With iCloud, you can recover data from any iOS device in just seven steps.

Although Apple products are known for their high performance and durability, problems with your iPhone, iPad, or Apple Watch can arise at any time. Fortunately, backing up Apple devices to iCloud is simple. However, just like with the best data recovery tools, you'll need to know how to restore a backup from iCloud in case something goes wrong.
We have thus provided these seven simple steps to help you reset your iOS device using an iCloud backup. Although iCloud is one of the better cloud storage options as one can open it in a new tab, it has one significant drawback: you must wipe your device completely before uploading a backup. If you require a fix for this problem, skip to step 7 of this article.
How to restore an iCloud backup: Setting up
Before restoring a device, you must configure iCloud's backup feature because there won't be anything to restore otherwise.
You must configure the iCloud backup before you may restore your iOS device from a backup. The best time to do this is when you first set up your device, but you can do it whenever you choose.
Go to the Settings app and tap on your name at the top to get started. Then, select "iCloud" and then "Backup" from the list. Ensure that "Backup" is turned on. iCloud will automatically back up your data when your device is locked, plugged in, and connected to WiFi after backup has been enabled.
To manually initiate an iCloud backup, go to Settings > iCloud > Backup and press "Back Up Now." Your Apple device can always be reset to the most recent iCloud backup if you encounter a technical problem or need to recover lost data.
Remember that the complimentary iCloud account that comes with your Apple ID only offers 5GB of storage space. The majority of Apple’s products have much more internal capacity than that. For instance, the iPhone 13 has at least 128GB of internal storage.
Consider eliminating any unnecessary files or upgrading to iCloud+, which starts at $0.99 per month for 50GB of storage, if you try to backup your smartphone to iCloud and discover that your iCloud storage is full.
Step 1: Get ready for a factory reset on your device
You must carry out a factory reset prior to restoring your device from a backup using the standard Apple procedure. This implies that you must delete all of the content that is currently on your device. You can work around this by utilising third-party software if you don't want to perform a reset. To learn how to restore from a backup using third-party software, skip to step 7.
Examine your notes, files, images, and any other apps you think may contain crucial information. After you complete the reset, anything that was added since your most recent backup will be irretrievably gone.
Step 1b (Optional): Disconnect your gadget (Apple Watch only)
Resetting an Apple Watch entails an extra step.
You must unpair your Apple Watch from your iPhone as a separate step before moving on to step 2 if you're resetting an Apple Watch.
Open the Apple Watch app on your iPhone and go to My Watch > All Watches to get started. To unpair an Apple Watch, tap the details button next to the watch you wish to do so. The system will prompt you to decide whether to keep or cancel your mobile plan. Keep it, because you will soon restore it from a backup.
Before continuing to the next step, tap once more to confirm, then enter your Apple ID password to finish the unpairing procedure.
Step 2: Reset your device
Go to Settings > General > Transfer or Reset [Device] once you are certain that nothing crucial will be lost. To start the factory reset, tap "Erase All Content and Settings" after that. You will now be required to enter your Apple ID password or device passcode.
Wait for the reset to finish after entering the passcode. Depending on how much stuff is already on your device, this can take a while. When you see the ‘Hello’ screen from when you first set up your iOS device, you will know the reset was completed.
Step 3: Configure and turn on your gadget
After a reset, you'll need to perform an initial installation once more.
You will need to go through the basic setup procedures the same way you did when you originally acquired your device because your iOS installation is now essentially brand new. Tap the ‘Hello’ screen to get started, then select your language.
To configure your device and connect it to the internet via WiFi or cellular data, simply follow the onscreen instructions. Set up your passcode, Face ID, and Touch ID lastly. Not all Apple devices will have all of these functions, so keep that in mind. You are currently prepared to restore your iCloud backup.
Step 4: Restore iCloud
You will have a number of options to restore your data on the following screen. "Restore from iCloud Backup" is the first choice; tap it. iCloud will now ask you to log in with your Apple ID.
You will get a list of available backups after logging in. Unless you want to backdate your device to a certain day and time, pick the most recent. iOS might be telling you that you need to execute an upgrade right now. If this happens, let the update finish installing before trying to restore your device.
Your files, notes, and photographs will all be restored at this time. Restoring your apps is the subsequent step.
Step 5: Restore your apps
Once you're logged in, restoring previously purchased apps is simple:
Log in with your Apple ID to recover apps that have been purchased. While your device downloads all of the apps linked to that ID, stay connected to WiFi. If you have several Apple IDs, sign into each one separately and wait for the corresponding apps to download.
Depending on how many apps you have, this stage may take some time, so be prepared to wait.
Step 6: Finish the setup procedure
There are a few last-minute adjustments to do before your device is ready for use, once you have finished restoring your data and applications. To continue configuring your iOS device, follow the on-screen instructions.
You will be prompted to choose whether you want iOS upgrades to launch automatically or manually as well as if you want to share data with Apple for development purposes.
Additionally, you'll be prompted to configure default features like Screen Time, Apple Pay, and Siri. Once you've finished, a big congratulations is in order! Your iOS device has been fully restored from an iCloud backup.
Step 7 (Optional): Restore your smartphone using third-party software without performing a reset
Using an iCloud backup to restore your iOS device can be a laborious and time-consuming operation. It can take hours to perform a factory reset, download the backup, download your apps again, and, possibly, re-update iOS.
Going through the entire reset and restore process can be a major inconvenience if you just lost a tiny amount of data, such as a single image or a few texts. Fortunately, certain third-party applications, like EaseUS and MobiMover, let you selectively restore a small amount of data from an iCloud backup file without performing a complete reset.
Download the reset program of your choice to get started. Keep in mind that the majority of third-party reset software is not free, but it does provide a free trial that allows only you to download a certain amount of data. If this is an isolated incident, you can recover a few files using the trial at no cost.
How to recover an iCloud backup: Synopsis
You now understand how to backup an iOS device to iCloud and restore your device using that backup. One of the numerous advantages of this robust cloud storage service is the ability to use iCloud to backup your gadgets.
How to recover an iCloud backup

Every day, people all over the world are spending more and more of their waking hours online. In addition, we're increasingly using our mobile devices for much of our internet activity. The banking industry is unquestionably following suit.
More than seventy percent of Americans conduct some or all of their banking transactions online. Mobile devices now account for more than half of all website traffic, and financial institutions are not far behind.
How safe is mobile banking?
Of course, popular things aren't always safe. Passwords are a prime example. Convenience is a major factor in the migration to the online world and mobile banking. Many people simply accept the new reality without weighing up the pros and cons.
In this article, we'll look at the dangers of mobile banking and what you can do to keep your information safe.
Is mobile banking security at risk?
The most secure method when it comes to banking is, without a doubt, in-person endeavours. But, even if you are paranoid about being hacked, you shouldn't abandon convenience because of it. You've already taken the first step in safeguarding yourself if you're aware of the dangers of online and mobile banking, but don’t be paranoid.
If you're using a web browser on your PC or a mobile banking app on your phone, you face the same basic hazards. However, the vulnerabilities of various devices vary. Moreover, different apps necessitate the possession of a diverse range of hacking capabilities.
People who are increasingly relying on their smartphones rather than PCs may want to consider the following:
When it comes to security, is online banking more reliable than mobile banking?
Indeed, this is a valid question. The more detailed response necessitates additional thought. Traditional PCs are still the primary target of most viruses. Hackers must focus on more precise targets than just a web browser in order to target mobile malware, which is rare.
Now that's wonderful news, right? The bad news is that research conducted by security experts on mobile banking apps has revealed that nearly all of them contain at least one vulnerability. The problem is that these are rarely high-level flaws, however, if you're careful, you can escape a lot of trouble.
Keeping your device safe is an important part of exercising caution. While your desktop computer is likely to stay put, your phone is more likely to follow you wherever you go. As a result, it's more likely to end up in the wrong hands. If you’re new to the smartphone era, this is an issue. It's still not a good reason to give up on mobile banking, however.
The best ways to keep your online banking information safe
Are you still unsure of what those safeguards are? We've compiled a list of our top five picks. All except the most serious threats should be covered by these measures. If you're using mobile networks or your home internet, these tools should enable you to keep your activity safe at all times.
