authenticate once and then securely access shared company vaults without disruption. This reflects a zero-trust approach in practice: identity is verified at the device level while the user experience remains seamless.
Continuous authentication monitors user behavior and device posture throughout sessions. Anomalies trigger re-authentication or access restrictions. If a device becomes less secure during a session, access is automatically adjusted.
Least privilege access limits what BYOD users can access based on role and necessity. Employees receive access to resources required for their jobs, nothing more. This minimizes potential damage from compromised devices.
Mobile threat defense and endpoint security
Mobile Threat Defense (MTD) solutions protect BYOD devices from threats specific to mobile environments. These platforms detect and respond to threats that traditional security tools miss.
Threat detection identifies malicious apps, network attacks, and device compromises. MTD solutions analyze application behavior, network connections, and device configurations to spot indicators of compromise.
Phishing protection extends to mobile browsers and messaging applications. MTD platforms detect and block access to known phishing sites, warn users about suspicious links, and prevent credential theft.
Network security evaluates Wi-Fi and cellular connections for risks. MTD solutions identify man-in-the-middle attacks, rogue access points, and insecure network configurations that could expose data.
Data protection strategies for BYOD
Think of containerization as a secure vault inside your employee's phone. Work apps and data stay locked in their own space — completely separate from personal photos, messages, and apps.
Application wrapping adds security controls to existing applications without modifying source code. Wrapped applications enforce encryption, prevent data leakage, and integrate with authentication systems.
Data Loss Prevention (DLP) within protected spaces prevents unauthorized data transfers. Users can't copy corporate data to personal applications, upload files to unsanctioned cloud services, or share information through unmanaged channels.
Remote wiping and data recovery
The future of BYOD security: Emerging trends and technologies
AI-powered threat detection will enhance BYOD security by identifying subtle behavioral anomalies and zero-day threats. Machine learning models will adapt to evolving attack patterns faster than signature-based approaches.
Passwordless authentication using biometrics and hardware tokens will replace traditional passwords. This shift reduces phishing risks and improves user experience on personal devices.
Edge computing will enable real-time security decisions without routing all traffic through centralized systems. Devices will make local security assessments, improving performance while maintaining protection.
Integration with SASE (Secure Access Service Edge) architectures will provide comprehensive security for BYOD users regardless of location. Cloud-delivered security services will protect devices accessing resources from anywhere.
Conclusion: Building a balanced BYOD security strategy
Effective BYOD security requires balancing protection with usability. Overly restrictive approaches drive non-compliance, and insufficient security exposes your organization to unacceptable risks.
Start with clear policies that employees understand and accept. Implement technical controls that protect data without unnecessarily invading privacy. Provide training that empowers employees to recognize and respond to threats.
Monitor your BYOD environment continuously, adapting to new threats and changing business needs. Regular assessments ensure your security measures remain effective as technology and attack methods evolve.
BYOD done right delivers flexibility, cost savings, and employee satisfaction without compromising security. The key is treating BYOD security as an ongoing program, not a one-time implementation.
Frequently Asked Questions

What is BYOD security?
BYOD security encompasses policies, technologies, and practices that protect corporate data and resources accessed through employee-owned devices. It addresses risks from device diversity, personal use mixing with business activities, and reduced IT control.
What are the main security risks of BYOD?
Primary risks include data leakage from lost or stolen devices, malware infections from personal use, unpatched vulnerabilities on outdated devices, shadow IT introducing unsanctioned applications, and compliance violations from inadequate controls.
How do you implement a BYOD security policy?
Start with risk assessment, identifying critical data and acceptable access scenarios. Develop comprehensive policies covering device requirements, security measures, and acceptable use. Deploy technical controls including MDM, MFA, and containerization. Train employees on security requirements and privacy boundaries.
How should employees manage corporate passwords on personal devices?
Organizations must avoid letting employees store work credentials in personal browser keychains or unencrypted apps. The most effective approach is deploying a corporate password manager with dedicated mobile applications. Passwork allows employees to access shared company vaults securely on their smartphones. Features such as biometric unlock and secure autofill ensure credentials remain protected and are never exposed to the device's unmanaged ecosystem.
What is the difference between MDM and MAM?
MDM (Mobile Device Management) controls entire devices, enforcing security policies across all device functions. MAM (Mobile Application Management) focuses on protecting specific applications and their data, leaving personal device areas unmanaged. MAM addresses privacy concerns by limiting IT control to work-related apps.
Can BYOD be secure enough for regulated industries?
Yes, with proper controls. Regulated industries successfully implement BYOD using containerization, strong authentication, encryption, network segmentation, and comprehensive monitoring. The key is matching security controls to regulatory requirements and data sensitivity levels.
How do you handle BYOD devices when employees leave?
Implement remote wipe capabilities that remove corporate data while preserving personal information. Revoke access credentials immediately upon termination. Maintain backups of corporate data independent of devices. Document offboarding procedures and verify completion for each departure.
What should a BYOD policy include?
Essential elements include scope and eligibility criteria, device and software requirements, security measures and controls, acceptable use guidelines, data classification and handling procedures, privacy boundaries and monitoring disclosures, incident response procedures, and offboarding processes.
How does zero-trust architecture apply to BYOD?
The zero-trust approach considers all devices to be potentially compromised and requires continuous verification. BYOD implementations use MFA for every access request, monitor device posture continuously, enforce least privilege access, and segment networks to limit blast radius from compromised devices.

BYOD security: Practical steps to keep corporate data secure

Most data breaches start the same way: with weak or poorly managed credentials. In basic web application attacks alone, the 2025 Verizon DBIR traced 88% of incidents back to stolen passwords. For any organization handling sensitive data, computer security starts with credential control. And password security has shifted beyond a recommendation and become a baseline requirement.
A password manager addresses this risk. For every account, it generates, stores, and auto-fills unique credentials — all protected by one master password. Instead of spreadsheets, sticky notes, and repeated password resets, teams get a controlled and auditable process across the entire workflow.
Main points:
- One master password replaces hundreds of weak, reused credentials
- AES-256 encryption and zero-knowledge architecture keep your vault unreadable, even to the provider
- Setup takes planning, but the payoff is fewer support tickets, stronger compliance, and reduced breach risk
Understanding password managers
A password manager works as an encrypted vault — a digital safe that holds login credentials, secure notes, and other sensitive data. When you sign in somewhere, the manager retrieves the right password and fills the form automatically. Behind that vault stand two technologies: encryption and zero-knowledge architecture.
How password managers protect your digital identity
Before data leaves your device, AES-256 encryption (Advanced Encryption Standard with a 256-bit key) scrambles it into unreadable ciphertext. The same algorithm is used by governments and financial institutions.
Zero-knowledge architecture adds a second layer. Under this model, the provider cannot decrypt your data. Because all cryptographic operations happen locally, even full server access would reveal only encrypted blobs. We publish our cryptography documentation openly so teams can verify exactly how this works.
What password managers can and cannot do
A password manager is a reliable layer of defense, though it does not cover every threat on its own. Knowing its limitations helps you plan additional safeguards.
Multi-factor authentication (MFA) adds a second verification step, such as a time-based one-time password (TOTP), and addresses gaps that a password manager alone cannot cover. Together, they form a much stronger defense.
Creating your master password
Your master password is the single credential that unlocks the entire vault — a weak one undermines every other security measure.
Released in August 2025, NIST SP 800-63B-4 sets a minimum length of 15 characters for passwords used as a single-factor authenticator. The same revision states that verifiers shall not impose password composition rules (e.g., requiring uppercase letters, numbers, or symbols) and instead must screen passwords against lists of commonly used or compromised values. A password like "P@ssw0rd123" would fail such screening.
Instead of random character requirements, the passphrase method works better: pick four or five unrelated words and combine them. A password generator can produce random word combinations, but many users prefer manual selection. "correct-horse-battery-staple" is a classic example — high entropy.
Step-by-step master password creation:
- Choose 4–5 random, unrelated words (avoid song lyrics or famous quotes)
- Add a separator between words (hyphens, dots, or spaces)
- Optionally insert one number or symbol at a random position — not at the end
- Test: can you type it from memory three times in a row?
- Write it down once, store that paper in a physically secure location, then memorize it within a week
Master password best practices
Do:
- Memorize it, never store it digitally in plain text
- Keep one physical backup in a secure place (a sealed envelope in a safe, for example)
- Practice typing it regularly during the first week
Don't:
- Reuse your master password for any other account
- Share it with anyone, including IT staff
- Change it on a fixed schedule without reason: according to NIST SP 800-63B-4, passwords should change only when evidence of compromise exists
Recovery options are limited by design. With a zero-knowledge architecture, the provider cannot reset your master password because they never had access to it.
Choosing the right password manager for your needs
Before committing to any password management software, define what your organization actually requires. Deployment model, encryption standards, and integration with existing infrastructure should all factor into the decision.
|
Criteria |
Questions to ask |
| Deployment | On-premise, cloud, or both? Who controls the server? |
| Encryption | AES-256? Zero-knowledge? Where does decryption happen? |
| Integrations | AD/LDAP support? SSO protocols like SAML or OAuth? |
| Team features | Role-based access? Shared vaults? Audit logs? |
| Compliance | GDPR audit trails? Exportable reports? |
| Scalability | Per-user licensing? Can it grow with the team? |
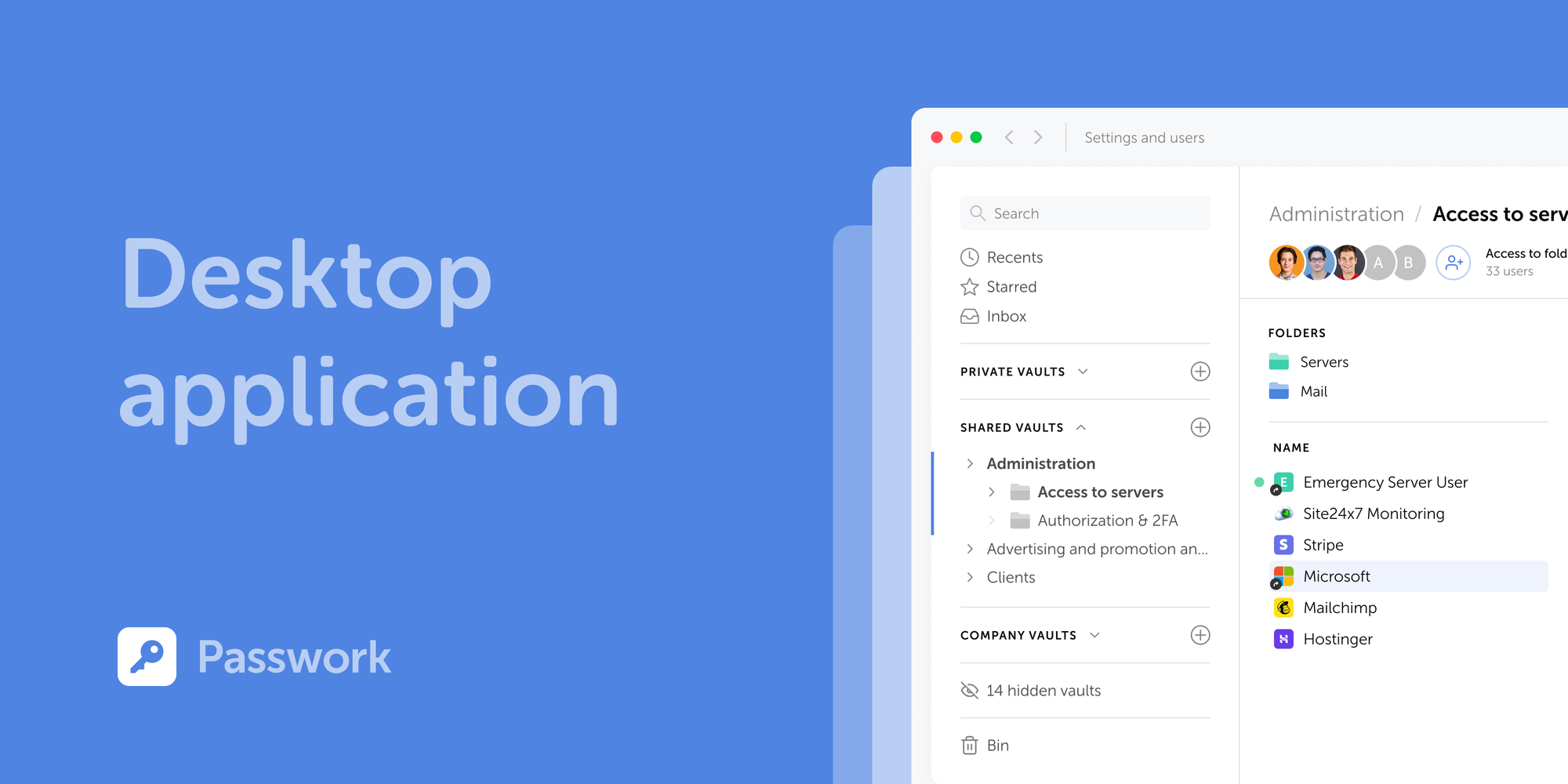
When deployment flexibility and security architecture matter, both on-premise and cloud options should be available. Passwork supports both models, so you can choose where your data lives. The platform features a user-friendly interface that teams can quickly adopt. It combines password management with DevOps secrets management, API keys, tokens, and certificates in one system.
If you're evaluating multiple solutions, see how we perform in a real deployment scenario. Get a demo environment and test alongside other enterprise password managers. No credit card required.
Browser-based vs. dedicated password managers
Browser-built password managers (like the ones in Chrome or Edge) are convenient, but they lack enterprise features. Within a single browser profile, credentials remain isolated — sharing, role-based access, and audit logging are either absent or limited.
With a dedicated password manager, encryption happens independently of the browser, alongside granular access controls and multi-platform sync. Auto-fill and credential capture still run through a browser extension, but the vault sits in a more controlled environment.
Getting started with your password manager

