
In the interconnected world of the 21st century, social media platforms have seamlessly integrated into our daily lives. They have revolutionized the way we communicate, share information, and even conduct business. These platforms, while fostering global connections and instant communication, also present a double-edged sword, especially for corporate entities. The delicate balance between accessibility and security is a tightrope that many companies grapple with, often finding themselves at a crossroads.
The allure and perils of unrestricted access
The digital age has ushered in an era where information is at our fingertips. The modern employee, driven by a desire to stay connected and informed, often finds the allure of unrestricted access to social media hard to resist. While tools like anonymizers, VPNs, and TOR provide gateways to this vast world, they also inadvertently open Pandora's box of cyber threats. These backdoors, often overlooked, can be exploited by seasoned cybercriminals, leading to catastrophic data breaches, significant financial losses, and irreparable damage to reputations. This begs the question: at what cost does this unrestricted access come?
The digital footprint
Every click, post, like, share, or comment on social media platforms contributes to an extensive digital trail. This trail, visible to anyone with the right tools, can be a goldmine for cybercriminals. By meticulously combing through this data, malicious entities can construct detailed profiles, targeting not just individuals but entire corporate hierarchies. The weaponization of this information can manifest in various sinister ways, from spear-phishing campaigns targeting specific employees to broader, more devastating attacks on a company's digital infrastructure. The depth and breadth of this footprint often go unnoticed until it's too late.
Historical context: lessons from past breaches
History is replete with examples that underscore the vulnerabilities tied to social media. The 2013 breach of the Associated Press's Twitter account serves as a grim reminder. Hackers disseminated false information about a terrorist attack, causing widespread panic and a temporary stock market crash. Similarly, the 2011 attack on RSA, a renowned system developer, highlighted the dangers of seemingly innocuous phishing emails. These emails, sourced from data harvested from social media, contained malicious links that, once clicked, wreaked havoc on the company's systems. More recent incidents, like the one faced by Elara Caring in 2020, further emphasize the ever-present and evolving nature of these threats.
The multifaceted nature of social media threats
The digital realm is vast, and so is the spectrum of threats emanating from social media. Phishing attacks, where cybercriminals don the guise of trustworthy entities, are becoming increasingly sophisticated. Corporate espionage, where competitors or rogue actors siphon confidential information for financial or strategic advantage, adds another layer of complexity. Even actions that seem benign on the surface, like an employee sharing a casual photo from their workstation, can inadvertently disclose confidential information. The ripple effects of such breaches can be far-reaching, affecting not just the immediate organization but also its stakeholders.
Towards a comprehensive security strategy
In the face of such multifaceted threats, a piecemeal approach to security won't suffice. Companies need a comprehensive, holistic strategy. This involves regular employee training not only to equip employees with the tools to recognize potential threats, such as phishing emails but also to instill a culture of vigilance and best practices for online behavior. The nuances of password security, the importance of two-factor authentication, and the need for restricted access rights are foundational pillars that need to be emphasized.
However, human vigilance alone isn't enough. The rapid advancements in technology have armed companies with powerful tools like AI and machine learning. These technologies, capable of analyzing vast datasets swiftly, offer a proactive approach to security. They can detect anomalies, identify potential threats in their nascent stages, and even block malicious attempts, such as phishing emails before they reach their intended targets.
The collaboration further strengthens this security framework. In the vast expanse of the digital realm, no company stands alone. By forging strategic alliances with external partners, including cybersecurity firms and industry peers, companies can share insights, pool resources, and present a united front against cyber threats. This collaborative ethos ensures that knowledge and expertise are continuously exchanged, enhancing the collective security posture.
Lastly, adaptability is key. The digital threats of today might not be the same as those of tomorrow. A robust security strategy is dynamic, evolving in response to new challenges and threats. Feedback mechanisms, where employees can promptly report suspicious activities, coupled with regular audits and assessments, ensure that security measures remain agile and ahead of potential threats.
Conclusion
The intricate dance between social media and corporate security is a testament to the challenges and opportunities of the digital age. While the threats are formidable, a proactive, informed, and collaborative approach can keep them at bay. In this ever-evolving landscape, security is not just an IT concern; it's a collective responsibility. By fostering a culture of awareness, vigilance, and collaboration, corporations can navigate the digital realm confidently, reaping its benefits while ensuring their assets remain secure.
The digital dilemma: navigating social media's threats to corporate security

Within the spheres of information systems and software development, the role of test servers is undeniably essential. Test servers are purpose-built environments designed to experiment, examine new features, and test software updates without posing any threat to the stability and continuity of the main operational systems.
However, the nature and purpose of these test servers inherently introduce an array of information security risks. In this more extensive discussion, we will delve deeper into the central cybersecurity issues associated with the operation of test servers, and propose potential countermeasures and protective strategies.
Unpacking the core problem
A prevalent misconception among developers and IT professionals is that test servers represent an insignificant component within the larger company infrastructure. Consequently, they often exhibit a level of nonchalance towards these servers' security, believing that any attack, compromise, or system failure will not impact the primary infrastructure's operation.
Simultaneously, the Information Security (IS) departments within organizations often relegate test server security to a lower priority, given the servers' perceived secondary status compared to the primary, production-grade infrastructure, which typically enjoys robust technical and organizational protection measures.