Use a VPN
In order to protect your mobile banking, you should use a virtual private network (VPN). Hackers can't see what you're doing if you hide your IP address and avoid internet tracking.
It doesn't matter if you're using public Wi-Fi or not. Public networks, by themselves, are extremely unsafe. A top-rated VPN like ExpressVPN or NordVPN, on the other hand, bring the security of your home internet connection with you wherever and whenever you travel. You can't link your phone data to your online banking activity because there is a virtual barrier between them.
If you’re not willing to sacrifice a bit of extra time for added security, this isn't for you. The convenience of using online banking can be compromised as a result. If you're using a VPN, your bank won’t know that you're trying to get into your own account. There will be an additional stage in the verification of your identity because of this.
Keep your devices safe!
Security risks in online banking aren't always posed by external sources such as the internet. Defending against direct device breaches is the initial step. Keeping your phone in a familiar location and making sure it's safe even if it gets lost is therefore a must!
In other words, the best way to unlock your home screen is by using a pin or facial recognition software. If you don't want apps and websites to save your passwords, you should log out of them and tell them not to do so. You'll have more time to notify your bank if your phone is stolen if you have more security measures in place.
Use only long, complex passwords
The majority of websites demand that you choose a complex password when you set up or update your account. However, you should be aware of the following guidelines:
- Make use of both capital and lowercase letters, digits, and other characters to enhance complexity;
- Never use the same password on more than one website, and make sure it's difficult to decipher. A strong password can be generated with the aid of specialised software.
As a result, most individuals wonder, "How am I supposed to remember so many strong passwords?" We're not counting on you to become a walking, talking, thinking machine. There is a common misconception that you should never write down your passwords. Passwords should be kept secure and separate from the devices on which they are used.
Keeping your online banking password in a separate location from your phone is the best way to keep it safe. Do not reveal what this location is used for.
Installing a password manager, on the other hand, allows you to store unique passwords for each website you visit. After that, all you have to remember is one secure password and the manager may log in on your behalf to all of your other accounts. And remember, that’s what we offer at Passwork.
Check your bank's security practices
Your bank's website should have instructions on how to keep your personal data safe. We strongly suggest that you take the time to read it. Even if you don't comprehend all that they say, you should be able to get an idea of whether or not their methods are secure.
The padlock icon, which indicates that the website is correctly encrypted, is one of the most obvious things to look for. Two-factor authentication is another option that can be used. Even if you don't feel the need for it, you should turn it on just in case. Each time you log in, you must either answer a security question or provide a one-time security code.
Your bank's dedication to security is demonstrated by measures such as these. It's also an indication of how safe their applications are. If your bank doesn't prioritise security, it's time to find a new one. It's likely that a bank that doesn't care about customer service isn't concerned about security either.
Recognize scams and phishing attempts, and avoid them at all costs
No matter how secure your bank is, they will never ask for your account information. This is almost probably a phishing attempt if you receive such a message.
In order to deceive people into disclosing personal information, hackers frequently send emails that appear to be from legitimate organisations. Fake websites may be used to trick you into clicking on dangerous links.
You’re sure to fall for this kind of scam if you don’t know what to look for. However, you can easily avoid it by teaching yourself to be sceptical of all unsolicited texts. Any notification you receive from your bank should be checked against the bank's website if you are unsure about it.
Conclusion
The better informed you are about internet safety, the better off you'll be in the long run.
Precautions like using a secure VPN and using strong passwords will help you stay safe online while also teaching you how to spot potential risks. That's why ExpressVPN is our top recommendation for online banking security.
Using our advice, you should be able to begin using mobile banking safely. You'll soon become used to the convenience of mobile banking if you're vigilant.
Is mobile banking safe? Top 5 safety tips

In order to keep its customers' devices safe, both Apple and Android employ a variety of safeguards. A group of IT security specialists from around the world looked at the effectiveness of these tools, and that’s what we’re going to be discussing today.
Indeed, IT security researchers from Germany and the US conducted a study into how mobile phone users pick their PINs and how they may be persuaded to choose a more secure number combination. According to the researchers, six-digit PINs are no more secure than four-digit ones in terms of protection. Apple's usage of a "blacklist" to keep track of frequent PINs might be improved, and it would make more sense to deploy one on Android devices as well, they found.
Dr. Maximilian Golla of the Max Planck Institute for Security and Privacy in Bochum and Professor Adam Aviv of the George Washington University in the United States collaborated on the study with Philipp Markert, Daniel Bailey, and Professor Markus Dürmuth from the Horst Görtz Institute for IT Security at Ruhr-Universität Bochum. The findings will be presented at the IEEE Symposium on Security and Privacy in San Francisco in May 2020, according to the researchers. The paper's preprint may be downloaded at arxiv.org.
What do users really need?
In the study, researchers had participants create either four- or six-digit PINs on Apple and Android smartphones and then analysed how simple it was to guess them afterwards. It was considered that the assailant had no idea who the victim was or cared about unlocking his or her phone. As a result, the most effective method of attack is to start with the most likely PINs.
PINs might be chosen at random by some research participants. Only PINs that were not on a blacklist were available to the rest of the population. One of the PINs that had been banned had a warning that this combination of digits was simple to guess.
IT security specialists utilised a variety of common passcode blocklists in the experiment, including the official list from Apple. The experiment involved a machine that tested all conceivable PIN combinations on an iPhone. The specialists also compiled their own lists which were tested too.
Is there any benefit in using a six-digit PIN over a four-digit PIN?
Six-digit PINs have been shown to be no more secure than four-digit ones. As Philipp Markert explains, "Mathematically speaking, of course, there is a tremendous difference." Ten thousand four-digit PINs and one million six-digit PINs may be generated, respectively. Philipp Markert also notes that consumers favour particular combinations of PINs, such as 123456 and 654321. This implies that the six-digit codes are not utilised to their full capacity by consumers. PIN security is something people don't seem to grasp instinctively, according to Markus Dürmuth.
Manufacturers restrict the amount of PIN entry tries, thus, a well-chosen four-digit PIN is safe. After 10 unsuccessful attempts to enter the pass code, Apple permanently locks the device. On an Android phone, several codes cannot be input in rapid succession. Philipp Markert points out that "in eleven hours, 100 number combinations may be examined."
Do blocklists matter?
Researchers discovered 274 four-digit PINs that were on Apple’s blocklist. This list is used as a mechanism for improving PIN selection, as Apple iOS users are shown the warning "This PIN Can Be Easily Guessed" with a choice to "Use Anyway" or "Change PIN." It’s effectively a list of very easily-guessed pins. Maximilian Golla says, "Since iPhone users only have 10 chances to guess the PIN, the blocklist does not make it any more secure." Using a blocklist for Android devices would make more sense, according to the researchers, because attackers may test out a wider range of PINs.
According to the study, the optimum blocklist for four-digit PINs should contain around 1,000 entries and varies somewhat from the list now utilised by Apple. Four-digit PINs like 1234, 0000, 2580 (the numbers show vertically below each other on the numeric keypad), 1111, and 5555 were found to be the most popular.
Now, iPhone users can choose to disregard the alert that they have entered a commonly used PIN, as we have seen. Because of this, the device does not reliably prevent entries on the blacklist from being chosen. The IT security professionals also took a closer look at this element as part of their research. It was up to the individual test participants to decide whether or not to enter a new PIN after receiving the warning. Those who were not on the list had to create a new PIN for themselves. Both groups' PINs were equally difficult to guess on average.
Pattern locks are less secure
Four and six-digit PINs were shown to be more secure than pattern locks, but not as safe as passwords.
The simpler the pattern is, the easier it is for lurkers to copy it, if they are watching over your shoulder. In fact, research found that lurkers were successful in recreating the swipe pattern 64.2% of the time after looking at it once. Of course, with multiple observations, that success rate rises.
According to the study, these are the most frequently used PINs:
- Four-digit PINs of the following kinds: 1234, 0000, 2580, 1111, 5555, 5683, 0852, 2222, 1212
- Six-digit PINs of the following kinds: 123456, 654321, 111111, 000000, 123123, 666666, 121212, 112233, 789456, 159753
So, don’t forget to double check that your PIN is not on the list above. If you’re interested in evaluating your password security, we strongly recommend checking them against the security.org password checker.
