If you still haven’t heard about Starlink, you’ve definitely heard about its creator — Elon Musk.
Elon Musk is a billionaire entrepreneur most famous for his electric vehicle firm, Tesla, and his space exploration company, Space X. Maybe you learned about him from our news headlines talking about his attempts to acquire Twitter or his past endeavors stirring up trouble on social media. Perhaps you only know him as one of the world's wealthiest people. Starlink is the less known facet of Elon Musk’s career that is focused on providing internet to every part of the world including hard-to-reach places, and that’s what we’re going to be talking about today.
What is Starlink, exactly?
Starlink is the name of the global and constantly growing network of orbital satellites overhead, based on SpaceX technologies. This project began in 2015, and the first prototype satellites were sent into orbit in 2018. In January 2021, after three years of development and successful launches, Starlink reached 1,000 satellites. Over the course of the next year, this number doubled. Now, Starlink has more than 2,000 operational satellites orbiting the Earth. Indeed, it’s still just the beginning. The plan will be completed as soon as the network covers most parts of the Earth’s surface. To do this, Starlink requires about 12,000 satellites in orbit.
Currently, the project’s creators are assuring the provision of its service in 32 countries. This number will increase every year. However, the budding broadband provider still has a backlog of prospective customers waiting to receive equipment and connect to the system.
How fast is Starlink?
Starlink offers high-speed broadband internet, the spread of which, according to the speed-tracking website Ookla, is above 100mbps in more than 15 different regions. When we’re talking about the United States, Starlink offers average download speeds of around 105Mbps and upload speeds of around 120Mbps, which is about five or six times faster than their satellite rivals. Elon Musk is focused on doubling the average internet speed and reaching 300 Mbps. In any case, even now, we can observe his success as the Starlink Internet system really is one of the fastest in the world.
How much does it cost?
The initial cost of the service was $99 per month, and the initial one-time payment for the satellite dish and router was $499. As Starlink is focused on the availability of the internet, it was announced that the cost of the service is going to decline in a few years. But, in March of 2022, the company announced a price increase. So now, the monthly payment is $110 and the initial payment for the equipment is $599. This price is quite high for satellite Internet, but the creators of Starlink bet on the wide coverage of their network and its availability in hard-to-get places.
As the president of SpaceX said last year, Starlink aimed to keep pricing as straightforward and transparent as possible, and that there were no plans to add more levels to the service. However, in 2022, a new premium level with a scanning array twice as large as the normal plan and download speeds ranging from 150 to 500Mbps appears to be modifying that strategy. This option costs $500 per month, and the initial payment for equipment will be $2,500. Now the company is taking orders for that tier, with the service set to arrive later in 2022.
The pros and cons of Starlink Internet
Starlink, like any other modern technology, has some benefits and drawbacks. Let's take a quick look at them.
The pros of Starlink:
1. Faster Internet. The internet offered by SpaceX is definitely faster than traditional satellite Internet. Starlink is so quick that it's almost impossible to compare it to traditional satellite connections.
2. Relatively cheap. Starlink's internet service is reasonably priced. In rural and suburban locations, it is less expensive than cable and satellite internet. Suburban consumers pay the same price as city residents in many areas, but they get much slower internet.
3. Wide availability. Regardless of your location, Starlink is available to every customer. It has wide network coverage and provides fast, unlimited Internet from Antarctica to the middle of the ocean.
4. Faster disaster recovery. Storms, tornadoes, wildfires, and floods can all cause internet cable to be seriously damaged. After any type of disaster, the recovery of the cable Internet takes quite a lot of time. The process of fixing it isn’t just costly but also time-consuming, unlike Starlink. The Internet will be available straight away after the disaster.
The cons of Starlink:
1. Hardware installation. For many users, hardware installation could become a problem as the creators of Starlink don’t provide the installation of the equipment needed for using their network. Thus, customers have to install the equipment themselves or hire professionals to spend extra money.
2. It’s not portable. When compared to cellular internet, Starlink is not as portable. We can use our phones to access the internet from any place. The Starlink dish is not at all portable. Though the dish can be installed above an RV or a boat, unfortunately, it is not small enough to be carried easily.
3. Service disruptions depend on the weather. It's common for satellite service to be disrupted by rain, storms, or solar flares. However, this isn't a major pro for cable internet either; it’s also subject to this type of disruption.
As the number of Starlink’s users increases, the question of the security of this Internet connection has become acute. People want to make sure that the provider that they use is safe enough and that nothing threatens their personal data.
So, is Starlink secure?
The main problem of satellite Internet is that some of the information carried by satellites can be intercepted as it is translated to and from the Earth. Some of that data can also be changed before it reaches its intended destination. This does not, however, necessitate the use of specialized equipment. According to a recent study, this could be accomplished with $300 worth of equipment. It's vital to keep in mind that this issue does not affect all traffic. If you're using an encrypted connection, this form of assault is likely to be unsuccessful. However, it does underline the reality that as satellite internet becomes more ubiquitous, cybercriminals will have additional chances.
Conclusion
Starlink is a quickly growing and highly available technology that is just at the start of its development. However, it already could demonstrate great advantages over the cable network. Like any modern technology, it has several disadvantages, such as weather dependence and the risks related to satellite networks. Now, SpaceX promises a very high level of service with wide coverage, but as practice shows, not all of their promises are worth trusting. If you’re going to get the Starlink dish, you have to consider this issue deeper to make sure that you’re making the right choice.
How secure is Elon Musk’s Starlink?
From smartphones to automobiles, almost every device is equipped with Bluetooth technology nowadays. Many people use it every day while connecting to headphones, sending files, or making remote calls in their cars. However, most people are unaware that using Bluetooth carries a number of risks when it comes to your privacy and safety.

What is Bluetooth?
Bluetooth technology is a standard for creating a local network that allows neighboring devices to exchange data wirelessly. In other words, you can use Bluetooth to transfer data between devices such as your phone and headphones without the use of a cable. Bluetooth is widespread and free to use, that’s why it is so popular with device creators and consumers.
Bluetooth was invented in 1994 by Ericsson — the telecommunications equipment manufacturer. Now, you can find this technology in almost every electrical device around the world. Even smart household appliances are equipped with Bluetooth nowadays, so you can send instructions to your refrigerator or vacuum cleaner remotely.
Bluetooth hacking
Of course, as with most standards, Bluetooth has its disadvantages and security vulnerabilities. Bluetooth allows devices to communicate with one another across short distances and for a limited time. As a result, most Bluetooth hackers focus on getting close to a target and carrying out the assault in a short amount of time. Particularly in areas where people tend to linger around. There are a number of places that pose a great amount of danger to your devices. For example, cafes, the underground during rush hour and on the bus.
However, when the attacker’s target moves out of range, it could stop the attack and ruin the hacker’s plans. It's worth noting that some attacks can be launched from hundreds of meters away. So moving a few steps isn't the same as being out of range.
Some hackers are also able to control your device for under 10 seconds using Bluetooth. Even more concerning is the fact that hackers can accomplish this without engaging with the user.
There are a variety of Bluetooth hacking techniques:
1. Bluejacking
This type of cyberattack on Bluetooth connection lies in sending spam messages via Bluetooth. One Bluetooth-enabled device hijacks another and sends spam messages to the hijacked device. First of all, this can be annoying to get such spam. But if you click it and accept files from an unknown device, you may get into big trouble. The message may contain a link that will lead to a website that is designed to steal your personal information and compromise you.
2. Bluesnarfing
This type of attack is similar to the previous one but much more detrimental to your privacy. During these hijacking attempts, hackers can not only send spam messages to one’s phone, but also collect some private information like chat messages, photos, documents, or even credentials from the victim’s device. All of this will be used to compromise you or for extortion attempts.
3. Bluebugging
This is the last and the most dangerous type of Bluetooth hijacking. Hackers use your device to establish a secret Bluetooth connection. This connection is then used to acquire backdoor access to your device. Once inside, they can monitor your activities, gain your personal information, and even use your personality on your device's apps, including those used for online banking. This type of assault is known as blue bugging since it resembles bugging a phone. Once hackers get access and complete control over the phone, they get the opportunity to make phone calls themselves and listen in on every phone conversation.
Bluetooth security concerns
If you think that the direct invention of hackers is the only danger that Bluetooth presents, we have some bad news for you. Many apps including popular ones such as Google or Facebook can monitor the location of users through the use of Bluetooth technology.
By switching on Bluetooth, you enable the transmission of information, but you also enable your device to catch adjacent Bluetooth signals. Thus, Bluetooth signals are used by app developers to pinpoint your location. So, the IT companies that develop apps can find out the information about your location wherever you go and keep track of your everyday activities. The most terrifying aspect here is that Bluetooth enables extremely precise tracking. The good thing is that most app creators write that “the usage of their apps requires Bluetooth utilization” in their privacy statement. Unfortunately, the majority of consumers do not read the privacy statements of the apps they use, so they automatically accept all the requirements and rules of the new app.
To protect yourself from activity and location tracking, you should read each app’s privacy policies and not use apps that require Bluetooth. If you determine that some of the apps you regularly use are requiring Bluetooth, you can disable the location tracking function for them.
What do we need to do to safeguard our Bluetooth connections?
In mentioning all of the risks associated with the use of Bluetooth, we have to give you some advice regarding the safeguarding of your devices.
1. Make your Bluetooth device non-discoverable. This can be done in your device’s settings.
2. Do not send any sensitive information via Bluetooth as it can be caught by intruders.
3. Do not accept any files or messages from unknown devices via Bluetooth, especially in crowded places.
4. Always turn your Bluetooth off after using it to prevent unwanted connections and breaches.
5. Don’t share anything via Bluetooth in crowded places, even if you want to connect to your friend’s device.
6. Install some security patches to protect your device and stop any possible tracking via Bluetooth.
Conclusion
Bluetooth is a common and useful technology that is used in almost every device due to its convenience and fast connection. But the simplicity of its technology leads to several flaws, which is why Bluetooth can’t be named a very secure standard. Nevertheless, most people cannot avoid using this technology — it’s just too widespread. To keep your device safe, we recommend following the aforementioned security rules.
How secure is Bluetooth? A complete guide on Bluetooth safety
What is WebSocket?
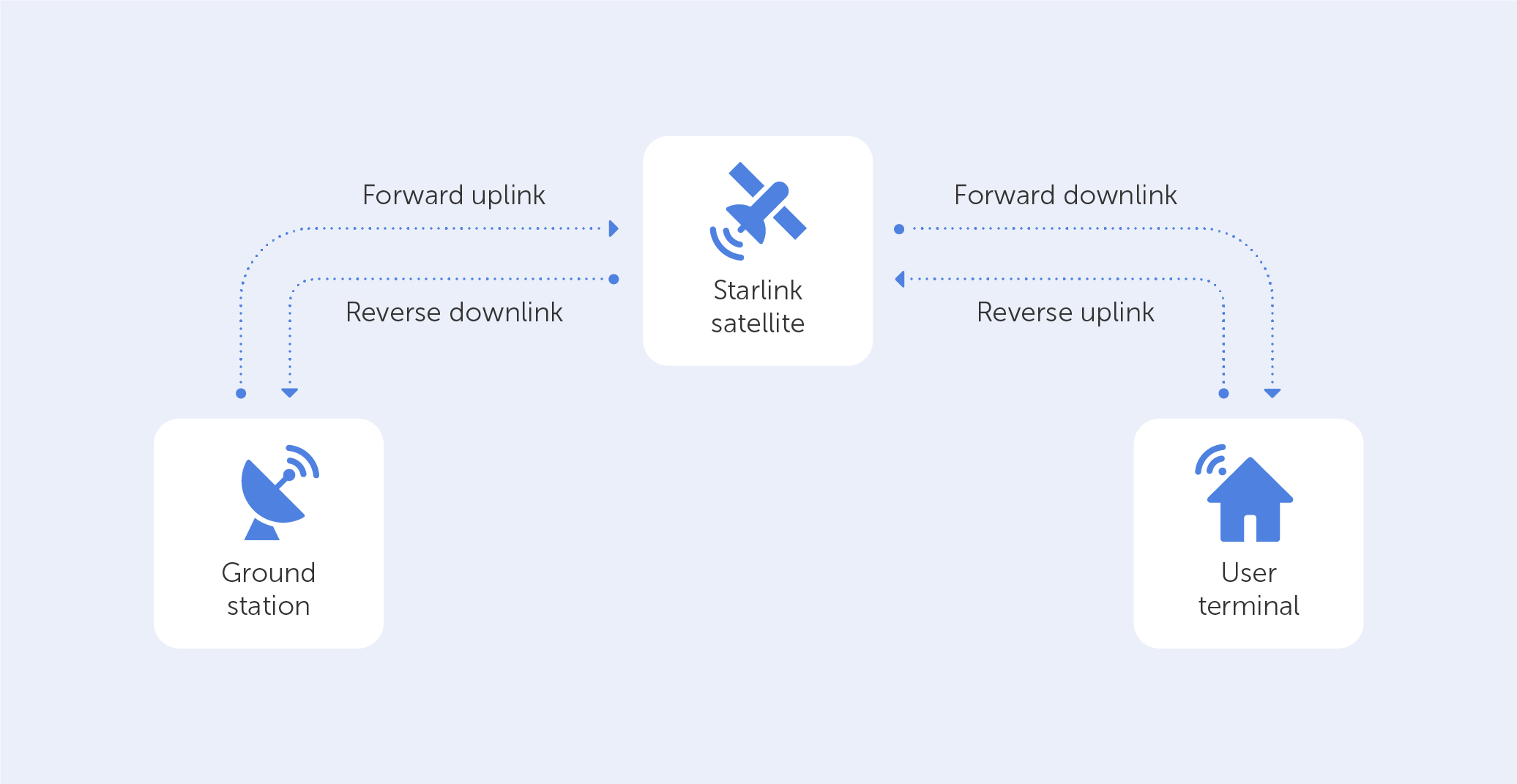
The WebSocket API is a cutting-edge technology that allows the opening of bidirectional interactive communication sessions between a user's browser and server. You can use this API to send messages to a server and obtain event-driven responses instead of polling the service. WebSocket is a stateful protocol which means that the connection between the client and server will remain open until any of the parties terminate it.