However, despite this dismissive attitude, test servers frequently handle sensitive data during the testing and debugging process. This data can range from main infrastructure configuration elements to the personal data of clients or employees. The result is a precarious situation where developers are utilizing sensitive data in an environment with minimal control and oversight, and the IS department is without the necessary resources and technical wherewithal to guarantee the security of this process. Given this scenario, an incident becomes not a matter of if, but a matter of when it will occur.
Incidents of note involving test servers
Due to their generally weaker protection measures compared to the main infrastructure, test servers can become attractive targets for cyber attackers. Malevolent actors can exploit these servers as a backdoor into the main infrastructure or gain unauthorized access to sensitive company data. This risk is clearly exemplified in several high-profile incidents:
Uber, in 2016, was subjected to a significant security breach related to their test server. Intruders were successful in accessing Uber's GitHub repository that stored archived files of application code. As a direct consequence of this incident, the perpetrators were able to access sensitive data, including comprehensive user and driver details.
Facebook, in 2013, fell victim to a data breach caused by insecure configuration and setup of a test server. The attackers managed to access a test server loaded with various development and testing tools. As a result, the personal data of over 6 million users were compromised, showcasing the potential harm from such incidents.
British Airways, in 2018, suffered a security breach that impacted their test server. Attackers intercepted data, including the personal and financial information of over 380,000 customers, by injecting malicious code into the airline's test server.
These incidents not only underscore the fact that the issues surrounding test servers can affect a wide array of industries but also emphasize that a security breach does not always necessitate an external hacker or intruder.
Pressure points and their protective measures
Test servers are generally configured to favor the IT department's ease of use, thus inadvertently leading to conventional security issues such as weak passwords and a lack of access restrictions. While such configurations might provide comfort to developers, they pose serious implications for overall information security. Some common issues related to test server security are:
Data sensitivity. It's common for companies to overlook the necessity to disguise or mask data used for testing. Similarly, it's not unusual for passwords for the test infrastructure to remain unchanged for extended periods.
Protection levels. Regular servers typically have more robust protection measures such as firewalls, intrusion detection systems, and intrusion prevention systems. On the contrary, test servers, which are meant for simplified operation and testing, frequently lack these powerful security mechanisms. These servers usually belong to a separate network infrastructure that offers a lower level of protection.
Access control. In the case of test servers, all users commonly have the same high-level permissions, making the infrastructure susceptible to breaches due to weak or duplicated passwords.
Vulnerabilities and bugs. Test servers, being the platform for new features and updates, may often contain older software versions, potentially brimming with exploitable vulnerabilities.
To tackle these issues, one primary protection method is to never use sensitive data in its unprocessed form on test servers. Data masking, despite being resource-intensive, can significantly decrease the severity of a potential leak.
In addition, the importance of a well-structured regulatory framework cannot be overstated. Even with minimal resources, adhering to a set of clear, structured regulations can greatly enhance the security of the test infrastructure.
Final thoughts
Security measures for test servers form a vital part of the overall development and testing process. Although dealing with test servers carries inherent risks that can have severe consequences for the company and its users, implementing appropriate security measures can greatly minimize these risks.
Key steps towards secure test servers include the isolation of test servers on a separate network, deployment of robust authentication and authorization mechanisms, regular server updates and configurations, restrictions on access to test data, and frequent vulnerability checks.
Security should not be an afterthought, but rather an integral part of every phase of development and testing. By instilling strong security measures, adhering to industry best practices, and regularly updating your security policies in line with the latest information security trends, the risks associated with test servers can be substantially mitigated. This ensures that data confidentiality and integrity are preserved, protecting your company from potential threats and incidents associated with test servers.
Test servers: the pitfalls of information security

When it comes to investing in company security, there are different approaches. Some organizations allocate substantial funds to proprietary solutions offered by vendors, while others opt to develop their own SIEM (Security, Information and Event Management systems) using open-source code.
The question arises: which option is more cost-effective in practice? Should one pay for a proprietary solution or rely on open-source alternatives? In this article, we delve into the realm of free SIEM solutions used in companies today, as well as the reasons why information security specialists often exhibit reluctance towards them.
A closer look at open-source SIEM systems
The appeal of open-source solutions increases with fewer restrictions. The most popular free SIEMs possess the ability to handle any number of users and data, offering scalability, and garnering support from the IT community.
Among the top-tier open-source SIEM systems, you’ll find:

AlienVault OSSIM SIEM. A version of AlienVault USM, a leading solution in this domain worldwide. Users gain access to a free framework encompassing intrusion detection systems, network and host monitoring, vulnerability scanning, and other open-source tools.

MozDef. Developed by Mozilla, MozDef is a SIEM system created from scratch. Similar to AlienVault OSSIM SIEM, it is built upon tried and tested open-source projects. The developers claim that MozDef can handle over 300 million events daily.

Wazuh. Originally developed within another open-source SIEM system called OSSEC, Wazuh evolved into a standalone product. It is capable of simultaneously collecting data through agents and system logs. Wazuh boasts a modern web interface, REST API, and an extensive set of rules.

OSSEC SIEM. Often referred to as the older sibling of Wazuh, OSSEC SIEM is widely recognized in the information security community as a reliable free intrusion detection solution.

Sagan. This SIEM tool specializes in real-time analysis of network inputs and the evaluation of their correlations. Its high performance stems from a multi-threaded architecture.

