Self-signed certificates are widely used in testing environments and they are excellent alternatives to purchasing and renewing yearly certifications.
That is of course if you know how and, more importantly, when to use them. Remember, that A self-signed certificate is not signed by a publicly trusted Certificate Authority (CA). Self-signed certificates are considered different from traditional CA certificates that are signed and issued by a CA because self-signed certificates are created, issued, and signed by the company or developer who is responsible for the website or software associated with the certificate.
You are probably reading this article because for some reason, you need to create a self-signed certificate with Windows. So, we’ve tried to outline the easiest ways to do that. This article is up-to-date as of December 2021. By the way, we’re referring to Windows 10 for all the following tutorials. As far as we know, the processes for Windows 11 are identical.
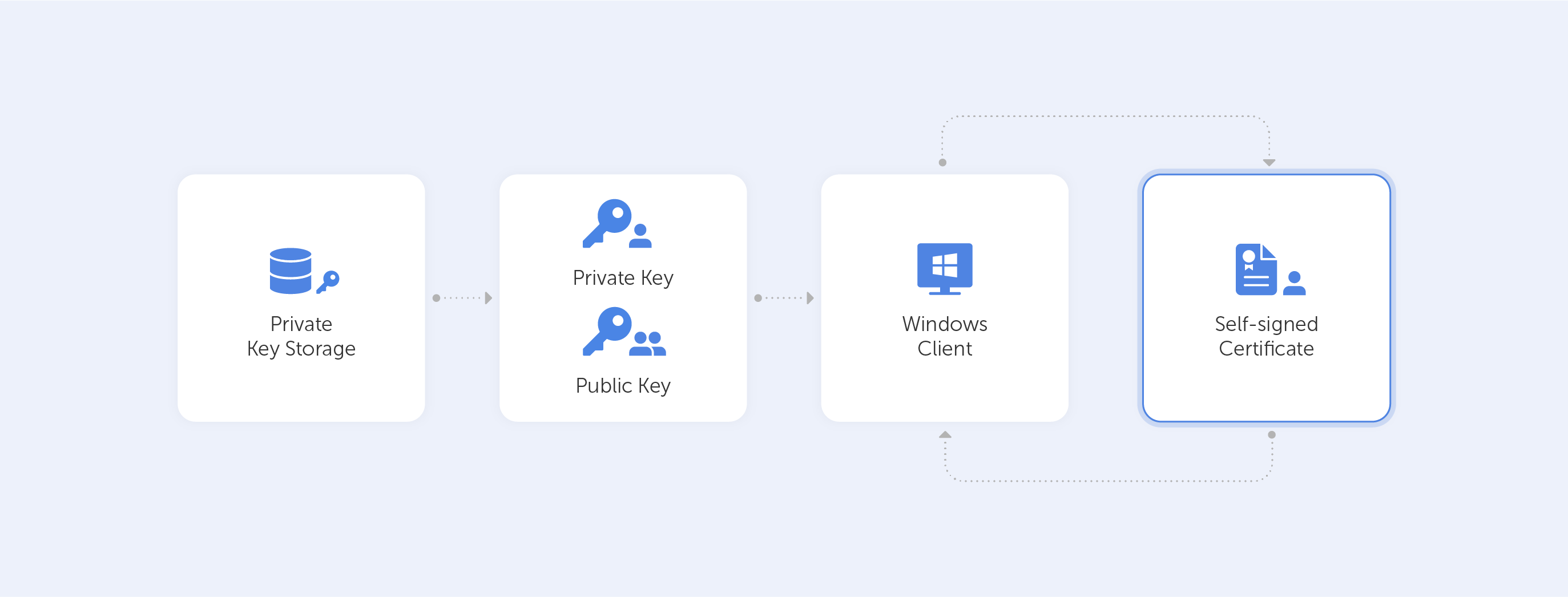
So what are our options?
Using Let’s Encrypt.
These guys offer free CA certificates with various SAN and wildcard support. The certificate is only good for 90 days, but they do give an automated renewal method. This is a great alternative for a quick proof-of-concept. Other options would require more typing, for sure.
But this option works only if you want to generate a certificate for your website. The best way to start is by going to Getting Started, the instructions thereafter are very easy to follow.
Other one-click option:
We’ve reviewed different online services that allow you to easily generate self-signed certificates. We’ve sorted them from one-click to advanced, and the first one is:
Just enter your domain name — and you are ready to go:
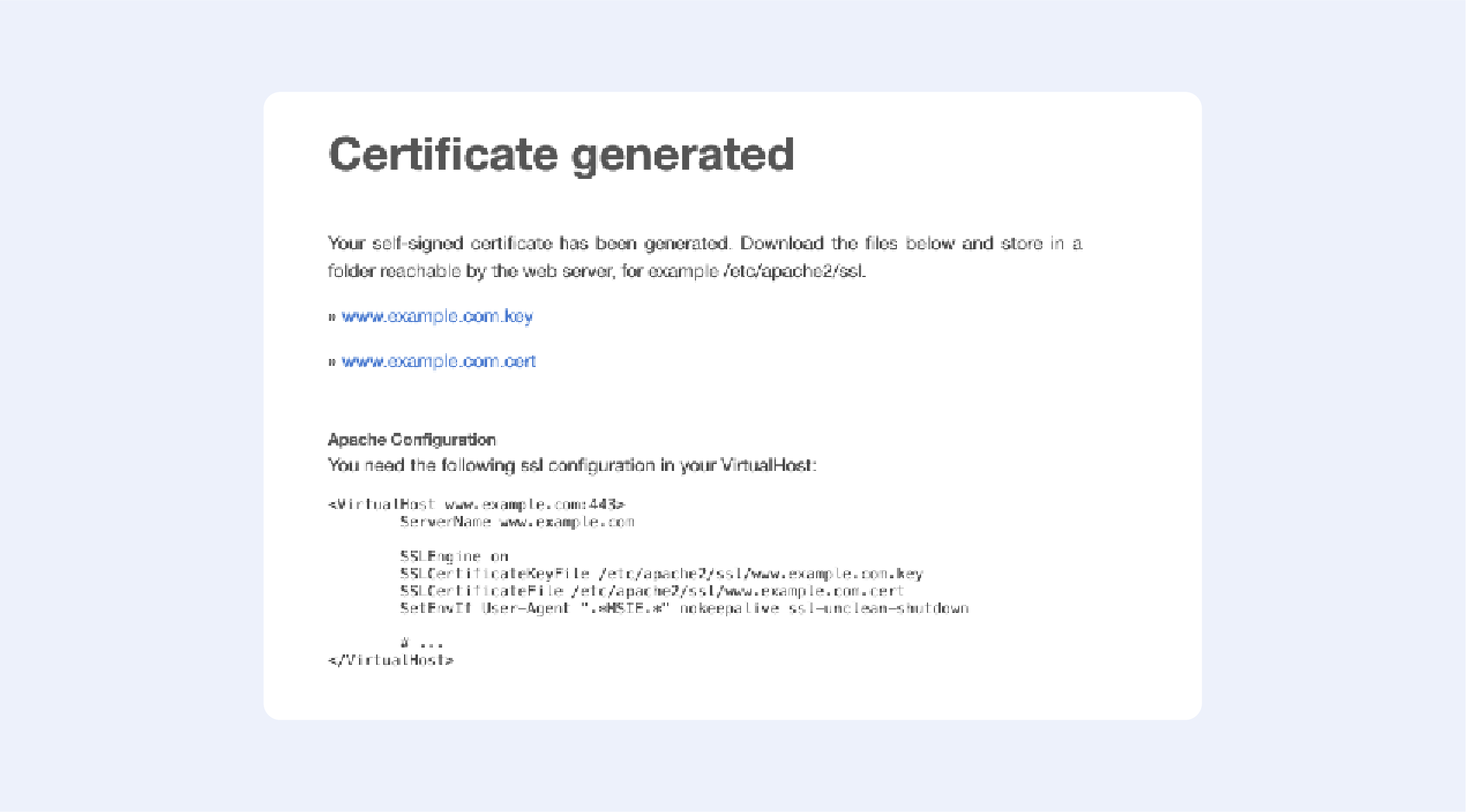
Fill out the following fields:
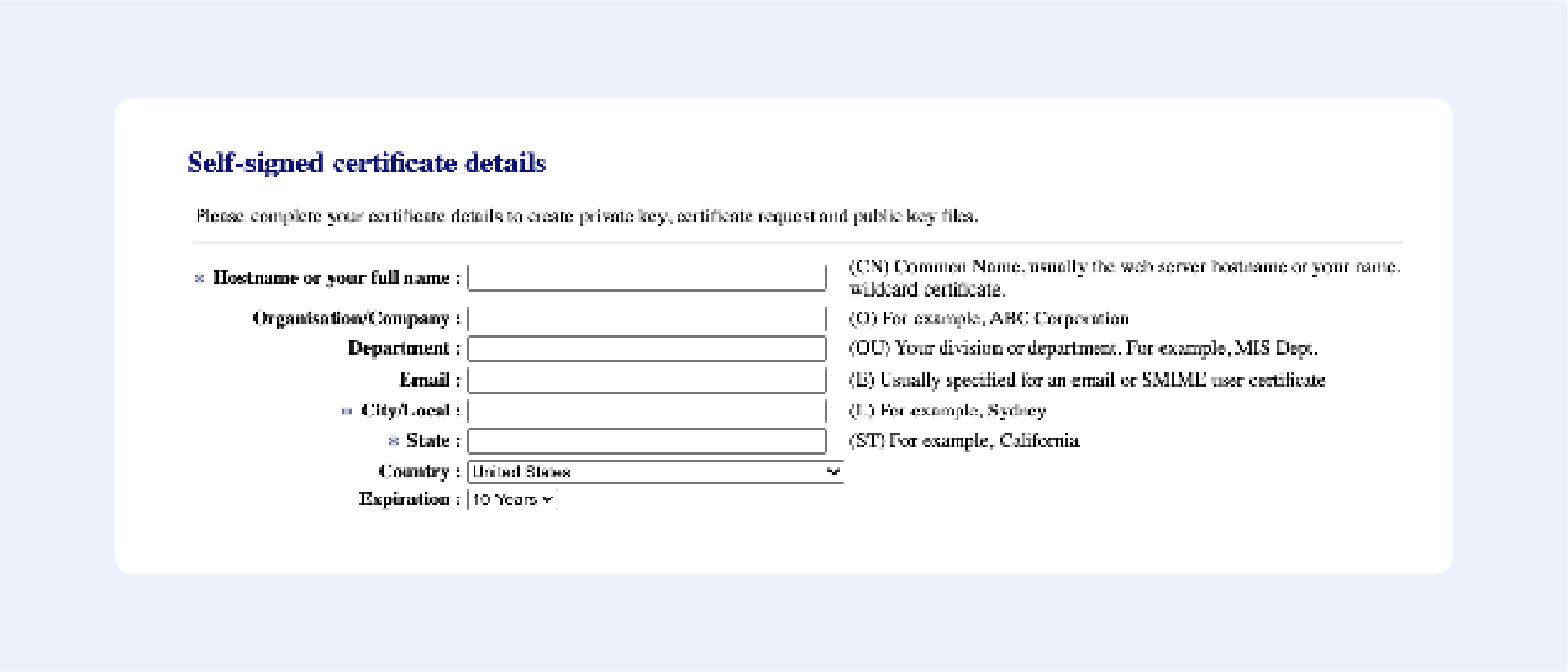
Press “Next”, then confirm your details, and get your certificate:
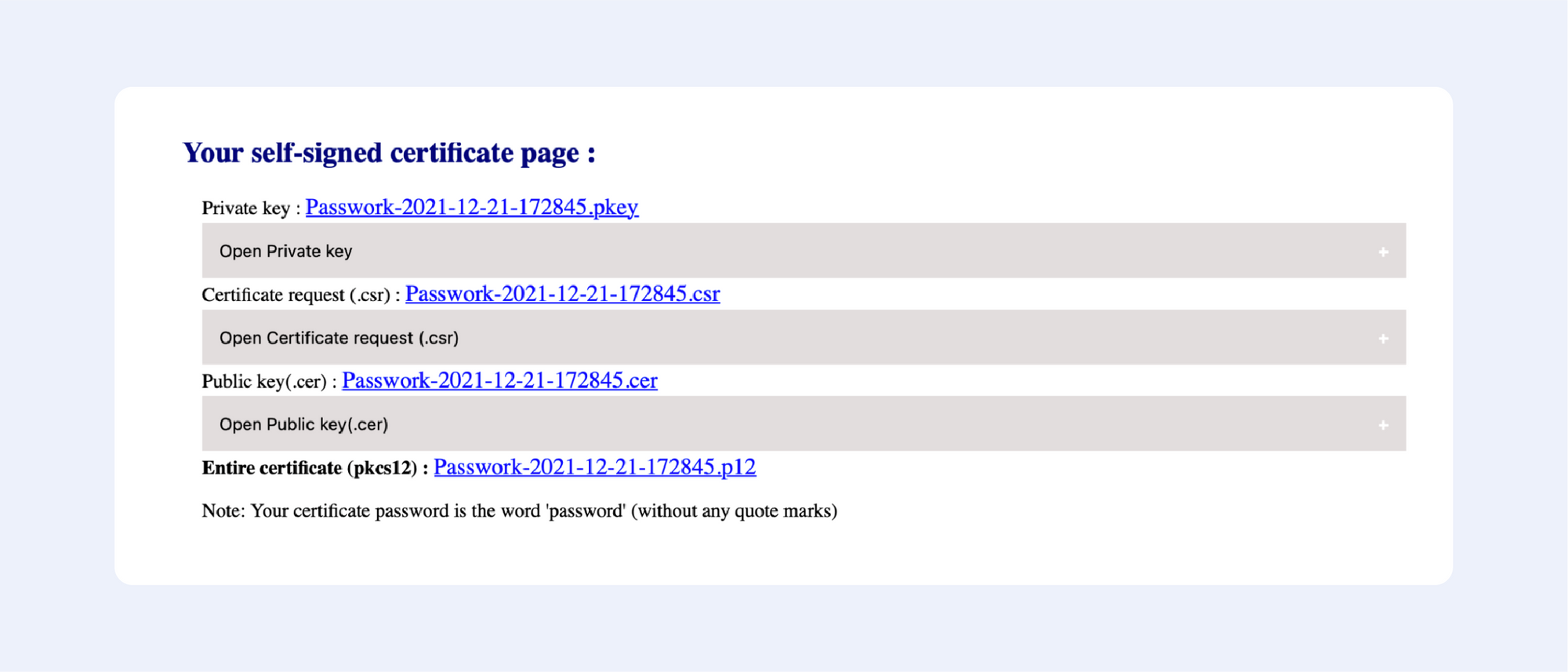
It’s that easy!