Consider the client-server communication: when the client initiates the connection with a server, a handshake occurs, and any other request will go via the same connection until either of the parties closes the connection.
WebSocket is a good thing for services that require constant data transmission, like network games, online trading sites, and other websites that work continuously.
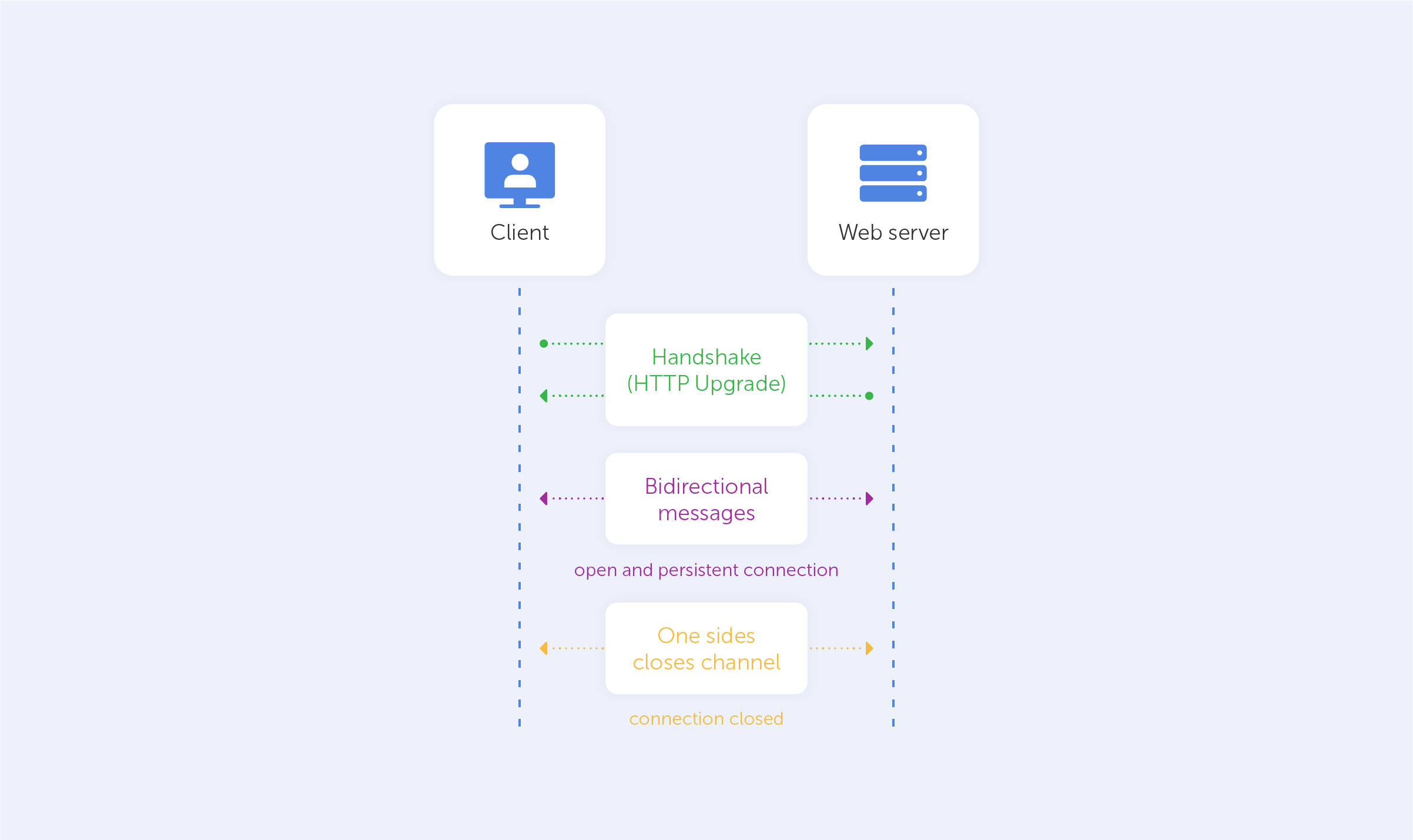
Where is WebSocket used?
1. Real-time web applications. Such services use the WebSocket to provide constant data translation to the client. This type of connection is preferred over HTTP as continuous data transmission goes through a connection which is already open. This makes the process much faster. A good example of a real-time web application is a Bitcoin trading webpage that continually pushes constantly changing data about the bitcoin’s price to the client;
2. Gaming applications. In such applications, data must be constantly transmitted from the server to the client’s computer. Otherwise, the collective acts between multiple users of the application will be unavailable;
3. Chat applications. WebSockets are used by chat applications to create a connection just once for the purpose of exchanging messages, video and audio between the interlocutors.
The Vulnerabilities of WebSocket
WebSocket technology causes a lot of excitement and at the same time disagreements among web developers. Despite all the benefits that it provides, it still has some risks as the technology is relatively new. Due to the complexity of WebSocket programming, it’s hard to provide comprehensive security for applications that use this technology. The constant transfer of data without closing the connection after every request opens up an opportunity for hackers looking to acquire access to the client’s data.
In early versions of WebSocket, there was a vulnerability named ‘cache poisoning’. It allowed the attack of caching proxy servers, particularly cooperative ones. The attack occurs in the following manner:
1. The attacker invites the client to attend a special webpage;
2. This webpage starts the WebSocket with the hacker’s website;
3. The page makes a WebSocket request that can’t be accepted by a number of proxy servers. The request passes through that server, and after that, the servers believe that the next request is the new HTTP one. But in fact, it’s a WebSocket connection that continues translating data. Both ends of the connection are now controlled by the hacker, so the hacker can transfer malicious data through the open connection. The deceived proxy-server will get and cache the malicious data;
4. Indeed, every user who utilises the same proxy-server will get the hacker’s code instead of real jQuery code.
The risk of such an attack had remained theoretical for a long time, until an analysis of WebSocket’s vulnerability showed that it really can happen.
Due to the existence of that vulnerability, WebSocket’s developers introduced ‘data masking’ to protect both parties of the connection from attacks. Masking prohibits security tools from doing tasks such as detecting a pattern in traffic.
WebSockets aren't even recognized by software such as DLP (Data Loss Prevention). They are unable to analyse data on WebSocket traffic as a result of this. This also makes it impossible for these software tools to detect problems such as malicious JavaScript and data leaks. It also makes the WebSocket connection more vulnerable than HTTPS.
Another disadvantage of WebSocket protocols is that they don’t manage authentication. This must be handled individually by any application-level protocols. Especially when sensitive information is being transferred.
The next type of cyber attack that WebSocket can be exposed to is tunnelling. Anyone can use WebSockets to tunnel any TCP service. Tunnelling a database connection right through to the browser is an example of this. A Cross-Site Scripting attack evolves into a comprehensive security breach when a Cross-Site Scripting assault is carried out.
Also, it’s necessary to know that data transfer over the WebSocket protocol is done in plain text, similar to HTTP. As a result, man-in-the-middle attacks on this data are the real threat. Thus, it’s better to use the WebSocket Secure (WSS:/) protocol to avoid data leaks.
How can we improve WebSocket security?
After looking through the main vulnerabilities of WebSocket, it’s necessary to take a look at the ways and tools that are able to protect your WebSocket connection.
First of all, good advice would be to use the wss:// protocol, instead of ws://. It’s really much safer and able to prevent a huge number of attacks from the outset.
Also, it’s necessary to validate the data that comes from the server via a WebSocket connection. Data returned by the server can potentially be problematic. Messages received from clients should always be treated as data. It's not a good idea to assign these messages to the DOM or evaluate them as code.
Another way to protect your connection is via a ticket-based authentication system. The separation of the WebSocket servers that handle headings of transmitting data from the HTTP servers hinders the authorization of headings that are based on HTTP standards. So, ticket-based authentication is a solution to this problem.
So, how secure is WebSocket?
To sum up, we can say that WebSocket doesn’t have a perfect security system, as is the case with any new kind of technology. It’s all due to the complexity of its creation and maintenance. WebSocket has enough vulnerabilities, such as a lack of authentication measures or its data input attack susceptibility, to enable attackers to transmit malicious codes. So, one should always be wary of this fact.
However, WebSocket is a progressive technology that is great to use in some spheres like gaming or trading. That’s why it should be improved to make its usage secure for every connected client or server.
How secure is WebSocket?
Upon entering your account on a website or in an app, you might be asked to enter a word or a number combination from a strange-looking picture. They are usually distorted and sometimes it can take a few seconds to determine the symbols on the picture. This security step is named CAPTCHA and seems to be useless and tedious, especially if you have some problems with recognizing and entering the right combination. But to be honest, this simple test plays an important part in the security system as it makes access to websites or online purchases wholly unreachable for bots and computers.
What is CAPTCHA
CAPTCHA is an abbreviation that can be decoded as a Completely Automated Public Turing Test to Tell Computers and Humans Apart. It’s a type of test that helps the websites’ creators minimise the ability of a bot's registration or purchasing power. They're also referred to as "Human Interaction Proof" (HIP). CAPTCHA is widely used across the internet and mobile apps alike. The most common type of CAPTCHA is the picture that contains distorted letter combinations that you should comprehend and write down in the answer box. If you wrote the right symbols, the system gives you access to the site or to the following task. You can also see a variety of CAPTCHAS on different websites. Some of them require you to take a look at a number of pictures and choose those that contain a target object such as bicycles or traffic lights.
How does CAPTCHA work?
CAPTCHA came about mainly because of certain individuals’ attempts to trick the system by exploiting flaws in the computers that power the site. While these individuals are likely a small percentage of total Internet users, their activities have the potential to harm a huge amount of websites and their users. A free email provider, for example, might be inundated with account requests from automated software. That automated application could be part of a wider scheme to spam millions of people with junk mail. The CAPTCHA test is used to determine which users are genuine people and which are computer programs.
The internet and its computers are built using a proprietary coding language. Because of the unique and complex norms that human languages adopt, as well as the slang that humans use, computers have to spend a lot of time understanding them.
Most CAPTCHAs include visual tests, which the “brain” of the computer can’t figure out; it’s much less sophisticated and it's definitely harder for them to determine the pattern in pictures. While humans will spend a few seconds on CAPTCHA, artificial intelligence has to spend much more time on finding a consistent pattern.