Additionally, you might find the password checker by Experte to be a valuable resource. It estimates how long a computer would need to crack your password and checks if it has been exposed in any data breaches. It also provides actionable suggestions for strengthening your password, helping users create more secure credentials. Both tools evaluate each password based on key factors such as:
- Its number of characters: The password should have at least eight to 10 characters, but 16 to 20 characters is ideal.
- Combinations: The password should include a combination of letters, numbers, and symbols rather than taking the form of a phrase. Each character has an associated numerical value, and these characters are summed to create a grand total.
- Uniqueness: The password shouldn’t be repetitive in terms of its characters, with unique combinations used instead.
- Data leak check: In addition to evaluating the strength of the password, this tool checks whether the password has appeared in any known data breaches, which is crucial for maintaining your security.
Using both tools can give you a comprehensive overview of your password security and help you make necessary adjustments to protect your accounts effectively.
Is it safe to use a four- or six-digit PIN on a mobile phone?
Backing up data is critical to ensuring system integrity, but if done incorrectly, it can exacerbate already-existing security issues. Fortunately, there are a number of best practices that can be followed.

In order to keep your data safe and secure, you need to have regular data backups. However, these backups are often the source of many security problems. In fact, a large number of security breaches can be traced back to the mismanagement of data backups. A lack of adequate data backup controls is evident in the headlines and security surveys that are published. There's nothing wrong with using best practices when developing an enterprise data backup strategy.
Millions of sensitive business records have been compromised in backup-related mistakes over the last few years, according to recent reports. Indeed, these are just the incidents that have been publicly reported. Confidential information, including intellectual property, is no less vulnerable to data backup-related breaches than other types of sensitive data. Without a solid back-up plan in place when things go wrong, security is the first thing on the shark’s menu.
As long as there is a process for replicating sensitive data, many storage professionals believe that their organisation is safe. However, this is only half of the battle. A new set of dangers arises from what can be done with data backups, which are often overlooked. Because of this, it is essential to incorporate secure data backup guidelines into the overall enterprise information security strategy.
Here are 10 ways to keep your data backups safe and secure from threats like ransomware, malicious insiders, and external hackers, both locally and in the cloud:
Make sure you have a backup plan in place
It is important to make sure your security policies include backup systems. Access control, system monitoring, and malware protection all have a direct impact on data backups.
Incorporate backup systems into your disaster recovery plan
Your disaster recovery and incident response plans should include a backup of your computer files and other important information. A ransomware outbreak, an employee break-in, or an environmental event such as a flood or hurricane can all compromise or destroy a company's data backups. If you don't have a plan in place for what to do if and when the time comes, your backups could be harmed.
In order to protect data backups, restrict access to them
Only those who need to be involved in the backup process should be given access rights. Software and data backups are no exception here either. Systems that provide backup access, whether on-premises or in the cloud, should not be undervalued.
Consider a variety of backup options
Keep your backups in a different location, such as a different building. Your data centre and your backups could be wiped out in one fell swoop if a natural disaster, a fire, or some other rare, but impactful, incident occurs.
Protect data backups from unauthorised access
Backing up to NAS, external hard drives, or tapes is fine as long as access to those locations can be tightly controlled. Your backup files are just as important as your computer's hard drive. SOC audit reports, independent security assessments, or your own investigations may be able to confirm this.
Ensure the safety of all backup media devices
Some backups are still kept on portable drives, tapes, and other media, despite the widespread use of hard disks and solid-state drives. Fireproof and media-rated safes should be used in these situations. One of the most common places to keep backups is in a “fireproof,” but paper-only safe. A standard fireproof safe only serves to provide a false sense of security for backup media such as tapes, optical disks, and magnetic drives, which have lower burning/melting points than paper.
Check out the security measures in place for your vendors
Find out what security measures your data centre, cloud, and courier service providers are using to keep backups safe. Despite the fact that lawyers appreciate well-drafted contracts, they are not always sufficient. As a fallback measure, contracts can help protect sensitive data, but they won't stop it from being exposed in the first place. Check to see if security measures are in place as part of vendor management initiatives.
Ensure the security of your network
Backups should be stored on a separate file system or cloud storage service that is located on a separate network. Ransomware-related risks can be minimized by using unique login credentials that are not part of the enterprise directory service. The use of two-factor authentication can increase the security of your backup system.
Encrypt backups as a top priority
Whenever possible, encrypt your backups. The same is true for backup media and files, which must be encrypted with strong passphrases or other centrally managed encryption technology if they are to be taken outside the premises at any point in time. Encryption is an excellent final layer of defence when implemented and managed correctly. It's reassuring to know that even if your backups are corrupted or destroyed, you won't be able to access them. This is especially useful when it comes to meeting compliance and notification requirements in the event of a data breach.
Ensure that all of your data is backed up and tested frequently
These data backup flaws are likely to exist within your business. Before you're hit by a ransomware attack or data destruction, it's a good idea to find out where your vulnerabilities lie. Hire an unbiased third party to find the holes in your data backup processes and systems on a regular basis or look for them yourself. In the end, it's the little issues that aren't so obvious at first that can be the most difficult to deal with.
What you need to know about protecting your data backups
As a kid, I was enthralled by science fiction films like 2001: A Space Odyssey, The Fifth Element, and Minority Report, hoping that the wonderful technology shown in these films — facial recognition, artificial intelligence, gesture controls, and flying cars — would one day become a reality. Today, we have access to most of these technologies, with the exception of flying automobiles, owing to the likes of Apple.
One of these emerging technologies is facial recognition. Face ID, Apple's replacement for Touch ID's fingerprint sensor, has been available to consumers since the release of the iPhone X. However, how secure is Face ID when we compare it to Touch ID, despite how nice, convenient, and futuristic it seems? What additional security or privacy concerns does it raise?
It's important to keep two things in mind while evaluating the security and effectiveness of various forms of authentication, including biometrics:
- An attacker can guess, duplicate, steal or fake the authentication factor with relative ease;
- It is not as secure as two-factor authentication!
And here’s why…

The inner workings of Face ID
Facial-recognition systems have always been weak authentication points because they were either simple to fool or highly sensitive to ambient conditions.
In addition to detecting movements in 2D video, Face ID uses a method called ‘structured light’ to map out 3D scenes. Taking this further, "TrueDepth" uses a structured IR light (30,000 dots) to create a 3D representation of your face by measuring the depth of various spots.
Now, this increases the identification accuracy and safety of Face ID dramatically. An old-fashioned photo or video will not mislead a 3D facial scanner, unlike in the past.
For Face ID to work, Apple advises you to stare straight into the phone’s camera. This means that the system is also looking for any movement of the eye or the pupil. The skin and texture cues seen in certain facial-recognition algorithms can also help increase recognition accuracy. But, this is not how Face ID works.
There is no such thing as impenetrable technology. When researchers used publicly available photos and the technology of photogrammetry, they were able to generate 3D representations of a person's face that were quite realistic (specifically, stereophotogrammetry). We shouldn't be surprised if researchers and attackers uncover additional ways to fool Apple's Face ID mechanism in the future.
In spite of all the Face ID joke memes and the botched log-in at Apple's launch event, I feel that Face ID has been built quite effectively. This facial-recognition system appears to be more secure than many others because of its underlying technology, I believe. Even a 3D-printed face isn't enough to pose a threat, you’d need to put in a tremendous amount of work to do so.
A digital copy of your face
The digital form of an authentication factor is a second security risk for authentication systems. To put it another way, can an attacker obtain a digital replica of your login credentials and log in as you?
As far as the numbers are concerned, Apple appears to have done an excellent job of protecting this information on paper. In Apple's words, the model of your face is never saved outside of your iPhone X. No network or cloud storage is used for this data. On an iPhone, a "secure enclave" is where the Face ID data is saved, much like how your Touch ID fingerprints are stored.