Among the online services that allow you to generate self-signed certificates, this one is the most advanced; just look at all available options to choose from:
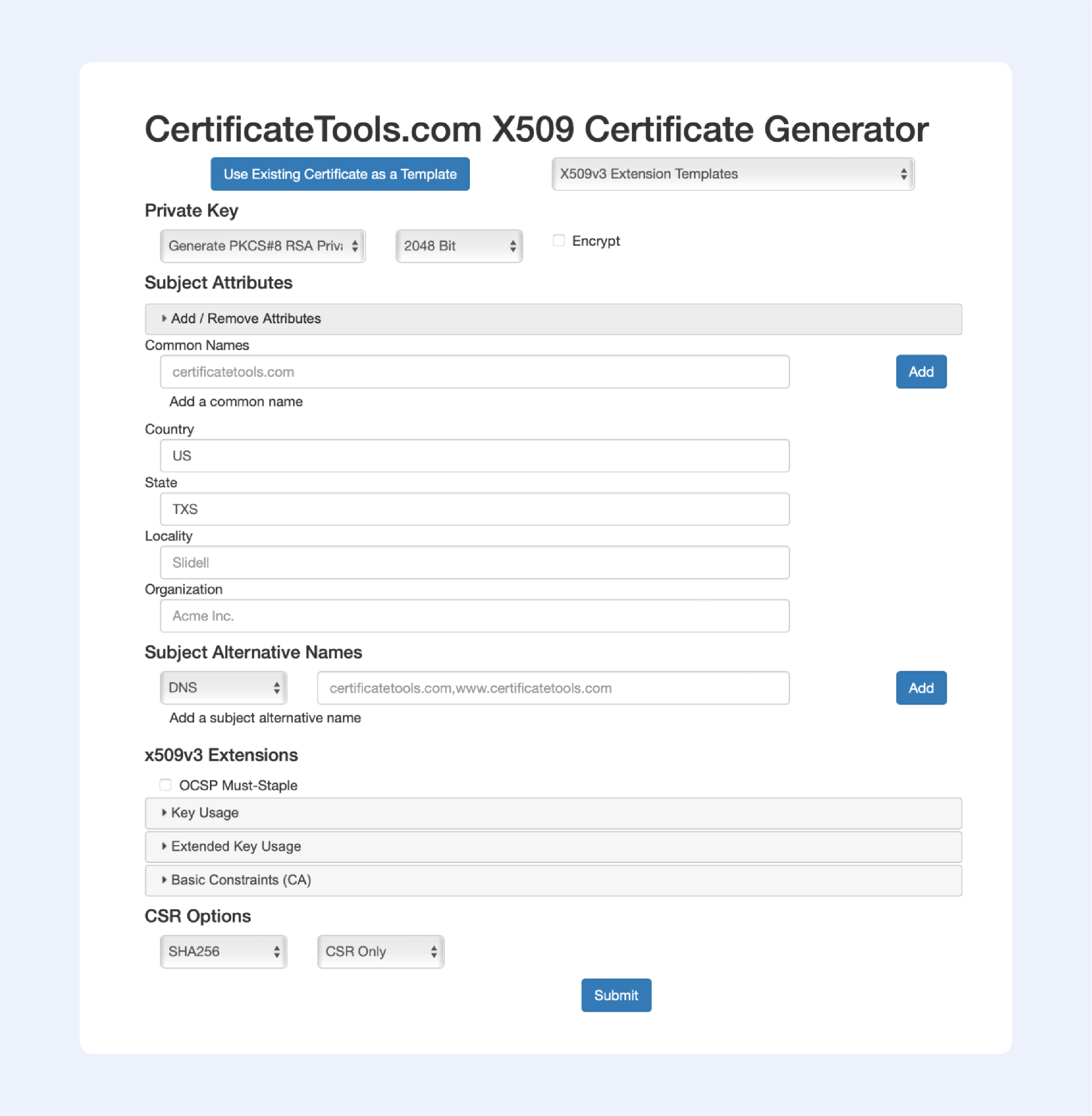
Now let’s continue with offline solutions, that are a bit more advanced:
PowerShell 4.0
1. Press the Windows key, type Powershell. Right-click on PowerShell and select Run as Administrator.
2. Run the New-SelfsignedCertificate command, as shown below.
$cert = New-SelfSignedCertificate -certstorelocation
cert:localmachinemy -dnsname passwork.com3. This will add the certificate to the locater store on your PC. Replace passwork.com with your domain name in the above command.
4. Next, create a password for your export file:
$pwd = ConvertTo-SecureString -String ‘password!’ -Force -AsPlainText5. Replace password with your own password.
6. Enter the following command to export the self-signed certificate:
$path = 'cert:localMachinemy' + $cert.thumbprint
Export-PfxCertificate -cert $path -FilePath
c:tempcert.pfx -Password $pwd7. In the above command, replace c:temp with the directory where you want to export the file.
8. Import the exported file and deploy it for your project.
Use OpenSSL
1. Download the latest OpenSSL windows installer from a third-party source;
2. Run the installer. OpenSSL requires Microsoft Visual C++ to run. The installer will prompt you to install Visual C++ if it is already not installed;
3. Click Yes to install;
4. Run the OpenSSL installer again and select the installation directory;
5. Click Next;
6. Open Command Prompt and type OpenSSL to get an OpenSSL prompt.
The next step would be to generate a public/private key file pair.
1. Open Command Prompt and create a new directory on your C drive:
C: >cd Test2. Now go to the new directory:
C: Test>3. Now you need to type the path of the OpenSSL install directory followed by the RSA key algorithm:
C: Test>c:opensslbinopenssl genrsa -out privkey.pem 40964. Run the following command to split the generated file into separate private and public key files:
C: Test>c:opensslbinopenssl ssh-keygen -t rsa -b 4096 -f privkey.pemOnce you have the public/private key generated, follow the next set of steps to create a self-signed certificate file on Windows.
1. Go to the directory that you created earlier for the public/private key file:
C: Test>2. Enter the path of the OpenSSL install directory, followed by the self-signed certificate algorithm:
C: Test>c:opensslbinopenssl req -new -x509 -key privkey.pem -out cacert.pem -days 1093. Follow the on-screen instructions;
4. You need to enter information about your organization, region, and contact details to create a self-signed certificate.
We also have a detailed article on OpenSSL – it contains more in-depth instructions on generating self-signed certificates.
Using IIS
This is one of those hidden features that very few people know about.
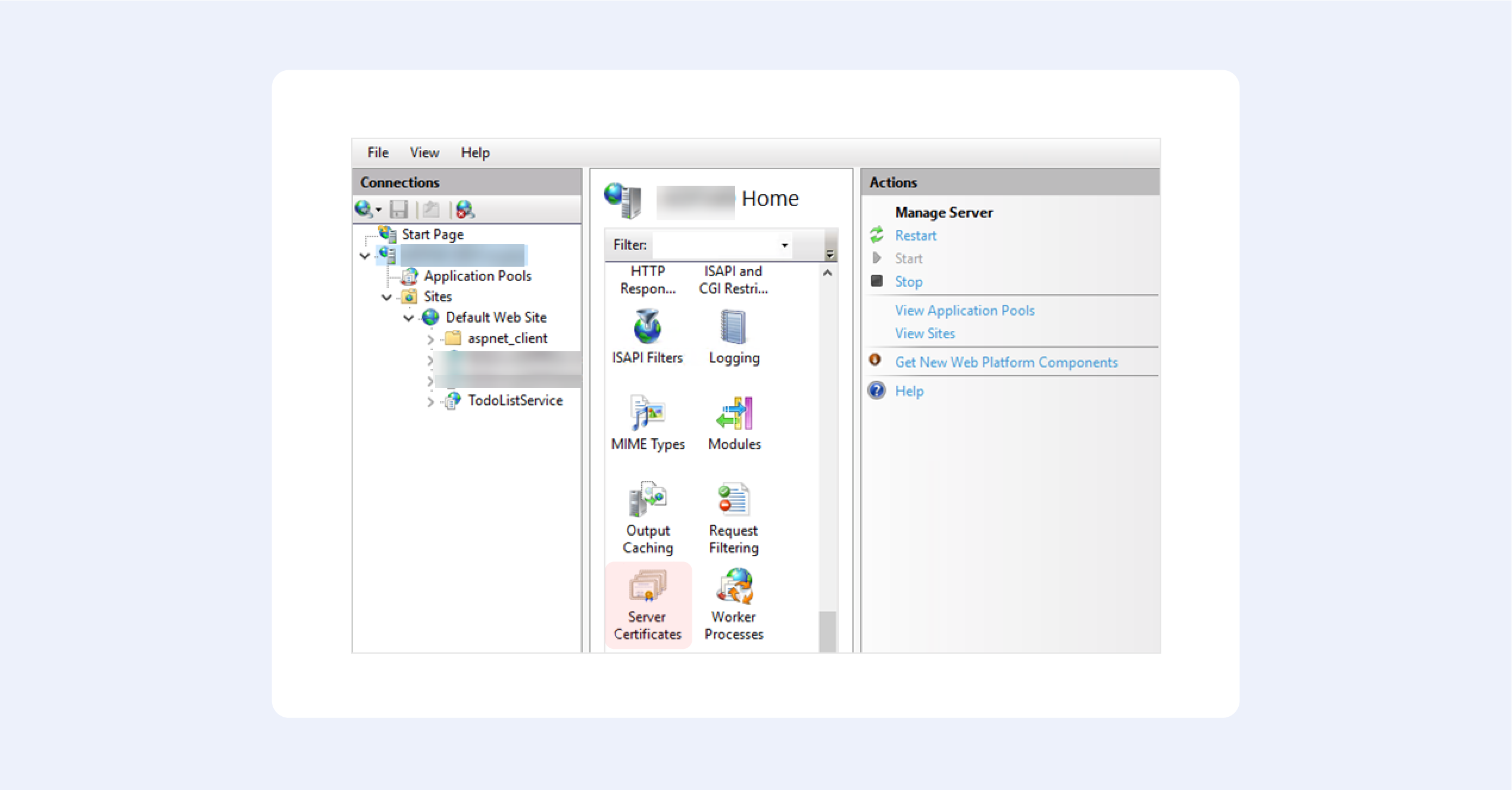
1. From the top-level in IIS Manager, select “Server Certificates”;
2. Then click the “Create” button on the right;
3. This will create a self-signed certificate, valid for a year with a private key. It will only work for “localhost”.
We hope this fruit bowl of options provides you with some choice in the matter. Creating your own self-signed certificate nowadays is trivial, but only until you begin to understand how they really work.