There’s also an alternative to a visual CAPTCHA — one that is based on audio access. That type was developed to make it possible for CAPTCHA to be passed by those who have a visual impairment. Although there are more deaf than blind, approximately 75% of all adults require some kind of visual correction, so it’s much more likely that you’ll encounter someone who can’t focus on the letters on screen. After all, they are usually quite hard to read. Usually, audio CAPTCHA is a succession of spoken characters and numerals. Frequently it also is accompanied by background noises and sound distortion to protect against bots.
The third type of CAPTCHA is a contextual one. The task for the user is to interpret some text with his or her own words, keeping the main idea of the passage. While computer algorithms can recognize significant terms in literature, they aren't very adept at deciphering the meaning of those words.
It’s also important to distribute the CAPTCHA pictures in a random order to every user. If imaging would repeat constantly or would be displayed in a specific order, it would be easy for spammers to trace the subsequence of the pictures and program a computer system that would be able to pass the test automatically based on the CAPTCHA’s order.
Turing test
CAPTCHA was based on the Turing Test. Alan Turing, an ingenious mathematician, who was named “the Father of modern computing”, suggested this test to find out whether the computer is able to think like a human or not. The point of the test is that there are a number of questions that must be answered by two participants. One of them is a real person while the other is a computer. There’s also an interrogator whose task is to find out which answers were given by the machine and which ones were given by the human. If the interrogator isn’t able to understand who is who, the test has been passed.
The main goal of CAPTCHA’s creators was to create a test that could be easily passed by a human, but not by a machine.
The pictures that we see on the screen that we need to pass the captcha test are usually very complicated as it must be possible for every user to enter it. But bots are mostly unable to determine the text that is presented in the form of a picture.
Who uses CAPTCHA?
CAPTCHA is a type of verification tool that is widely used by websites and apps to ensure that a user is not a robot.
It is usually used to protect online pools from bots’ votes employed by scammers to cheat. Another purpose of using CAPTCHA is to restrict access to websites where consumers can create free accounts, such as Gmail. Spammers can't use bots to establish a slew of spam email accounts because of CAPTCHAs.
CAPTCHA is also used by ticket services to prevent profiteers from buying too many tickets for big events. This helps honest people to buy tickets in a fair manner while preventing scalpers from putting in hundreds of orders.
Finally, CAPTCHA is used to prevent spamming messages or comments on websites where it’s possible to contact the page’s user directly. It helps to stop bots from automatically sending spam and spoiling the ratings of products or services.
To sum up, CAPTCHA is a good tool to prevent the creation of spamming bots or automatically controlled web pages that spread viruses. It helps the creators of apps and websites to verify that a user is a real person, and not a computer programmed to spoil the system. This small but necessary stage of identification of the user is really helpful and recommended for exploitation on any websites where users are able to create free accounts. If you want to use CAPTCHA to protect your own website, you should be aware of the numerous failure possibilities that you may encounter. We recommend using a service like Google's reCAPTCHA to generate one for you. It’s also a good idea to download an antivirus program and use it together with CAPTCHA to keep your device secure.
CAPTCHA — How does it actually work?
When we look at the statistics, the number of cybercrimes increases year on year. Hackers have invented a wide range of tools that can crack your password or get your access information with ease. But there are also other ways of violating your privacy. Every click you make is tracked by websites, advertising agencies, ISPs, and other third parties. Thus, you need to secure your privacy online using a web browser optimised for making your web-surfing secure. So, which browsers are really designed to preserve your personal data and prevent leaks?
Everyone knows that Microsoft Edge or Safari are built into smartphones and laptops supported by the corresponding operating systems. So most users are unconcerned about the browser they use assuming that the default option is the best one. Although browsers like Safari, Google Chrome, or Opera are the most common, they really can’t pretend to be the most secure and privacy-conscious. Indeed, there are some less common but highly powerful and privacy-focused browsers that could provide you with plenty of embedded privacy settings that can block cookies, ads, and data tracking. It’s pretty difficult to name the best one as each of them contains its own privacy features enabling them to become contenders for victory. So let’s go through these browsers and their privacy customizations to help you make the call.
1. Tor Browser
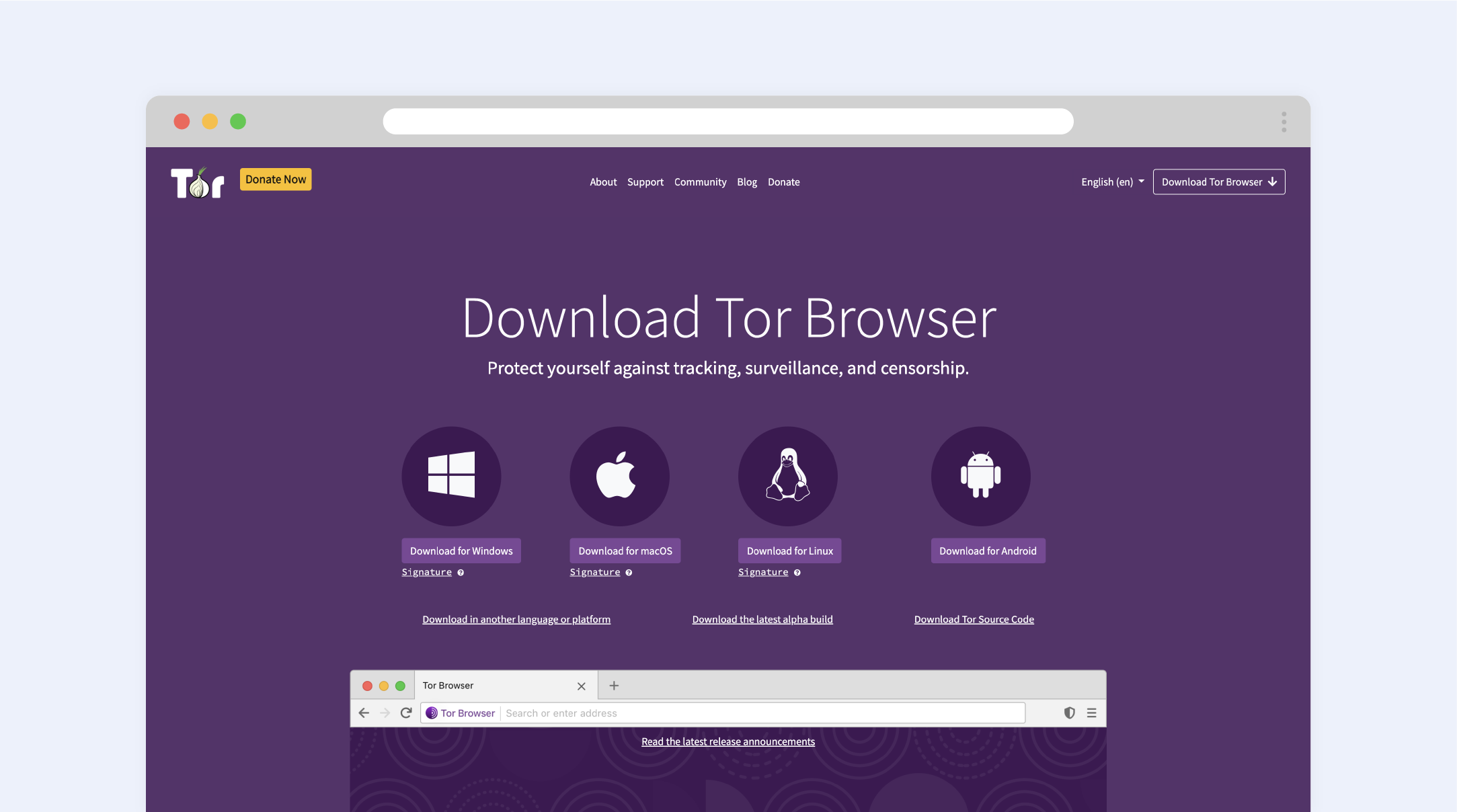
Tor is one of the well-known privacy-oriented browsers. It is based on Firefox’s browser and equipped with its own hidden relay servers that are focused on anti-surveillance functions. It automatically erases your cookies and browsing history on the fly. Tor makes users’ internet access anonymous by encrypting their traffic in at least three separated layers (nodes) that are decentralised and run by volunteer computers. Each node focuses on a single layer of encryption, making it impossible to get the entire message in any of them. Thus, no one can trace your online activity or identify you until you deliberately identify yourself. The unique technology of Tor is also available to lessen the uniqueness of your fingerprint, which is an unmatched feature in successfully decreasing the possibility of identifying a user.
Of course, Tor Browser has its drawbacks. Due to the complexity of protecting certain processes, the speed of your internet could be affected. Also, the NoScript function may break some websites. Moreover, there is a possibility that law enforcement is able to see who is using the Tor browser, even if they are not aware of what people do there.
2. Brave
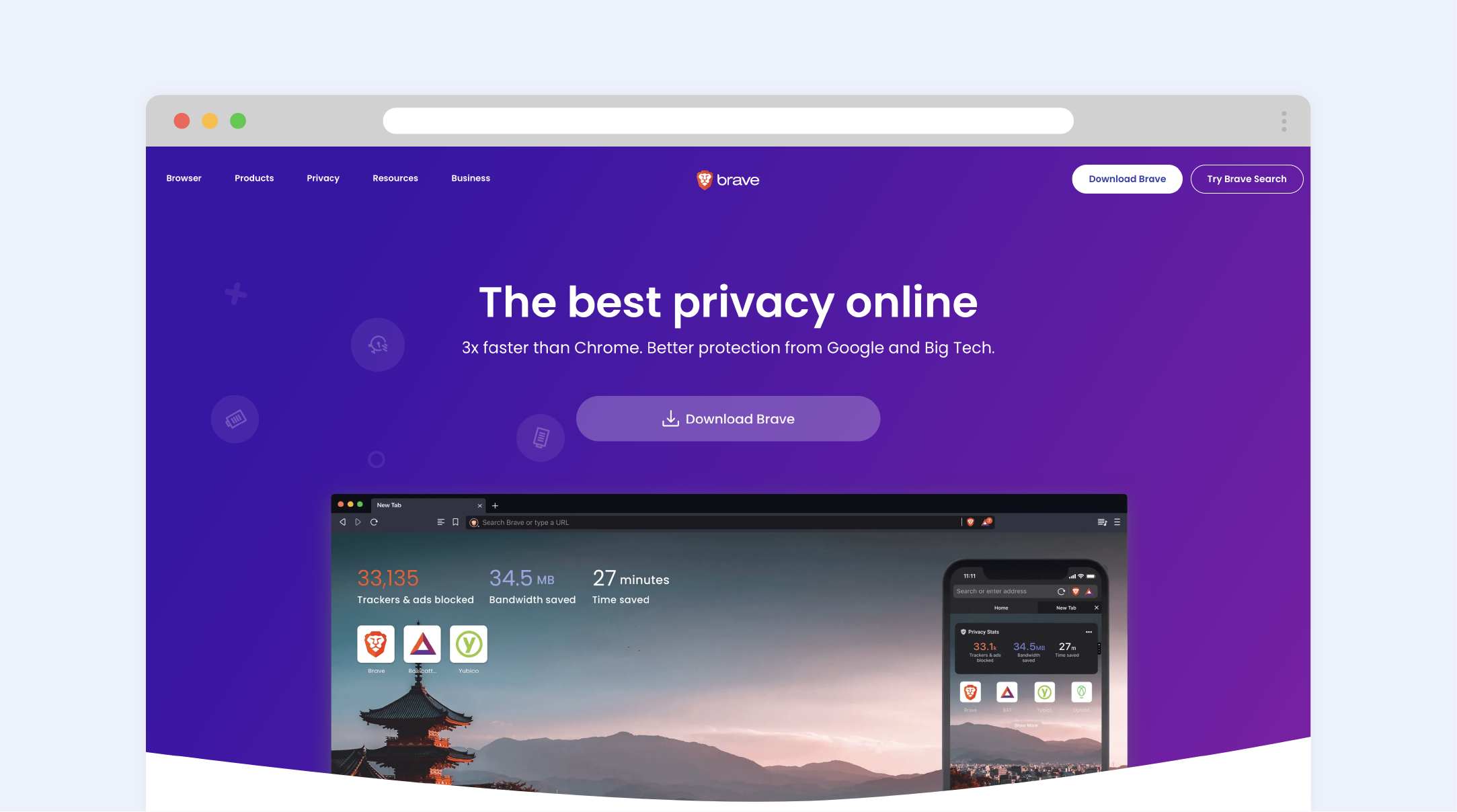
Brave was founded in 2016 and despite it being a quite new browser, it is worth considering. This privacy-focused browser is based on a Chromium network and truly packs a punch with features like an ad-blocker, anti-tracking, and anti-fingerprinting technology. Brave also automatically changes your connection to HTTPS, as it's always important to have a safely encrypted connection. The security options of this next-generation browser enable you to choose which data to erase when you exit the program. Another useful thing is the embedded feature that could prevent scripts from launching. Recently, Brave entirely switched to a Chromium core, which simplified the process of bringing over their Chrome extensions. It allows the browser to be made more functional and convenient. Nevertheless, users still should be cautious in selecting extensions, as it’s important to use ones that respond to individual security requirements.