With the master password ready and the solution selected, setup begins. The process follows a predictable path.
- Install the core application: desktop client, web interface, or self-hosted instance
- Create your account with the master password you prepared
- Enable MFA immediately before adding any credentials to the vault
- Install browser extensions for Chrome, Firefox, Edge, or Safari
- Install mobile apps for iOS and Android if remote access is needed
- Configure vault structure: create shared and personal vaults by department, project, or access level
Setting up browser extensions and mobile apps
After installing the extension, adjust a few settings:
- Enable auto-lock after inactivity — five minutes is a reasonable default
- Turn on PIN or biometric lock for the mobile app
- Confirm the extension connects to the correct server URL (required for on-premise deployments)
- Disable auto-fill on public or shared devices
A password saved on your laptop appears on your phone within seconds through cross-platform sync. All data travels encrypted, so even an intercepted sync payload is useless without the master password.
Setting up two-factor authentication for your password manager
MFA adds a second lock to your vault through an additional security verification step. Even if someone learns your master password, access still requires that second factor.
Authenticator apps (Google Authenticator, Authy) generate six-digit TOTP codes that refresh every 30 seconds. During setup, scan the QR code, verify the first code, and save the backup recovery codes in a physically secure location. Without those codes, losing your phone could mean losing vault access.
Importing and organizing your existing passwords
Migration from browsers, spreadsheets, or another password manager into your password storage vault usually starts with a CSV (Comma-Separated Values) export. Most managers accept this format and map fields (URL, username, password) automatically.
Before importing, audit what you have. Old accounts, duplicate entries, and credentials reused across services all need attention. The import stage is the ideal time to replace weak passwords with generated ones.
Our admin tools let you configure vault structures that mirror your team's organization. With role-based access, the finance team sees only finance credentials, while IT administrators maintain oversight of everything. This combination with a cost-efficient approach gives you enterprise-grade control without paying for features you do not need.
For teams implementing password management for the first time, setting up the right structure early prevents future access issues. Book a consultation to define your access model, deployment approach, and rollout plan.
Prioritizing your most critical accounts
Not all accounts carry the same risk. Start migration with the credentials that would cause the most damage if compromised:
- Primary email accounts (often the recovery method for everything else)
- Financial services and payment platforms
- Cloud infrastructure and admin panels
- Business communication tools (Slack, Teams, email servers)
- Social media and public-facing accounts
According to IBM's 2025 Cost of a Data Breach Report, the global average breach cost reached $4.44 million, and the average time to identify and contain an incident was 241 days. Early migration of high-value accounts reduces that exposure window.
Using password health and data breach tools
Once credentials are in the vault, run a password vault health report — a routine computer security check. Built-in data breach monitoring scans your entries against known breach databases, while compromised password detection flags reused or weak credentials. Address critical findings first, especially any accounts where the same password protects multiple services.
Generating and managing strong passwords
For every new account or password replacement, use the built-in password generator. A strong configuration for high-security accounts: 20+ characters, mixed case, numbers, and symbols. Where services impose character limits, adjust — but never go below 15 characters.
A generated password like "g7#Kp!2xVmNqR9bW" has no predictable structure, which makes brute-force attacks impractical. The password manager remembers it, so complexity costs nothing in usability.
Using autofill features securely
Auto-fill speeds up form filling, but it requires awareness. Before letting the extension complete a login, verify these indicators:
- The URL in the address bar matches the expected domain exactly
- The connection uses HTTPS (look for the padlock icon)
- The password manager recognizes the site; if it doesn't offer auto-fill, the domain may be spoofed
- No unexpected redirects occurred before the login page loaded
A phishing page at g00gle.com looks convincing, yet the password manager matches exact domains and will not auto-fill on a fake site. On personal and work devices, keep the extension locked when not in active use.
Sharing passwords securely with others
For joint accounts, admin panels, and third-party services, teams need to share credentials. Sending passwords over email, Slack, or text messages is the wrong approach. Through built-in sharing features, encryption stays intact — credentials remain protected in transit.
We designed our role-based access controls to manage department-specific credentials and temporary contractor access. With on-premise deployment, shared secrets never transit through external servers. Learn more about our approach to business password management.
Managing family and team access
Shared password vaults work like shared folders: each vault has its own access permissions. An IT administrator might have full access, while a marketing team member sees only the social media credentials vault. Under GDPR, organizations must both protect personal data from unauthorized access and prove that protection is in place. Granular access controls and audit logs address both requirements at once.
Advanced features worth using
Beyond storing passwords, most enterprise password managers include features that teams often overlook. Secure notes let you store Wi-Fi credentials, server details, software license keys, or recovery codes — all protected by AES-256 encryption.
Through SSO (Single Sign-On) integration, the password manager connects with your identity provider, reducing friction for users who already authenticate through AD or LDAP. Audit logs track every action: who accessed which credential, when, and from which device — this simplifies GDPR and PCI-DSS (Payment Card Industry Data Security Standard) reporting.
Secure notes and document storage
Secure Shell keys (SSH), API tokens, recovery phrases, or internal procedures — all of these belong in secure notes rather than scattered across email threads or shared drives. Encryption protects them identically to passwords, and access controls determine who sees what.
Device syncing and access management
When a team member updates a password on their laptop, every authorized device reflects that change within seconds. Encrypted in transit, the data travels to the server (or your on-premise instance) and arrives at other devices still protected. Decryption happens only locally.
Proper device management requires MFA verification before any new device gains vault access. Without this step, an attacker who clones a session token could silently reach stored credentials.
Troubleshooting common password manager issues
Maintaining your password security long-term
Security is not a one-time setup. Quarterly reviews keep your vault in good shape:
- Run the vault's security audit to identify weak, reused, or old passwords
- Replace any flagged credentials using the built-in password generator
- Review shared vault access — remove former employees or contractors
- Verify MFA is still active and backup codes are accessible
- Check for any accounts in known breach databases and rotate those passwords immediately
What to do if your password manager is compromised
If you suspect your master password has been exposed, immediate damage control is critical for your computer security:
- Change the master password immediately from a trusted device
- Enable or re-verify MFA on the vault account
- Rotate passwords for your highest-priority accounts (email, financial, infrastructure)
- Review the vault's audit log for unauthorized access
- Notify your security team and begin an incident response according to your organization's protocol
Conclusion: your next steps to password security
A password manager replaces guesswork with structure, a direct upgrade to your organization's digital protection. Instead of hoping employees choose strong passwords, you give them a tool that does it automatically and keeps every credential encrypted, auditable, and under control.
The first step is the simplest: choose a solution, create a strong master password, and start migrating your most critical accounts today.
Frequently Asked Questions

What is a password manager and how to use it?
Inside one encrypted vault, a password manager stores all your credentials – protected by a single master password. For new accounts, it generates strong passwords automatically and auto-fills login forms. We built our platform with AES-256 encryption and zero-knowledge architecture – once client-side encryption is enabled, your data stays unreadable, even to us.
How to use a password manager for the first time?
Create a strong master password (at least 15 characters, following NIST SP 800-63B-4 guidance). Enable MFA, install browser extensions, then import existing passwords from your browser or a CSV file. The process is well-documented and predictable with proper planning.
How do I create a master password?
Use the passphrase method: combine four or five random, unrelated words with separators (e.g., timber-clock-river-frost). Avoid personal details, common phrases, or song lyrics. The goal is high entropy – unpredictable to attackers, memorable for you.
What should I do if I forget my master password?
Under zero-knowledge architecture, the provider cannot recover it. Store a physical backup in a secure location (a sealed envelope in a safe, for example). Some platforms offer emergency access features or recovery keys – configure these during initial setup.
Are password managers safe?
With AES-256 encryption and zero-knowledge architecture, a properly configured password manager is safe by design: decryption happens only on the user's device, so even full server access reveals nothing. The 2025 Verizon DBIR found credential abuse in 22% of breaches – most involving weak or reused passwords. A password manager directly addresses that risk.