Security and cryptography operations are handled by a distinct processor in Apple's newest SOC processors, the secure enclave processor (SEP). This processor is separate from the main processor and runs on its own operating system.
It is possible to store a digital key (such as a Face ID model) in your phone's SEP, but the main CPU does not view or manage it. Only the "outcomes" of the key's activities are received. Your face isn't shown to the operating system; it just receives a "matched" or "not matched" response from an encrypted area of your device. Simply put, Apple has created a method that makes it extremely difficult for attackers to get your Face ID data.
Is it enough?
Researchers and hackers will eventually find a way to get around Face ID's security measures. When it comes down to it, no one form of verification can ever be completely secure. We can use something we already have (passwords) or something we know (tokens or certificates) to authenticate (biometrics). The concern is that these tokens may be stolen, guessed, or replicated in a variety of ways.
Biometrics, such as Touch ID and Face ID, have grown increasingly popular since they are considerably easier to use than passwords and provide a reasonable level of protection. A lengthy series of random characters and numbers is simply too difficult for the ordinary human to recall.
But we're falling into the same trap, as well. All authentication methods have flaws, including biometrics. We will one day learn that biometrics like Face ID are no better than passwords.
That's why multifactor authentication is the only option that is genuinely safe. We need to combine two or more parameters instead of using them on their own. Someone could definitely make a convincing clone of your face with enough time and effort, but what if your phone or bank account demanded that you log in with both your face and your password? That would make it a million times more difficult to decipher.
It's time to stop arguing over which authentication method is more secure: Face ID vs. Touch ID; certificates vs. passwords; or a combination of both. Face ID is a solid piece of hardware, but it's vulnerable to hacking if you don't use it in conjunction with anything else.
How secure is Apple's Face ID?
The storage of data is the single most significant factor to consider when it comes to the safety of mobile devices. It's true that malware and viruses are capable of infecting operating systems, which will require you to spend time and effort wiping out and reinstalling everything following a security breach. Another possibility is that actual computers could be taken, leaving you with the burden of replacing the system along with the associated costs and hassles. However, the actual worth of practically every company's digital cache is its data, which includes personal details, trade secrets, confidential information, and private chats; the chance that this data will fall into the wrong hands significantly outweighs any other issue regarding mobile security.
It can be tough to keep your data secure on all fronts, but solid-state drives (SSDs), which have intrinsic performance advantages, can make this work easier and more efficient by supporting encryption. SSDs also have other inherent advantages.
Why is encryption necessary to ensure the safety of data?
Encryption is the most important component of a secure storage system. Many businesses operate under the assumption that a device containing sensitive data would, at some point, be misplaced or stolen. The answer, then, is not to concentrate all of your energy on keeping track of physical devices or the components of their drives; rather, the thing that is most important is to preserve the real data that is stored on them. In fact, the cost of lost data or data that has been compromised might be significantly higher than the cost of a lost machine.
The process of hiding information by putting it through a series of complicated mathematical operations is referred to as encryption. After encryption, reverting back to the earlier version of the data and undoing the process that was just performed requires the use of a coded phrase known as a ‘key’. Therefore, even if the storage device that contains the data is misplaced or stolen, the data will still be unreadable; at least, it will be unreadable without the key.
There is unquestionably a great deal more to the mathematics behind encryption, such as the number of times the encryption scheme is run, the length of the key, and a variety of other considerations. The more complicated an encryption method is, the more difficult it is to read and write data as well as use the computer's processing power. This might cause the processing speed of the computer to become increasingly sluggish. This is where solid-state drives (SSDs) shine thanks to their naturally faster performance. Calculations necessary for the encryption and decryption process can take place significantly more quickly when the data can be written to or read from the drive at a higher rate.
Encryption and solid-state drives: safety and speed
There are two approaches that can be taken to accomplish encryption. One method involves using software, in which case the mathematics required for decryption and encryption is handled by the primary processor of a computer. The second method includes what is known as "delegating" the encryption process to the drive's hardware so that the storage device may do the necessary mathematical operations on its own. The disk then provides the host CPU and memory with newly decrypted data in order to avoid imposing a "performance tax," also known as a lag, on the primary components of the system.
The server-class solid-state drives (SSDs) produced by Samsung are equipped with options for full disk encryption built right into the hardware. This makes protecting company data as easy as checking a box and entering a key. Typically, this entails the drive storing a copy of the decryption key in a protected area within the drive controller circuitry itself, and then encrypting that key with another key that is provided at boot time by the user, such as a multifactor PIN or passcode. This allows the user to access the drive without having to remember multiple passwords or PINs.
What outcomes are possible in the event that computers are taken during a break-in? Would anyone else have access to the information you provide? At boot time, the information would be safe to access if it were encrypted with hardware as long as the key, which is retained by the user, was not disclosed.
Maintaining safety without sacrificing speed
Doesn't the use of encryption make things slower? The mathematics that underlies encryption does take up resources, and the more data you have, the faster your drive needs to read and write, which in turn requires more complicated mathematics. This effect is typically most evident when we consider spinning material that was produced in the past. Users are able to continue being productive and have the peace of mind that the sensitive data they are accessing will be kept secure at all times thanks to the faster performance of solid-state media, which helps to reduce the impact of the encryption’s "performance penalty."
Why encryption and SSD safety are so important
Almost everything that can be connected to via a network can be also hacked. But what about cars? Can they be hacked? If so, how much time do criminals have to spend on it?
In fact, hackers are able to shut off your engine while you’re driving, control your steering or brakes, and even open and close your doors and boot. As a result, driving a hacked car can be pretty dangerous.
Finding a hole in your car's software is all it takes for someone to compromise the system. It isn't always that difficult for hackers to find a means to get into your car, even though it could take some time. A committed hacker can enter a reasonably sophisticated system with enough time. According to the research of Upstream — a car cybersecurity organization — by 2025, more than 86% of cars will be connected to the global network. ‘Connected’ refers to the sharing of data among servers, applications, phones, etc. Because of this connectivity, there are several ways that automobiles can be compromised.
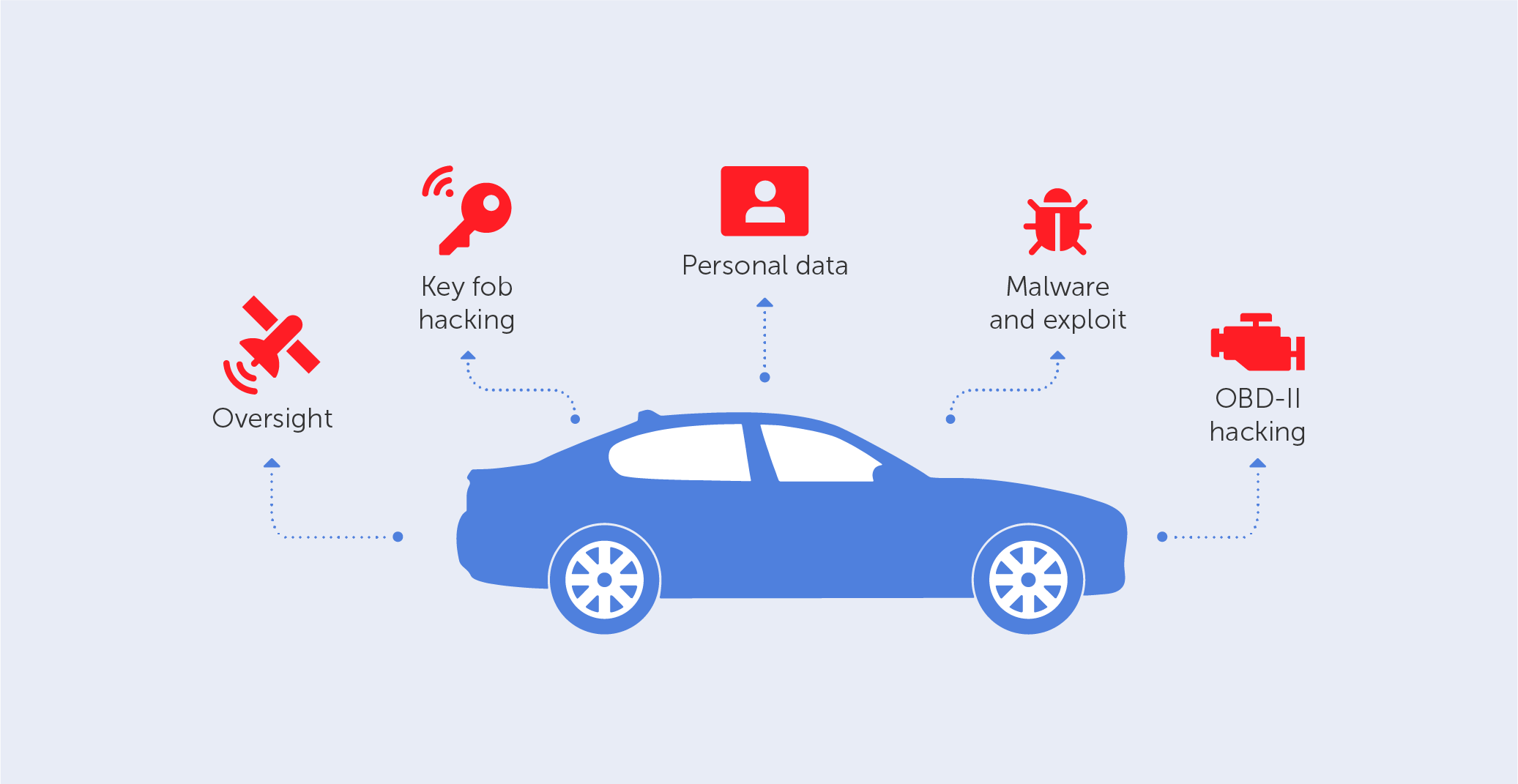
What damage can hackers do if they hack your car?