Despite the fact that Brave is open-sourced, some users may be wary of its Chromium foundation. Brave’s advertising model is particularly contentious, as it favours adverts that benefit the browser over those that benefit the websites you visit.
3. Mozilla Firefox
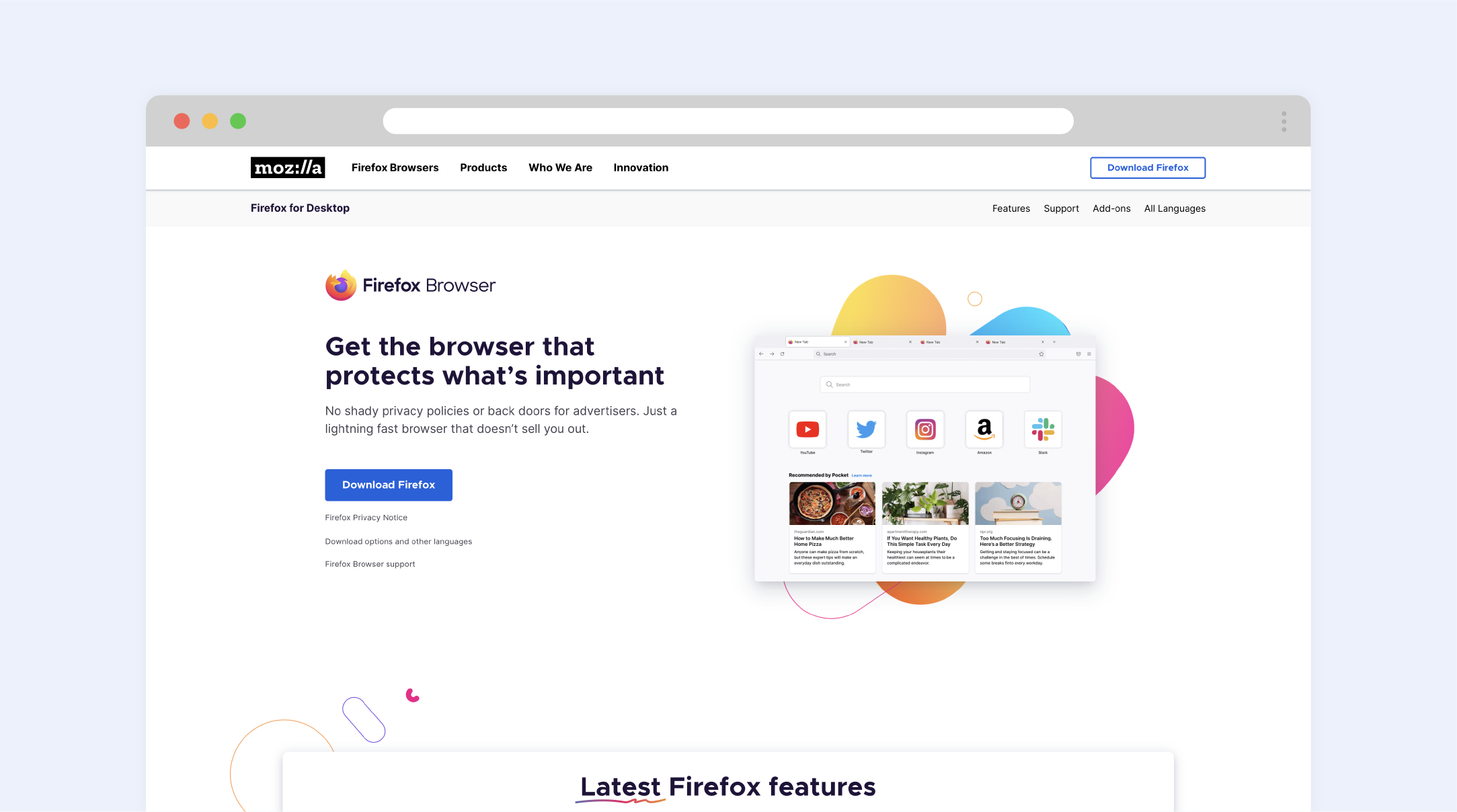
Firefox is well-known for the variety of settings and extensions that it provides for its users. It’s one of the more commonly used alternatives to Chrome or Safari. Although Firefox doesn’t release updates as frequently as the previously mentioned browsers, it does so on a regular basis. If we take into account the fact that Mozilla is a non-commercial organisation, it’s worth evaluating the work of the company’s volunteers, who do a great job to ensure that Firefox has the most up-to-date security systems in place. Firefox’s security features really have something for everyone. It includes phishing and malware protection, for example, banning attacked websites, and informing the user about attempts of installing site add-ons. It’s also equipped with ad blockers and tracker-detection systems. Moreover, it’s easy to use due to its minimalistic style and simplicity. However, be sure to turn off the telemetry feature as it shares your browser’s data with Mozilla. Such features might disturb the users that appreciate their privacy, but that can be easily disabled via the settings tab.
4. Epic
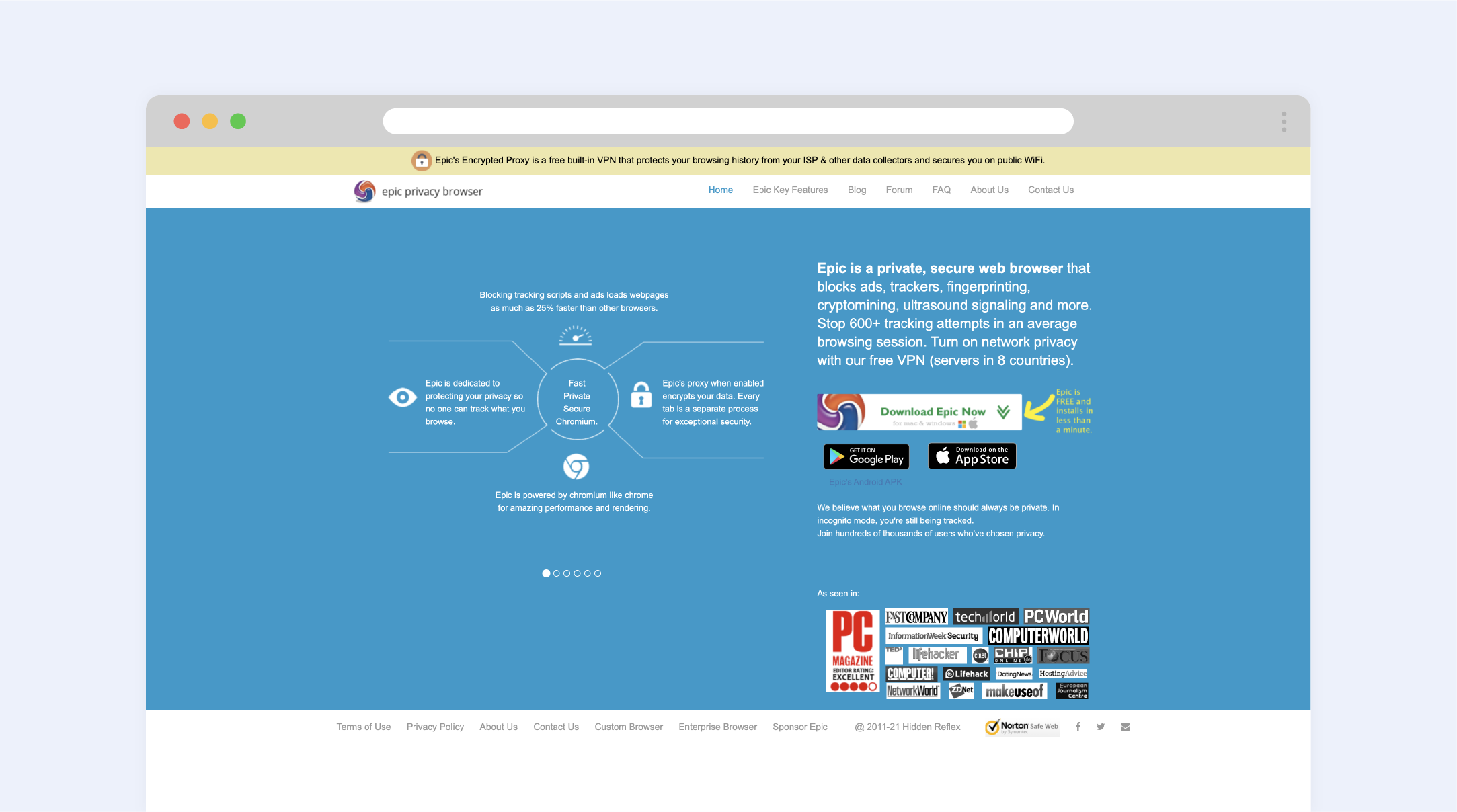
The main point in using Epic is that you’re able to benefit without changing the built-in extensions. It’s already configured to make the process of internet access secure and confident. Its customizations will block cookies after every session, preventing data tracking and unwanted ads. Epic also has an option to search the information via DuckDuckGo (A privacy-focused search engine that is a good tool to ensure your personal data stays safe). This browser is fundamentally aimed at making your internet access private. It disables auto-syncing, spell-check, auto-fill, and many other functions that can collect users’ personal information. Of course, it doesn’t save you browser history, access credentials, and cookies. Epic also aims to hide your IP address in any possible way in order to protect the information about your location and your device’s data.
While the settings focused on high privacy can disable some sites and functions, which means the browser is not ideal in all cases, extensions can be changed at the expense of privacy.
The explicit disadvantage of the Epic browser is that it’s based on the Chromium code, which is not open-sourced. So there’s no certainty that this code will be independent in the future.
Conclusion
So, what browser can be named the best one suited to protecting your identity and personal data? Well, none of them can be completely private. There are a number of browsers that claim to be the most private and protected ones, but even they have flaws that can disturb some users. So, you should choose the browser that mostly satisfies your own requirements and seems to be the best one for you. In this article, we’ve collected some facts on the ‘chef’s pick’ of browsers. Now, the decision is in your hands.
What is the most private internet browser in 2022?
What is a brute force attack?
Among a myriad of different cyberattacks, the brute force attack seems to be the most common and primitive way of hacking. This technique involves guessing login information through trial-and-error, where hackers try all conceivable combinations in the hope of guessing correctly.
The term “brute force" refers to the method itself, being both brutal and forceful. Despite the fact that brute force attacks are a pretty ancient cyberattack approach, they still remain a prominent technique among modern-day hackers.