Our option of choice is, of course, OpenSSL — after all, it is an industry-standard.
7 ways to create self-signed certificates on Windows
Are you having trouble remembering your passwords or accessing your account? Perhaps you’re stressing out that you may have been hacked? Well, in any case, restoring your Facebook account utilising reliable Facebook account recovery solutions shall be covered by this article, so buckle up!
In order to regain access to your Facebook account, you can use one of several automated methods. Many are based on the information you provided when you set up your account, which isn’t helpful if you can’t remember the most important piece of information you provided when you set up the account — your password. Also, some information will be out of date, like your recovery phone number or your active email address.
And even if all methods listed below fail, we’ve got an alternative for you right at the very bottom of the article.
Firstly, make sure that you aren't still logged into Facebook somewhere else!
Android and iOS Facebook apps, as well as mobile browsers may all be used to access the site, so you might be logged in on them.
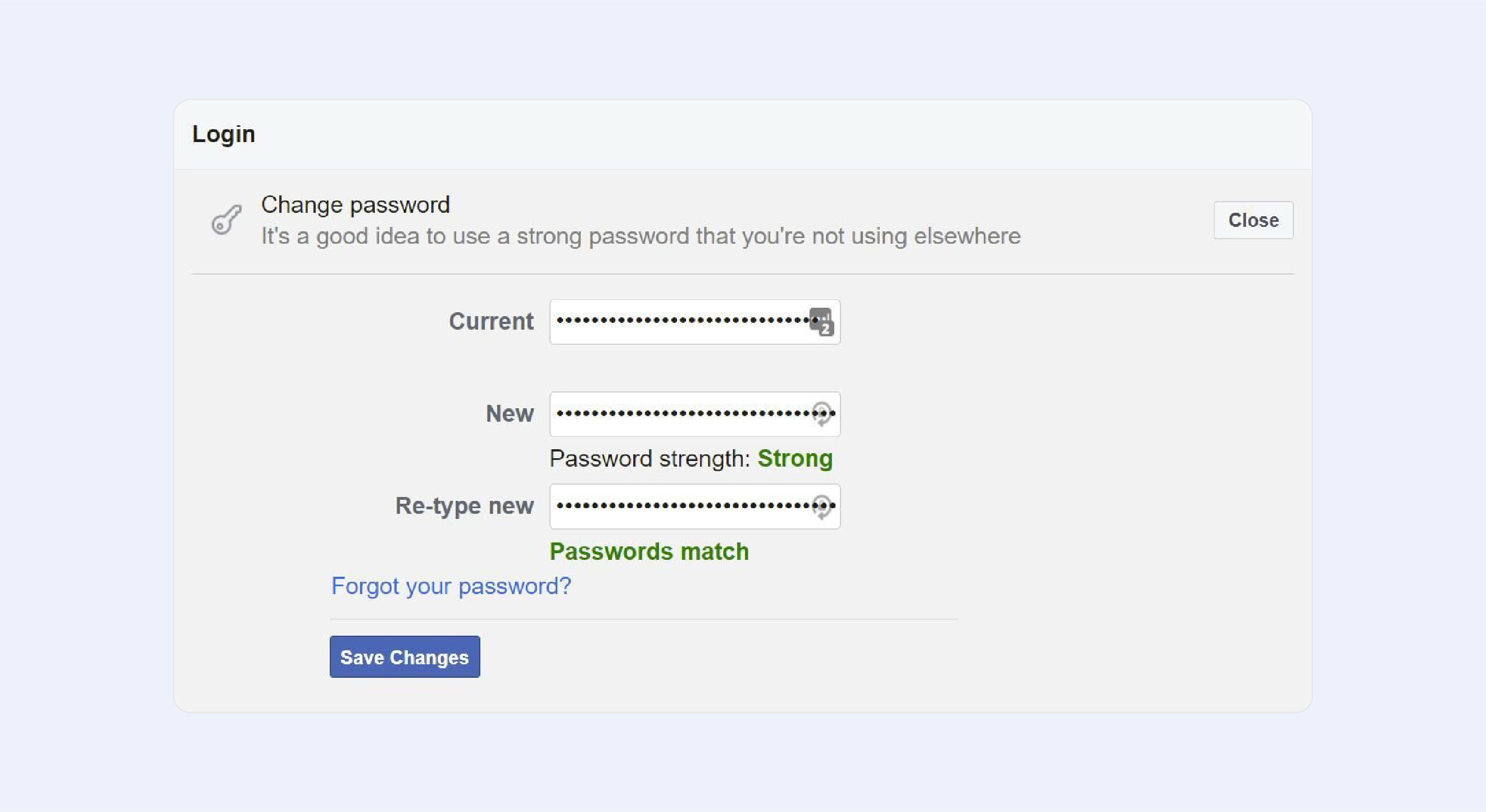
If you are logged in, you can ‘recover’ your account by simply changing the password, and it can be done without a confirmation reset code!
But if you are not logged into Facebook on other devices or browsers — try Facebook's Default Account Recovery Methods.
If at all feasible, log into your Facebook account using the same internet connection and computer or phone that you've used on a regular basis in the past. If Facebook detects your network and device, you may be able to reset your password without having to provide any extra information to Facebook. But first and foremost, you must authenticate your account.
Find and recover your account by providing contact information
The best option is to directly go to the Facebook Recovery Page.
To sign in, enter an email address or phone number that you previously associated with your Facebook profile. When looking for a phone number, test it both with and without your country code, for example, 1, +1, or 001 for the United States; all three variants should work just fine. Even if it doesn't explicitly say so, you may use your Facebook credentials to log in — instead of your mobile number or email.
Your profile will be summarised once you have successfully identified your account, as seen in the screenshot below. Please double-check that this is indeed your account and that you still have access to the email address or phone number mentioned before proceeding. The option of choosing between email or phone recovery may still be available to you.
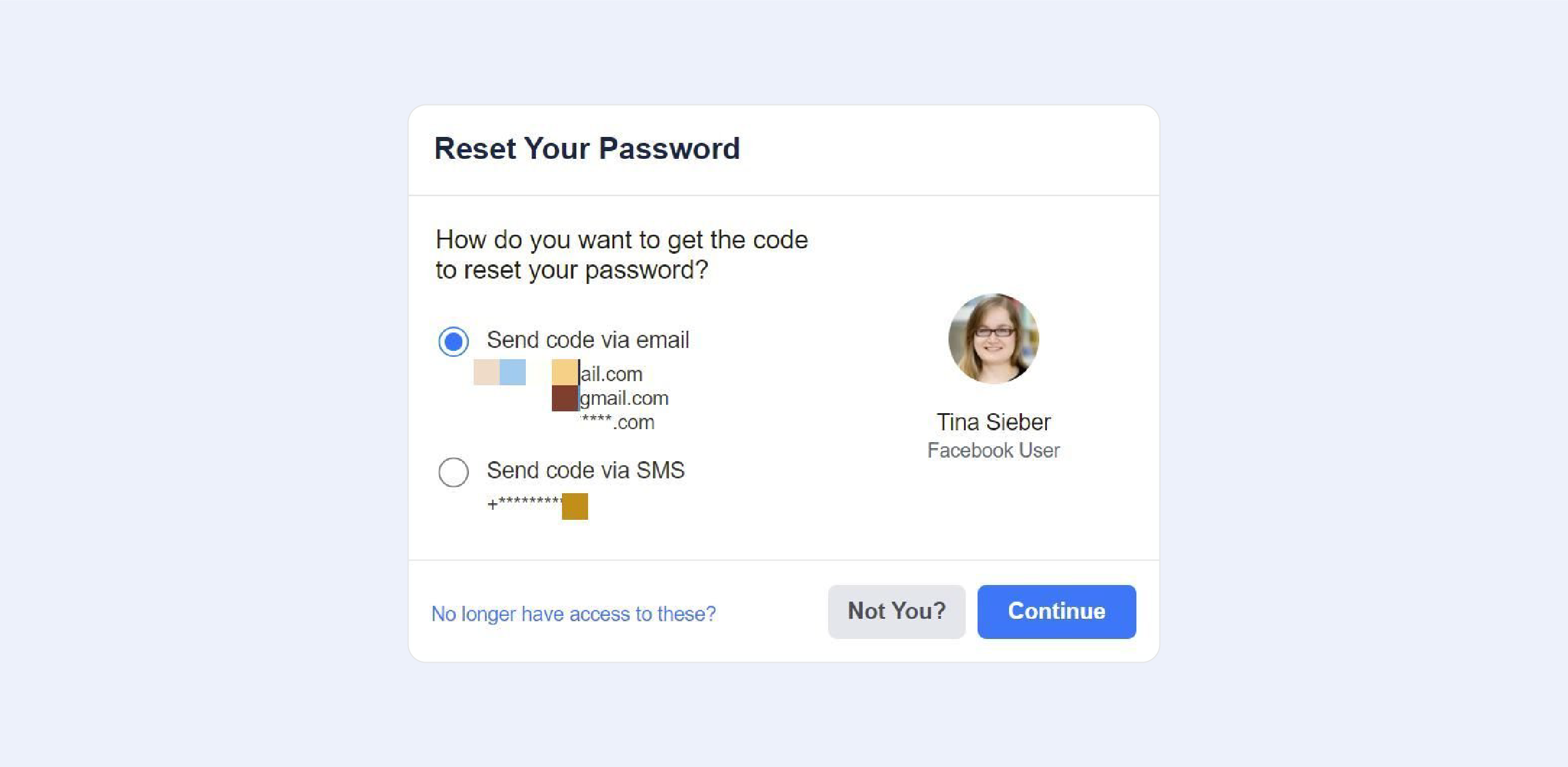
If everything appears to be in order with the contact information that Facebook has on file for you, though, click Continue. A security code will be sent to you by Facebook.
Retrieve the code from your email or phone (depending on whatever method you used), input it, and rejoice in the knowledge that you have regained access to your Facebook profile.