Prelude OSS. Serving as an open-source counterpart to the paid Prelude SIEM system from French developer CS, Prelude OSS supports various log formats and seamlessly integrates with popular open-source tools developed by others.
Additionally, companies often employ other free products like ELK SIEM, Snort, Suricata, SecurityOnion, Apache Metron, and more to construct their own systems. Many of these options are limited versions of proprietary software offered by vendors to familiarize users with their core systems.
When open source code is appropriate
One popular reason for implementing open-source SIEM today is to test-drive commercial systems, even with a minimal set of features. Free open-source versions allow professionals to evaluate expensive products in a live environment and gain insights into their inner workings.
Moreover, an open-source SIEM system becomes a viable choice when an organization can engage a large team of programmers. Any open-source solution necessitates further development and adaptation to fit seamlessly within the company's IT infrastructure. If there is no team available to handle these tasks, the utilization of free solutions loses its purpose.
One of the main challenges faced by companies employing open-source software is the lack of qualified specialists. Developing and maintaining such SIEM systems requires experienced Linux administrators, analysts, and experts proficient in connecting new sources, developing correlation rules, designing dashboards, and more. Given that freeware often comes with minimal features and customization options out of the box, significant work is involved, particularly during the initial months post-implementation.
These factors can impact the total cost of ownership of a system. Consequently, Open Source SIEM is a viable choice only for those who possess a thorough understanding of their requirements and have the necessary resources.
Challenges in open-source SIEM
There is a saying that "Linux is only free when you don't value your time." The same holds true for open-source SIEM tools. Difficulties in product improvement contribute to the compromised security of open-source products. Addressing identified vulnerabilities can often take weeks or even months, providing an opportunity for cybercriminals to exploit them.