How to use a password manager: A guide to reliable security
A password manager replaces guesswork with structure, a direct upgrade to your organization's digital protection.
Passwork is now available as a full-featured desktop app for Windows, macOS, and Linux. The desktop app delivers complete password management functionality: manage credentials, access vaults, collaborate with your team, all with the native performance and convenience of a desktop environment.
Supported operating systems
The desktop application supports Windows 10/11 (64-bit), macOS 12 (Monterey) and later, and Linux distros including Ubuntu 20.04+, Fedora 34+, Debian 11+, and others (64-bit).
How to download
You can download the desktop app directly from the Passwork interface.
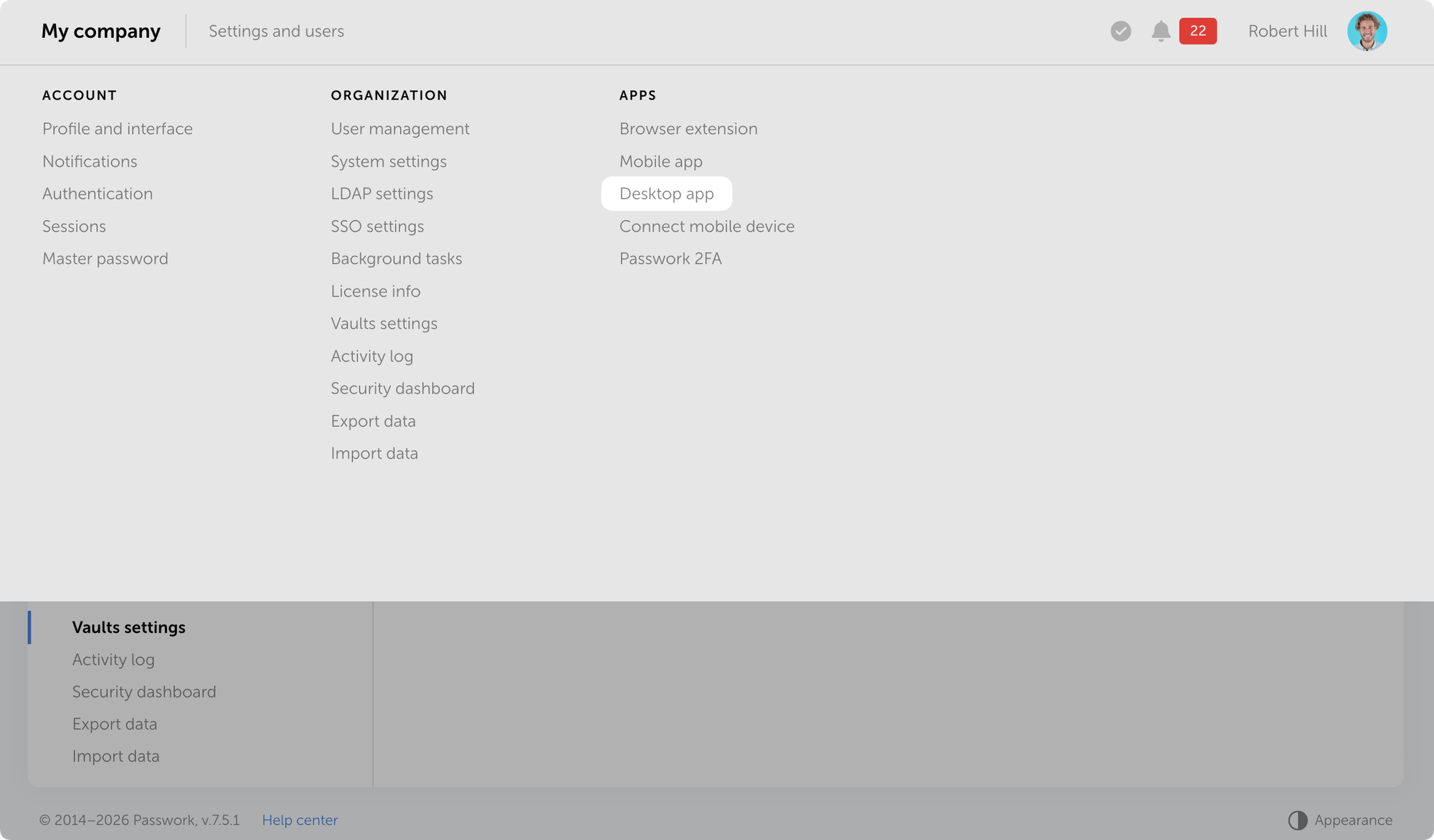
Open Passwork → Settings and users → Desktop app and download the installer for your operating system.
Installation
The app authenticates through your browser. You'll need your Passwork instance hostname.
- Download the installer
- Install the app for your OS and launch it
- Enter your Passwork hostname and click Sign in with browser
- Authenticate in the browser: enter your credentials or sign in via SSO or passkey
- Allow the app to connect to your browser session
- If client-side encryption is enabled in Passwork, enter your master password in the app
Note: If you have an active session in the web version, Passwork will prompt you to continue with the current user or switch accounts.
How to update
New desktop app versions are released alongside Passwork updates. When a new version becomes available, the app prompts you to update. The process is automatic — the installer downloads from the repository and installs without manual intervention.
What's next
Upcoming releases will introduce desktop-exclusive features, including offline mode. Access your passwords without a server connection, ensuring continuity even when network access is unavailable.
All information about Passwork updates in our release notes


Introducing Passwork Desktop app
Passwork is now available as a full-featured desktop app for Windows, macOS, and Linux. The desktop app delivers complete password management functionality: manage credentials, access vaults, collaborate with your team, all with the native performance and convenience of a desktop environment.

Password security stands as your first line of defense against cyber threats. A comprehensive approach combines strong password creation, encrypted storage through password managers, and multi-factor authentication to counter increasingly sophisticated attacks targeting your digital identity.
The true cost of weak passwords
Data breaches cost organizations an average of $4.35 million per incident, according to IBM's Cost of Data Breach Report. According to the Verizon DBIR 2025 Report, compromised credentials are the leading cause of security incidents: 22% of hacking-related breaches leverage stolen or weak passwords.
Beyond financial losses, organizations face regulatory penalties, operational disruption, and reputational damage. Identity theft affects millions annually, with attackers exploiting weak passwords to access banking systems, healthcare records, and corporate networks. The cascading effects extend far beyond the initial breach — customer trust erodes, legal liabilities mount, and recovery efforts consume months of resources.
Companies struggle daily with password-related security incidents, where basic credential weaknesses lead to significant business disruption. Passwork's Zero-knowledge encryption architecture and transparent cryptography documentation help organizations understand exactly how their passwords are protected, eliminating the guesswork that often leads to security compromises.
Common password vulnerabilities and attack methods
Credential stuffing exploits password reuse across multiple accounts. Attackers obtain credentials from one breach and systematically test them against other services, succeeding when users recycle passwords. Dictionary attacks rapidly test common passwords and predictable patterns against target accounts.
Phishing remains devastatingly effective. Hackers craft convincing emails that trick users into revealing credentials directly. Brute force attacks test character combinations, with weak passwords falling within minutes. Password cracking tools leverage GPU processing to test billions of combinations per second.
The most exploited vulnerabilities stem from human behavior: using "password123" or "qwerty," incorporating easily discoverable personal information such as birthdays, and reusing the same password for years. Have I Been Pwned documents over 12 billion compromised accounts, demonstrating the scale of credential exposure. Password checkers reveal that most user-created passwords would crack in under an hour using standard tools.
Creating secure passwords and management strategies
Password strength fundamentally depends on length rather than complexity. NIST guidelines recommend a minimum 12-character password, with each additional character exponentially increasing crack time. A 16-character passphrase like "correct-horse-battery-staple" provides superior security compared to "P@ssw0rd!" while remaining more memorable.
Combining uppercase, lowercase, numbers, and symbols creates complexity, but a 20-character phrase of random words defeats attackers more effectively than an 8-character jumble of special characters. The mathematics of password entropy clearly favors length.
Longer passphrases provide better security than complex character combinations. Passwork's built-in password generator follows NIST guidelines, while our dual capability combines enterprise-grade password management with secrets management for DevOps teams — something most traditional password managers can't offer. Learn more about Passwork's enterprise deployment options.
Secure storage becomes essential when managing dozens of unique passwords. Writing passwords on paper creates physical security risks. Storing them in unencrypted documents or browser storage exposes credentials to malware. Password managers solve this problem by providing encrypted vaults that are protected by a single master password. This allows you to create and maintain unique and complex passwords for each of your accounts without having to remember them all.
Password manager selection and setup guide
Enterprise password management requires evaluating deployment models, security architecture, and operational capabilities. 1Password emphasizes business sharing features and cross-platform accessibility. KeePass provides open-source flexibility with local database control. LastPass offers cloud convenience but has faced security incidents that raise deployment concerns.
Password manager feature comparison chart:
While 1Password offers strong business features and KeePass provides open-source flexibility, businesses need both password management and secrets management in one platform. Modern infrastructure includes not only human passwords, but also API keys, tokens, certificates. Passwork provides on-premises deployment, whereas Bitwarden is cloud-based. For companies, cost-efficiency without feature bloat is important.
Setup begins with master password creation. This single credential protects your entire vault, requiring maximum strength — minimum 16 characters combining random words or a memorable phrase with added complexity. Enable encryption at rest and verify that the password manager uses AES-256 or equivalent encryption standards.
Migration requires a systematic approach: inventory existing credentials, prioritize critical accounts, and gradually transfer passwords while updating weak credentials. Configure browser extensions for autofill convenience, but verify they require authentication before populating credentials. Establish backup procedures for encrypted vault data, ensuring recovery options if master password access is lost.
Multi-factor authentication and future security
Multi-factor authentication (MFA) transforms password security from single-point failure to layered defense. Even when attackers obtain passwords through phishing or breaches, MFA blocks unauthorized access by requiring additional verification. This secondary defense layer reduces account compromise risk by 99.9%, according to Microsoft security research.
MFA combines something you know (password), something you have (phone or security key), and something you are (biometric data). This approach ensures that credential theft alone proves insufficient for account access. Organizations implementing MFA across critical systems dramatically reduce successful breach attempts, as attackers rarely possess multiple authentication factors.
The authentication landscape evolves toward passwordless systems. Biometrics leverage fingerprints, facial recognition, or behavioral patterns for verification. Passkeys, built on WebAuthn standards, enable cryptographic authentication without traditional passwords. These technologies promise enhanced security while reducing user friction.
Passwork integrates seamlessly with existing MFA systems through SSO and LDAP connections, ensuring that it becomes part of your existing security infrastructure rather than creating another authentication silo. This integration approach reduces user friction while maintaining the security benefits of multi-layered authentication.
MFA methods and emerging authentication technologies
Authenticator apps like Google Authenticator or Microsoft Authenticator generate time-based codes, providing strong security without SMS vulnerabilities. Hardware security keys offer maximum protection against phishing through cryptographic challenge-response protocols. SMS-based codes remain common but face interception risks through SIM swapping attacks.
Biometric authentication delivers convenience and security when properly implemented. Fingerprint sensors and facial recognition systems verify identity without memorization requirements. However, biometrics cannot be changed if compromised, requiring careful implementation with fallback options.
Passkeys represent the authentication future. WebAuthn enables public-key cryptography where private keys never leave your device. Passkeys prevent phishing by using cryptographic verification instead of shared secrets for authentication. Major platforms now support passkey implementation, with adoption accelerating across consumer and enterprise environments. Biometric hardware works seamlessly with WebAuthn, combining the security of cryptographic keys with the convenience of fingerprint or face verification.
Conclusion

Effective password security balances protection with usability. Implement unique, lengthy passwords for every account. Store credentials in encrypted password managers rather than memory or insecure documents. Enable multi-factor authentication on critical systems. Monitor for credential exposure through breach notification services.
Passwork is designed to be both enterprise-grade secure and genuinely usable — the best security system is the one people actually use consistently.
Frequently Asked Questions

What makes a strong password?
Strong passwords combine length and unpredictability. Use a minimum of 16 characters, combining random words or mixed character types. Avoid personal information, dictionary words, or predictable patterns. Each additional character exponentially increases crack time — a 16-character password resists brute force attacks for years, while 8-character passwords crack in hours. NIST guidelines emphasize length over complexity rules that create memorable but weak passwords like "Password1!". Password managers eliminate memorization burden, enabling truly random credentials.
Why should I use a password manager?
Password managers solve the fundamental conflict between security and usability. Humans cannot remember dozens of unique, complex passwords, leading to dangerous reuse patterns. Passwork has Zero-knowledge encryption where your master password never reaches our servers, ensuring only you can decrypt credentials. On-premise deployment options provide additional control for regulated industries. Password managers also generate cryptographically random passwords, store API keys and certificates for DevOps workflows, and provide audit trails for compliance requirements. The security improvement dramatically outweighs the minimal learning curve.
How does multi-factor authentication improve my security?
MFA creates layered defense requiring multiple verification methods. Even when attackers steal passwords through phishing or breaches, they cannot access accounts without the second factor. It's better to use authenticator apps or hardware keys over SMS codes, which face interception risks. MFA integration with password managers through SSO and LDAP ensures seamless workflows while maintaining security. Organizations implementing MFA reduce successful account compromises by over 99%, according to security research. The additional seconds required for authentication provide exponentially greater protection against credential-based attacks.
What should I do if I suspect my password has been compromised?
Immediately change the compromised password and any accounts sharing that credential. Check HaveIBeenPwned to verify if your email appears in known breaches. Enable MFA on affected accounts if not already active. Review account activity logs for unauthorized access. Conduct a comprehensive password audit using your password manager to identify and update reused credentials. Monitor financial accounts and credit reports for fraudulent activity. Consider freezing credit if personal information was exposed. Document the incident timeline and affected systems for potential regulatory reporting requirements.



Security password guide: Expert methods to protect your digital identity
Password security stands as your first line of defense against cyber threats. A comprehensive approach combines strong password creation, encrypted storage through password managers, and multi-factor authentication to counter increasingly sophisticated attacks targeting your digital identity.