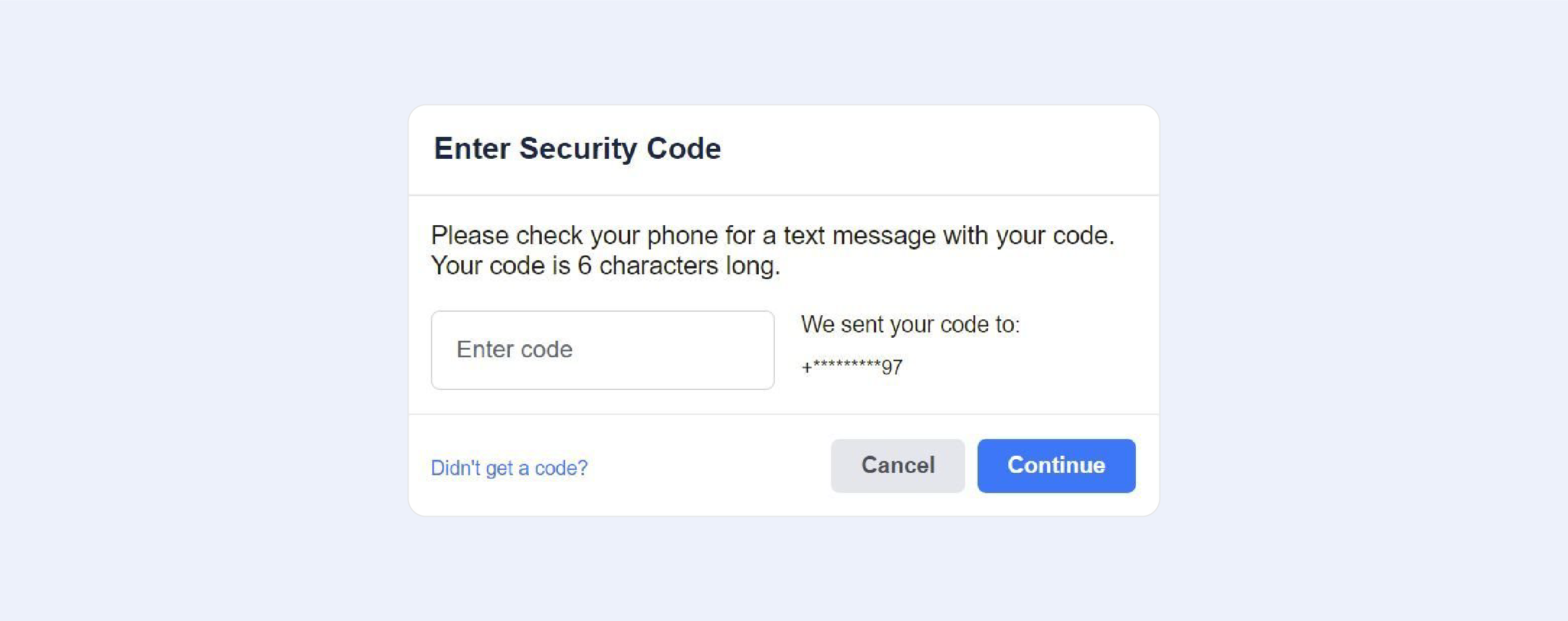
At this point, you have the option of creating a new password, which we highly advise you to do.
If you don't receive the code via email, check your spam folder, or make sure you can receive text messages from unknown senders if the code doesn't arrive to your mobile.
If you are still unable to receive the code, choose Didn't get a code? from the drop-down menu. You can return to the previous screen by clicking the X in the bottom-left corner of the Enter Security Code box.
Maybe you'll get lucky and discover that you don't, in fact, have access to the account at all!
Log back into your Facebook account
You should immediately reset your password and update your contact information if you have regained access to your Facebook account after a suspected hijacking.
To keep your Facebook account safe, follow two simple rules. Don't forget to get rid of any email addresses or phone numbers that you no longer have access to. Also, enable two-factor authentication on all of your social media accounts in order to prevent a loss of access in the future.
Don’t forget, the Facebook Help Community is a great place to find answers to your issues.
If all else fails, creating a new Facebook profile might not be as bad as you think
Over the past few years, we've received a large number of letters from users who were unable to regain access to their Facebook accounts, despite following each and every one of the instructions listed above.
Typically, their contact information was out of date, the recovery codes offered by Facebook were ineffective, or the corporation never responded to their request for identification verification. And at that point, you’re pretty much out of options.
You have to accept the fact that you must move on. Even though it's painful, you must learn from your mistakes and register a new user account.
Always include legitimate contact details, don’t forget to up the security on your Facebook account, and completely re-create your profile from the ground up. Despite the inconvenience, it’s a better option than doing nothing. Not to mention, you won’t have any of those embarrassing old photos, and you can only add people as friends that really matter to you now.
How to recover your Facebook account

In Passwork 6.2 we have introduced a range of features aimed at enhancing your security and convenience:
- Bin
- Protection against accidental removal of vault
- Protection against 2FA brute force
- Accelerated synchronization with LDAP
- Improved API settings
- Bug fixes in role management
Bin
Now, when deleting folders and passwords, they will be moved to the Bin. If needed, they can be restored while preserving previously set access permissions. Vaults are deleted without being moved to the Bin — they can only be restored from a backup.
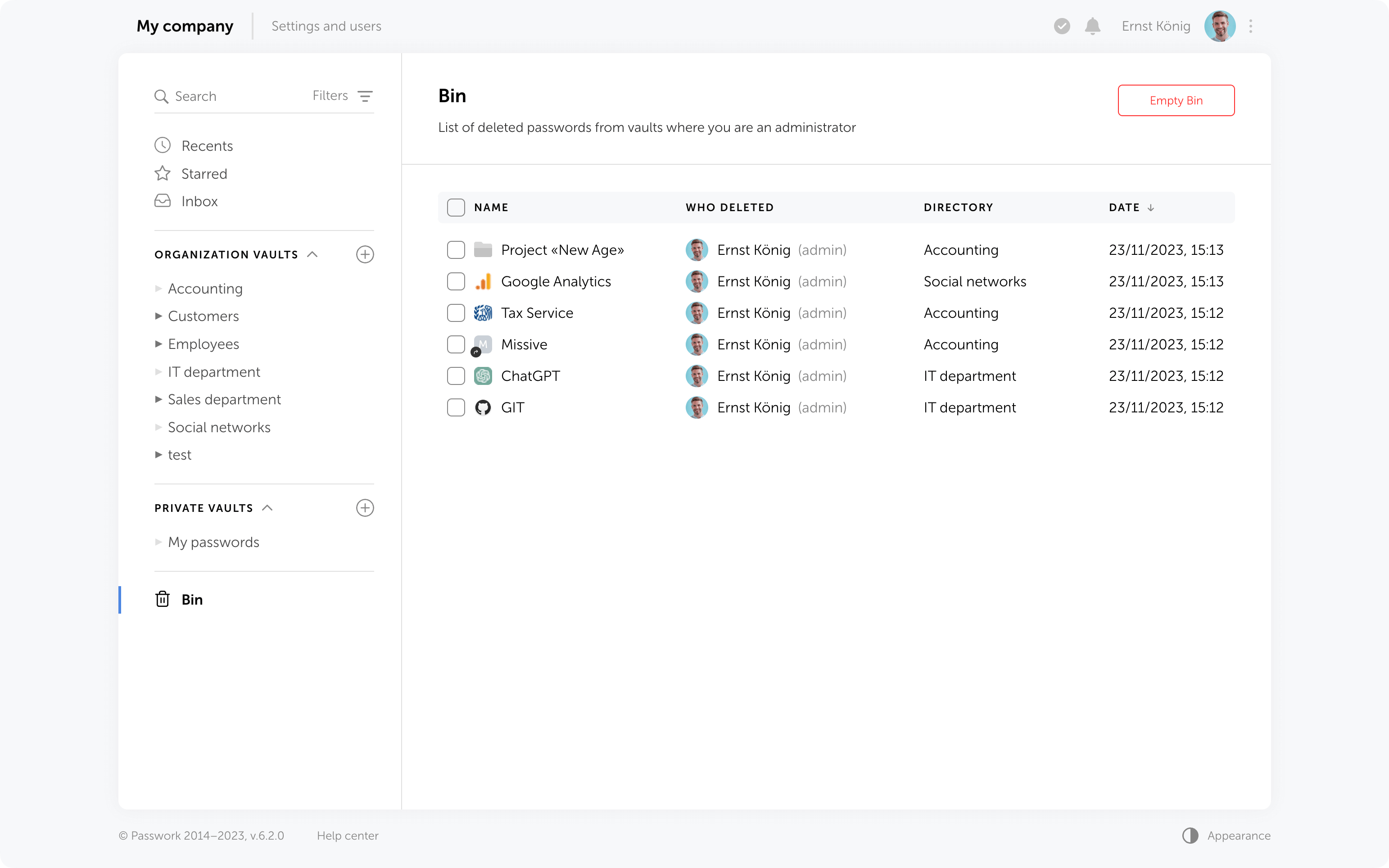
Who can view deleted passwords and folders in the Bin?
Inside the bin users can see the deleted items from those vaults in which they are administrators. For instance, an employee who is not an administrator of organization vaults will only see the deleted passwords and folders from his personal vaults when opening the Bin.
In addition to object names, the Bin also displays the usernames of people who deleted data. You can also see the initial directory name and the deletion date.
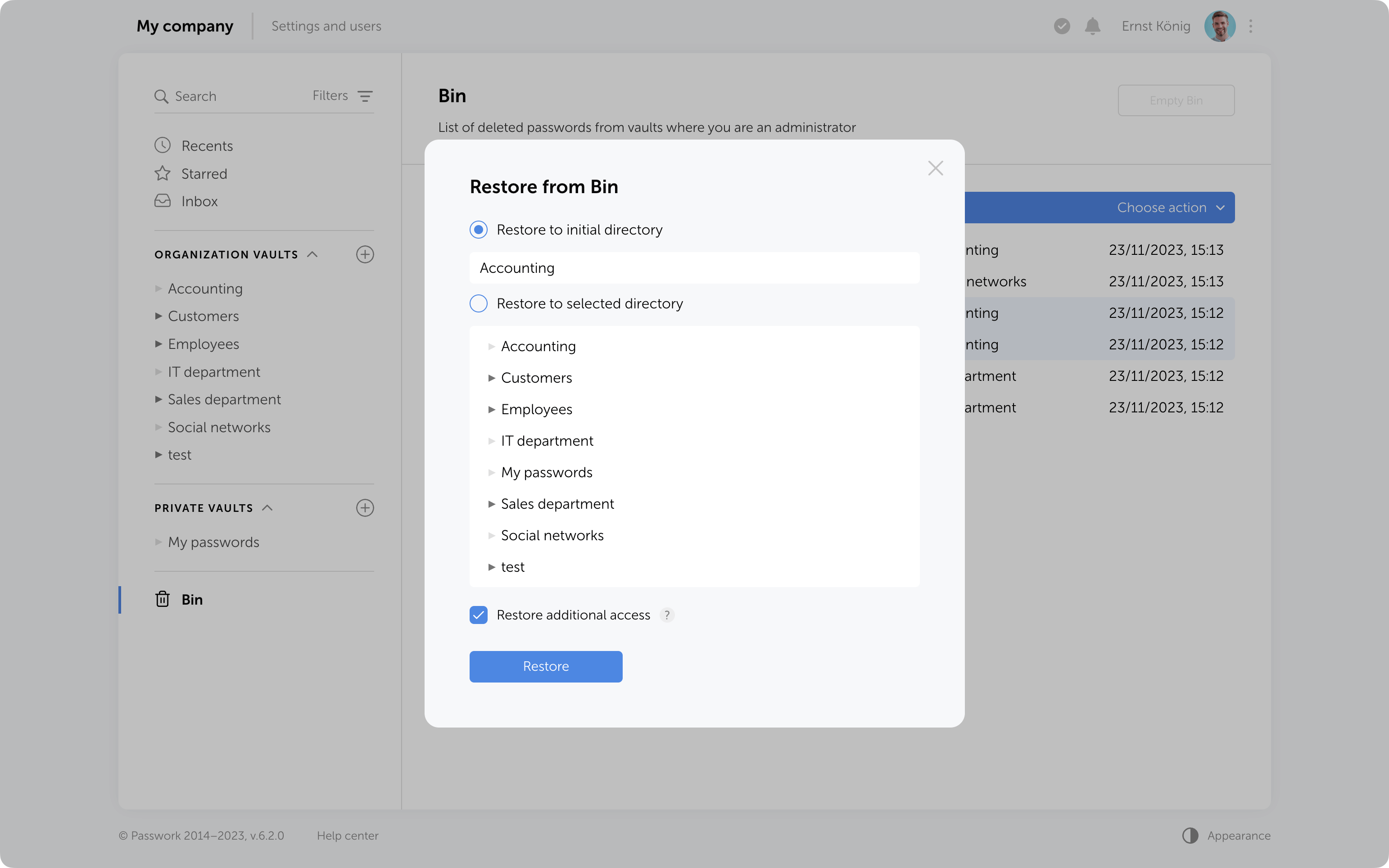
Object restoration
Objects from the Bin can be restored to their initial directory if it has not been deleted or moved. Alternatively, you can choose any other directory where you have edit and higher access levels.