There are other notable considerations when it comes to open-source SIEM. Specifically, an open-source system. For example, it lacks official technical support: User queries regarding installation and maintenance of free solutions are typically addressed by fellow users, rather than a dedicated owner-developer of the software. Moreover, it may simply cease to exist. Indeed, even if a community actively supported a product yesterday, it may be abandoned the next day, leaving users without crucial updates.
Next, it’s not a ready-to-use solution. To ensure proper functioning with data sources, connectors are required to convert incoming events into a compatible format for further processing.
These challenges are inherent to open-source SIEM systems and cannot be completely avoided. It is up to each company to determine whether they are willing to accept these risks.
Conclusion
Open Source SIEM systems are not universally suitable for every company. On one hand, adapting open-source code to align with specific requirements necessitates a team of highly skilled IT professionals and significant financial resources. On the other hand, regulatory requirements often dictate the installation of certified software in most cases.
However, dismissing open-source tools entirely would be unwise. They can be employed as references when establishing requirements and preferences for paid SIEM solutions.
Exploring free open source SIEM tools: Advantages and disadvantages

This latest update demonstrates our focus on refining user experience and enhancing collaborative password management.
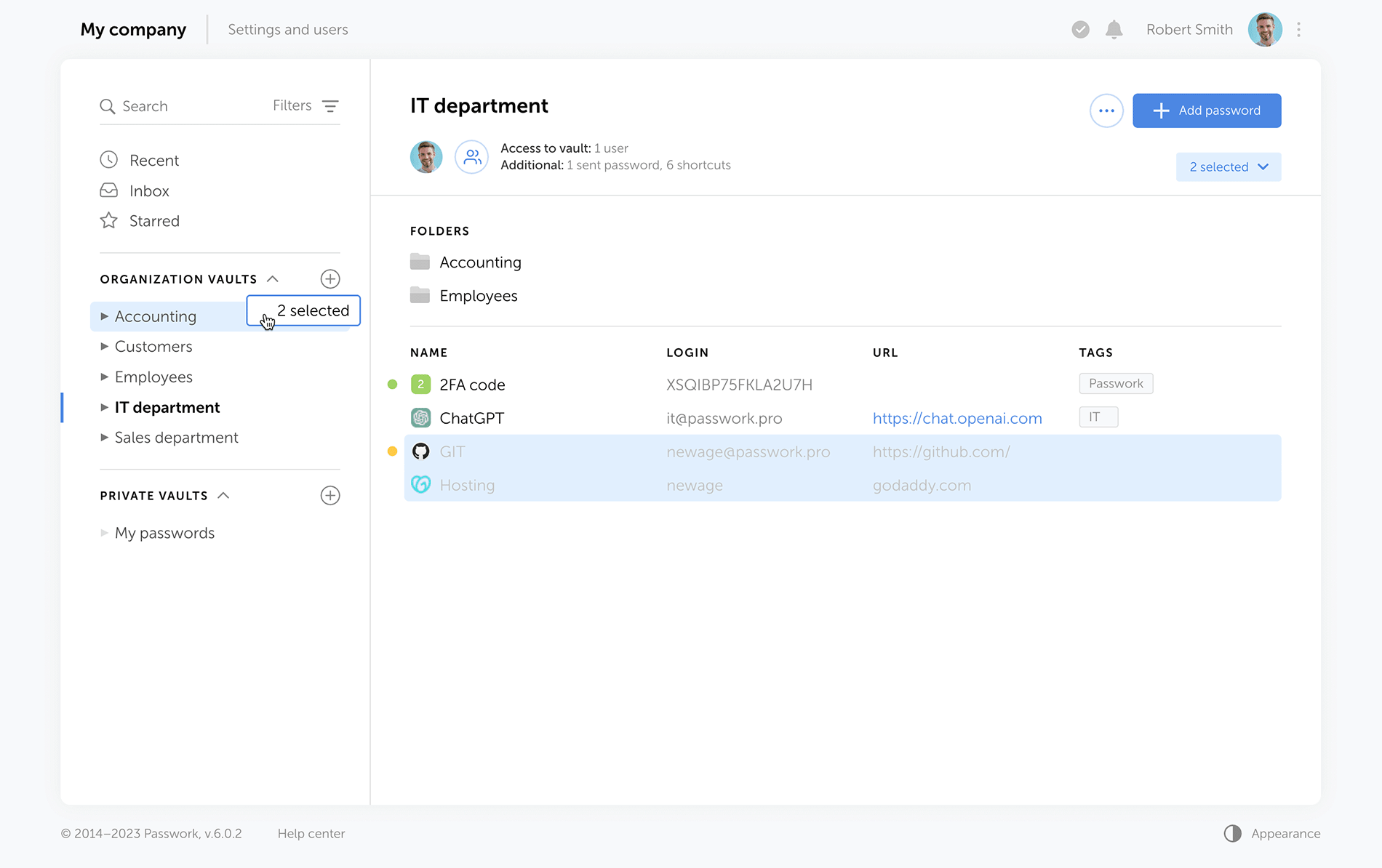
No longer will you need to create password copies in various vaults — we've introduced shortcuts. With these handy labels, you can easily organize access to passwords from different directories.
The new enhanced settings provide administrators with more control over configurations and user rights, and all changes require approvals, preventing any unintentional actions.
LDAP user management has now become simpler with its cleaner interface and background data updates.
In addition to that, Passwork 6.0 brings new notifications and interface improvements. All these enhancements contribute to a more comfortable user experience while ensuring the security of passwords and sensitive data.
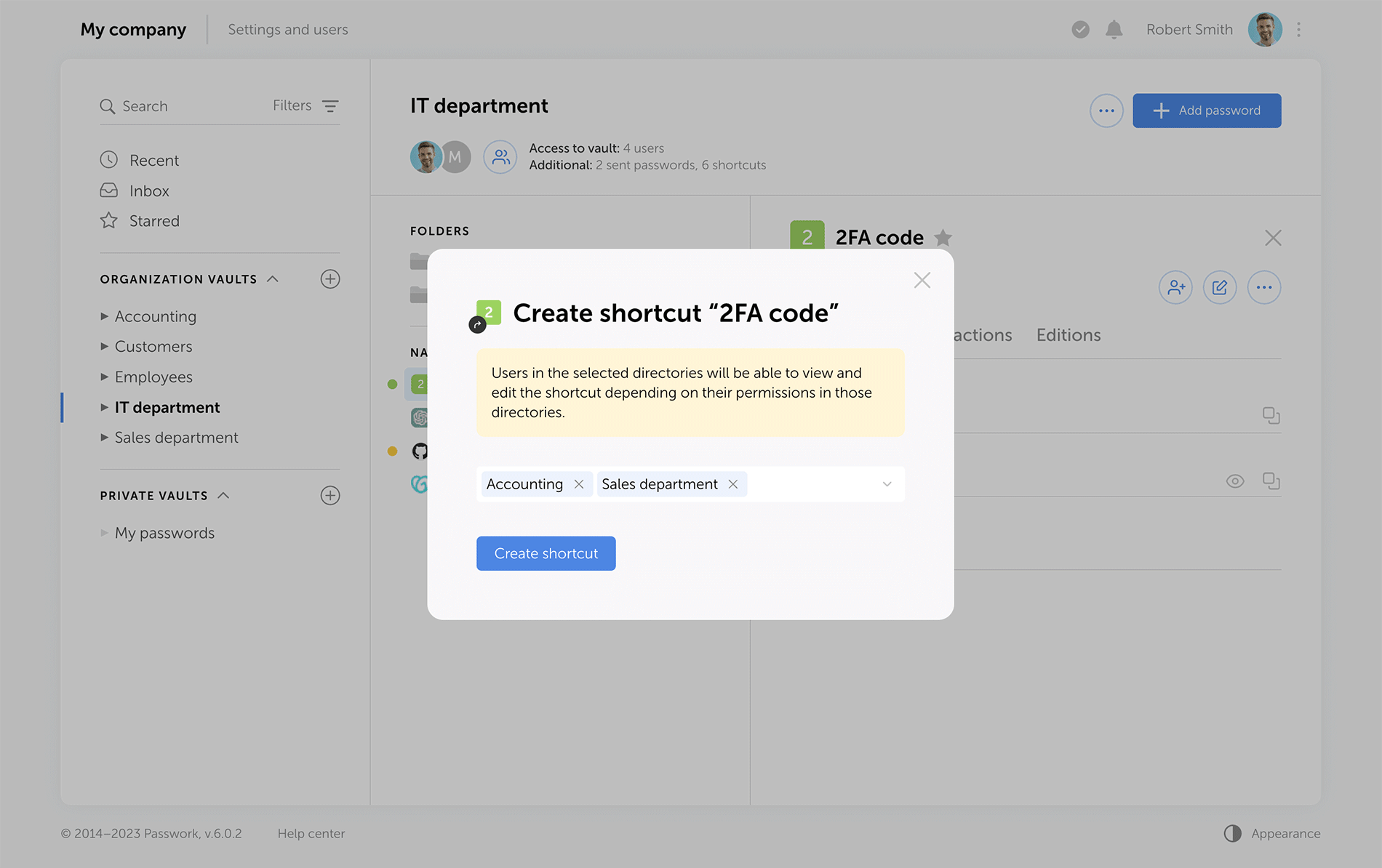
Shortcuts
Shortcuts are a new way to share passwords, enhancing collaboration flexibility. There's no need for creating password duplicates in different vaults — instead, create multiple shortcuts in required directories. All changes to original passwords are reflected in shortcuts, keeping your team up to date. Users can view or edit data via shortcuts according to their access rights.