We're excited to share that Passwork's customer support has been recognized as the best in the Password Managers category by Software Advice. This award is based on real customer reviews and serves as an objective indicator of our product and service quality — we don't just answer questions, we help clients solve their challenges effectively.
What customers say about us
There are many reviews available across multiple platforms, and here are some of them.
"Clients highlight our responsiveness, deep expertise, and willingness to help even in non-standard situations. Excellent support during the testing and implementation phase, as well as very responsive managers who quickly and flexibly helped resolve all organizational issues." — Information security officer
Passwork has improved the internal security at the Melle city administration by creating a reliable system for password management:
"I ran into some minor difficulties after migrating to Passwork 7, but the support team literally walked me through the entire process. Within a day at most, I received answers to all my questions. Perfect. No issues. I'm very satisfied." — System administrator
Through careful evaluation and a security-focused implementation strategy, the deployment proceeded smoothly. A tailored onboarding approach drove high user adoption.
About the platform
Software Advice is an international platform for discovering and comparing IT solutions for businesses. It's part of Gartner Digital Markets, alongside GetApp and Capterra, which recognized Passwork with the Best Ease of Use 2025 award in the password management category by Capterra, a leading software review platform.
At Passwork, we believe cybersecurity should feel manageable, not overwhelming. Our expert support team and managers work closely with you, offering fast responses, practical guidance, and personal assistance whenever you need it.
Customer trust and honest feedback play a key role in how we improve and develop Passwork.


Passwork wins Best Customer Support 2026 from Software Advice
We're excited to share that Passwork's customer support has been recognized as the best in the Password Managers category by Software Advice.
The new releases introduce restrictive settings for User vaults (including the option to block adding new users and groups), smooth appearance switching, and other improvements and fixes.
Restrictions for User vaults
We've added a new block of additional restrictive settings for User vaults in the Vaults settings, allowing administrators to centrally permit or restrict the following actions for all user vaults (private and shared):
- Adding users and groups
- Sending passwords
- Creating password links
- Creating password shortcuts
The restrictions do not apply to Company vaults and are automatically enforced on all existing and new User vaults.
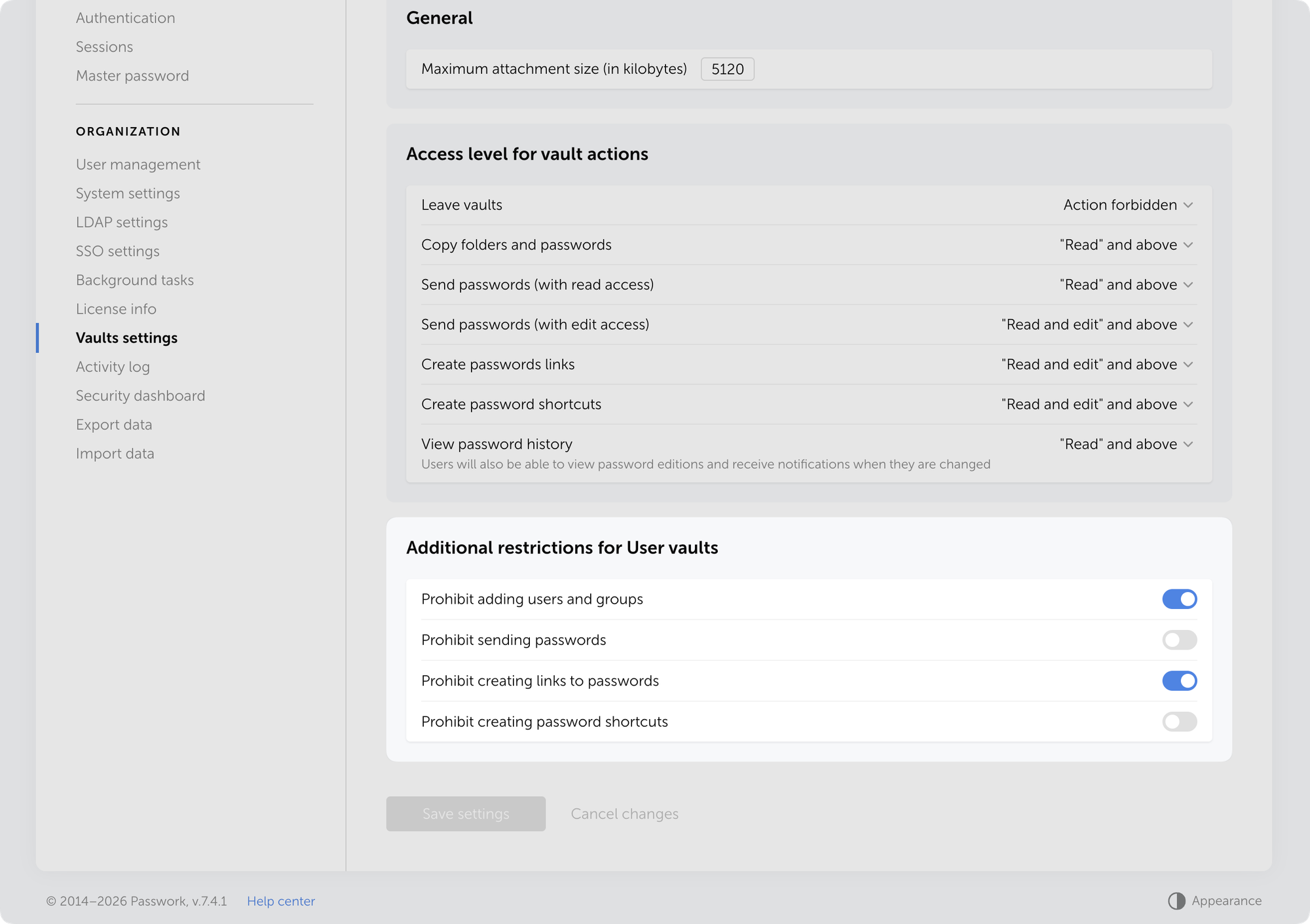
Additional restriction settings for user vaults are located in Settings and users → Vaults settings → Settings tab.
New restrictions solve three security problems:
- Lower breach risk — Blocking link creation and password sending from User vaults prevents accidental or intentional data leaks outside the organization.
- Centralized policy management — Administrators control actions at the platform level rather than relying on employee discipline.
- Stronger control over data distribution — Prevent unmonitored password sharing through personal vaults. Critical for organizations with strict security requirements.
Use cases
Three common cases where additional restrictions for User vaults resolve specific security challenges:
Prohibiting password sharing from Personal vaults
- Problem: Employees store corporate passwords in personal vaults and share them directly with colleagues, bypassing company vaults.
- Solution: Enable all four restrictions. Employees can store passwords in personal vaults but cannot share them — sharing requires Company vaults with controlled access.
Prohibiting link creation for external contractors
- Problem: Employees create temporary password links from personal vaults and send them to external contractors, creating leak risks.
- Solution: Enable "Prohibit creating password links." Links can only be created from Company vaults, where administrators control expiration time and access rights.
Preventing corporate password duplication
- Problem: Employees copy passwords from Company vaults to their personal ones, create shortcuts, and then share them with colleagues. As a result, the same credentials are stored in multiple locations, and when a password is changed in the Company vault, outdated copies remain in personal storage.
- Solution: Enable the restrictions "Prohibit creating password shortcuts" and "Prohibit adding users and groups." This will force employees to work directly with Company vaults, where passwords are always up to date, and the administrator controls their lifecycle and change history.
Other changes
- Added visual indicators informing users about the mandatory email confirmation in order to receive notifications
- Added dynamic list loading for the user filter in the Security dashboard
- Added smooth transition when switching appearance
- Added automatic setting of the Read value in the Access field when sending a password to another user
- Fixed an issue where users couldn't confirm their email addresses when the master password wasn't saved in the browser
- Fixed an issue where, after resetting access in User management, an incorrect access level was displayed until the page was reloaded
- Fixed an issue where the list of inbox passwords wasn't displayed correctly after enabling the "Search only in Inbox" checkbox with an empty search query
- Fixed an issue where XML files from KeePass could not be imported if they contained folders with names consisting only of digits
- Made minor UI and localization improvements


Passwork 7.4 and 7.4.1 releases
The new version introduces restrictive settings for User vaults, including the option which blocks adding new users and groups, adds smooth appearance switching, and other improvements and fixes.

The new version adds a resizable note field, enhanced event descriptions in Action log, and several other improvements and bug fixes.
Improvements
- Added the capability to resize the Note field when creating and editing entries
- Changed the behavior of the Export data menu item: it now becomes inactive when there is no data to export
- Improved the description of user email confirmation events in the Activity log
Bug fixes
- Fixed an issue where passwords with special characters could be processed incorrectly when saving an LDAP server
- Fixed an issue where search results with an empty search query and no filters applied displayed incorrectly for a specified vault
- Fixed an issue where after exiting search in a selected vault, only folders were displayed while passwords and shortcuts did not load until re-entering the vault
- Fixed an issue where not all passwords were being exported during the data export process
- Fixed an issue where resetting a user's master password incorrectly required permission to manage master password complexity policies
- Fixed an issue where the sign-up form accessed via link returned a 401 error when self-registration was disabled
- Fixed an issue that prevented adding a WebAuthn credential with an empty transports field


Passwork 7.3.2 release
The new version adds a resizable note field, enhanced event descriptions in Action log, and several other improvements and bug fixes.

In the new version, we've added search filtering by current directory and made minor improvements to the import process, localization, and UI. The update is available in the Customer portal.
Search in vault or Inbox
Added an option to limit search to the current vault or Inbox. A checkbox is now available below the search bar that, when enabled, restricts search to the selected area.
Other changes
- Fixed an issue where quickly switching between directories and Recents, Favorites, or Inbox pages could display an incorrect or empty password list
- Fixed an issue where importing files with long notes could cause the process to freeze
- Fixed an issue in MongoDB connection string handling
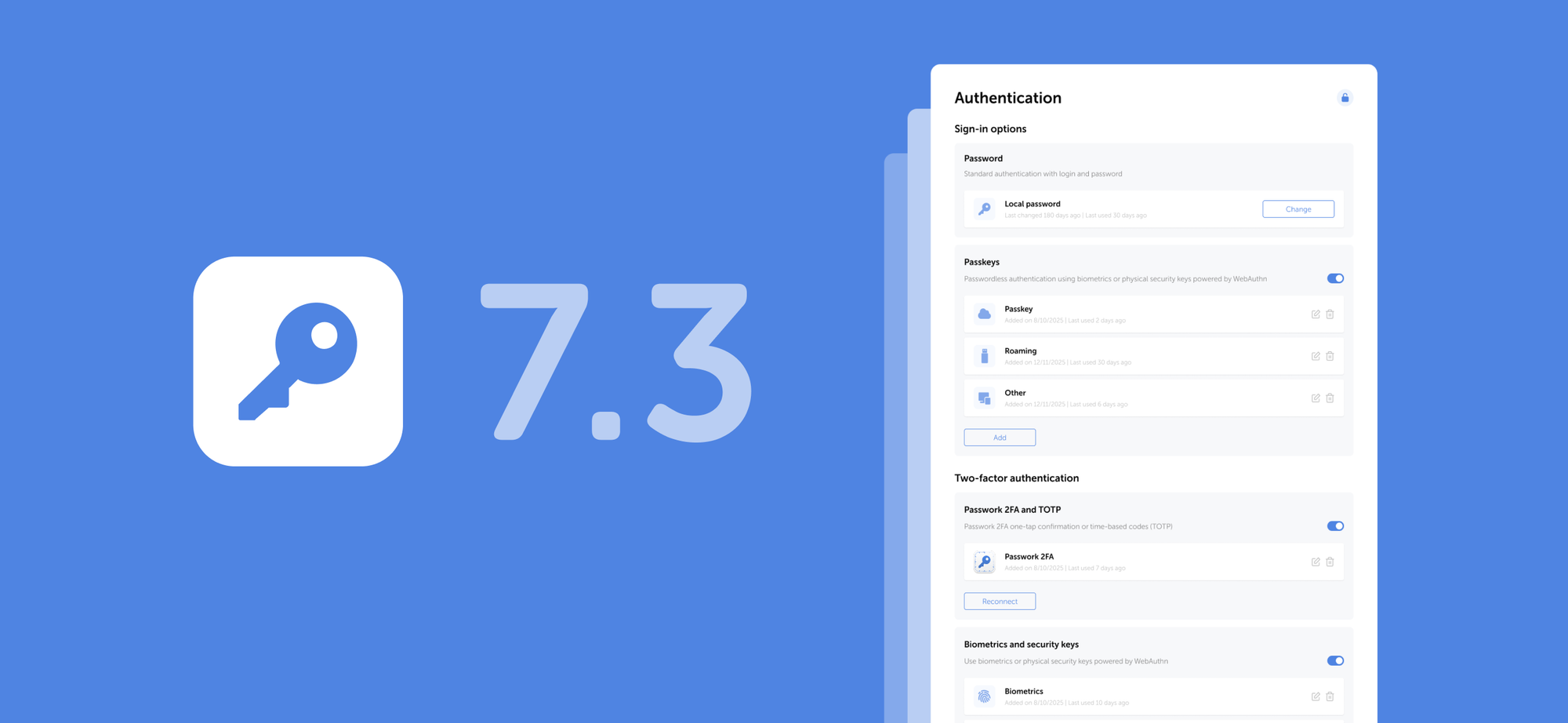