When restoring deleted folders to their initial directories, user and role access levels will also be restored exactly as they were previously manually set in these folders. Other access permissions will be set based on the current permissions in the initial directory.
When restoring folders to a directory different from the initial, access levels will always depend on the current permissions in the selected directory.
Additional access to deleted passwords
If passwords have been shared with users, moving them to the Bin will remove them from the “Inbox” section, and any shortcuts or links to these passwords will become nonfunctional.
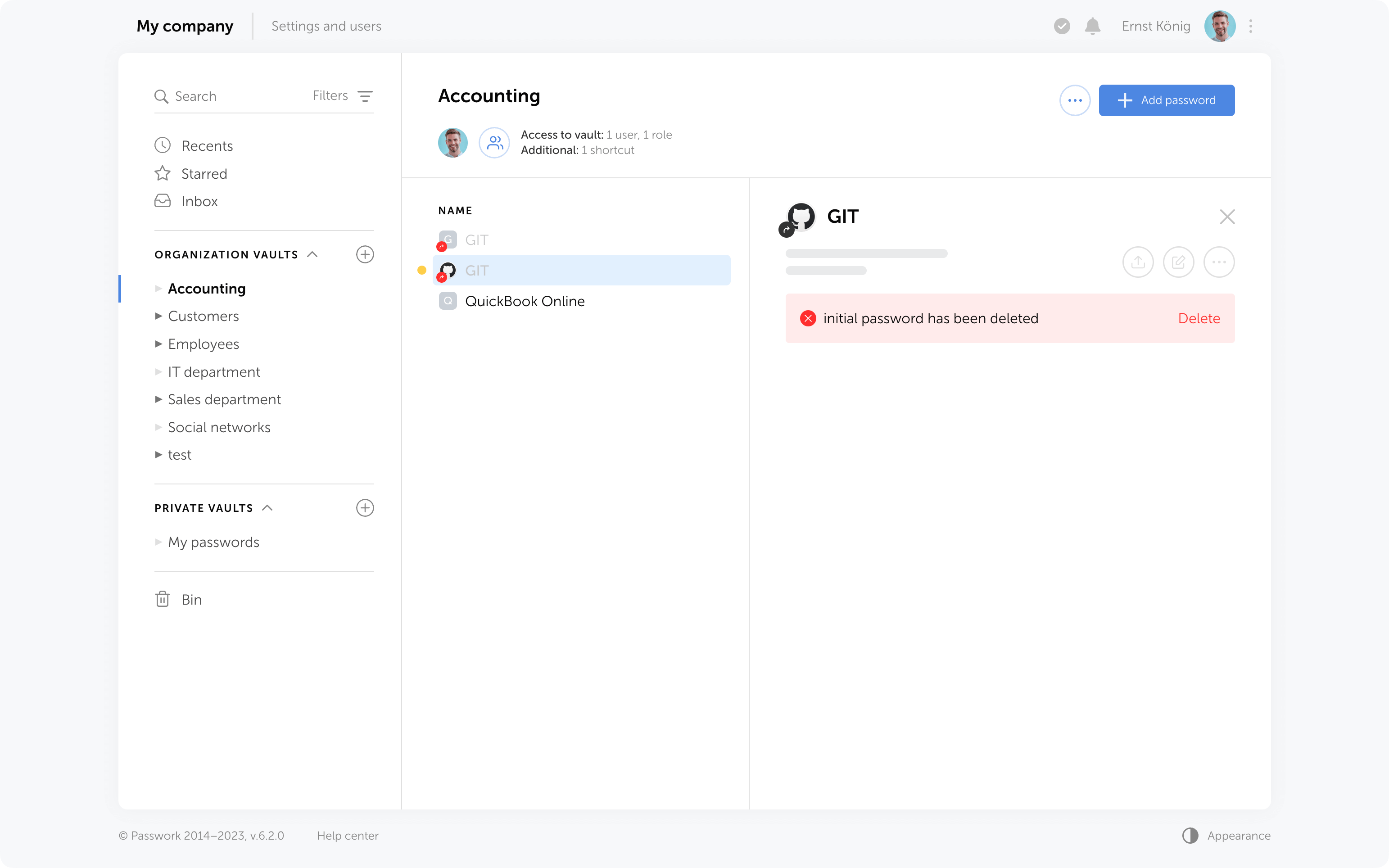
Restoring additional access
When restoring from the Bin, it is possible to regain additional access levels to passwords. Passwords that were shared with users will reappear in their “Inbox” section, access to passwords through shortcuts will be restored, and links that have not expired will become functional again.
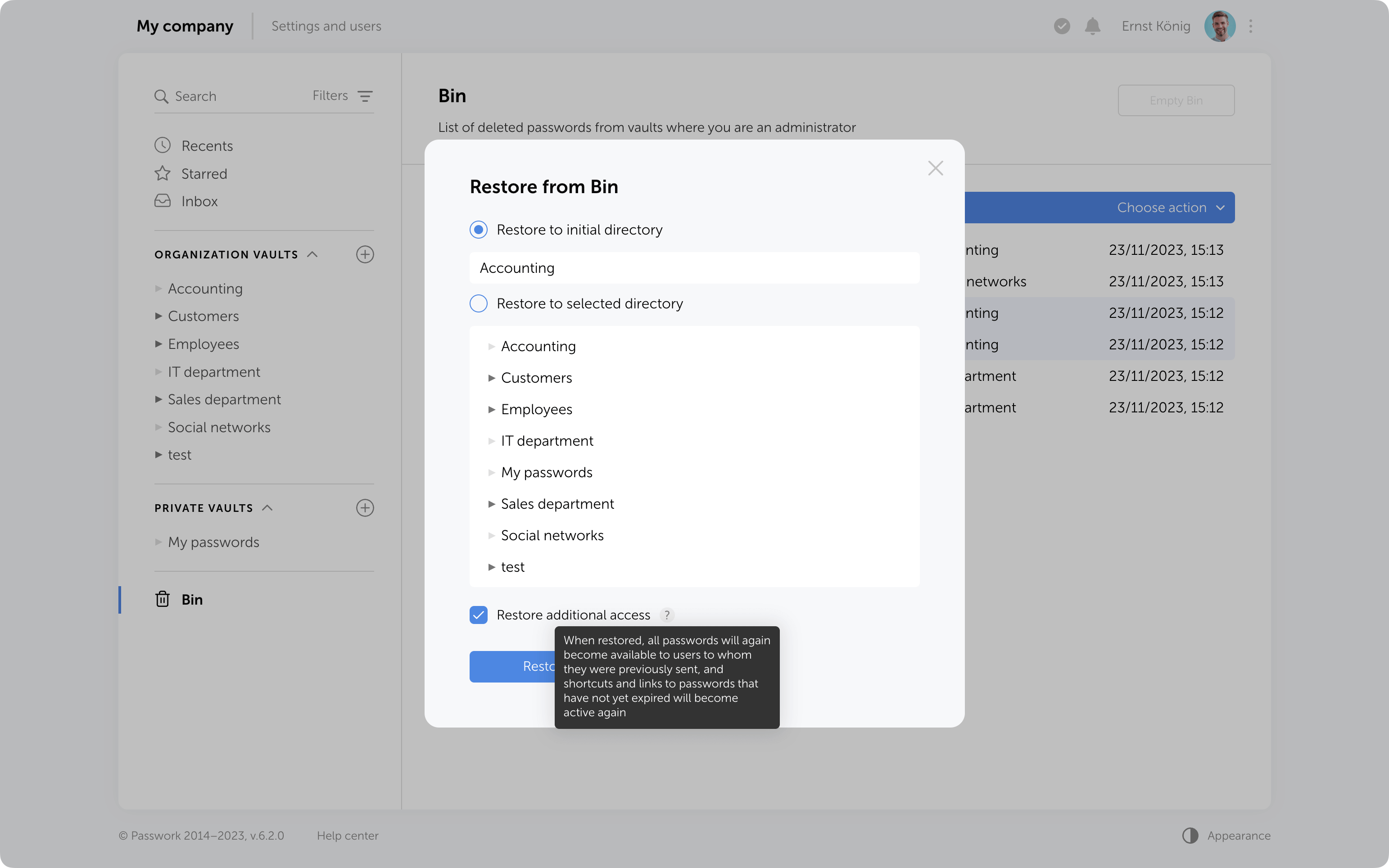
Bin cleanup
You can delete selected items from the Bin or use the "Empty Bin" button to remove all items contained inside.
It's important to note that in the Bin you only see the items which were deleted from the vaults where you are an administrator. Objects from other vaults are not visible, and clearing the Bin will not affect them.
In future, the option to configure automatic Bin cleanup will be added.
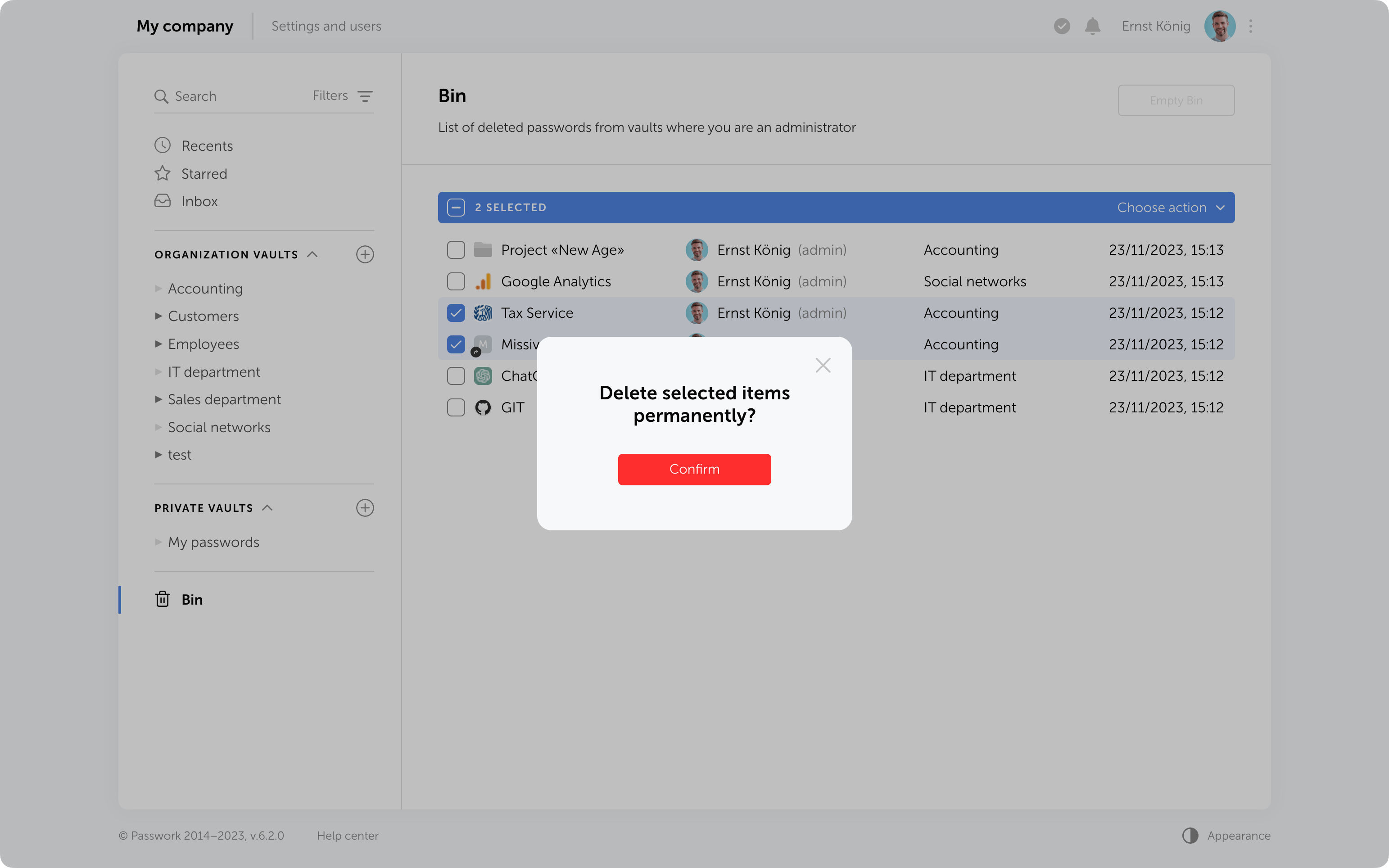
Protection against accidental removal of vault
To confirm the deletion of a vault, you now need to enter its name. It will be permanently deleted along with all the data inside. Additionally, if there are passwords or folders from this vault in the Bin, they will also be removed.