Sending passwords without granting partial access to vaults
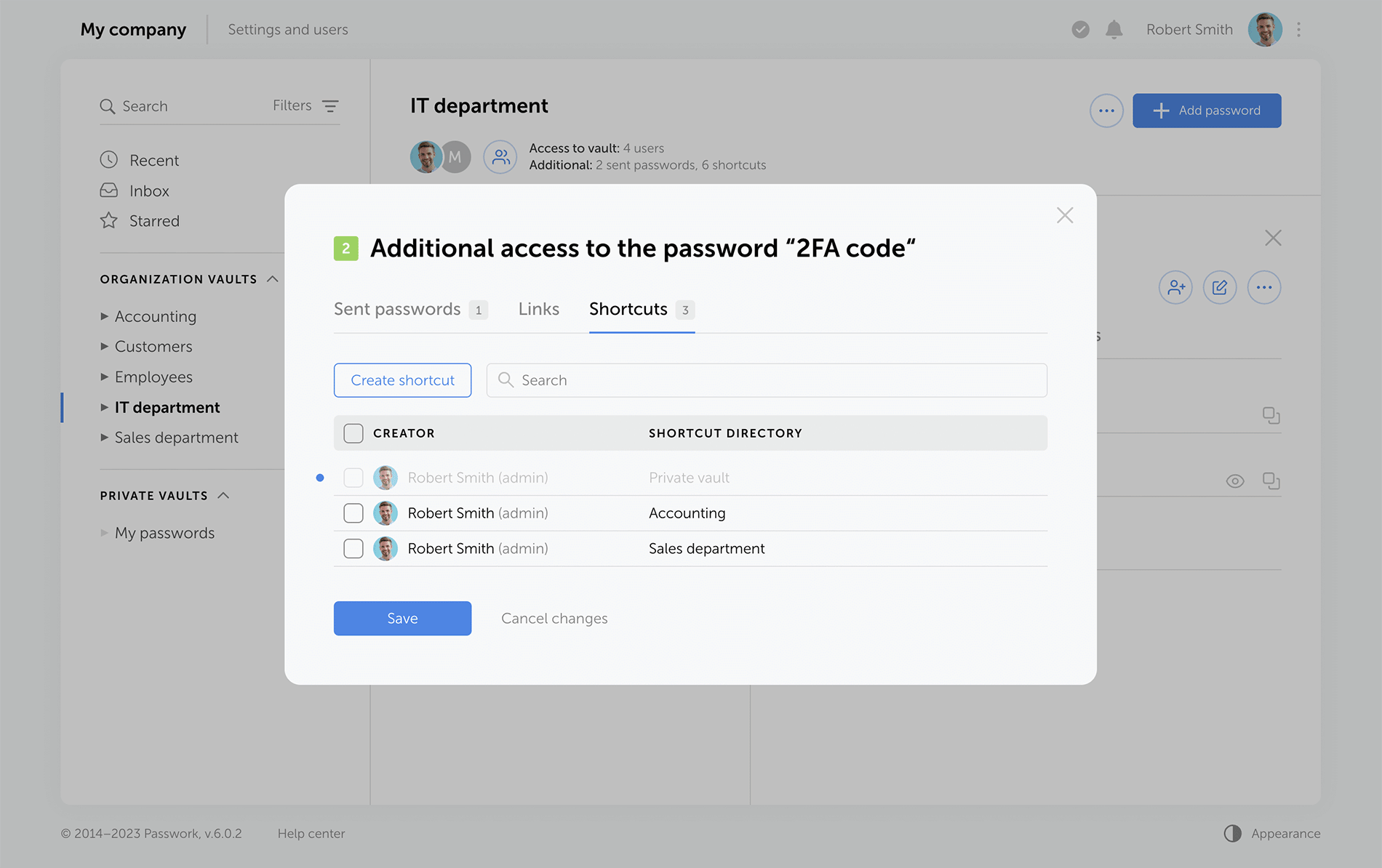
Previous versions of Passwork encrypt passwords at the vault level. This type of encryption gives users partial access to vaults even when a single password is shared with them. Now, when users access passwords via their "Inbox" or a shortcut, they receive keys to specific passwords, but not their vaults.
Administrators can clearly see who has vault access rights, and who can only work with specific passwords.