There are multiple ways criminals can hack your car. First of all, the brake pedal and engine are vulnerable. Although your brake pedal is within your control, the onboard computer's microprocessors are what actually cause your brakes to function. Your brakes can be disabled and the engine can even be stopped by hackers who get access to your onboard computer.
Hackers also could interfere with the movement of the car using wipers, heaters, conditioners, or radio. Each of these options could be controlled remotely and used to distract the driver. Although windshield cleaning fluid is helpful, it’s more of a burden when it’s released repeatedly or abruptly. If that’s the case, it might endanger your visibility. Your windshield wipers and this system are both hackable. The same can be said for heating or conditioner systems. They are useful until they can be used to harm you.
Another way of hacking can be performed by unscrupulous repair shops. The majority of initial diagnosis is done by onboard vehicle diagnostics equipment. However, dishonest businesses may trick your diagnostics system into suggesting that you need repairs that aren't actually necessary. This is an easy way for them to earn money. Thus, it’s important to use services that are reliable.
Hackers can also use a car’s interconnected system to impact one’s car safety and its correct operation. This could, for example, lead to forced acceleration. When a car is driven or reaches a given speed, power locks frequently contain functions like automatic locking. Such integrated systems in cars make them susceptible to issues like power locks being overridden to compel an acceleration.
It’s also possible to extend the key fob range to gain physical access to the car. Modern wireless key fobs open automobile doors when the owner is nearby. Thieves who aren’t focused on harming the car owner, but rather looking to steal the car can also exploit the functionality of the key fob and increase its range using radio repeaters. It allows one to unlock the car from up to 30 feet away.
Moreover, if hackers break into your car’s entire system, they could gain your private information, especially if the car is equipped with a GPS telematics system. This data could be misused to invade your privacy and possibly to learn where you live, work, or send your children to school. The serious threat is presented by the connection between your car and your smartphone. Some advanced hackers might be more interested in your connected mobile phone than the automobile’s system. Your information is in danger if they manage to get access to the system in your car and locate the mobile device that is connected to it. The connected smartphone is a direct source of your bank credentials, passwords, and other sensitive data.
Will your car be hacked?
Nowadays, almost every car is susceptible to being hacked. But, talking about chances that you will be impacted by car hacking, it is unlikely you'll experience any issues with hacking at this stage. In any case, it’s better to be safe than sorry. Due to the lack of financial benefit, most hackers prefer not to enter this sphere, with the exception of car thieves who use elements of hacking to neutralize the car’s alarm and relevant security systems.
Car hackers frequently do this for amusement or malicious intent. Very few hackers in the real world have targeted automobiles. Instead, the majority of vehicle hacks are either theoretical or carried out by research teams looking to find weaknesses in the car’s protection. Most car hacks are difficult for average hackers to execute since they typically call for a great deal of knowledge, equipment, and sometimes even physical access to the vehicle itself. However, vehicle makers are still working to develop defenses to shield their products from cyber harm. All due to the potential possibility of hacking attempts. More and more vehicles become connection-available, smart, and independent, so it may lead to an increase in car hacks in the future.
How can you protect your car?
Currently, hackers aren't really interested in your car. However, the situation may change. Hackers may become more interested in and adept at hacking cars as they become aware of their ability to kidnap automobile owners, steal their data, and carry out nefarious deeds like larceny. There are some easy steps that should be done by every car owner to protect their privacy and security.
First of all, do not program your home address into your GPS system. While having a GPS may be handy, car thieves and hackers can use it to locate your home location.
Then, it’s necessary to limit wireless systems connected to your vehicle. You are most in danger from such technologies, as wireless or remote systems are frequently operated online and are more susceptible to hackers than many other systems.
And the last, but not the least piece of advice, use reputable shops, as anyone who gets physical access to your car and is computer savvy can wreak havoc on it. Therefore, when you leave your automobile in a shop, whether it’s for minutes, hours, or days, you run the risk of someone hacking it to make it seem as though you need repairs that aren't actually required.
How easy is it to hack your car?

Whenever the word ‘cybersecurity’ appears, the word ‘password’ springs to mind in parallel. People use them everywhere, from mobile phone locks to the protection of personal and state data stored on individual devices or websites. Everyone knows that a strong and secure password is able to save our sensitive information, however, cybercriminals have invented a huge variety of methods to hack our passwords in order to compromise us. So, modern problems require modern solutions. Now, there are a lot of alternative ways to protect access to personal data. The usual passwords are replaced by multi-layer authentication or just more progressive technologies. These are fingerprints and face recognition functions, keychains, and password vaults. But what is the future of passwords? Will they become an outdated option or stay a necessary part of access.
Why are passwords considered weak?
With the growth of cybercrime, the requirements for passwords are increasing. The first passwords consisted of short, easily-memorized word or numeral combinations, but they were too easy to crack. Now, passwords are sophisticated alpha-numeral combinations, sometimes too long to remember. Nevertheless, it is still possible for hackers to find the solution and get access to your account. Passwords are usually based on some common information like a date of birth, the name of a child, or a home pet, which implies that hackers are able to find out what it is if they have enough time. The other reason why passwords become targets is the fact that they provide unrestricted access to your account. Moreover, many people use the same or similar passwords for many different accounts, so they simplify the process of collecting their sensitive data from multiple sources. Of course, using the same password for every account mitigates the risk of forgetting the password, but reusing the combination is quite risky. Users are sure that they won’t be hacked as the data they store is not valuable enough to be stolen, but it’s a common mistake as almost everyone can be compromised or fall victim to a bot attack that is aimed at spreading spam or malicious links. So, the best way to protect your privacy is not to reuse the same password and exploit multi-layer authentication for your accounts.
The anti-password movement
This movement was established as soon as people understood that usual passwords are more vulnerable than they should be. Passwords are inconvenient and provide multiple avenues for fraudsters to obtain your data and profit from it. The most typical method for hackers to profit from this data is to sell it on the dark web for fast cash. Advanced attacks on logins have been known to shut down entire corporations or launch ransomware campaigns. Credential stuffing is the most well-known form of password hacking, it is based on the reusing of the same password for multiple accounts, pairing it with different email addresses or logins. It is usually aimed at taking over as much information from corporate accounts as possible. Thus, internet users realized that passwords are not the most powerful protection that can be exploited for security goals. So, what was made in addition to, or in place of, the password?