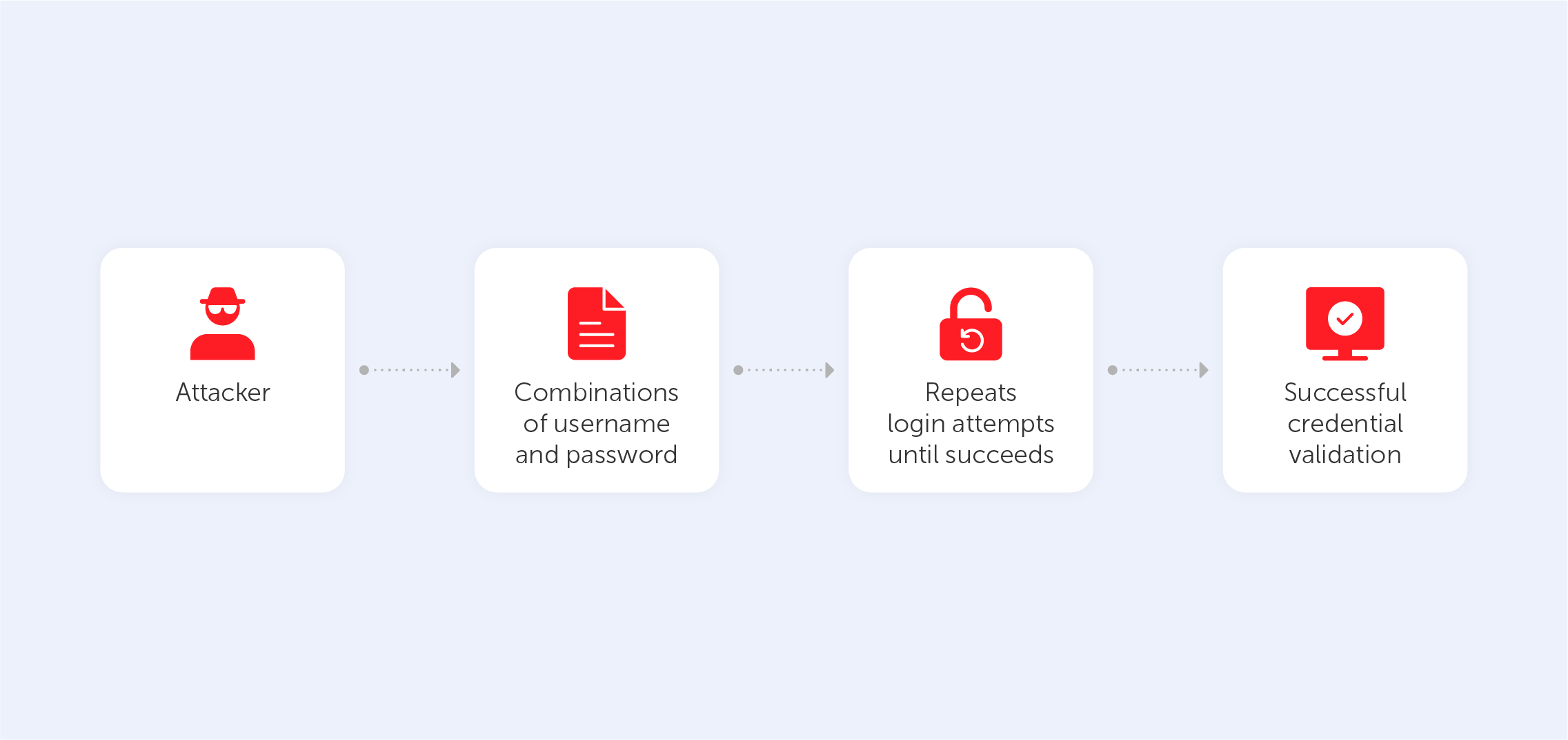
Types of brute force attacks
A brute force attack can be split into a few different types, each kind employing a variety of techniques that serve to unearth your private data. You should be aware of how cybercriminals apply each type in order to ensure maximum protection.
1. The simple brute force attack — this refers to the process of simply guessing the login credentials via logical deliberation, without the use of any software. Hackers just go through every standard combination of letters and numerals, perhaps combining this with some information that they know about you. This method is cumbersome yet reliable as many people still use primitive and common passwords and PINs like “user1” or “12345” in order to remember it easily. Also, users, who use the same password for every account put themselves in extra danger; if the hacker does guess one password correctly, then it’s likely that they’ll be using that password as the first port of call when it comes to other accounts.
2. A dictionary attack — this is a type of brute force attack that involves the user submitting a very large variety of different password combinations. Although this kind of assault is technically a brute force attack, it takes a significant place in the process of cracking passwords. The name of this technique comes from the actions that a hacker performs during the break-in attempt. The criminals scan through password dictionaries modifying words using different numbers and abbreviations. It usually takes a lot of time and has poor success rates when compared to newer techniques. However, it’s easy to do if you have a computer at your disposal.
3. A hybrid brute force attack — this type combines the two that we’ve just looked at: the brute force attack and the dictionary attack. Combination passwords, which mix common words with random characters, are cracked using these approaches. Usually, it starts with a certain username which is used as a base for the following actions: hackers input a list of words that potentially could be included in the password, then combine them with different characters and numbers until they reach the correct password.
4. Reverse brute force attack — contrasting with other types of brute force attack, the reverse attack starts with a known password. Usually, hackers get these from leaked databases that are freely available on the internet. Attackers choose one password and look through millions of accounts until one matches. Of course, it’s easier for the criminal to locate a match when the password includes a name or a birth date, so it’s better to avoid using such information in your password.
5. Credential staffing — this type of attack is based on users’ cybersecurity illiteracy. Hackers collect and store lists of already cracked or stolen passwords and usernames connected to them and then go through dozens of other websites to see if they can obtain access to other accounts of the same user. Thus if the person utilises the same password for various social networks, apps and websites, he or she allows the attacker to get every bit of private information contained on each account.
6. Botnets — this type of attack can be combined with any of the above. The main point of a botnet attack is to use extra computational resources to attack the victim. This way, hackers manage to avoid the costs and difficulties associated with running programs on their own systems by exploiting hijacked machines to carry out the brute force attack. Furthermore, the usage of botnets provides an additional layer of anonymity which is also desirable for hackers.
Brute force attack tools
It can take a long time to crack the password of somebody’s email or website, so hackers have created some software to assist them in breaching accounts, which makes the process easier and faster.
1. Aircack-ng is a toolset that provides the hacker with the opportunity to enter various Wi-Fi security systems. They’ll be able to monitor and export data through the use of this software. They can even hack companies using techniques such as spoofing access points and packet injection. Such software is free and can be acquired by anyone.
2. DaveGrohl is a brute-forcing tool that was made to assist in dictionary attacks. It offers a mode that helps hackers to attack a victim using the force of several computers.
3. John the Ripper is a program made for recovering passwords. It supports thousands of encryption systems including those used in macOS, Unix, Windows, various web applications, network traffic, and document files.
These programs can quickly go through all conceivable combinations and choose the correct one to breach a variety of computer protocols, encrypted information storage systems and modems.
Examples of brute force attacks:
Brute force attacks are so common that almost every person or organisation has at least once fallen victim. Even worldwide organisations that are known for their robust security systems could be exposed to a brute force attack. For example, in 2018, it was uncovered that Firefox’s master password was quite easy to figure out. Because of this, nobody knows how much personal data was actually leaked into the network. This wasn’t the only brute force attack to occur that year. Unknown hackers compromised the accounts of numerous members of the Parliament of Northern Ireland.
Three years before that, Dunkin Donuts, a doughnut and coffee franchise, became a victim of another brute force attack that resulted in people losing large quantities of money due to a breach that took place in the company’s mobile app. Cybercriminals utilised brute force to obtain illegal access to the credentials of more than 19 thousand people, eventually taking their money. Unfortunately, the company didn’t make users aware of the attack and people couldn’t take the appropriate precautions to protect their personal data and money in the future, so a complaint was eventually filed against it.
Despite most people actually being aware of the measures required for privacy maintenance, a lot of users still disregard the rules of cybersecurity by trying to simplify access to their accounts with a simple, reusable and easily memorable combination. This way, they make themselves potential victims of brute force attacks, which are largely possible thanks to the carelessness of cyber-civilians.
The brute force attack: definition and examples
Hacking attacks are often pretty minor and can include things such as personal data theft for the purpose of extortion. These attacks usually fail, but can sometimes be really devastating when the subject is a business or government organisation; we’re talking huge monetary losses. There are a huge variety of applications and software that were created to protect users from theft of data that is kept on their electronic devices or online accounts, and one of them is a firewall.
What is it?
A firewall is a network security system that filters incoming and outgoing network traffic according to the firewall's rules settled by a user. The main goal of the firewall is to minimise or just to remove undesired network contacts and let in all admissible communication. Firewalls are a significant part of cybersecurity and can be used in parallel with other tools to provide a high level of personal data security.
Firewalls are useful for every Internet user, no matter if we’re talking about a company or an individual user. Hackers can attempt to exploit every computer connected to the network in their malicious purchases. Your computer might be hacked in order to spread damaging links through your email or social networks accounts. That’s why you should be aware of how to protect yourself from breaches.
A firewall can be built into an operating system; an ordinary user usually doesn’t notice the work of this protective system until it reveals a threat in an incoming file.
What is inside it?
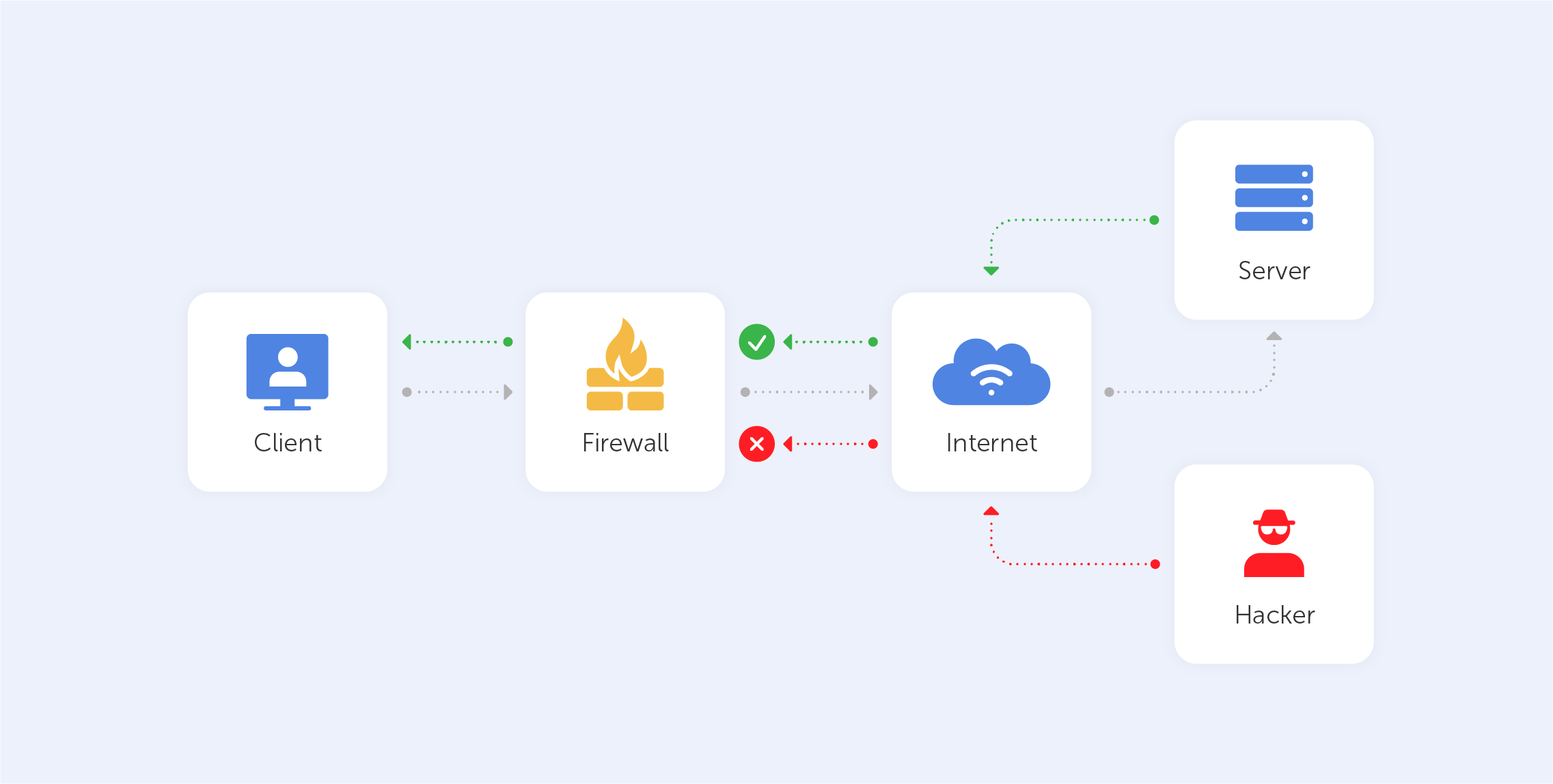
A firewall could be a type of software or hardware that looks for threatening elements that have been flagged as dangerous. Hardware options for intercepting traffic travelling between the broadband router and user devices are frequently included in routers. Software options are programs that track the data that enters and exits your computer. Regardless of the type, the main function of the firewall is to block the access or dispatching of data packets that have been identified as a safety risk. This reversible security system not only protects your computer from attacks but also prevents the spread of malicious data through the network. It can also be used to block unwanted applications.