Passwork 7.3.1 release
In the new version, we've added search filtering by current directory and made minor improvements to the import process, localization, and UI. The update is available in the Customer portal.
The new version introduces biometric and passkey authentication, the option to add multiple URLs for a single password, email address verification for users, email-based authentication, and numerous other improvements and fixes.
Biometric authentication and passkeys
We've added support for biometric authentication, passkeys, and security keys based on the WebAuthn standard. You can now sign in to Passwork using your fingerprint, Face ID, PIN code, or a hardware security key (YubiKey and similar devices).
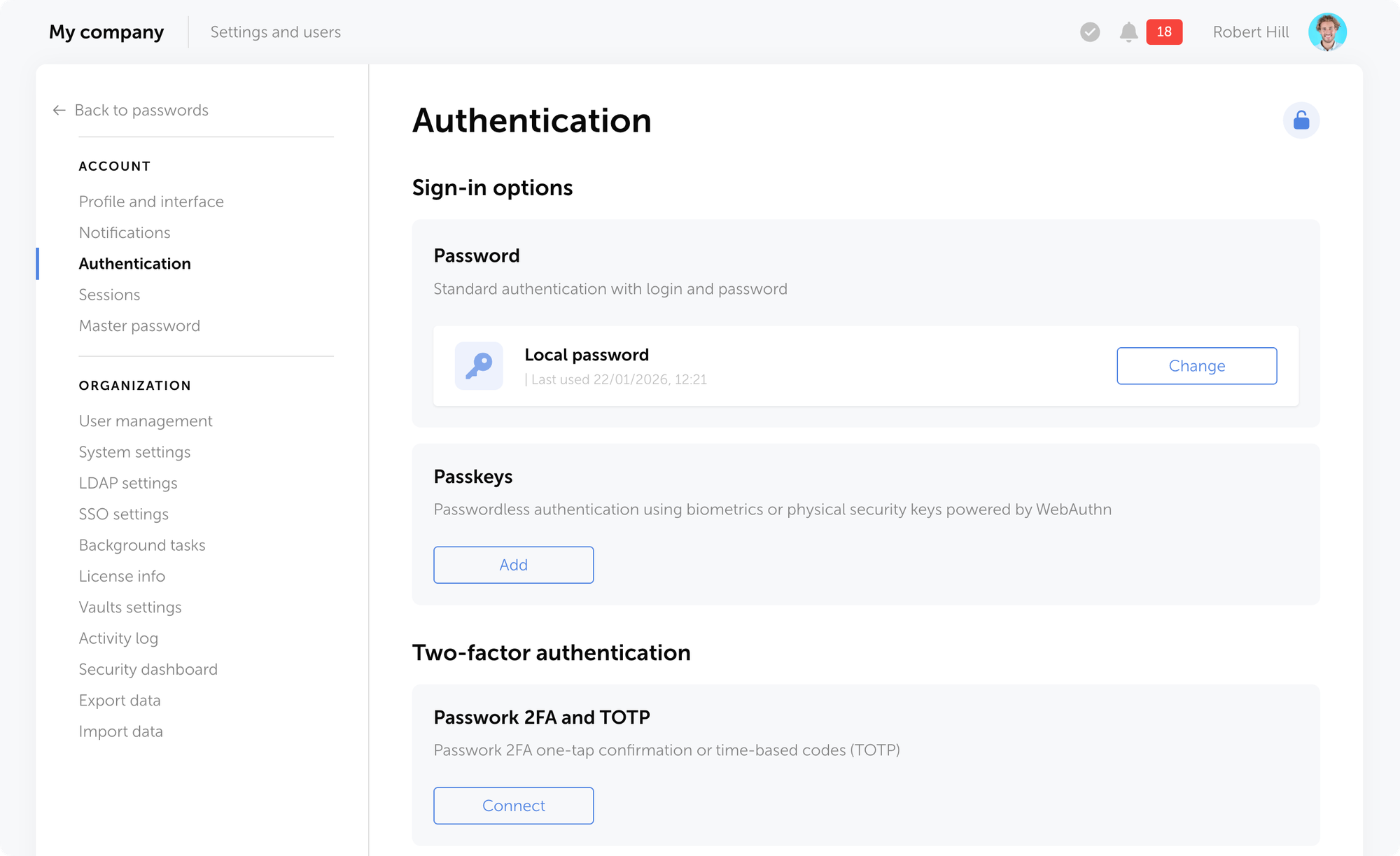
On the Authentication settings page, you can add new sign-in methods, manage existing ones, change your password, or enable passwordless authentication through biometrics or hardware security keys.
The new role setting Use passkey instead of password allows users to authenticate with a passkey instead of their local or domain password.
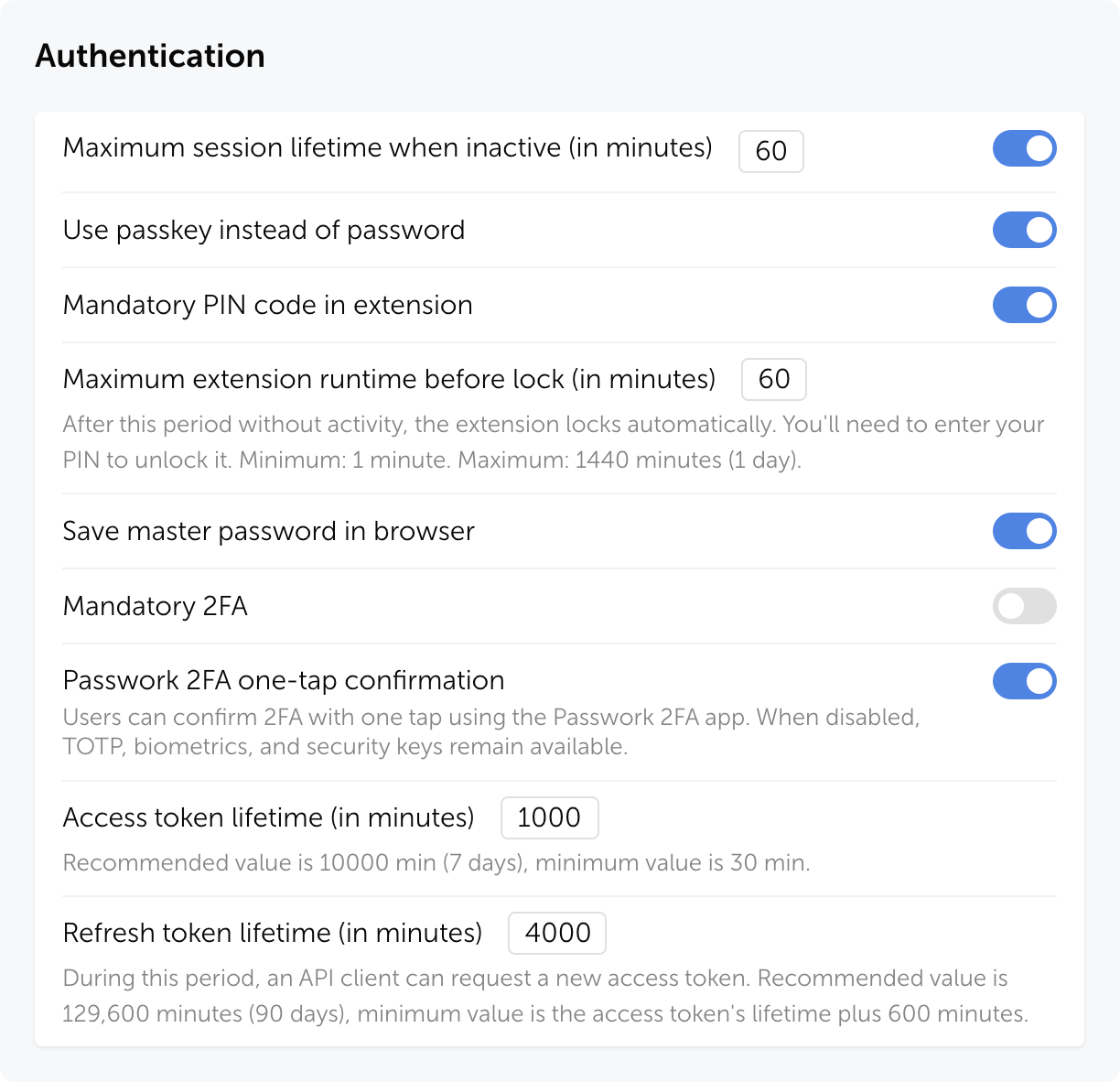
You can reset a passkey for an individual user on their page in the User management section through the Authentication modal window.
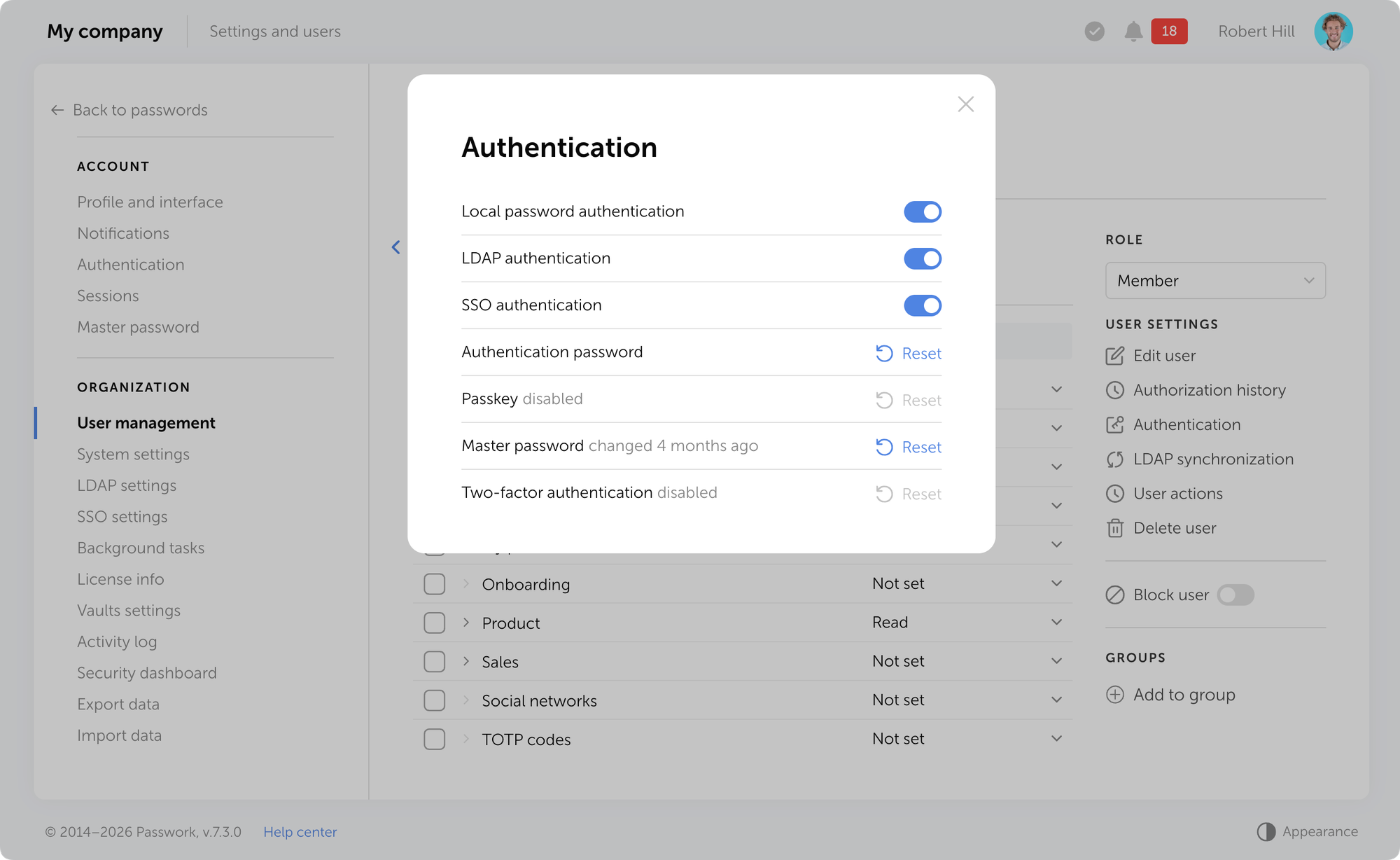
Learn more about authentication methods in our user manual.
Multiple URLs per entry
You can now add multiple URLs to a single entry. This is useful when one account is used to access different addresses: test and production environments, regional versions of a website, or related company services. The browser extension will automatically suggest filling in credentials on any of the specified URLs.
Email verification
Passwork now supports mandatory email verification for users. When a user adds or changes their email address, Passwork sends a verification email with a confirmation link.
You can enable mandatory email confirmation in System settings → Registration → Mandatory email confirmation.
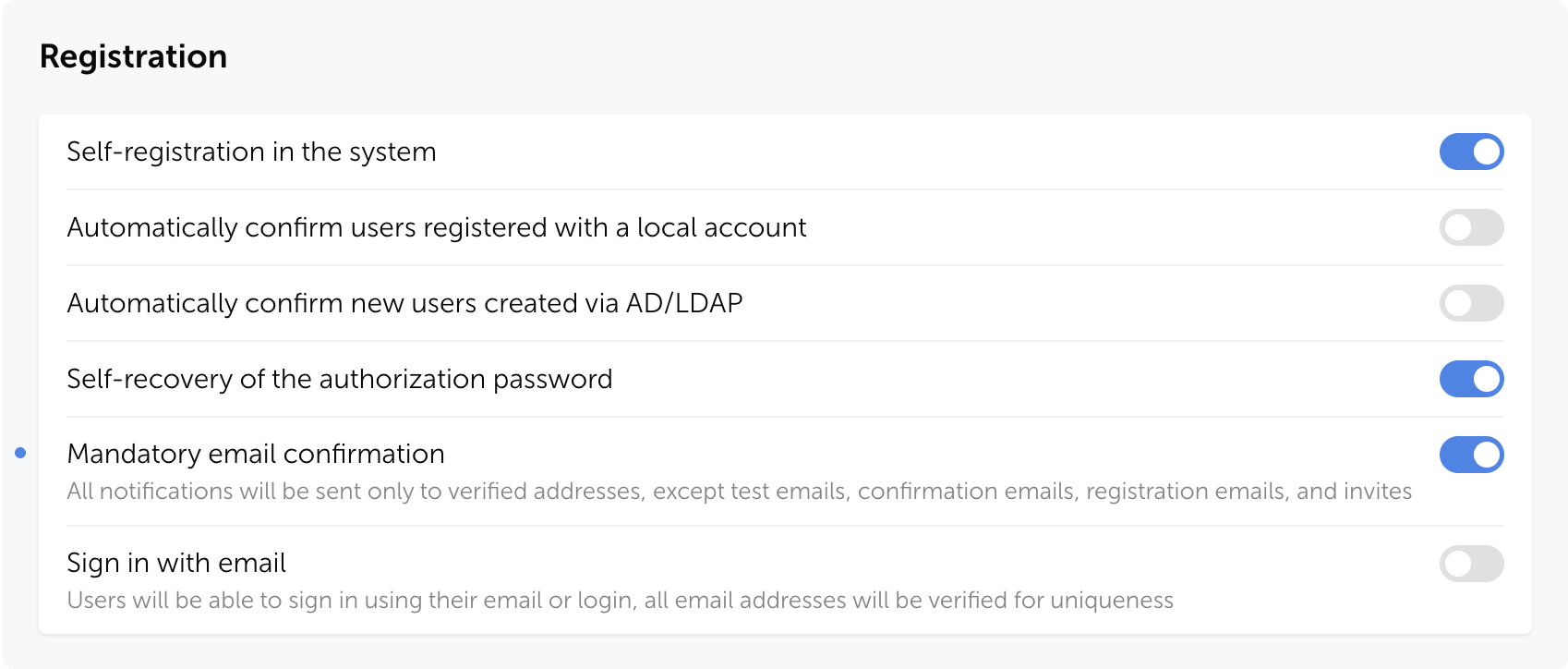
Without email verification, invalid addresses can appear in the system. This can create problems: notifications don't reach users, password reset fails, and security risks emerge. Email confirmation ensures that messages are delivered only to legitimate recipients.
Email-based authentication
We've added the ability to sign in to Passwork using a verified email address instead of a login to simplify authentication and reduce login errors. After enabling this setting, username-based sign-in remains available, and all email addresses will be checked for uniqueness in the system.
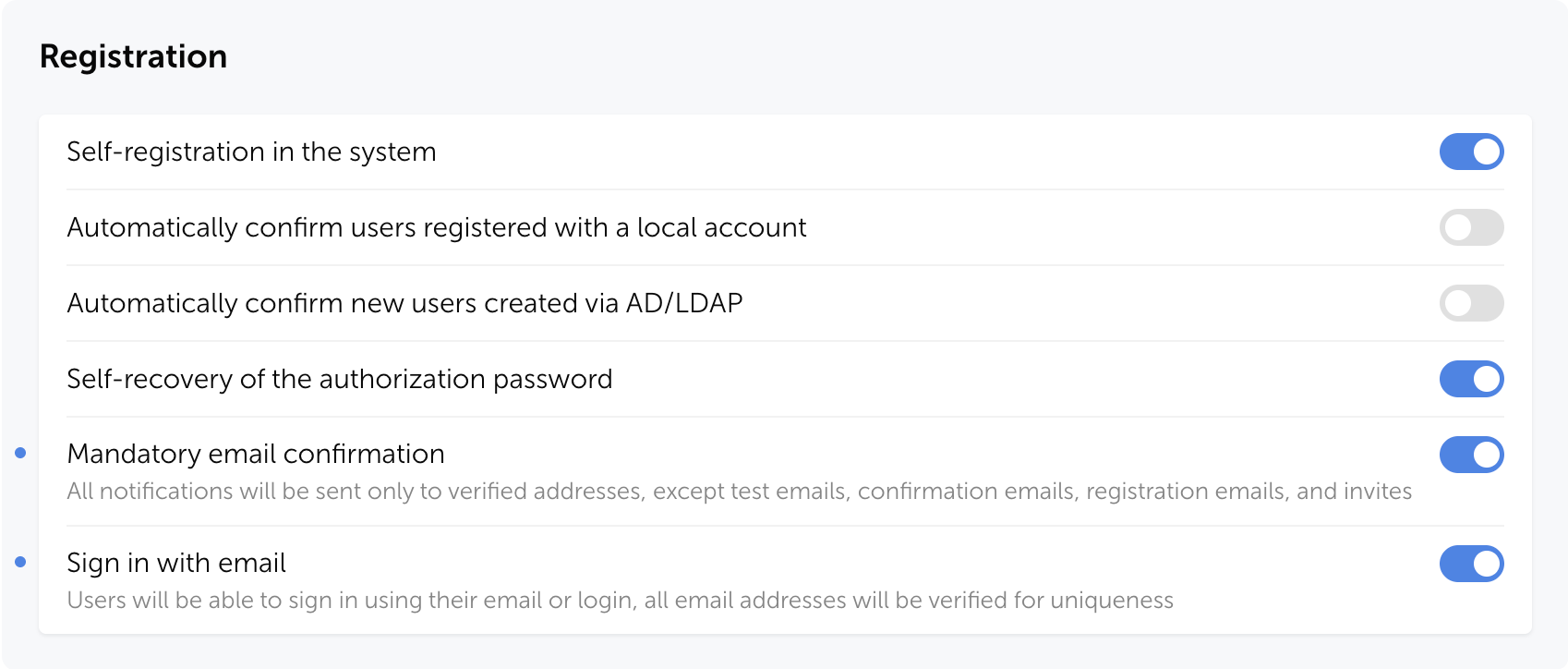
You can enable email-based authentication in Passwork in System settings → Registration→ Sign in with email.
Improvements
- Improved the user filter in the Activity log: search now considers not only the action initiator but also linked users
- Fixed an issue where the folder filter in Security dashboard and Activity log might not include data from nested subfolders when selecting a parent folder
- Added automatic locking of the authentication settings page after 5 minutes of inactivity
- Added an option to set a color for each shortcut individually without changing the color of the initial password
- Added Trusted Proxies support (see documentation for details)
- Made improvements to the UI and localization
Bug fixes
- Fixed an issue where the Edit option in User management was not activated when the "Edit user email" option was enabled in role settings
- Fixed incorrect display of the banner prompting to add a service account on the LDAP server edit page after reloading the page
- Fixed an issue where the Update button in the user edit modal could remain inactive when there were unsaved changes
- Fixed an issue in the setup wizard where an incorrect "Database already exists" message could be displayed on the database connection page
- Fixed an issue where after saving changes in the Vault access or Folder access modal, an incorrect "Discard changes?" message was displayed when attempting to close the window
- Fixed an issue where notifications about failed PIN code entry attempts in the browser extension might not be sent