Protection against 2FA brute force
Protection against 2FA brute-force attacks has been added. After several incorrect attempts to enter the 2FA code, the user will be temporarily locked. The number of attempts, input intervals, and the lockout time are set in the config.ini file.
Other changes
- LDAP synchronization has been accelerated
- Descriptions of parameters and minimum allowable values for API token expiration time and API refresh token expiration time have been added to the API settings section
- Automatic assignment of "Navigation" to parent folders in role management has been fixed
- The issue when a vault administrator could not add roles to a vault and manage its permissions has been fixed
- The issue with showing additional access rights to passwords when moved to another vault has been fixed
Upgrade Instructions — How to update Passwork
More information about features and prices — on the Passwork website
Introducing Passwork 6.2

Over the past decade, data has transitioned from mere information to a precious asset. Numerous enterprises thrive on data, while others crumble with its loss. Customer personal information, analytics, financial transaction records and more hold monetary value. Yes, there's an abundance of informational "clutter" around, but even amid hard-to-spot data, a skilled cybercriminal can discover a gold mine.
The acceleration of information technology is rapid, with fresh information emerging and being processed every moment. Often, companies simply lack the time to sift the "wheat" from the "chaff" and, as a result, release sensitive data, like customers' home addresses for delivery, into the open.
Most firms have mastered data collection, some have ventured into processing it, and a fewer number into analyzing it, but not all have grasped how to safeguard it. In this article, we’ll explore what qualifies as sensitive data, how to shield it, and the primary blunders made while handling sensitive data.
What sets apart ordinary data from sensitive data?
With the trend of data accumulation in the market, corporations have embraced it wholeheartedly. This opens up numerous avenues for growth, business broadening and optimization, and introducing new offerings to the market. For instance, by scrutinizing customer conduct, you can present them with the products they need at the opportune moment. Or, simply, knowing customers' birthdays, send a discount coupon as a present, encouraging a new purchase. The possibilities are myriad, and they stem from entirely diverse data types. That's why enterprises amass data even before understanding its use. It's for the just-in-case scenario.
Similarly, it's not always feasible to instantly determine the significance of data and the extent of protection required. Some opt for overcaution, storing data securely from the outset, while others leave it in public view, thus risking it. The sensitivity of data can be gauged by asking — what’s the fallout if it’s pilfered?
Two outcomes exist. Nothing occurs — the data isn't sensitive. The offender, directly or indirectly, could inflict harm on the business or customers. For instance, by pilfering personal data, like full names and phone numbers, and releasing them online, the company’s reputation takes a hit. Or, by stealing an individual’s data — their address, purchasing tendencies, and, say, date of birth, orchestrate a social engineering assault.
Sensitive data encompasses information that could potentially jeopardize its possessor. For regular folks, it’s mainly personal and financial data, medical details, relationship data, personal visuals, and data on preferences. For companies, it includes internal business records, customer and employee databases, confidential documents, market evaluations, and the like.
Recognizing sensitive data
The theft or exposure of sensitive data undermines a company's customer privacy, triggers financial setbacks, and could even threaten an organization’s security. Hence, distinguishing sensitive personal data from common data is crucial. This involves carrying out a data classification and risk assessment.
This could encompass evaluating potential damage in case of a data breach, as well as examining legal mandates for specific data types. Primarily, anything related to sensitive information and personal data should be guarded. However, the task of identifying data types doesn’t conclude here. For instance, trade secrets can be shielded under 21 orders or at your discretion, but personal data must be classified and shielded by law. Information security experts opine that to pinpoint sensitive company data, the IS division, along with representatives from various sectors — accounting, legal, HR, and marketing — should formulate guidelines to identify sensitive information. The primary focus here would be potential financial or reputational harm from information leakage. Yet, the potential threat indicator of a data breach may not always be objective. Numerous cyber incidents involving social engineering demonstrate that even seemingly harmless data about a person can be utilized to perpetrate a crime.
Key blunders in handling sensitive data
Both enterprises and users can be culpable for sensitive data leakage. On the corporate side, the usual culprit is a basic disregard for information security norms. For instance, unprotected corporate networks, operating on outdated operating systems, or absence of antivirus protection. On the user side — unawareness of cyber hygiene norms and a lack of understanding of what data might be sensitive. Common errors enabling sensitive data leakage:
• Inadequate password and account safeguards
• Lack of data categorization within the firm
• Improperly set up security systems
• Absence of data encryption
• Employees are untrained in cyber hygiene
Moreover, information is often undervalued by both corporations and individuals. For instance, a person may deem their passport information crucial but be indifferent about sharing their health information on social networks. Like any other domain of information security, elementary measures are paramount. For example, remembering updates, prompt training of staff in cyber hygiene, and employing protective software.
Conclusion
The subject of sensitive data is steadily gaining traction, as only in recent times have assailants learnt to actively exploit personal or corporate data to commit offenses. For larger and more technologically advanced companies, the issue is being addressed at a more sophisticated level, as they have not only learnt how to analyze and segment data but also how to defend it. However, there's another facet to consider - the company service users themselves. They may possess minimal awareness of the worth of their personal data and trigger leaks.
Sensitive information: Distinguishing the crucial from the commonplace

Prominent enterprises have endured substantial setbacks due to security breaches within their mobile applications, underscoring the criticality of app security that is often overshadowed by server-side concerns. Contrary to popular belief, mobile apps are not mere interfaces for server data; their vulnerabilities can inflict extensive damage, not limited to a single user but potentially devastating to the business at large. This article aims to elucidate this often-overlooked risk by showcasing notable instances where mobile app vulnerabilities have led to significant financial and reputational harm.
TikTok's multi-faceted security dilemmas
The year 2020 was marked by significant scrutiny directed at TikTok, a widely used social platform. The app was caught accessing clipboard data on Apple devices without user authorization, a clear invasion of privacy that could potentially lead to the exposure of sensitive personal and professional information. The same period saw the emergence of other security loopholes that provided attackers with the capability to compromise accounts, exfiltrate personal data, or circulate harmful content. The situation was further aggravated by concerns over TikTok's alleged ties to foreign government entities. The controversy was so severe that it led to the app's prohibition in several regions and culminated in a class-action lawsuit that cost the company $92 million in settlements. This series of events underscored the imperative for app developers to meticulously govern data collection practices to safeguard user privacy.
Strava's global heatmap incident
The fitness-oriented app Strava faced its own share of controversy in 2018 when it released a global heatmap of user fitness activities. What might have been a novel idea turned sour when it inadvertently compromised the safety of military personnel by revealing their movements and even the locations of military facilities. Although Strava claimed that the map was anonymous, resourceful individuals managed to de-anonymize the data, proving that even data represented as anonymous can be reconstructed to reveal identities. This incident sparked a global debate on the security ramifications of sharing fitness tracking data through apps and the potential threats it could pose to individuals and national security.
Starbucks' mobile app compromise
In 2015, Starbucks, the global coffeehouse chain, confronted a serious breach when its mobile app fell victim to an attack. Due to inadequate authentication processes, cybercriminals managed to hijack customer accounts. This security oversight led to unauthorized access to payment details and illegal transactions, leaving customers financially vulnerable and causing a major dent in Starbucks’ corporate image.
WhatsApp and a spate of security breaches
WhatsApp, one of the most popular messaging apps worldwide, wasn't immune to security flaws. In 2019, a vulnerability was exploited to install Pegasus spyware on users' devices, leading to a significant breach of confidential information, including personal messages and call logs. Another flaw, known as "Media File Jacking," was identified, affecting both Android and iOS users. This particular vulnerability allowed cybercriminals to alter media files, replacing them with inappropriate or harmful content. A notably critical issue emerged in 2021, involving WhatsApp's group chat feature, which inadvertently exposed users to phishing and other social engineering attacks due to flawed invitation controls. These incidents collectively contributed to a substantial erosion of trust among WhatsApp users.
Clubhouse's privacy controversy
Clubhouse, the audio-based social network that gained rapid popularity, faced serious backlash when a significant vulnerability was discovered. The flaw allowed malicious actors to secretly record and broadcast live audio conversations, a blatant violation of user privacy. Furthermore, the transmission of user IDs in plain text made it possible to de-anonymize conversations, adding fuel to the growing privacy concerns. The repercussions included a severe reputational hit and heightened skepticism about the security protocols of emerging social media apps.
Signal's unexpected security flaw
Signal, an app that prides itself on security, encountered a surprising setback when a vulnerability was discovered, allowing for PIN brute-force attacks. This revelation was particularly alarming given the app's reputation for robust security, and it inevitably affected its perceived reliability.
Zoom's security and privacy scandals
Zoom, a leader in video conferencing, faced multiple issues in 2020. A vulnerability was exploited by uninvited individuals to intrude on private meetings, leading to the infamous "Zoom-bombing" incidents. Furthermore, misleading claims about the app's encryption standards led to public uproar when it was revealed that Zoom had the technical capability to access private conversations. This forced the company to revamp its encryption system on a tight schedule, incurring considerable costs.
Snapchat's ongoing security struggles
Snapchat, popular among younger demographics, has had its fair share of security woes. Various vulnerabilities allowed for account breaches and even real-time location tracking, posing a severe threat to user safety and privacy. These issues resulted in negative publicity and declining user engagement.
Uber and Airbnb's security breaches
Both Uber and Airbnb have experienced security breaches that enabled attackers to take over user accounts. These incidents, involving unauthorized rides and bookings, underlined the critical importance of robust authentication mechanisms and the potential financial and reputational damages stemming from such breaches.
Fortnite’s gaming data breach
Fortnite, a gaming sensation, hasn’t been spared from security flaws. Vulnerabilities discovered allowed attackers to hijack accounts, make unauthorized in-game purchases, and access sensitive personal data. These incidents brought to light the risks associated with online gaming platforms and the need for enhanced security measures, particularly given the young age demographic of many users.
Conclusion
In summary, it's evident that mobile app vulnerabilities are a widespread issue, often underreported or overlooked by the general populace. Users must recognize the gravity of the personal and sensitive information stored within their devices and the apps they use. It's prudent to avoid reusing passwords, to be wary of suspicious apps, and to exercise caution when sharing information online. In an era where digital threats are increasingly sophisticated, vigilance is our first line of defense.
Unveiling the giants: Corporations whose flawed apps inflicted business catastrophes

In 2024, the digital finance landscape is increasingly challenged by sophisticated forms of fraud, particularly carding. This type of credit card fraud, involving the unauthorized use of stolen card information, poses significant risks to both individuals and financial institutions. This comprehensive exploration delves into the mechanisms of carding, its evolutionary trajectory in the realm of financial fraud, and the multi-faceted strategies being employed to protect bank accounts in this digitally-dominated era.
Understanding carding
Carding is a complex process initiated by the illicit acquisition of credit card information. This can occur through various methods:
• Sophisticated hacking operations that breach financial databases
• Phishing schemes designed to deceive individuals into divulging their details
• Large-scale data breaches at major retailers or financial institutions
Once fraudsters acquire this data, they test it to verify its legitimacy and then use or sell it for unauthorized transactions, often leveraging the anonymity of the dark web. The speed and stealth with which carding operations are conducted make them a particularly pernicious and challenging form of financial fraud to counteract.