For example, if an employer wants to control the work of its employees, they’re able to set the system to block certain apps such as Skype, gaming apps, or social networks. Also, firewalls provide an opportunity to block unwanted advertising while controlling access to traffic. A good example of this function can be found when connecting to certain kinds of public WiFi, specifically when you should enter your phone number or email address to get access.
Now let's take a look at the three most common types of firewalls: packet filtering, proxy service, stateful inspection and NGFW. Of course, they are quite different in how they monitor and filter network communication.
Packet filtering
Packet filtering, also known as a ‘stateless’ firewall, analyses particular packets (little data units) one at a time using a set of filters. Thus, the system finds out and stops packets that contain danger while allowing the rest to proceed to their destination. This type of firewall is based on the filtration of unique headers of the packets — the main part that contains basic data like the origin of the packet and its destination.
Proxy service
An application firewall (or proxy service) is quite an efficient tool. It acts as a cyber agent rather than a filtering system. They safeguard your network location from any malicious actors by effectively producing a ‘mirror’ of the computer behind the firewall that excludes the possibility of direct communication between your computer and the information itself. But this type has some flaws. Primarily, it works slower than firewalls of other types and generally has application limitations.
Stateful inspection
Stateful firewalls are more versatile than the previous types as they are able to evaluate not only the headers of the packets but also the variety of aspects that each data lot contains. To pass the firewall, the incoming packet must correspond to the trusted information defined by the firewall rules. This type of firewall is the most streamlined and provides efficient security.
NGFW
The last genus of firewalls is also attributed to application firewalls, although developers usually call them next-generation firewalls (NGFW). This type includes the best of the previous generations of firewalls and also includes a more comprehensive double-checking of packets. It prevents system mistakes in detecting potentially threatening traffic. The newest firewalls are also equipped with extra security systems like VPNs, IPSs (intrusion prevention systems), and identification control systems. This allows users to utilise just one app or kind of software for multi-layer security.
By using firewalls, you mitigate the risks of data theft and the unauthorised entry into your personal devices and accounts. These systems provide safety by establishing protective filters inside every part of your network to detect and eliminate threats like backdoors, viruses, remote logins, or spam.
Also, firewalls vary depending on their appointment. Some of them were created for personal or small-group (under 100 people) use. A good example is a firewall that is built into the Windows operating system. Others have been developed for companies with 1,000 or more employees. These ones should be attentively set up and are usually controlled by an in-house company programmer.
Now, let's talk a bit more about system-based firewalls. As previously stated, traffic that passes through a firewall is compared with the firewall's rules to figure out whether it can be accepted into the system or not. The program contains a list of rules which is consistently compared with incoming data packets. Every rule begins with an index word: accept, drop or reject. The system acts according to those words and the following directions. If the packet satisfies the direction indexed with ‘accept’, it’ll be accepted. Indeed, if it satisfies the ‘reject’ direction, that traffic will be blocked with an ‘unreachable’ error tag. Also, the ‘drop’ means that the traffic will be blocked without sending a reply.
That is, of course, just a ‘tap on the water’ explanation of what a firewall is. For a deep dive, visit https://www.bu.edu/tech/about/security-resources/host-based/intro/.
What is a firewall and how does it work?
Almost every user of the internet faces hacking at least once. Cybercriminals have invented a wide range of techniques that aim to crack your password or harvest the credentials and personal data including financial and banking details that are stored on your computer. The timely detection of break-ins may save your privacy and protect your data from being compromised. That’s why you should always be aware of the signs of being hacked and the actions to be taken if you do find yourself in such a situation.
To begin with, it’s important to confirm whether you’ve been hacked or not. Nowadays, the Internet provides multiple ways to do it:
1. Information about almost every cyberattack is available on the Internet. Various news sources publish alerts about data breaches that could be an early indicator that your account has been compromised and that you should take action. Indeed, it’s important to make sure that you have at least one reliable source which provides information about cyberattacks.
2. There is a range of websites available that provide information about every hacked account. One of them is “Have I Been Pwned” which contains a wide database of records about cyberattacks and compromised accounts. To check the security of your account, you should just enter your email address and the system will tell you if your data was the subject of a hacker attack. A positive result doesn’t guarantee that your privacy was violated by cybercriminals, but it does mean that some of your login credentials may have become publicly available.
3. Another powerful tool for ensuring the security of your data is Dehashed.
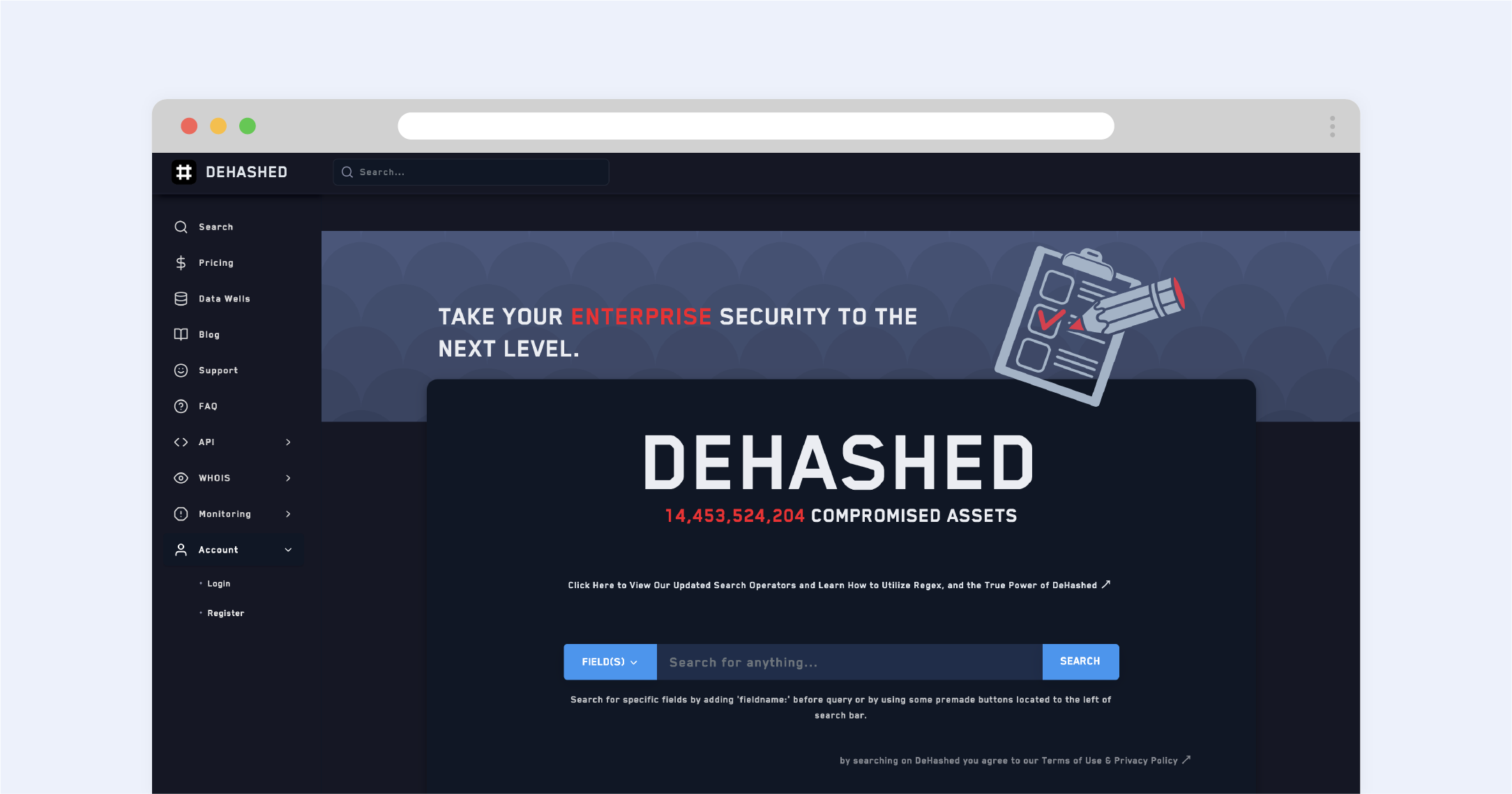
It's a more comprehensive program than the previous one. Just enter any keyword connected to your account like an old username and Dehashed will surf the Internet to check whether that nugget of your private information has been leaked to the public.
4. Most official public apps and sites alert users about access attempts by sending emails or text messages. So, if you get suspicious alerts that someone has accessed your account from a peculiar IP address or at a strange time, check your VPN to make sure it wasn’t you, and if it wasn’t, there’s a high likelihood that you’ve been hacked.
5. To mitigate the risks of being hacked, check the security of sites that you use regularly. There are a lot of tools that can help you to do that. One of the best is the Sucuri Site Checker. To find out if one of your daily used sites was attacked or endangered your private data, you should enter the website link and the program will provide you with information about any threat that the site could pose. If you reveal that the website you use every day is risky, it would be better to change the password of any account connected to that site and also check the safety of your accounts with the tools aforementioned.
It’s also worth checking for suspicious activity on your account manually. Many sites and apps provide the possibility of tracing recent activity and it’s a wonderful way to find out if anyone else has been using your account. This feature gives information about where, when, and from what device you logged in. Frequenting this setting is the thin end of the wedge of successfully protecting your data; it ultimately prevents any undetected interference. If you have some active sessions opened in an unknown place or from an unknown device, you’ll be in the know. Such an issue can simply be solved by changing the password and logging out all existing sessions. Besides, it's better to protect your account by activating two-factor authentication in addition to changing the main password.
What should you do next?
First of all, you should notify your friends, colleagues, and other people you contact through the hacked account to make sure that they don’t fall prey to the activities of your hacker. Most shallow cybercriminals use your account to prolong the hacking chain. They pretend to be you and send messages or emails asking about material help for an ill grandma or for a phone number to send an SMS with a malicious link, pretending that it is needed to recover access to a locked account of theirs. Nowadays, almost everyone knows about such criminal ploys, but elderly people or loved ones often still fall victim. Thus, it’s necessary to alert everybody that someone else is using your account for the purposes of scamming.
The next significant recommendation is not to pay the ransom. If you received a message from the scammer telling you that you have to pay for the safety of your data, just don’t respond and you won’t have to pay. The main reason why hackers breach your account is to get money. If he understands that you won’t pay, they’re more often than not going to leave you alone. But, if you’re still worried about the security of your data, you should contact your local law enforcement agency. Another reason why you mustn’t pay the ransom is that you indirectly promote the hackers' actions; you’re investing in their endeavour and stimulating their activity. Moreover, they might see you as a cash cow and try even harder to extort you in the future.
The next course of action in taking control over your account is changing your password. Indeed, use your noggin to figure out which sites may use the same password, and change those passwords too; it goes without saying that you shouldn’t reuse the same password on multiple websites. It’s also worth using a password generator to acquire new passwords, consisting of sophisticated alpha-numerical combinations that are naturally hard to guess.
In some instances, cybercriminals will anticipate these steps if they feel that their cover is blown, and they’ll beat you to changing your password. In this situation, you should contact the site’s support team to prove that you’re the true owner of the account. Sites such as Facebook will ask you to upload a proof of ID, for example. To prevent hacking from happening in the future, it’s worth taking advantage of the ability to link your email address and phone number to your account.
Recovering access to the account is time-consuming, as all the information ought to be checked manually. So, if you get in such trouble and find yourself waiting to get back your account, take some time to reflect on getting yourself a good-quality password manager that will eliminate the burden in the future. Hint hint.
How to check if you’ve been hacked & the next steps
Which words pop into your head when creating a password for your new account on a website or on a social network? Safety? Privacy? Well, there’s some bad news for you here — in our digital world, hackers are clued-up on hacking any kind of password that you can think into existence, and as a matter of fact, it’s a global problem. Users of the internet can never be sure that their accounts are protected enough to prevent data theft. Even global organizations such as Facebook can be the subject of cyber-attacks. And we mention the social giant for good reason too — in March 2020, the British company Comparitech stated that the data of more than 267 million people was leaked.
Ergo, it’s of paramount importance to know which techniques cybercriminals use to hack your password and steal your private information. There are a great number of methods that hackers can use to deceive people in order to steal private credentials and data. That’s why, today, we’re going through the most common techniques that can be used, so you’ll be in the know and much more secure online as a result.