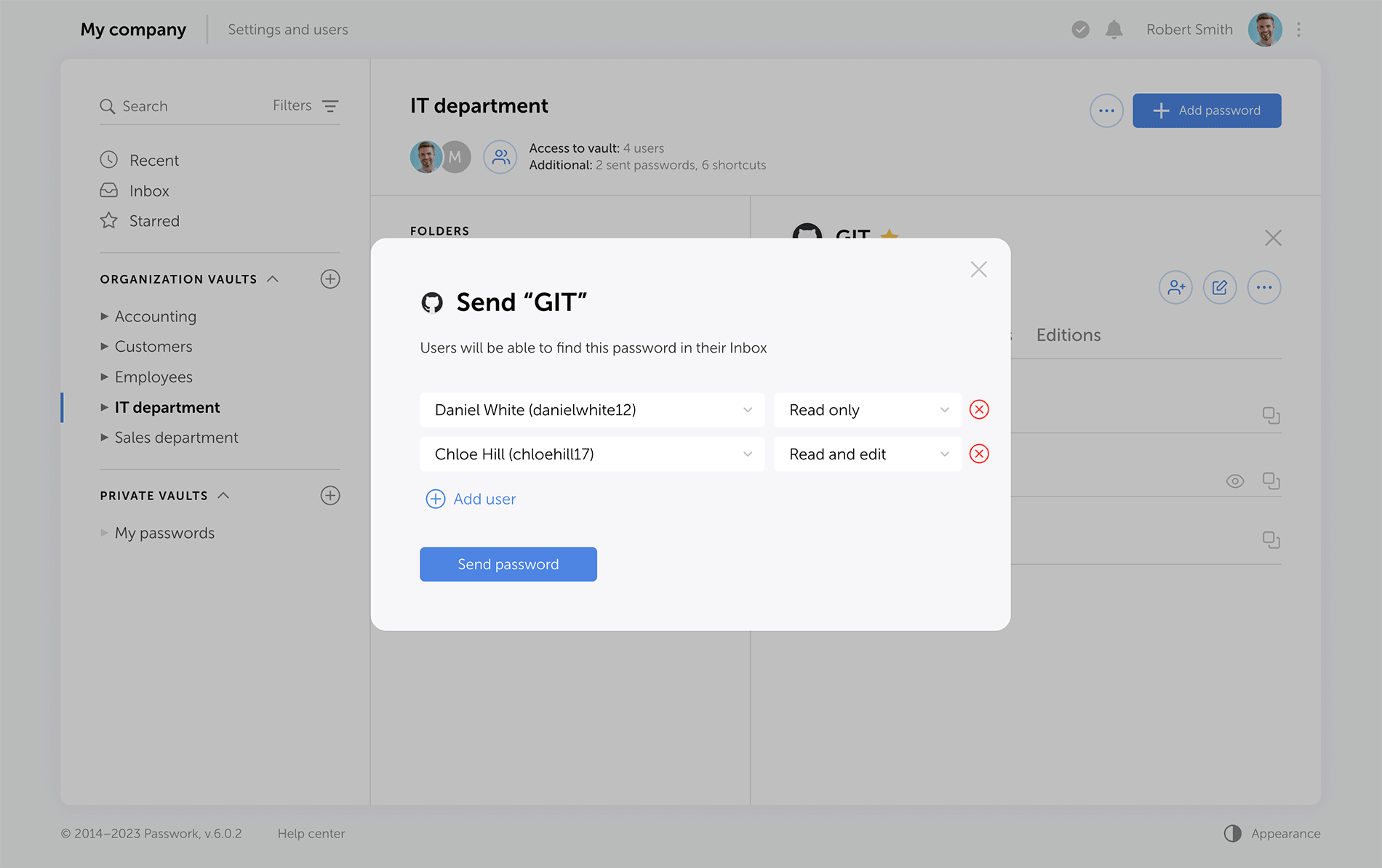
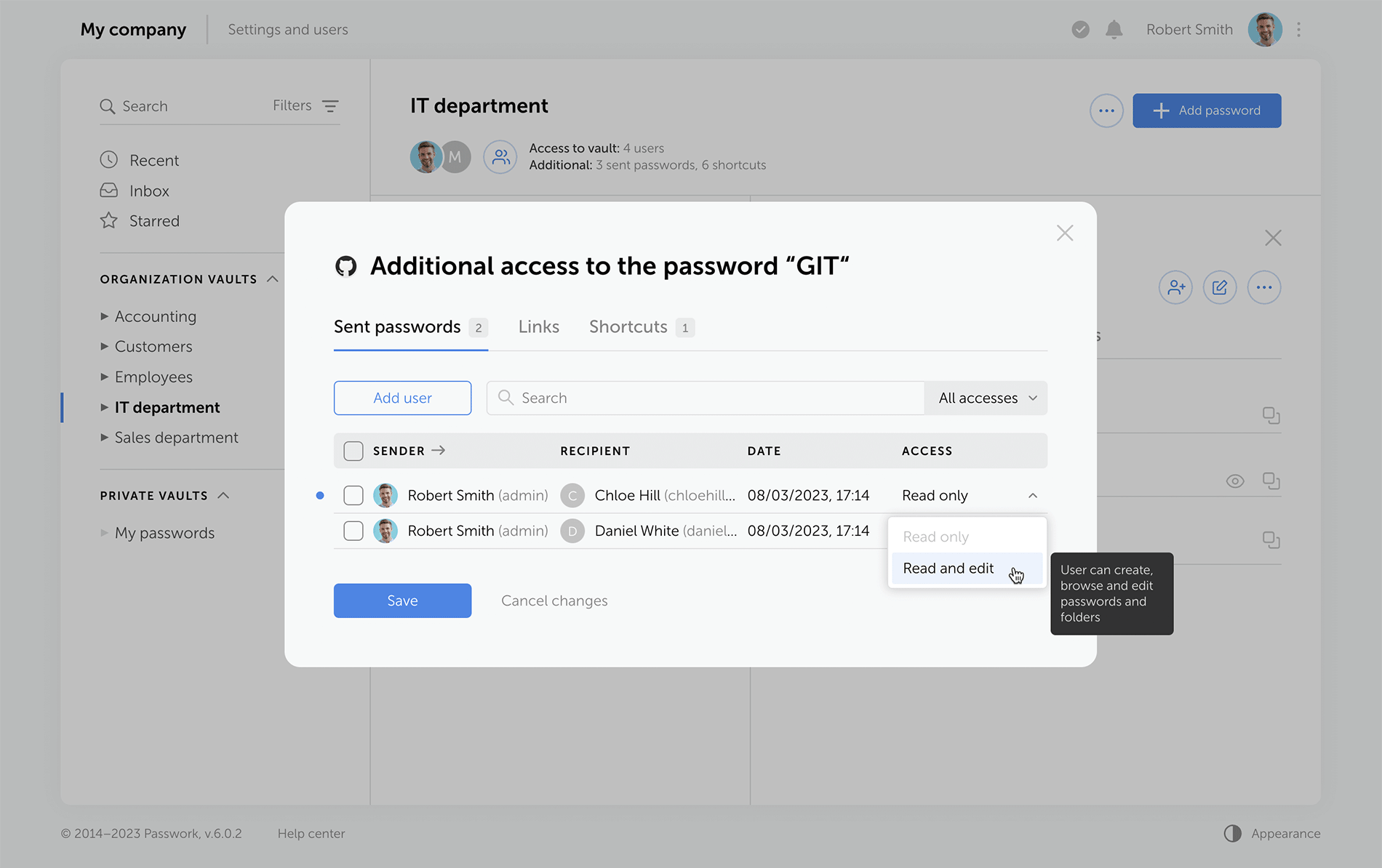
LDAP
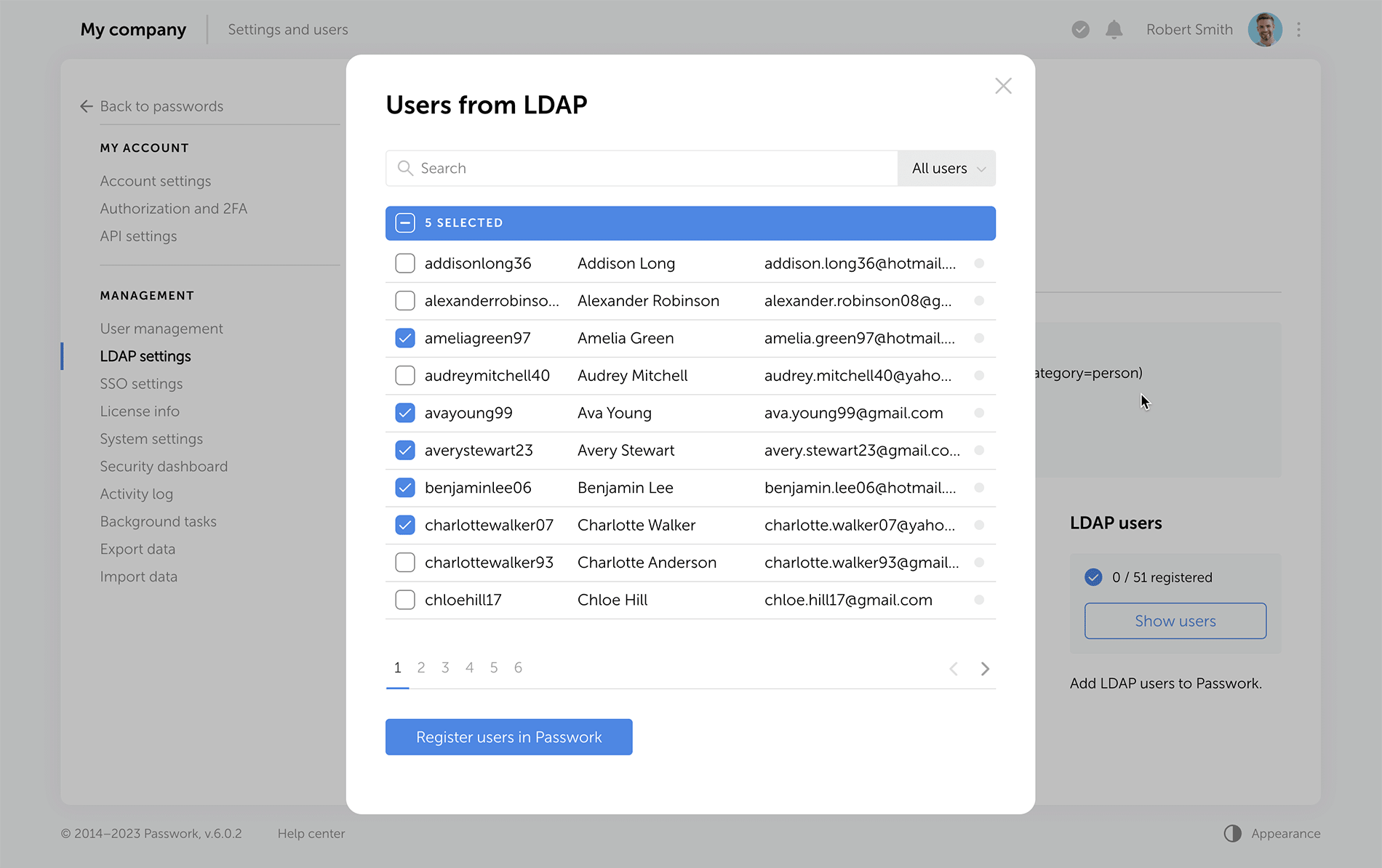
The LDAP interface is now cleaner and more intuitive, with a reimagined user management logic. Adding new LDAP users is simpler and safer, especially with the client-side encryption enabled.