The evolution of financial fraud
Financial fraud has undergone a significant transformation over the years. Initially, fraudsters employed physical methods like skimming devices on ATMs. However, the digital revolution brought about more complex and less detectable methods, including malware that captures sensitive information and sophisticated phishing operations. These digital methods necessitate equally advanced countermeasures in security and consumer awareness.
Regulatory bodies have escalated their efforts in enforcing data security standards. Financial institutions are now mandated to comply with rigorous data protection regulations, including conducting regular security audits and adhering to cybersecurity best practices. These regulations are crucial in ensuring a baseline of security across the financial sector.
Protecting bank accounts in 2024
Enhanced authentication
In response to these threats, banks have significantly enhanced their security measures. The integration of biometric verification methods, such as fingerprint and facial recognition technologies, has introduced a personalized layer of security challenging for fraudsters to replicate. Additionally, two-factor authentication (2FA), combining knowledge-based (passwords) and possession-based (a mobile device for OTPs) elements, has become a standard security practice, drastically reducing unauthorized account access.
Advanced encryption
Encryption is a cornerstone in securing data transmission. Modern banking involves sophisticated encryption protocols that cloak data during transmission, making it virtually impenetrable to interception and misuse. This ensures that even if data is captured by unauthorized entities, it remains secure and indecipherable.
AI and machine learning
The adoption of artificial intelligence and machine learning has been a game-changer in detecting and preventing fraud. These technologies analyze extensive transaction data, identifying anomalous patterns indicative of fraudulent activity. By quickly flagging these irregularities, banks can proactively address potential fraud, often before customers are aware of any risk.
Secure banking applications
The development of secure banking applications has been a focus for financial institutions. These applications come equipped with features like automatic logout after periods of inactivity, fraud alert systems, and encrypted communication channels for reporting suspicious activities. Such features empower customers to safely manage their accounts and contribute to the overall security framework.
Consumer education
Consumers are essential in safeguarding their financial information. Vigilant monitoring of account activities, cautious sharing of personal information, and using secure networks for online banking are fundamental preventive measures. Prompt reporting of any anomalies or suspicious activities to their banks is also vital in preventing the escalation of potential fraud.
Educating these consumers is pivotal in the fight against financial fraud. Banks are actively investing in campaigns to heighten awareness about safe online practices, such as recognizing phishing attempts, using secure networks for financial transactions, and the criticality of promptly reporting unusual account activities.
Conclusion
Given the dynamic nature of financial security, continuous collaboration across sectors is imperative. Financial institutions, technology companies, and law enforcement agencies must maintain open channels of communication and strategy sharing. Ongoing innovation in security technologies and consistent consumer education are critical in staying ahead of evolving threats.
As we proceed through 2024, the safeguarding of bank accounts from threats like carding requires an integrated approach. This strategy involves leveraging cutting-edge technology, enforcing strict regulatory measures, cultivating informed consumer habits, and maintaining constant vigilance. By comprehending the complexities of financial fraud and adopting comprehensive, proactive security measures, we can aim for a more secure financial environment for all participants.
Navigating financial security: Carding and bank account protection in 2024

In the current digital landscape, where we frequently engage in conversations without visual context, our reliance on audio cues to verify the identity of our conversational partners has intensified. Our brains have developed an astonishing ability to discern and recognize the intricate details in someone’s voice, akin to an auditory signature that is unique to each individual. These vocal signatures, composed of elements such as pitch, pace, timbre, and tone, are so distinctive that we can often identify a familiar voice with just a few spoken words. This remarkable auditory acuity serves us well, but it is under threat by the advent of advanced technologies capable of simulating human voices with high accuracy—voice deep fakes.
What are deep fakes?
The term 'deepfake' has quickly become synonymous with the darker potential of AI. It signifies a new era where artificial intelligence can manipulate reality with precision. Early deepfakes had their tells, but as the technology has progressed, the fakes have become almost indistinguishable from the real thing.
The entertainment industry's experimentation with deep fakes, such as the lifelike replicas of celebrities in a TV show, serves as a double-edged sword. It showcases the potential for creative innovation but also hints at the perils of AI in the wrong hands, where the distinction between truth and fiction becomes perilously thin.
The creation of voice deep fakes is rooted in complex AI systems, particularly autoencoders, which can capture and replicate the subtleties of human speech. These systems don't just clone voices; they analyze and reproduce the emotional inflections and specific intonations that make each voice unique.
The implications are vast and varied, from actors giving performances in multiple languages without losing their signature vocal emotion, to hyper-personalized virtual assistants. Yet, the same technology also opens avenues for convincing frauds, making it harder to trust the unseen speaker.
The dangers of convincing voice deep fakes
Crafting a voice deepface is a sophisticated endeavor. It involves a series of complex steps, starting with the collection of voice data to feed into AI models. Open-source platforms have democratized access to this technology, but creating a voice deep fake that can pass for the real thing involves not just the right software but also an expert understanding of sound engineering, language nuances, and the intricate details that make each voice distinctive. This process is not for the faint-hearted; it is a meticulous blend of science and art.
The misuse of deepfake technology has already reared its head in various scams, evidencing its potential for harm. Fraudsters have leveraged these fake voices to imitate CEOs for corporate espionage, mimic government officials to spread disinformation, and even duplicate voices of family members in distress as part of elaborate phishing scams. These incidents are not simply one-off events but indicative of a troubling trend that capitalizes on the inherent trust we place in familiar voices, turning it against us.
The path that deepfake technology is on raises profound questions about the future of trust and authenticity. Currently, the most advanced tools for creating deep fakes are closely held by technology companies and are used under strict conditions. But as the technology becomes more accessible, the ability to create deep fakes could fall into the hands of the masses, leading to widespread implications. This potential democratization of deepfake tools could be a boon for creativity and individual expression but also poses a significant threat in terms of misinformation, privacy, and security.
The defense against deep fakes: a multifaceted approach
To tackle the challenge of deep fakes, a robust and varied approach is essential. Researchers are developing sophisticated detection algorithms that can spot signs of audio manipulation that are imperceptible to the human ear. Legal experts are exploring regulatory measures to prevent misuse. And educational initiatives are aiming to make the general public more aware of deep fakes, teaching them to critically evaluate the media they consume. The effectiveness of these measures will depend on their adaptability and continued evolution alongside deepfake technology.
Awareness is a powerful tool against deception. By educating the public on the existence and methods behind deep fakes, individuals can be more vigilant and less susceptible to manipulation. Understanding how deep fakes are made, recognizing their potential use in media, and knowing the signs to look out for can all contribute to a society that is better equipped to challenge the authenticity of suspicious content. This education is vital in an era where audio and visual content can no longer be taken at face value.
Navigating the ethical landscape of deepfake technology is critical. The potential benefits for creative industries, accessibility, and personalized media are immense. Yet, without a strong ethical framework, the negative implications could be far-reaching. Establishing guidelines and best practices for the responsible use of deepfakes is imperative to prevent harm and to ensure that innovation does not come at the cost of truth and trust.
Conclusion
As voice deep fakes become more advanced, they pose a significant challenge to the trust we place in our auditory perceptions. Ensuring the integrity of our digital communications requires not just caution but a comprehensive strategy to navigate this new terrain. We must foster a society that is equipped to recognize and combat these audio illusions—a society that is as critical and discerning of what it hears as it is of what it sees. It is a complex task, but one that is essential to preserving the fabric of trust that binds our digital and real-world interactions together.
The trustworthiness of sound in the age of voice deepfakes

Information security (IS) courses are needed not only for IS department employees and not even only for certain employees of a company but for everyone. Information security training in today's world, where virtually all areas of life have been digitized, should be on par with fire safety and other fundamental rules that employees are required to observe in the workplace.
Even the most ordinary employee today has access to corporate email or other means of communication within the company, as well as internal information systems and archives. If they do not know the basic rules of cyber hygiene or do not update them in a timely manner, they can become a springboard for attackers to access sensitive company data.
In this article, we will discuss the importance of cyber hygiene in the enterprise, why this knowledge needs to be updated, the pros and cons of in-house and third-party cyber security courses, and what should be included in a cyber hygiene course.
Why cyber hygiene training matters
Almost every aspect of modern business operations has been transformed by the digital revolution. From communication to data storage, the modes have shifted from tangible to virtual platforms. This transition has been a boon in many ways. However, the virtual world, much like its physical counterpart, is not devoid of threats.
Previously, threats were physically visible, like a fire, necessitating measures like fire drills. Today, threats are more intangible, often lurking behind an innocent-looking email or website link. This paradigm shift means that cyber safety has become as crucial as any other workplace safety protocol. It is here that cyber hygiene courses play a significant role.
Most employees, regardless of their designation or role, interface with digital tools like emails, messaging platforms, and digital databases. This widespread access to digital tools, while indispensable, poses a significant risk. If employees are not equipped with basic cyber hygiene knowledge, even unintentional actions can expose the entire organization to threats.
A deep dive into the essentials of cyber hygiene training
Every company has a diverse set of employees, from those in HR and marketing to IT professionals, legal experts, and database managers. While their roles vary, their interaction with the company's IT infrastructure is common, necessitating cyber hygiene training for all in the following categories:
Awareness of threats. The digital realm has a vast array of threats, from phishing attacks to malware and deceptive social engineering tactics. Comprehensive training ensures employees can identify these threats, mitigating potential risks.
Password protocols. A strong password can often be the first line of defense against cyber-attacks. Employees need guidance on creating robust passwords and the benefits of two-factor authentication.
Data protection. Data is often referred to as the 'new oil.' In a business context, data can include everything from company secrets to customer details. Understanding the importance of data and the protocols for its protection is paramount.
Incident management. Not every threat can be prevented. However, swift action can often limit the damage. Employees should be trained to recognize unusual activities and report them promptly.
The in-house vs. third-party training dilemma
Recognizing the need for training is only the beginning. The subsequent challenge is determining the optimal delivery method. The question arises: should businesses lean on their established in-house IT teams, or would it be wiser to seek the expertise of external professionals?
When considering the Advantages of Engaging External Specialists, several factors stand out:
Proficiency. Firms in the cybersecurity domain naturally offer a reservoir of specialized knowledge. Their immersion in the field ensures that they bring a high degree of expertise to the table.
Bespoke solutions. Each business has its nuances. Recognizing this, external specialists are adept at fashioning strategies that are uniquely tailored, focusing on a company's specific requirements and vulnerabilities tied to their industry.
State-of-the-art tools. Another compelling reason to consider them is their familiarity with the latest in the cybersecurity landscape. These experts have their fingers on the pulse, utilizing cutting-edge tools and being aware of evolving threat scenarios. This ensures training remains pertinent and forward-thinking.
Yet, it's essential to balance these benefits with potential drawbacks. Among the challenges of relying on external expertise are the costs involved, which can stretch the budget, especially for larger organizations. There's also the concern that an external perspective might miss nuances inherent to a company's internal processes and culture.
On the other hand, the Benefits of Internal Training are manifold:
Personalization. An internal approach offers a distinct advantage in its adaptability. Companies can sculpt the training, ensuring it's laser-focused on their infrastructure and unique challenges.
Autonomy. Having in-house training offers an unparalleled level of control. Every stage, from conception to delivery, remains under the company's purview.
The economic perspective. While the outset might require considerable investment, the long-term financial implications of in-house training can often skew towards being more economical.
Yet, as with all strategies, there are inherent challenges to consider. Relying solely on in-house capabilities can sometimes lead to gaps in expertise. Limited resources might also become a constraint, and the time commitment to design and implement robust training modules shouldn't be underestimated.
Ensuring periodic refreshers
Experts recommend holding awareness courses at least once a year to update employees' knowledge and skills. Whenever new technologies are introduced or new security threats emerge, separate training should be conducted. This is to ensure that knowledge is up-to-date and to avoid compromising the effectiveness of the company's defenses.
Employees who have already taken a full course do not need to retake the same course every year. Testing can be done to determine if the employee has lost knowledge, as well as new training on updates and new attack techniques. For those employees who have forgotten some of the topics and have difficulty with them, a shortened version of the training can be scheduled. Also, knowledge should be updated after a cyber incident and a case study should be conducted.