Multi-factor authentication
Single-factor authentication refers to the requirement of only one password to access an account. This method of protection has been used for a long time, but now it’s obsolete. The new practice in authentication is multi-factor access which requires passing two or more layers of authentication before accessing an account. The possible steps of this sophisticated technology could be the PIN code, the server-generated one-time code sent to your email address or mobile phone, or even fingerprints and face recognition.
It makes access more complicated but also serves as an additional barrier to compromise attempts and data thieves. This motivates them to move on to more straightforward targets. While it isn't infallible, it does dissuade attackers from trying anything else, potentially rescuing you from disaster.
Another successful way of protection is the passphrase that is used instead of common password combinations. It is represented as the meaningful or meaningless word combination consisting of up to 100 words. It seems to be hard to remember a long phrase, but it is much easier than remembering alpha-numeric combinations including substitution, capitalization, and different numbers. Hackers will find it incredibly difficult to break into a system since passwords are several words long and can contain an endless number of word combinations. Another good thing about such protection is the lack of necessity to install the special apps or systems required to use this technique. It can be applied to every account without special password character limits.
Is the password dead?
The first hacking attacks were conducted as early as the 80s. Regardless of this, people still use passwords as the main protection force for their private information. So, why can’t we replace it with more modern and convenient technologies?
First of all, it’s related to the ease of creating passwords. The password is generated by the user himself, so there’s no need to create and exploit special services that would be able to provide protection for the account on the user’s behalf. Another point is the privacy of users. The password is one of the more private ways of authentication as it doesn’t require any personal information, it can be a random combination of numbers and lack sense, unlike methods such as biomedical data access, which is connected with personal information that could get out into cyberspace. The last but not the least important point lies in the simplicity of replacing passwords. It can be useful in the event of a major data breach, as it’s easier to change the password than the biomedical options that are used for fingerprints or face recognition.
Conclusion
So what will be the future of passwords? Passwords will definitely be used as one layer of a multi-factor security system for the next few years as there are still no more useful options for saving our privacy than passwords. People are continuing to look for the perfect method of protection, so maybe in a few years, something will finally appear and the world will be able to say goodbye to long sophisticated passwords. Some services have already turned to new systems of access, like one-time codes or fingerprints, but there is still a possibility of being hacked. Indeed, users still believe that a multi-layer system of protection is more convenient than any possible alternative.
The future of password security

Migration to PHP 8
The new version of Passwork now runs on PHP 8. Previous versions of PHP are no longer supported.
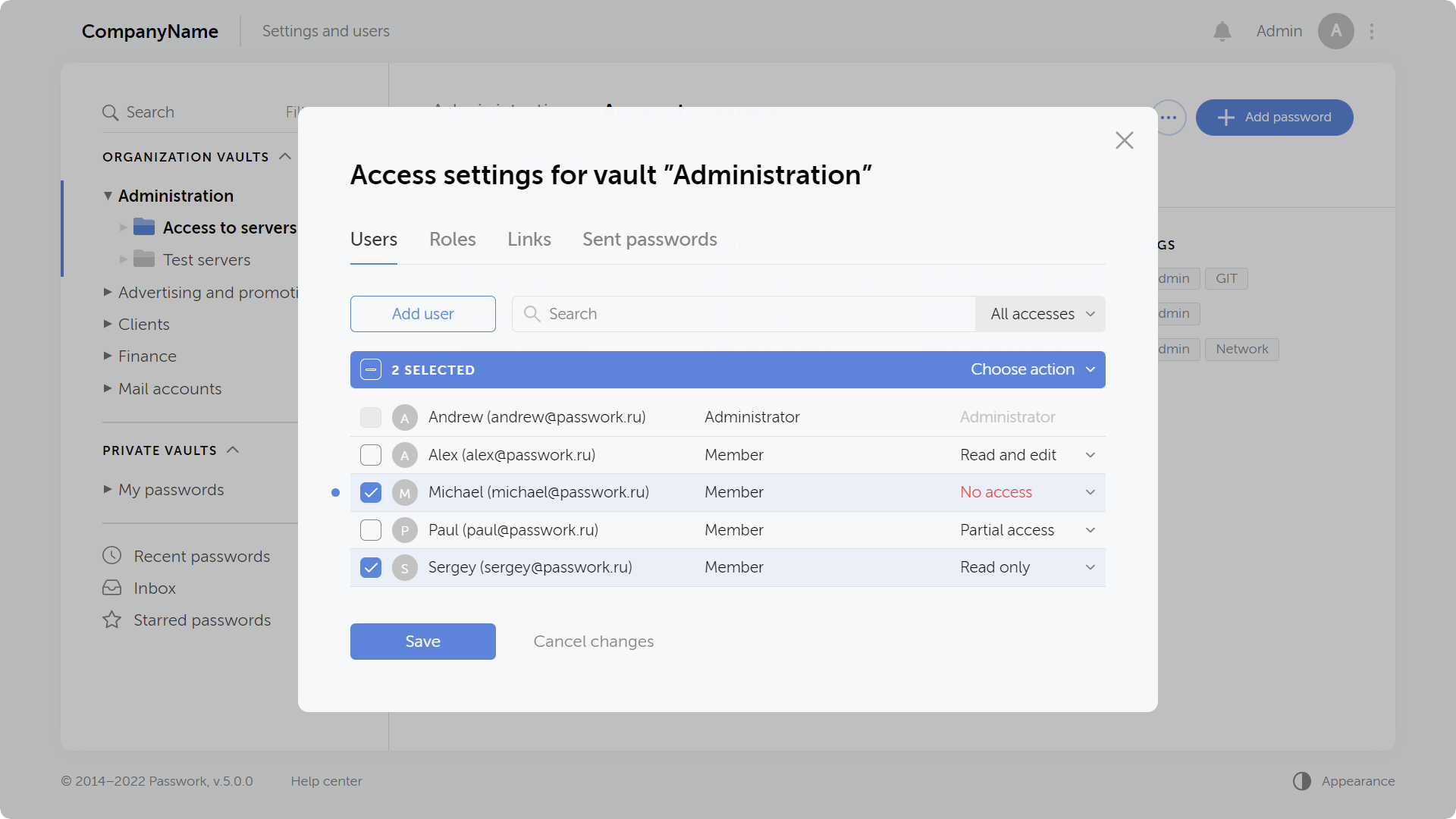
New access rights window
The window with access settings for vaults and folders has been completely redesigned. All users and roles having access to a vault or folder are now collected here as well as links and sent passwords.
The rights can now be edited on each tab by selecting multiple objects at once. All modified and deleted objects are marked by an indicator until you save changes. Search filters allow you to display all objects with a certain access right.