Passwork 7.3 release
In the new version, we've added support for passkeys and biometrics, an email address verification mechanism for users, the option to specify multiple URLs for a single password, independent shortcut color customization, as well as numerous improvements and fixes.

The city of Melle, a municipality in Lower Saxony with more than 48,000 residents, is recognized for its modern approach to city administration and citizen services. The local government manages a wide range of responsibilities: urban development, education, social care, environmental protection, cultural initiatives, municipal infrastructure, and economic support for the region.
In recent years, Melle has invested heavily in digital transformation, introducing online citizen services, modernizing internal administrative workflows, and improving the technological foundation that supports daily municipal operations. The administration is known for its commitment to transparency, efficiency, and service quality — regularly receiving positive recognition from residents for its well-organized city services and proactive, solutions-oriented governance.
As a city institution, the administration is committed to upholding the highest standards of data protection and operational integrity. The city's IT team continuously seeks to implement modern technologies that streamline workflows, enhance security, and support its employees in their daily tasks. This commitment led them to reevaluate their password management approach, seeking a solution that would meet their security requirements while remaining user-friendly for employees.
Location: Lower Saxony, Germany
Industry: City administration
Company size: 450+ employees
Challenge: Unified password management without security risks

The city administration of Melle recognized a need to improve credential security across employee workflows. Different departments relied on various password management solutions, with most using the one integrated into Microsoft Edge. This resulted in isolated systems with limited central oversight, no visibility into user actions, and inconsistent security standards across the organization.
Beyond security, the IT team wanted to simplify password management for employees. The city administration employs people with varying levels of technical proficiency, so ease of use was just as important as protection.
"That was especially important to us so that we wouldn't have an additional password, another hurdle for people. So really just their Windows password and then the PIN for the browser extension at the end of the day." — Andre Kahlen, system administrator
This meant finding a solution with LDAP support — allowing users to authenticate with their existing Windows credentials and eliminating an additional barrier to adoption. This led the IT team to make a strategic decision to evaluate and introduce a centrally managed, enterprise-grade password management solution.
The main objective was to find a platform that combined three core requirements:
- Security: high security that aligns with strict data protection regulations and internal security policies.
- Usability: exceptional user-friendliness with seamless integration into existing IT infrastructure.
- Control: simple, centralized administration that keeps data accessible while providing fast technical support.
The city of Melle required a service that could unify the workflows across all departments, establish transparent access management, and ensure secure password storage.
Solution: Building a resilient infrastructure