The bottom line
Cybersecurity today has become an important part of human security. While in the past it was more common to steal money in the underground or on the street, today it is increasingly being done online. Whereas in the past, attackers only had physical opportunities to harm a business, today any company can be attacked online.
Statistically, the most common cause of a cyberattack is human error. That's why employee cyber hygiene training is the foundation of all the basics in a company's information security. No matter how advanced anti-viruses are installed, no matter how professional the IS department is, one small mistake by an ordinary manager and the company's database is in the hands of attackers or a malicious program enters the company's network.
Regular sessions on cyber security not only prevent such incidents but can also help raise threat awareness and strengthen the security culture of an organization.
The necessity of cyber hygiene training in today's digital world

Augmented Reality (AR) has made a huge impact on various sectors, ranging from gaming and entertainment to healthcare and industrial applications. As AR technologies evolve, concerns regarding their safety are becoming more prominent. This article analyzes the safety aspects of AR technologies through various lenses — user health, data security, and public safety.
User health
One of the foremost concerns regarding AR technology is its impact on user health. Extended usage of AR glasses or headsets can lead to eye strain, fatigue, and in severe cases, altered perception of the real world. For instance, Microsoft’s HoloLens, a pioneering AR headset, initially faced criticism for causing discomfort during extended use. Manufacturers have since been focusing on reducing weight and improving ergonomics. Moreover, as AR applications can be very immersive, there's a risk of physical accidents due to users not being fully aware of their surroundings. Niantic’s Pokemon Go, an AR game, reported several accidents where users, engrossed in the game, inadvertently put themselves in danger. To counter this, developers are now integrating real-world awareness features in applications to alert users of potential hazards.
Data security
As AR technologies often require access to sensitive data, such as user location and preferences, ensuring data security is imperative. Cyber-attacks aimed at AR devices can compromise personal information and in cases of industrial applications, trade secrets. For instance, the AR application Wikitude, which provides information about nearby locations, requires access to the user's location data. A breach could reveal sensitive information about a user’s movements. To mitigate such risks, companies are employing end-to-end encryption and robust authentication methods. Also, adherence to data protection laws such as the General Data Protection Regulation (GDPR) is essential.
Public safety
AR technologies have the potential to impact public safety. For instance, the use of AR in automobiles for navigation and information display should not divert the driver’s attention and contribute to accidents. Furthermore, as AR becomes prevalent in public spaces, such as shopping malls or airports, ensuring that AR content does not create panic or confusion is vital. In the automotive industry, companies like Hyundai are integrating AR in their Head-Up Displays (HUDs) to ensure that the information is non-intrusive and genuinely aids the driver without causing distractions.
Regulatory scrutiny
Regulatory bodies worldwide are keeping a close watch on AR technologies. The US Food and Drug Administration (FDA), for example, is actively involved in regulating AR devices used in healthcare. AR applications in surgeries and diagnostics should comply with safety and efficacy standards. Additionally, the Federal Trade Commission (FTC) may also step in to ensure that AR advertising does not mislead or harm consumers.
Social implications
It's also crucial to consider the social implications of AR. For instance, Google Glass faced backlash due to privacy concerns, as people around the wearer were unaware if they were being recorded. AR technologies must respect social norms and privacy expectations. Users should be informed and in control of the data that AR applications access and share.
The industrial aspect
In industries, AR is used for training, maintenance, and complex assembly tasks. While it enhances productivity, it is vital to ensure that AR does not compromise worker safety. Lockheed Martin, an American global aerospace, defense, and security company, employs AR for assembly and manufacturing processes. They have integrated safety protocols that make sure that AR usage complies with workplace safety norms.
Future directions
To ensure that AR technologies remain safe as they continue to evolve, a multi-pronged approach is needed. This includes continuous evaluation and improvements in hardware design, stringent data security measures, adherence to regulatory norms, and public awareness campaigns. The development of international safety standards for AR technologies could also be instrumental in ensuring a globally accepted safety benchmark.
Human factors
One aspect that needs further investigation is how AR affects human psychology and behavior. In educational environments, for example, AR can be a powerful tool. However, over-reliance might impede critical thinking and problem-solving skills if not implemented thoughtfully. It's essential that educationalists and psychologists work together with technology developers to create AR content that enhances learning while nurturing essential life skills.
Economic concerns
The economic implications of AR should not be ignored. As industries adopt AR for various applications, the job market dynamics are likely to change. On one hand, AR can enhance productivity and create new avenues for employment, but on the other hand, it can also render certain jobs obsolete. Governments and policymakers need to be proactive in identifying such trends and ensuring that the workforce is prepared to adapt to these changes.
Privacy paradox
The privacy concerns associated with AR are particularly challenging. As AR devices become more integrated into our daily lives, the line between what is private and what is not begins to blur. For example, future AR glasses might be capable of facial recognition and instant background checks. While this could be useful in certain scenarios, it raises significant ethical and privacy concerns. In this context, robust and adaptable privacy laws are crucial. Users should have the autonomy to control the data they share and understand the implications.
Ethical considerations
Beyond privacy, there are broader ethical questions to consider. As AR can manipulate the perception of reality, there is potential for misuse. The deepfake technology, for instance, can be combined with AR to create hyper-realistic forgeries that can deceive individuals. This could have serious implications in terms of misinformation, fraud, and personal safety. Ethical guidelines and regulations that specifically address such concerns are required.
Digital divide
As AR technologies advance, there is also a risk of widening the digital divide. Those who have access to these technologies may have significant advantages in terms of education, employment, and social opportunities compared to those who don’t. Ensuring that AR technologies are accessible and affordable is an important societal challenge that needs addressing.
Conclusion
AR technologies are a double-edged sword. On one side, they hold immense potential in enhancing our capabilities and experiences; on the other, they bring along a host of concerns pertaining to health, data security, public safety, ethics, and social equity. As technology continues to evolve, a multidisciplinary approach involving technologists, psychologists, lawmakers, ethicists, and the public is essential in ensuring that the development of AR is guided by principles that prioritize human safety and well-being. The road ahead should be paved with innovation, but caution should be the guiding light.
How safe are AR technologies?

In the modern, fast-moving era, mobile banking has emerged as the go-to banking method for a vast majority. The allure of accessing your bank account from any location at any moment has indeed contributed to its widespread adoption. Yet, this ease of access is not without its drawbacks, primarily in the form of potential security breaches in mobile apps.
Mobile banking applications have turned into a hotspot for cybercriminals, incessantly seeking opportunities to exploit any weak points present in these apps. A security infringement in a mobile banking app can have catastrophic repercussions, affecting not only the individual user but also the banking institution at large.
In this article, we delve into the prevalent security threats that mobile banking apps are prone to, and the preventative measures that can be adopted to counteract these threats. But first, let's delve into the reasons behind the susceptibility of banking apps to such threats.
What makes banking apps prone to attacks?
The popularity of mobile banking apps among cybercriminals is hardly surprising. These apps harbor confidential data, including account details and personal identification information, which can be manipulated to siphon off funds or perpetrate identity fraud. Moreover, the extensive user base of these apps globally makes them a lucrative target for cyber assaults. While mobile banking apps offer a seamless user experience, they inadvertently create substantial security loopholes for both the users and the financial entities involved.
The security gaps in banking apps can facilitate unauthorized access to user accounts, data theft, and unauthorized fund transfers, among other issues. Cybercriminals might employ phishing schemes or other social engineering strategies to deceive users into disclosing confidential information or installing malware on their devices. Furthermore, these security lapses can tarnish the reputation of financial organizations. A data leak or other security incidents can diminish customer confidence and harm the brand's image. Several factors contribute to these risks, including:
Complexity. Contemporary banking apps are laden with a plethora of features aimed at enhancing user convenience. However, this complexity also escalates the difficulty in securing the apps, as each new feature potentially introduces new vulnerabilities.
Third-party integrations. A significant number of mobile banking apps depend on third-party code libraries and frameworks for functionalities like payment processing and data storage. These components, although handy, can pose security threats if not adequately scrutinized for vulnerabilities.
User conduct. Users can inadvertently augment the vulnerability of banking apps by opting for weak passwords, reusing passwords across various accounts, or neglecting timely security updates.
Indeed, these elements collectively render banking apps a lucrative target for attackers. Therefore, it is imperative for financial institutions to fortify their mobile apps to safeguard user data and assets. Having understood the vulnerabilities, let's now explore the specific threats that mobile apps are exposed to.
Identifying common vulnerabilities in banking apps
Cybercriminals are perpetually scouting for weaknesses in these apps to exploit and gain unauthorized access to user accounts. Despite the security protocols in place to shield user data, here are some prevalent vulnerabilities that could undermine mobile banking security:
Inadequate data protection. Mobile banking apps sometimes store sensitive details like user credentials and transaction histories on the device itself. If not encrypted or securely stored, this data can be an easy target for attackers.
Interception attacks. Man-in-the-middle (MITM) attacks happen when a hacker intercepts the communication between the user's device and the app's server, allowing them to view and alter the transmitted data, including login details and financial transactions.
Weak authentication protocols. Insufficient authentication methods, such as basic passwords or lack of multi-factor authentication, can facilitate easy access to user accounts for attackers. Hence, robust lockout systems, along with multi-factor authentication, should be implemented to prevent brute-force attacks.
Service sharing. Mobile banking apps sometimes share services with other apps on a device, creating potential security risks if those apps are susceptible to attacks.
Flawed encryption techniques. Encryption is vital for safeguarding sensitive data. However, if a banking app employs weak or improperly implemented encryption algorithms, it can be easily bypassed by attackers. Code Manipulation Attackers might alter the app's code by adding or modifying malicious code, enabling them to access confidential data or seize control of the app.
Exploiting app vulnerabilities. Attackers might exploit vulnerabilities in the app itself, arising from insecure coding practices or outdated software components. A notable instance is the 2016 incident where hackers siphoned off $81 million from the Bangladesh Central Bank by exploiting a flaw in the SWIFT payment system utilized by the bank.
These vulnerabilities can severely compromise mobile banking security, potentially leading to financial losses and identity theft. Hence, it is vital for app developers to establish stringent security protocols.
How to fortify your mobile banking apps?
To guarantee the integrity of mobile banking apps, it is essential to adopt potent security strategies. In this segment, we will outline some of the most effective security protocols to shield against common app vulnerabilities:
Data encryption. Encrypting data is a potent security strategy that renders the data unintelligible to those without the decryption key, thereby thwarting attempts to misuse encrypted sensitive data.
Multi-factor authentication (MFA). MFA necessitates users to furnish multiple forms of verification before accessing their accounts, adding an additional security layer to mobile banking apps.
Application strengthening. Application strengthening involves altering the app's code to hinder reverse engineering attempts. This includes code obfuscation, data encryption, and incorporating anti-tampering mechanisms, making it challenging for attackers to retrieve sensitive data or alter the app.
Frequent updates. Regular updates to mobile banking apps are essential to address any existing security gaps. These updates often encompass bug resolutions and security enhancements, urging users to keep their apps updated to fend off emerging threats.
It is vital for top-tier management to recognize the significance of implementing robust security protocols in mobile banking apps. This not only safeguards customer data but also preserves the brand's reputation. A data breach can incur substantial financial and reputational losses. Hence, utilizing platforms like GuardRails can facilitate easier vulnerability detection and rectification, streamlining the process for both security and development teams.
Conclusion
While mobile banking apps have transformed financial management, they have introduced significant security concerns. Given the growing reliance on mobile apps for banking transactions, safeguarding mobile banking security is paramount to prevent financial and reputational damage. It is incumbent upon both individuals and organizations to comprehend the risks and adopt necessary precautions against potential threats. Banks and financial institutions must establish robust security protocols to protect customer data and finances. We have highlighted some prevalent banking app vulnerabilities and potential mitigation strategies. Regular security assessments, staff training, and customer awareness are crucial to maintaining a resilient mobile banking security stance. By adopting these strategies, banks can substantially diminish the risk of cyber-attacks, safeguarding customer assets and data, and ensuring that the convenience of mobile banking does not compromise security.