1. Phishing
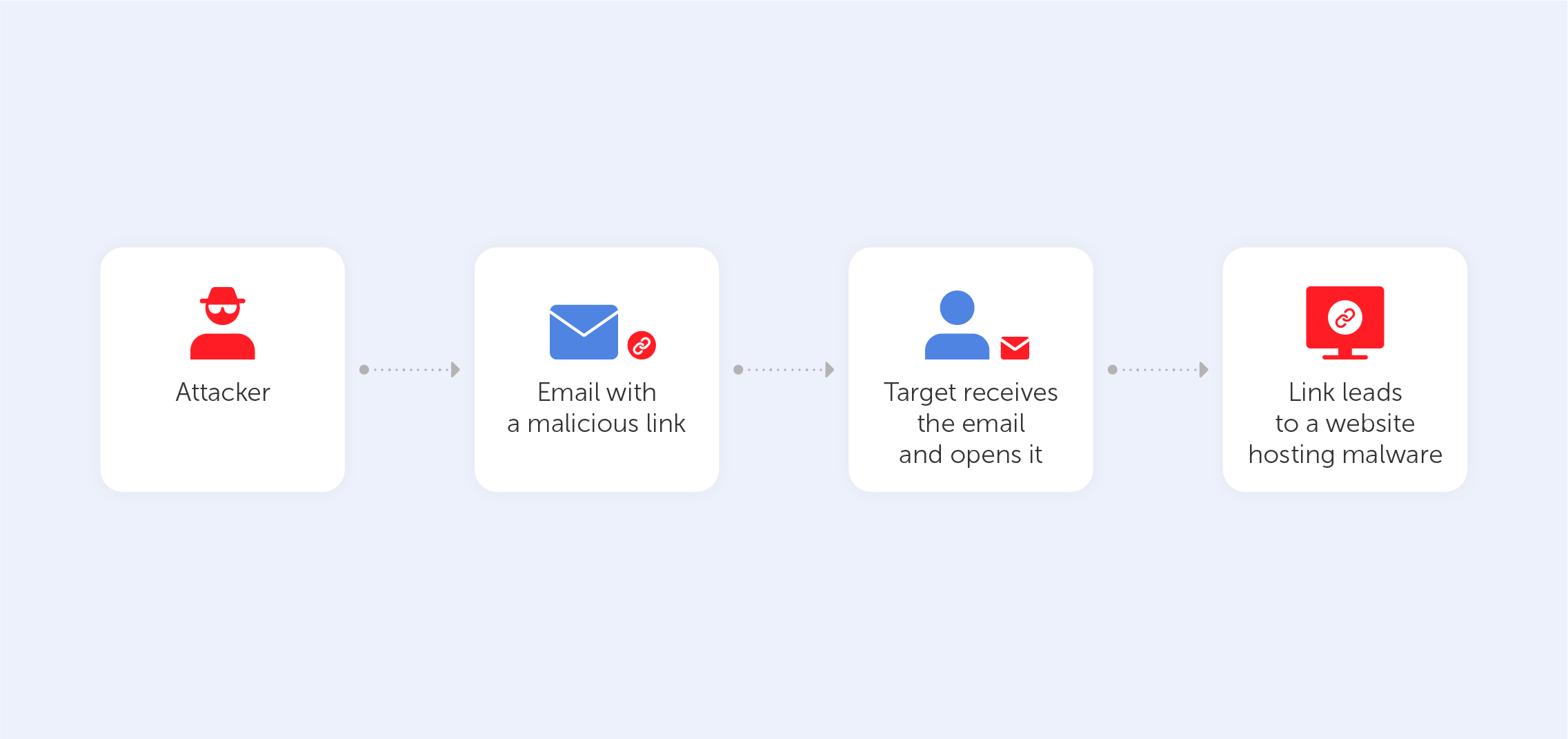
The easiest and most common way of hacking someone’s password is phishing. There are plenty of techniques here: phishing can take the form of an email, an SMS, a direct message on a social media platform, or a public post on a website. Cybercriminals spread a link or attachment that hooks an internet user in. Pushing leads a victim to a fake log-in page where he or she has to enter their data. After hacking, the hackers get a variety of data that can be used for any purpose. This way, people get their sensitive information served on a silver platter. As this technique is one of the oldest ones in the book, most users are aware of such a ploy. Almost everyone knows that following a suspicious link on the internet is a sure way of compromising yourself. Indeed, that’s why emails from unknown addresses tend to fall straight into the spam box and we’re used to blocking unknown numbers.
2. Social engineering
This type of cyberattack is based on the mistakes and imprudence that come as standard with the human brain. A criminal tricks the victim by acting like he or she is a real agent of an official company. It might be a fake call from your bank or some kind of technical support branch. You’ll likely be asked to provide confidential data so that the ‘agent’ may investigate ‘suspicious activity’ on your bank account. Usually, social engineering is mostly successful in manipulating pensioners due to their often dull mental blade and trusting nature. This technique is quite widespread and is much easier than creating an entire fake website to phish someone’s password.
3. Brute force attack
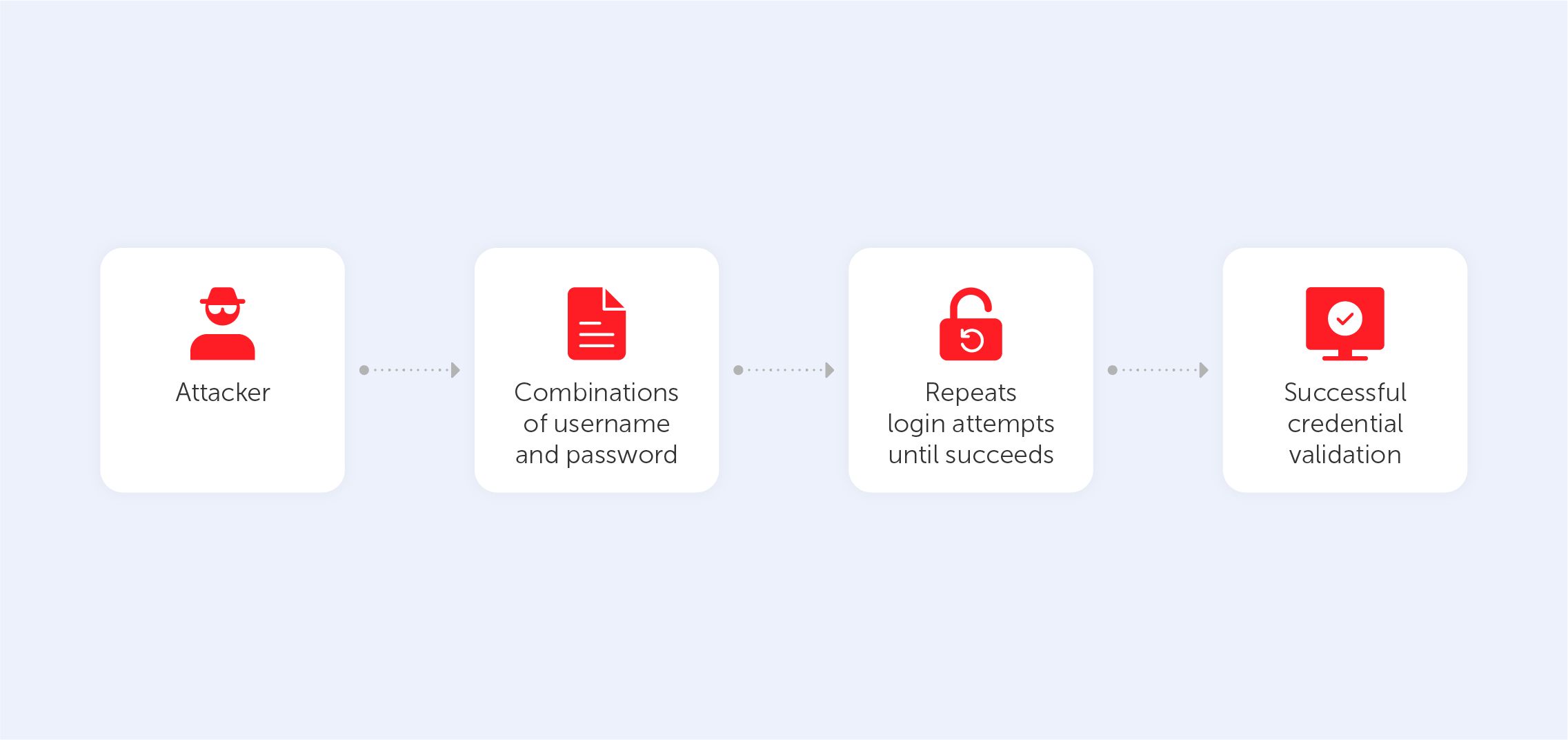
Brute force attacks are best characterized by the long, heavy method of checking each possible password variant. This way is really time-consuming, so most hackers use special software to automate the process. Most of the time, such attacks are based on knowledge gained from previous cracks as users often reuse their passwords on multiple websites and platforms. Also, cybercriminals might try lists of common variations of letters and numbers. That’s why, to protect yourself from such attacks, you should use as many symbols as possible and create passwords from unconnected words and unpredictable alpha-numerical compilations. Alternatively, you could use a password manager to automate this struggle (nudge nudge).
4. Dictionary attack
The dictionary attack partly resembles the previous method (brute force attack), the main idea of such a cyber attack is to submit all possible password variations by taking words from the dictionary. It makes the process of researching the right combination easier due to the strict structure of the dictionary. Moreover, it takes less time to crack the password If the hacker knows some sensitive information about the victim, like the name of their child, pet, or favorite color, for instance. Indeed, predictable human nature is the reason why this is such an effective method. To eliminate the possibility of such a cyberattack, it’s worth mixing semantically unconnected words, numerals, and other symbols. The best way, of course, is to get a password manager (nudge nudge).
5. Rainbow table attack
Passwords stored on the victim’s computer are usually encrypted. The plain text is replaced by various strings (hashes) to prevent data leaks. This method is named ‘hashing’. However, this method doesn’t guarantee that the password won’t be cracked; hackers are very familiar with such multi-layer security. The ‘rainbow table’ is a list of passwords and their hashes that have already been acquired through previous attacks. Hackers try to decrypt hashes by figuring out the correct combination based on different variations from the rainbow table. As a result, the password’s code may be retrieved from the database, removing the necessity to hack it. A good way to mitigate the risks of such an attack is to use software that includes randomly generated data in the password before hashing it.
6. Spidering
Many companies base their passwords on the names of the products they produce to help their staff remember the credentials that they need to access corporate accounts. Spidering is a type of cyberattack that uses this information to hack the company’s system and exploit the obtained information for malicious purposes. They surf the sites of organizations and learn about their businesses. Then, this knowledge is used to make a list of keywords that can be exploited in brute force attacks. As this process is quite time-consuming, experienced hackers utilize automatic software such as the infamous ‘web crawler’.
7. Malware
Malware is a harmful kind of software created to steal private information from the computer that it has been installed on. The victim gives access to his or her computer by clicking on a link specially made by cybercriminals. While this technique has various forms, the most common are keyloggers and screen scrapers that take a video of a user's screen or screenshots when passwords are being entered. They then send this data to the hacker. Some kinds of malware can encrypt a system’s data and prevent users from accessing certain programs. Others can look through users’ data to find a password dictionary that can be used in a variety of ways.
The amount of techniques being used by hackers to crack our passwords is increasing exponentially. The more ways there are to prevent break-ins, the more work hackers ought to do to get around them. That’s why, you should leave it to us, Passwork, your neighborly password managing wizards, to lift the burden from your shoulders.
Password-cracking techniques used by hackers
If you've heard of ‘SHA’ in various forms but aren't sure what it stands for or why it's essential — you’re in luck! We'll attempt to shed some light on the family of cryptographic hash algorithms today.
But, before we get into SHA, let's go over what a hash function is and how it works. Before you can comprehend what SHA-1 and SHA-2 are, you must first grasp these principles.
Let's get started.
What Is a Hash Function?
A hash function relates to a set of characters (known as a key) of a certain length. The hash value is a representation of the original string of characters, however, it is usually smaller.