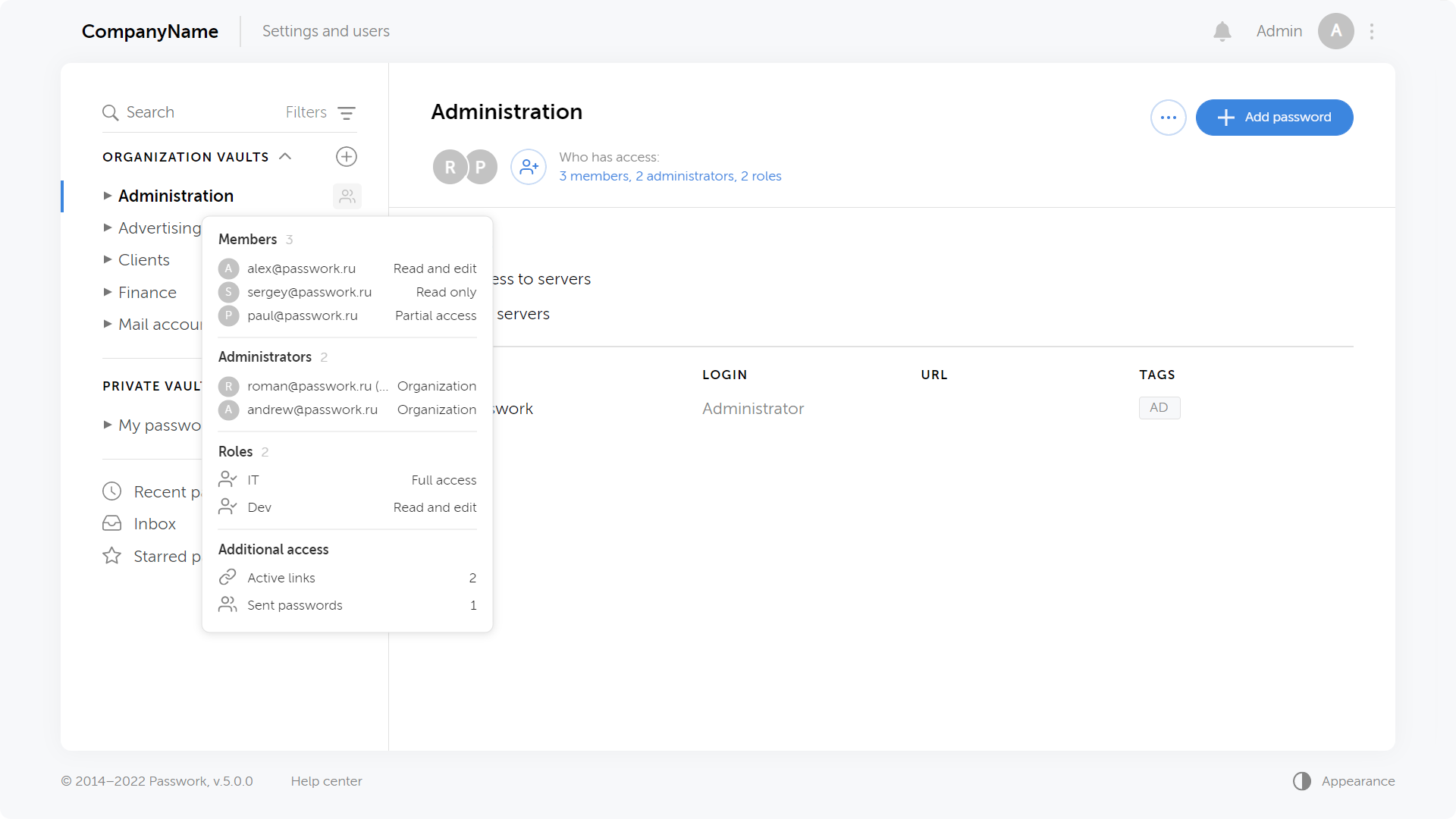
Ability to quickly view who accessed vaults and folders
When hovering over an icon next to the name of a vault or folder you can see some brief information about the number of users, roles, links and sent passwords.
Clicking on a list opens up the window for access rights management inside a given vault or folder.

Granting access to individual passwords without adding users to a vault
In previous versions of Passwork, it was possible to send a password copy to users. In the new version, users will see the original password in the Inbox, which will be updated when the original vault changes.
That means you can now give access directly to a password without adding users to a vault or folder.
You can send a password and enable users to edit it, then when a user changes this password, it will be updated for you as well.
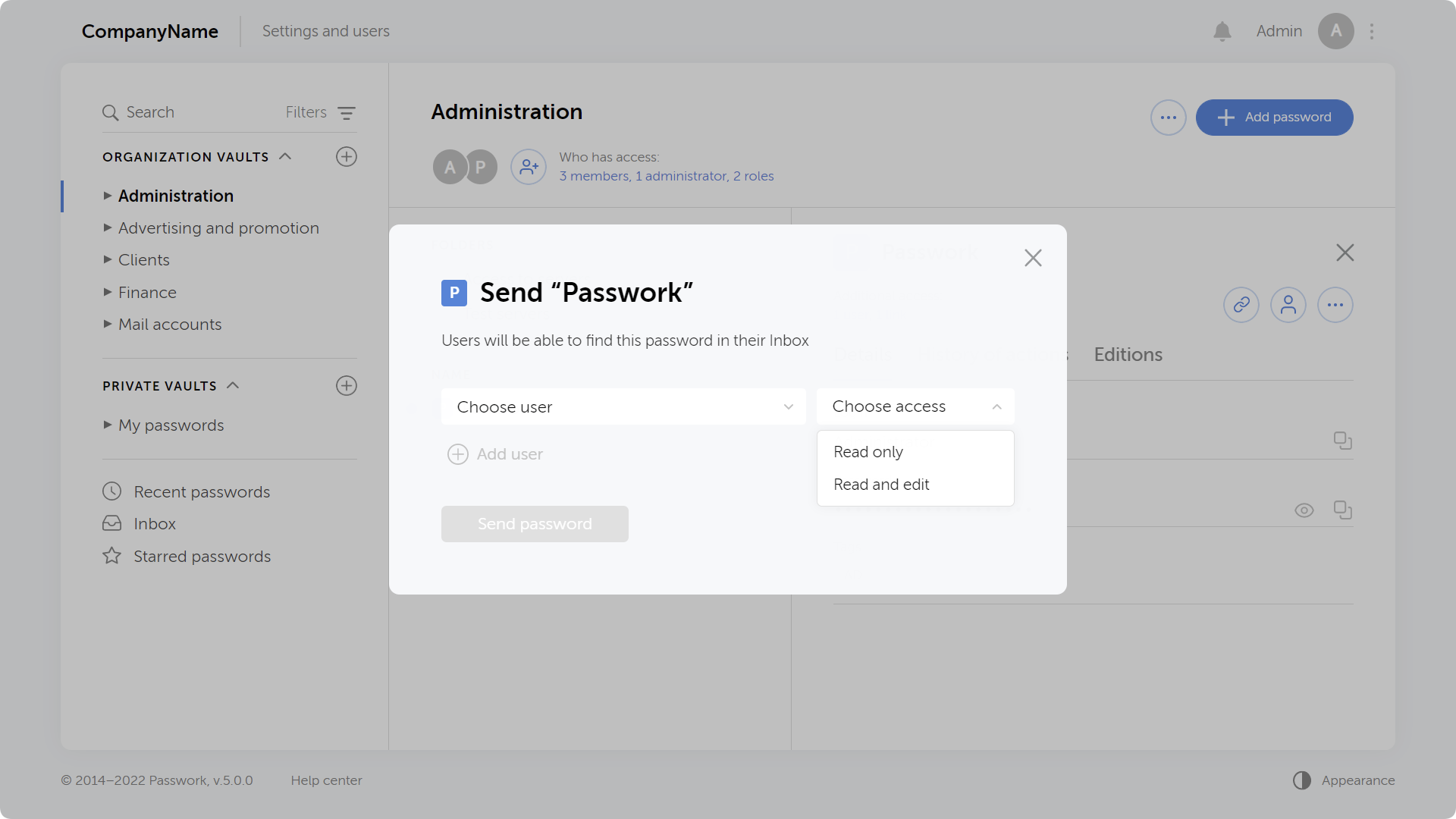

Ability to add TOTP keys and then generate 2FA codes
When adding and editing a password, you can add a TOTP field and enter a secret code to generate 2FA codes. The generated code is updated every 30 seconds.
The "Password" field is now optional, so you can keep 2FA codes separate from main passwords.
Adding TOTP keys and generating 2FA codes is available in the web version, browser extension, and mobile app.