To select a password manager, the IT team conducted a thorough analysis of the available solutions on the market. After careful consideration, they chose Passwork for its security features, granular control, and user-friendly interface — all of which closely matched their criteria.
Passwork's ability to provide centralized control while still offering a secure space for users was beneficial to the IT team. The vault structure was also considered a deciding factor.
"We want to maintain control, since we assign many people, especially those outside of IT, to deal with passwords. One of the advantages of Passwork is centralized management."
This level of control was essential for the municipality, as administrators handle a vast amount of sensitive data and require protection that effectively prevents unauthorized access to confidential information.
The team successfully tested all the declared functions and analyzed database-level security. The decision was based on an intensive three- to four-month testing phase involving about eight members of the IT department. The entire Passwork implementation process, from initial selection to final implementation, took over a year.
Technical Integration

LDAP integration was essential to minimize user friction. After testing, the city administration deployed Passwork within its infrastructure with the following setup:
- LDAP integration for centralized user management based on Active Directory
- The self-hosted solution with an additional instance for employees with heightened security requirements in an isolated network segment
- Snapshot-based and classic backups to ensure data can be quickly restored in case of an incident
"We set up LDAP integration to centrally manage user accounts and permissions, which was highly important. We decided to split the solutions into several instances. Access is heavily restricted this way."
After the successful implementation, the IT team needed to structure the employees' work in the new system.
Organizing work with data in Passwork
The goal was to build a balanced and flexible system that combined control with the freedom of personal information space for employees. The IT team established a clear governance structure:
- Centralized administration — IT admins automatically granted access to all vaults to maintain control
- Personalized training on secure password export and import procedures to ensure safe data migration
- Onboarding sessions for each user during setup to build confidence and ensure smooth adoption
- Clear guidelines on what information belongs in shared organizational vaults and personal vaults
With Passwork, users gained the flexibility to create and organize vaults based on their workflow requirements.
User onboarding
During the rollout, the IT team discovered that centralized training sessions were ineffective — many employees found it challenging to absorb the information all at once. A new method was chosen instead: a personalized approach intended to encourage users to accept the product, use strong, generated passwords, share credentials securely, and learn to use Passwork effectively.
"Passwork adoption is getting very good: employees are taking to new features easily. There is a personal briefing for every user we set up. This also covers security requirements and guides how to effectively utilize the tool. Employees are already organizing their space to fit their structure, thinking about how to design vaults."
Staff always have access to user instructions, and the IT department provides ongoing support to address any questions that arise.
Result: Security and efficiency in workflows

After more than a year in use, the City of Melle remains highly satisfied with Passwork. The solution is actively used by office employees today. The following points were highlighted as particularly positive.
Unified secure space for data storage
The municipality has abandoned browser-based solutions: all passwords are now stored in a secure system with multi-level encryption. Access to them is strictly controlled and logged — this helps prevent leaks and enables incident investigation if necessary.
Positive user acceptance
Many employees have embraced the tool and are proactively thinking about how to structure organizational vaults.
Reliable customer support
The Passwork support team played an important role in the successful implementation and upgrade from version 6 to the recently released Passwork 7.
"Customer support has been excellent so far with its fast responses. I always have answers to my questions, always with the right scripts included or the right syntax I needed to enter, everything already prepared. Perfect."
The City of Melle plans to continue rolling out Passwork until all users are successfully onboarded. The IT team has begun systematically gathering feature requests to refine the system to meet the specific requirements of the city administration's IT infrastructure and to ensure it aligns with their operational needs.
Conclusion

Passwork has improved the internal security at the City of Melle by creating a reliable system for password management. Through careful evaluation and a security-focused implementation strategy, the deployment proceeded smoothly. A tailored onboarding approach drove high user adoption, while the platform's reliability and responsive technical support solidified its position as an essential tool in daily administrative operations.



The city of Melle: How Passwork сentralized password management

The browser extension is available for Google Chrome, Microsoft Edge, Mozilla Firefox, and Safari.
- Improved recognition and autofill algorithm for simple and multi-step login forms, including TOTP code fields
- Improved local storage security for the extension in Chromium-based browsers
- Fixed an issue where password icons displayed incorrectly when entry names contained Unicode characters
- Fixed vault list display issues that occurred after deleting folders within a vault and returning to the main screen
- Fixed unintended session reset when removing the PIN code in the extension
Browser extension 2.0.30 release
The browser extension is available for Google Chrome, Microsoft Edge, Mozilla Firefox, and Safari.

Password management is the practice of securely creating, storing, organizing, and controlling access to passwords and other authentication credentials. It combines human processes with specialized software tools to ensure that every account uses a strong, unique password without requiring users to memorize them all.
Whether you're an individual trying to secure your online life or an IT administrator protecting your organization's digital assets, understanding password management is essential.
This guide explains everything you need to know: what password management is, why it matters, how it works, and how to implement it effectively. You'll learn about different types of password managers, key features to look for, and best practices that protect you from the most common security threats.
Understanding password management
At its core, password management addresses a fundamental challenge: humans are terrible at creating and remembering secure passwords. We default to predictable patterns, recycle familiar combinations across accounts, and prioritize convenience over security.
Password management systems compensate for these inherent limitations by assuming the cognitive burden and complexity on our behalf. As both a practice and a technology, password management encompasses several key functions:
- Password generation: Creating strong, random passwords that meet security requirements and resist common attack methods like brute force and dictionary attacks.
- Secure storage: Encrypting and storing passwords in a protected vault that only authorized users can access.
- Organization: Categorizing and managing credentials across hundreds of accounts, making them easy to find when needed.
- Access control: Determining who can access which passwords, particularly important in team and enterprise environments.
- Autofill and automation: Automatically entering credentials into login forms, reducing friction while maintaining security.
- Audit trails: Recording who accessed which credentials and when, allowing security teams to detect suspicious activity, investigate incidents, and maintain compliance with regulatory requirements.
Password management has evolved from rudimentary practices to sophisticated security infrastructure. The first generation of digital password managers introduced basic encryption (like Blowfish algorithm) and centralized storage, addressing immediate security gaps but lacking the granular controls enterprises required.
Modern password management systems represent a fundamental shift: they combine military-grade encryption, zero-knowledge architecture, role-based access controls, and comprehensive audit capabilities. Today's solutions enforce security policies, detect anomalies, integrate with existing infrastructure, and provide the visibility organizations need to maintain compliance and respond to threats in real time.
Why is password management important?

According to Verizon's 2025 Data Breach Investigations Report, stolen credentials served as the initial access vector in 22% of all confirmed breaches, with that figure jumping to 88% for basic web application attacks.
In the first half of 2025 alone, over 8,000 global data breaches exposed approximately 345 million records, demonstrating the persistent and catastrophic scale of credential-based attacks. Behind these statistics lies a fundamental incompatibility between human cognition and modern security demands.
The human factor
Our brains simply weren't designed for this pace of information. Psychological research shows that humans can reliably remember only 7±2 pieces of data in working memory. Yet we're expected to manage hundreds of unique, complex passwords — each a random string of uppercase letters, lowercase letters, numbers, and symbols.
Faced with this impossible task, people develop coping mechanisms that undermine security:
- Predictable patterns: Adding "123" or "!" to meet complexity requirements.
- Password reuse: Over 60% of people reuse passwords across multiple accounts.
- Writing passwords down: Sticky notes on monitors remain surprisingly common.
- Simple passwords: "password," "123456," and "qwerty" still rank among the most common passwords globally.
This behavior isn't laziness. It's a rational response to an overwhelming cognitive burden. Password fatigue is real, and it leads to security shortcuts.
The consequences of poor password hygiene
When password security fails, the consequences cascade:
- For individuals: Identity theft, financial fraud, privacy violations, and the time-consuming process of recovering compromised accounts. The average victim of identity theft spends 200 hours resolving the issue.
- For businesses: Data breaches cost an average of $4.44 million per incident, according to IBM's Cost of a Data Breach Report. Beyond direct financial losses, organizations face regulatory fines, legal liability, reputational damage, and loss of customer trust.
- For IT teams: Password-related help desk tickets consume 20-50% of IT support resources in typical organizations. Every "forgot password" request represents time that could be spent on strategic initiatives.
The benefits of effective password management
Implementing proper password management delivers measurable improvements:
- Enhanced security: Unique, strong passwords for every account eliminate the domino effect of credential reuse. Even if one password is compromised, your other accounts remain secure.
- Reduced cognitive load: You remember one master password instead of hundreds. The mental relief is immediate and significant.
- Time savings: Autofill eliminates the minutes spent typing or resetting passwords. For organizations, this translates to thousands of hours of productivity annually.
- Compliance support: Many regulations (GDPR, HIPAA, SOC 2) require organizations to demonstrate proper credential management. Password managers provide the audit trails and controls needed for compliance.
- Improved user experience: Seamless access to accounts without the friction of password resets or account lockouts.
How does password management work?
Understanding the mechanics of password management helps you appreciate both its security and its usability. Modern password managers balance strong encryption with user-friendly access.
The master password concept
Everything starts with your master password — the single password you need to remember. This password unlocks your encrypted vault containing all your other credentials.
Many users create master passwords using passphrases, random words strung together like correct-horse-battery-staple, which are both secure and memorable.
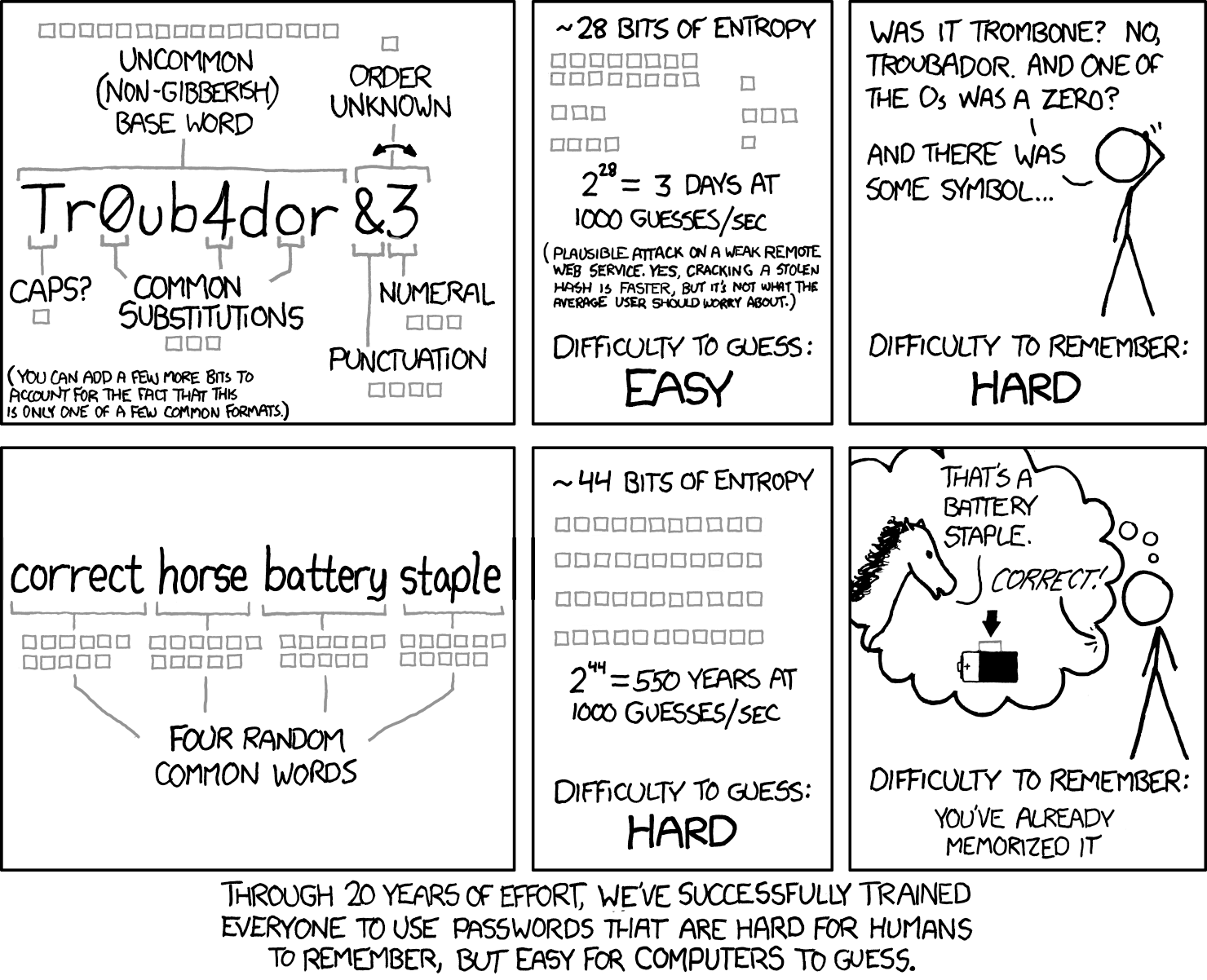
The XKCD comic that popularized this concept demonstrated a crucial insight: four or five random common words create more entropy (randomness) than a shorter complex password, while being far easier to remember.
The encrypted vault
Your password vault is an encrypted database that stores all your credentials, notes, and other sensitive information. Modern password managers use AES-256 encryption, the same standard used by governments and militaries worldwide.
Here's what makes it secure:
- Encryption at rest: Your data is encrypted before it leaves your device. Even the password manager company cannot read your vault contents.
- Zero-knowledge architecture: The service provider never has access to your master password or unencrypted data. If their servers are breached, your passwords remain protected.
- Encryption in transit: When syncing across devices, your encrypted vault travels through secure channels (TLS/SSL), adding another layer of protection.
The user journey
Here's how password management works in practice:
- Initial setup: You create your master password, set up your account and security settings — multi-factor authentication, access controls, and vault parameters.
- Adding passwords: As you log into existing accounts, the password manager detects login forms and offers to save your credentials. You can also manually add passwords or import them from browsers or other password managers.
- Password generation: When creating new accounts, the password manager generates strong, random passwords according to the site's requirements. You never need to think about password creation again.
- Autofill: When you visit a login page, the password manager recognizes the site and offers to fill in your credentials. One click, and you're logged in.
- Syncing: Your encrypted vault syncs across all your devices — phone, tablet, laptop, desktop. Changes made on one device appear everywhere.
- Secure sharing: When you need to share credentials with family members or team members, the password manager encrypts and transmits them securely, without exposing them in plain text.
Types of password managers