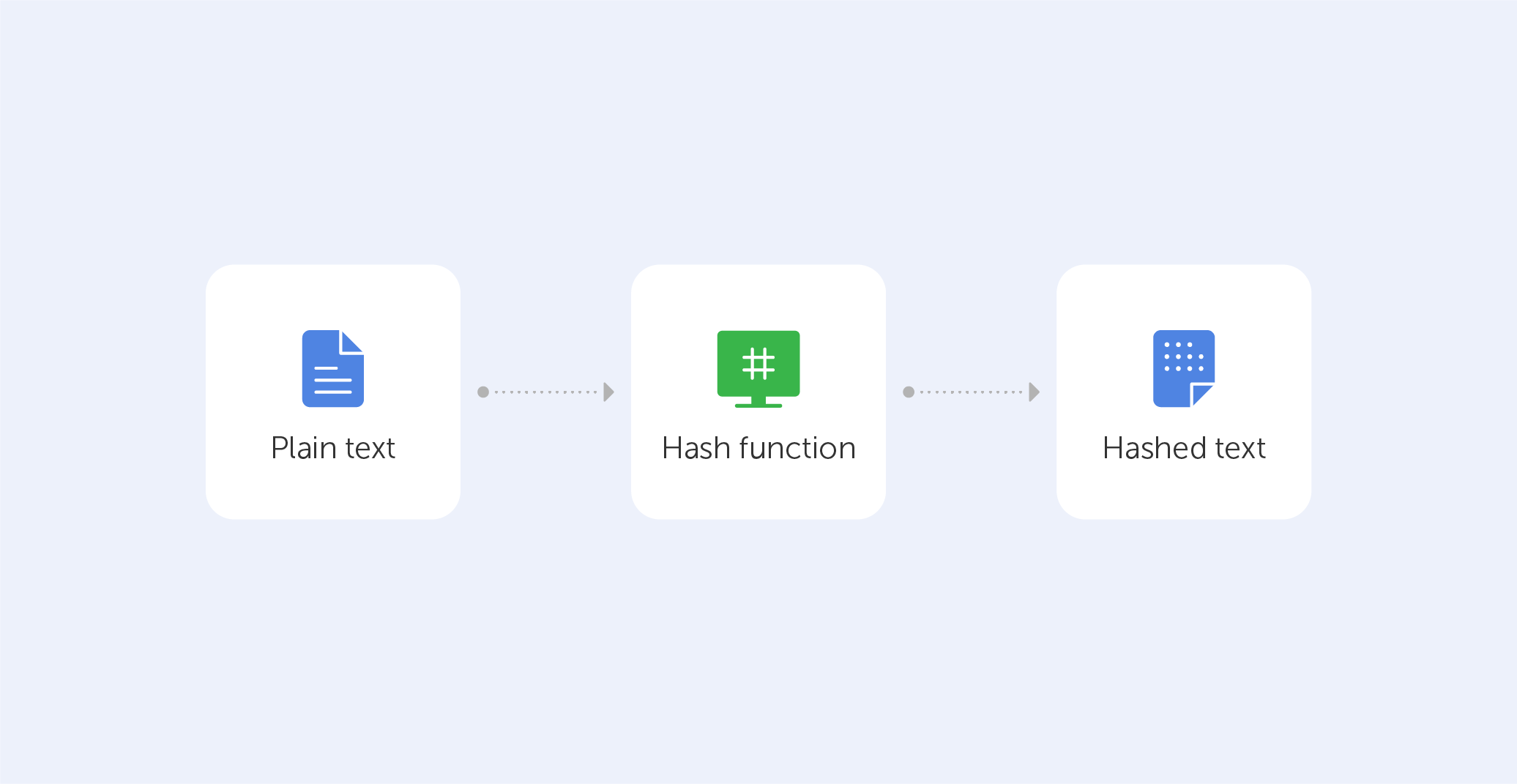
Because the shorter hash value is simpler to search for than the lengthier text, hashing is used for indexing and finding things in databases. Encryption employs hashing as well.
SHA-1, SHA-2, SHA-256… What’s this all about?
There are three types of secure hash algorithms: SHA-1, SHA-2, and SHA-256. The initial iteration of the algorithm was SHA-1, which was followed by SHA-2, an updated and better version of the first. The SHA-2 method produces a plethora of bit-length variables, which are referred to as SHA-256. Simply put, if you see “SHA-2,” “SHA-256” or “SHA-256 bit,” those names are referring to the same thing.
The NIST's Formal Acceptance
FIPS 180-4, published by the National Institute of Standards and Technology, officially defines the SHA-256 standard. Moreover, a set of test vectors is included with standardization and formalization to confirm that developers have correctly implemented the method.
Let’s break down the algorithm and how it works:
1. Append padding bits
The first step in our hashing process is to add bits to our original message to make it the same length as the standard length needed for the hash function. To accomplish so, we begin by adding a few details to the message we already have. The amount of bits we add is determined so that the message's length is precisely 64 bits less than a multiple of 512 after these bits are added. This can be expressed mathematically in the following way:
n x 512 = M + P + 64
M is the original message's length.
P stands for padded bits.
2. Append length bits
Now that we've added our padding bits to the original message, we can go ahead and add our length bits, which are equal to 64 bits, to make the whole message an exact multiple of 512.
We know we need to add 64 extra bits, so we'll compute them by multiplying the modulo of the original message (the one without the padding) by 232. We add those lengths to the padded bits in the message and get the complete message block, which must be a multiple of 512.
3. Initialize the buffers
We now have our message block, on which we will begin our calculations in order to determine the final hash. Before we get started, I want to point out that we'll need certain default settings to get started with the steps we'll be taking.
a = 0x6a09e667b = 0xbb67ae85c = 0x3c6ef372d = 0xa54ff53ae = 0x510e527ff = 0x9b05688cg = 0x1f83d9abh = 0x5be0cd19
Keep these principles in the back of your mind for now; all will fit together in the following phase. There are a further 64 variables to remember, which will operate as keys and are symbolized by the letter 'k.'
Let's go on to the portion where we calculate the hash using these data.
4. Compression Function
As a result, here is where the majority of the hashing algorithm is found. The whole message block, which is 'n x 512' bits long, is broken into 'n' chunks of 512 bits, each of which is then put through 64 rounds of operations, with the result being provided as input for the next round of operations.
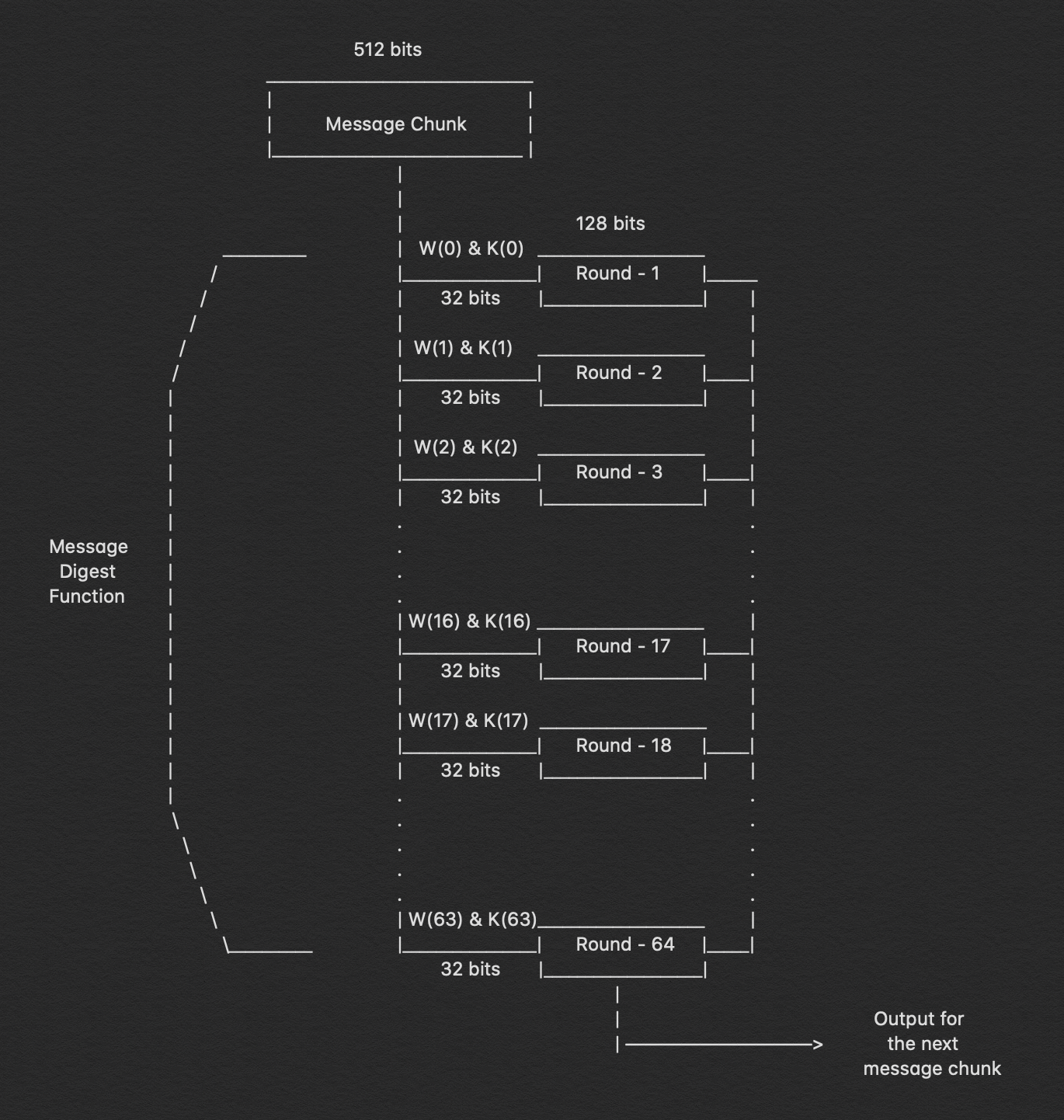
The 64 rounds of operation conducted on a 512-bit message are plainly visible in the figure above. We can see that we send in two inputs: W(i) and K(i). During the first 16 rounds, we further break down the 512-bit message into 16 pieces, each consisting of 32 bits. Indeed, we must compute the value for W(i) at each step.
W(i) = Wⁱ⁻¹⁶ + σ⁰ + Wⁱ⁻⁷ + σ¹where,σ⁰ = (Wⁱ⁻¹⁵ ROTR⁷(x)) XOR (Wⁱ⁻¹⁵ ROTR¹⁸(x)) XOR (Wⁱ⁻¹⁵ SHR³(x))σ¹ = (Wⁱ⁻² ROTR¹⁷(x)) XOR (Wⁱ⁻² ROTR¹⁹(x)) XOR (Wⁱ⁻² SHR¹⁰(x))ROTRⁿ(x) = Circular right rotation of 'x' by 'n' bitsSHRⁿ(x) = Circular right shift of 'x' by 'n' bits
5. Output
Every round's output is used as an input for the next round, and so on until just the final bits of the message are left, at which point the result of the last round for the nth portion of the message block will give us the result, i.e. the hash for the whole message. The output has a length of 256 bits.
Conclusion
In a nutshell, the whole principle behind SHA would sound something like this:
We determine the length of the message to be hashed, then add a few bits to it, beginning with '1' and continuing with '0' and then ‘1’ again until the message length is precisely 64 bits less than a multiple of 512. By multiplying the modulo of the original message by 232, we may add the remaining 64 bits. The complete message block may be represented as 'n x 512' bits after the remaining bits are added. Now, we split each of these 512 bits into 16 pieces, each of 32 bits, using the compression function, which consists of 64 rounds of operations. For the first 16 rounds, these 16 sections, each of 32 bits, operate as input, and for the next 48 rounds, we have a technique to compute the W(i). We also include preset buffer settings and 'k' values for each of the 64 rounds. We can now begin computing hashes since we have all of the necessary numbers and formulae. The hashing procedure is then repeated 64 times, with the result of the i round serving as the input for the i+1 round. As a result, the output of the 64th operation of the nth round will be the output, which is the hash of the whole message.
The SHA-256 hashing algorithm is now one of the most extensively used hashing algorithms since it has yet to be cracked and the hashes are generated rapidly when compared to other safe hashes such as the SHA-512. It is well-established, but the industry is working to gradually transition to SHA-512, which is more secure, since experts believe SHA-256 may become susceptible to hacking in the near future.