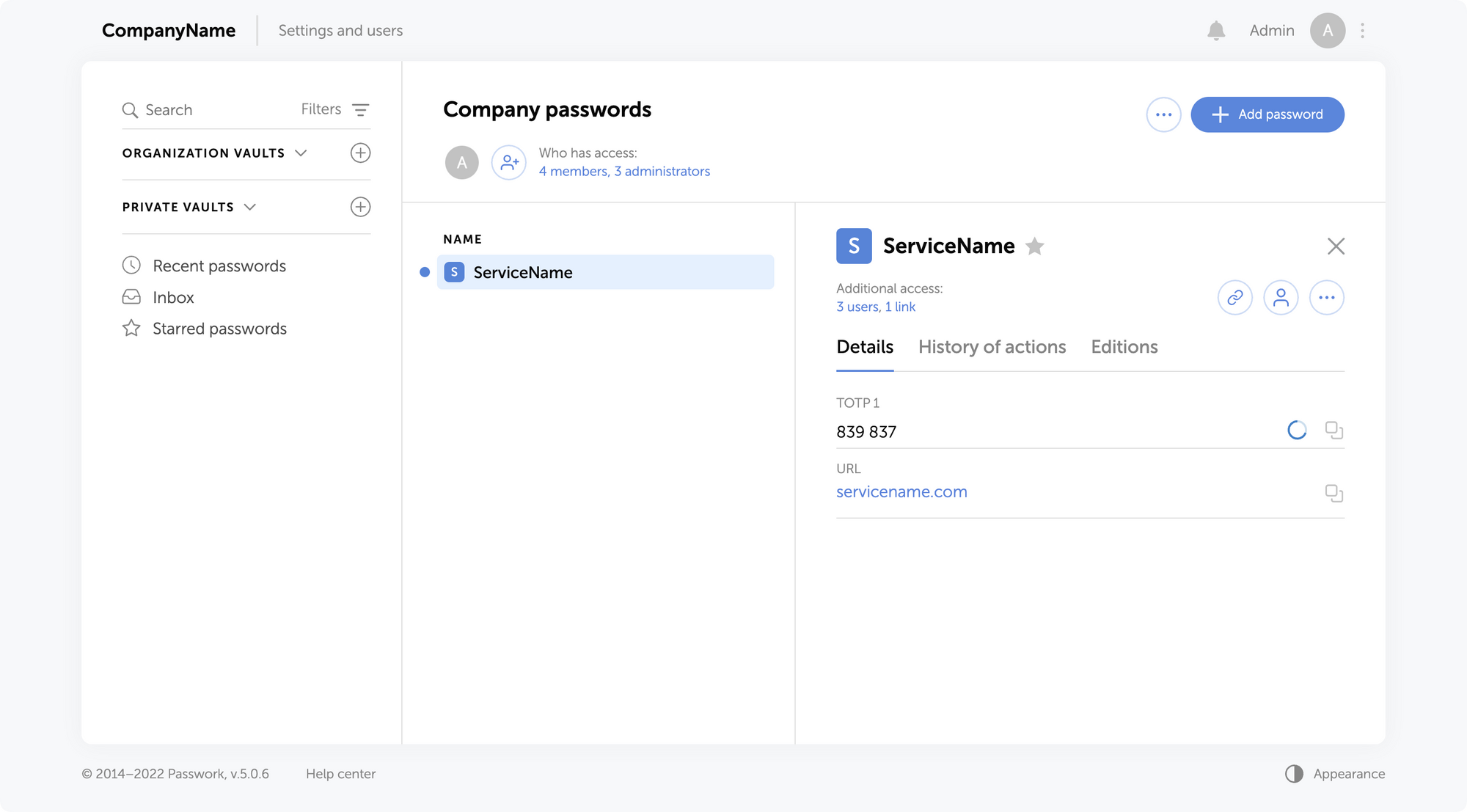

Failed login attempts are now displayed in the action history
The action history displays all failed user authorization attempts. This allows you to better track unauthorized access attempts and the actions of blocked users.
You can see all failed login attempts on the Activity Log page by enabling a filter in the Action column.

Ability to enable priority authorization using SSO
The new version of Passwork now allows you to enable SSO priority authorization for all users. You can enable it in the "SSO settings" section.
With this option enabled, only the "Sign in via SSO" button is displayed on the authorization page, the login and password fields appear only when switching to the standard authorization.

Optimized work with a large number of users
Passwork has been tested and optimized for 20,000+ users.
Improved LDAP integration
- Test mode for LDAP roles and groups linking
- Saving LDAP logs to a CSV file
- Updating user attributes during synchronization with LDAP directory
Mobile app update
- Passwork 5 support
- Ability to copy passwords on long press
- New home screen view with separating by type of vault
- Inbox passwords
- Improved search mechanism
- Debug mode
If you are already using Passwork, update your version
How to upgrade Passwork 4→5 version.
Or request a free demo at passwork.pro.
Introducing Passwork 5.0
Are you sure that your home is protected in the way that you think? Sure, you can secure it with modern locks or an alarm system to protect yourself from robbers who want to steal your money or furniture, but what about those who are looking at your home as a means of stealing your privacy?
As the number of smart electronic devices we use every day increases, we have to make sure that the personal information that is recorded by these devices is safe.
So let’s talk about home security and how to protect yourself from those that are looking for ways to hack your smart devices.
Which smart devices can be hacked?
Almost every smart system used with modern devices is potentially dangerous as hackers know hundreds of ways to obtain remote access to them. But still, some devices seem too ordinary and primitive to be hacked. Perhaps a robot vacuum cleaner or a smart baby monitor. But there are more sophisticated technologies like a smart TV or smart house security system. They're all vulnerable since they're connected to the internet and are frequently part of your home WiFi network. Recent research showed that every one of them has several serious security flaws.
What are the risks?
Many experts note that when it comes to smart home devices, you should be thinking about ‘when’ they will be hacked, not 'if,' because many are notoriously easy to hack and provide no protection whatsoever. Scientists from the European watchdog Eurovomsumers examined 16 regularly used devices from a variety of manufacturers and discovered 54 vulnerabilities that exposed consumers to hacker attacks, with potential implications ranging from security system deactivation to personal data theft.
According to the results of research, hackers can gain access to highly sensitive information such as banking credentials or even utilise many linked devices to stage enormous distributed denial of service (DDOS) operations, which allows them to ruin banking or other service networks.
Whenever most internet users realise the vulnerabilities associated with the usage of computers connected to the Internet, many people still do not pay enough attention to the fact that their home smart devices also present the same danger. As all home devices are commonly connected to the same Wi-Fi network, it gives an opportunity for hackers to get access to all domestic technologies at the same time.
Security gaps
One of the most significant dangers that are presented by smart home devices is the potential for a ‘deauthentication attack’, in which a hacker orders the device to disconnect from the house WiFi. It may cause the blocking of systems and devices, which won’t be able to respond to users’ requests as a result. It was also discovered that some apps designed for home appliances are able to transfer unencrypted data. It means that if hackers break into their system, they’ll gain access to the owner's personal information, such as WiFi passwords or even listen to what happens around the device if it’s equipped with a microphone. A stolen WiFi password may provide hackers access to phones or computers connected to this network and lead to an eventual data leak.
Due to the gaps in security systems, smart devices often have flaws that make them vulnerable to attack. Designers of these devices focus on the comfort of exploitation and multifunctionality of their products, but not on their security. But now, when almost everything from house alarms to refrigerators can be hacked, it becomes a paramount point.
Recent research that took place in America and Europe has shown that about a half of interviewees use smart home devices, but most of them do nothing to protect themselves from being compromised. Thus, even though people know about the risks, they still do nothing to minimise them. One of the possible reasons for such behaviour is the lack of knowledge and accessible information about how to make the usage of smart home devices secure.
How can you secure your home devices?
Of course, the most basic way to protect yourself from the hacking of your smart home devices is just not to use them and replace them with less functional but safer options. But what if you can’t go without such a pleasure? Well, Euroconsumers — one of the most well-known private organisations for consumers — developed a list of recommendations that can help people who want to maintain their privacy while using smart devices:
1. Use an ethernet cable instead of Wi-Fi to connect your devices to the network where possible;
2. Create strong multilayered passwords for your devices and Wi-Fi;
3. After installing your WiFi network, always change the default name;
4. Always keep your devices up-to-date and switch them off if you’re not using them at a certain moment;
5. When you use a device for the first time, always finish the setup procedure;
6. Do not buy cheap devices with a low level of protection.
Conclusion
When we’re talking about smart devices, we’re not just talking about full smart house systems such as alarms. Rather, we’re talking about smart appliances such as TVs, doorbell systems, vacuum cleaners, and other common household things. Using them makes our lives more comfortable and saves time and energy. However, they each have their own flaws, and many are vulnerable when it comes to hacking. So, consumers should pay attention to this point of using smart devices and consider all possible ways to protect their privacy without refusing to exploit such useful appliances. If you use one of these devices, try to get more information regarding what manufacturers pay more attention to regarding the security of their goods. Moreover, make sure to protect your own devices from hacking. It won’t take a lot of time or effort, but it will save your sensitive data and protect you from being compromised.