Password managers vary significantly in architecture, security model, and deployment options. Understanding these differences is essential for selecting the right solution.
Browser-based password managers
Built into web browsers like Chrome, Firefox, Safari, and Edge, these password managers offer basic functionality without additional software.
Pros:
- Free and immediately available
- Seamless integration with the browser
- Automatic syncing across devices using the same browser
- No learning curve
Cons:
- Limited to browser-only passwords
- Basic security features compared to dedicated solutions
- Vulnerable if browser account is compromised
- Limited sharing capabilities
- Inconsistent cross-browser functionality
Best for: Casual users with simple needs who primarily use one browser ecosystem.
Standalone password managers
These applications store your encrypted password vault locally on your device rather than in the cloud. Designed for individual use, they prioritize local control over multi-device convenience.
Pros:
- Complete control over your data
- No reliance on cloud services
- Works offline
- Maximum privacy
Cons:
- Manual syncing across devices
- Risk of data loss if device fails without backups
- Less convenient for multi-device users
- Requires more technical knowledge
Best for: Privacy-conscious users, those with limited internet connectivity, or anyone who prefers local data storage.
Cloud-based password managers
The most popular category, these services store your encrypted vault on their servers and sync it across all your devices.
Pros:
- Seamless syncing across unlimited devices
- Accessible from anywhere with internet
- Automatic backups
- Rich feature sets (sharing, auditing, breach monitoring)
- User-friendly interfaces
- Mobile apps with biometric authentication
Cons:
- Requires trust in the service provider
- Subscription costs for premium features
- Dependent on internet connectivity
- Potential target for attackers (though encryption protects data)
Best for: Most individual users, families, and small teams who want convenience and comprehensive features.
Enterprise password managers
Designed for organizations, these solutions add administrative controls, compliance features, integration with corporate systems and are deployed on-premise. This architecture eliminates dependencies on external providers. You define the security perimeter, manage access controls, and maintain complete operational independence.
Pros:
- Complete data sovereignty
- Zero external dependencies or cloud service providers
- Automatic compliance with data residency regulations
- Integration with Active Directory, LDAP, and SSO systems
- Centralized administration with granular policy enforcement
- Role-based access controls and privileged access management
- Comprehensive audit logs and compliance reporting
- Automated onboarding/offboarding workflows
- Protection from provider-side security incidents
Cons:
- Higher upfront infrastructure and licensing costs
- More complex setup and administration
- May require IT expertise
- Organization manages backups and disaster recovery
Best for: Businesses of all sizes, IT teams managing shared credentials, organizations with compliance requirements.
Key features of password managers
Modern password managers offer far more than basic password storage. Understanding these features helps you evaluate solutions and maximize their value.
Core features
- Password generation: Creates strong, random passwords based on customizable criteria (length, character types, symbol inclusion). The best generators create passwords that resist brute force attacks for centuries.
- Secure storage: Encrypted vault for passwords, with many managers also storing secure notes, credit card information, identity documents, and other sensitive data.
- Autofill: Automatically detects login forms and fills credentials with one click or tap. Advanced autofill distinguishes between similar sites to prevent phishing attacks.
- Cross-platform syncing: Keeps your vault synchronized across Windows, macOS, Linux, iOS, Android, and web browsers.
- Browser extensions: Integrations for Chrome, Firefox, Safari, Edge, and other browsers that enable autofill and password capture.
- Mobile apps: Full-featured applications for smartphones and tablets, often with biometric authentication.
Security features
- Multi-factor authentication (MFA): Adds a second verification step beyond your master password. Options include authenticator apps (TOTP), SMS codes, hardware keys (YubiKey), or biometric verification.
- Biometric authentication: Unlock your vault using fingerprint, face recognition, or other biometric methods on supported devices.
- Security dashboard: Analyzes your passwords and identifies:
- Weak passwords that don't meet security standards
- Reused passwords across multiple accounts
- Old passwords that haven't been changed recently
- Zero-knowledge architecture: Ensures that even the password manager company cannot access your unencrypted data.
- Emergency access: Designates trusted contacts who can access your vault after a waiting period if you become incapacitated.
Sharing and collaboration features
- Secure sharing: Share individual passwords or entire folders with family members or team members without exposing passwords in plain text.
- Team accounts: Organize passwords by department, project, or access level with role-based permissions.
- Access controls: Define who can view, use, or modify specific passwords.
- Sharing history: Track when passwords were shared, accessed, or modified.
Advanced features
- Password history: Maintains previous versions of passwords, allowing you to revert if needed.
- Secure notes: Store sensitive information beyond passwords — software licenses, WiFi credentials, server details, recovery codes.
- File attachments: Attach encrypted files to vault items (contracts, certificates, documents).
- API access: For developers and power users, programmatic access to the password manager.
- CLI tools: Command-line interfaces for integrating password management into development workflows.
- Audit logs: Detailed records of all vault activities for security monitoring and compliance.
Password management best practices

Having a password manager is only the first step. Following these best practices ensures you're using it effectively and securely.
1. Create an unbreakable master password
Your master password is the single point of failure for your entire password security. Make it count:
- Use at least 16 characters (longer is better)
- Combine random words into a memorable passphrase
- Avoid personal information (names, dates, addresses)
- Never reuse a password you've used anywhere else
2. Enable multi-factor authentication
Add a second layer of security to your password manager account. Even if someone discovers your master password, they can't access your vault without the second factor. Authenticator apps (Passwork 2FA, Google Authenticator, Authy) are more secure than SMS codes. Hardware security keys (YubiKey) offer the strongest protection.
3. Use unique passwords for every account
This is the fundamental rule of password security. Your password manager makes it effortless — let it generate a unique password for each account. If one site is breached, your other accounts remain secure.
4. Generate long, complex passwords
When creating passwords, maximize length and complexity:
- Aim for 16-20 characters minimum
- Use all character types (uppercase, lowercase, numbers, symbols)
- Let the password manager generate them randomly
5. Conduct regular password audits
Schedule quarterly reviews using your password manager's security dashboard:
- Update weak passwords
- Eliminate reused passwords
- Change old passwords (especially for critical accounts)
- Remove passwords for accounts you no longer use
6. Respond immediately to breach alerts
When your password manager notifies you of a compromised password, change it immediately. Don't wait, breached credentials are often exploited within hours.
7. Organize your vault thoughtfully
Create a logical structure:
- Use folders or tags to categorize passwords (Work, Personal, Finance, etc.)
- Add notes to passwords with security questions, account numbers, or other relevant information
- Mark critical accounts for easy identification
8. Back up your vault regularly
While cloud-based password managers handle backups automatically, consider:
- Exporting an encrypted backup periodically
- Storing the backup in a separate secure location
- Testing your backup to ensure it works
9. Set up emergency access
Designate a trusted person who can access your vault if something happens to you. Most password managers offer emergency access features with configurable waiting periods.
10. Use secure sharing features
When sharing passwords with team members:
- Use the password manager's built-in sharing features
- Never send passwords via email, text, or messaging apps
- Revoke access immediately when no longer needed
- Regularly review who has access to shared passwords
11. Keep your password manager updated
Enable automatic updates to ensure you have the latest security patches and features. This applies to browser extensions, mobile apps, and desktop applications.
12. Avoid common mistakes
- Don't store your master password in your vault (circular dependency)
- Don't share your master password with anyone, ever
- Don't use password manager autofill on public or shared computers
- Don't ignore security warnings from your password manager
- Don't assume you're completely secure — stay vigilant
Frequently Asked Questions

Are password managers safe?
Yes, when properly implemented, password managers are significantly safer than the alternatives (reusing passwords, writing them down, or using weak passwords). They use military-grade AES-256 encryption and zero-knowledge architecture, meaning even the password manager company cannot access your unencrypted data. While no system is 100% invulnerable, password managers have proven track records and are recommended by security experts, including the NSA and CISA.
Can password managers be hacked?
While password managers can theoretically be targeted by attackers, successful attacks are extremely rare and typically require sophisticated techniques. The encryption used is virtually unbreakable with current technology. Most "password manager breaches" you hear about involve compromised user accounts (weak master passwords, no MFA) rather than flaws in the password manager itself. Using a strong master password and enabling multi-factor authentication makes your password manager highly resistant to attacks.
Should I use a free or paid password manager?
Free password managers provide adequate security for basic needs. Paid password managers offer additional features like advanced sharing, priority support, dark web monitoring, and more storage. For individuals, free options are often sufficient. For families and businesses, paid plans provide better collaboration tools and administrative controls. The most important factor is choosing a reputable password manager and using it consistently, regardless of whether it's free or paid.
Can I share passwords safely with family or team members?
Yes, modern password managers include secure sharing features that encrypt passwords before transmission. You can share individual passwords or entire folders with specific people, and you can revoke access at any time. This is far safer than sending passwords via email, text, or messaging apps. Family plans typically allow each person to have their own vault plus shared family folders. Business plans offer more granular permission controls.
Do I need a password manager if I use two-factor authentication?
Yes. Two-factor authentication (2FA) and password managers serve complementary purposes. 2FA adds a second verification step beyond your password, providing protection even if your password is compromised. However, you still need strong, unique passwords for each account — which is what password managers provide. In fact, many password managers can also store and autofill 2FA codes, making the combination even more convenient.
Can I use a password manager on public or shared computers?
It's generally not recommended to use your password manager on public computers (libraries, internet cafes) or shared computers (hotel business centers) due to the risk of keyloggers or other malware. If you must access accounts from a public computer, use your password manager's web vault in a private/incognito browser window, log out completely when finished, and change your master password afterward.
Conclusion
Password management isn't optional anymore — it's essential infrastructure for digital life. The average person manages hundreds of accounts, each requiring secure authentication. Trying to remember unique, strong passwords for every account is impossible, and the alternatives — password reuse, weak passwords, or written notes — create serious security vulnerabilities.
Password managers solve this problem. They generate strong passwords, store them securely with military-grade encryption, and autofill them when needed. You remember one master password; the password manager handles everything else.
The benefits extend beyond security. Password managers save time, reduce frustration, improve productivity, and support compliance requirements. For businesses, they reduce help desk burden and protect against the costly consequences of data breaches.
With on-premise deployment at its core, Passwork ensures complete data ownership, zero-knowledge encryption, and compliance with industry regulations — backed by ISO 27001 certification.
Further reading