Previously, admins had to add an employee and provide a master password. Now, users set their master passwords upon the first login, and admins confirm them afterwards.
The "Users" tab shows registered users, and there is a separate window for adding new ones. LDAP user data updates take place in the background, allowing admins to navigate elsewhere without waiting for data refresh.
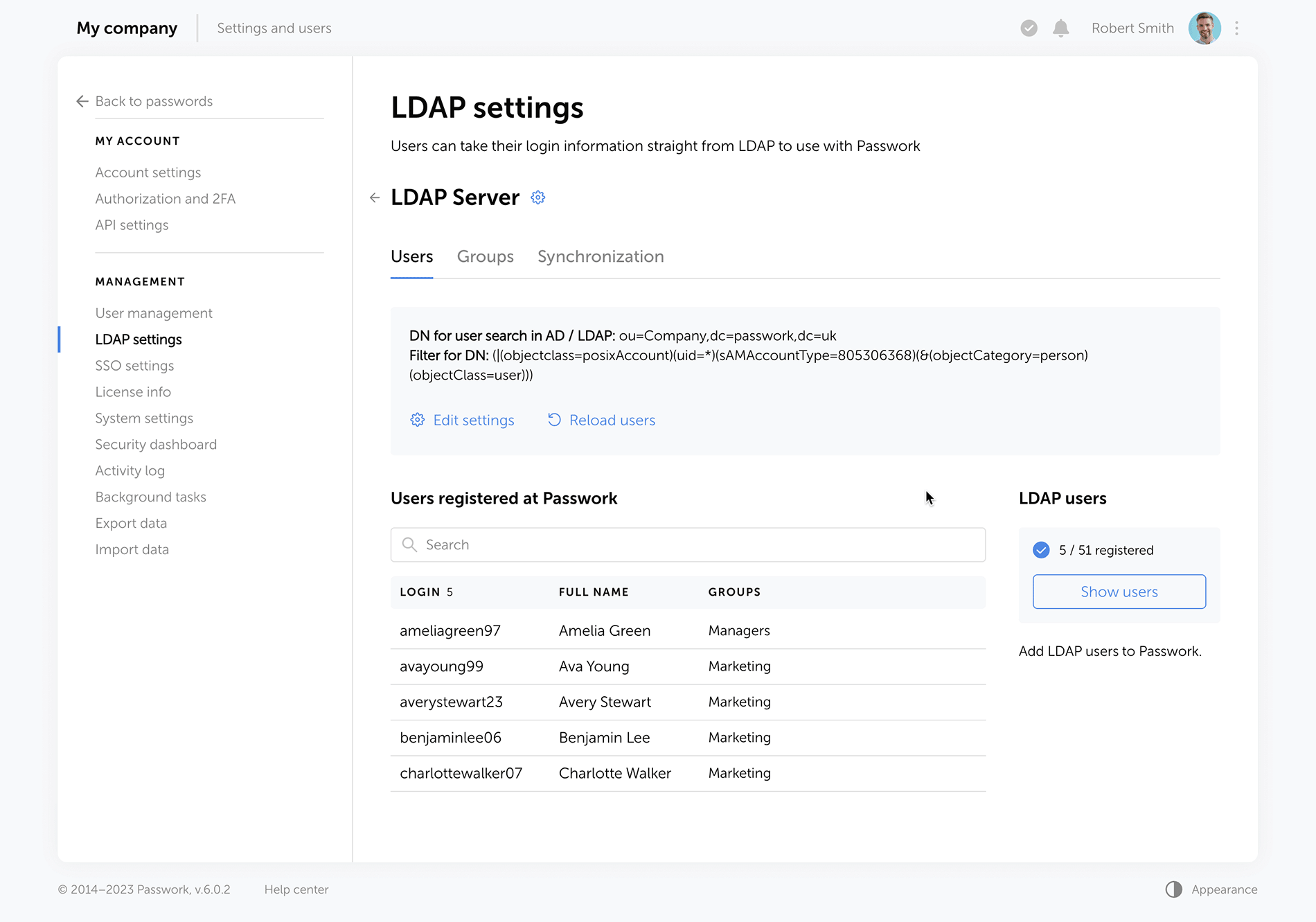
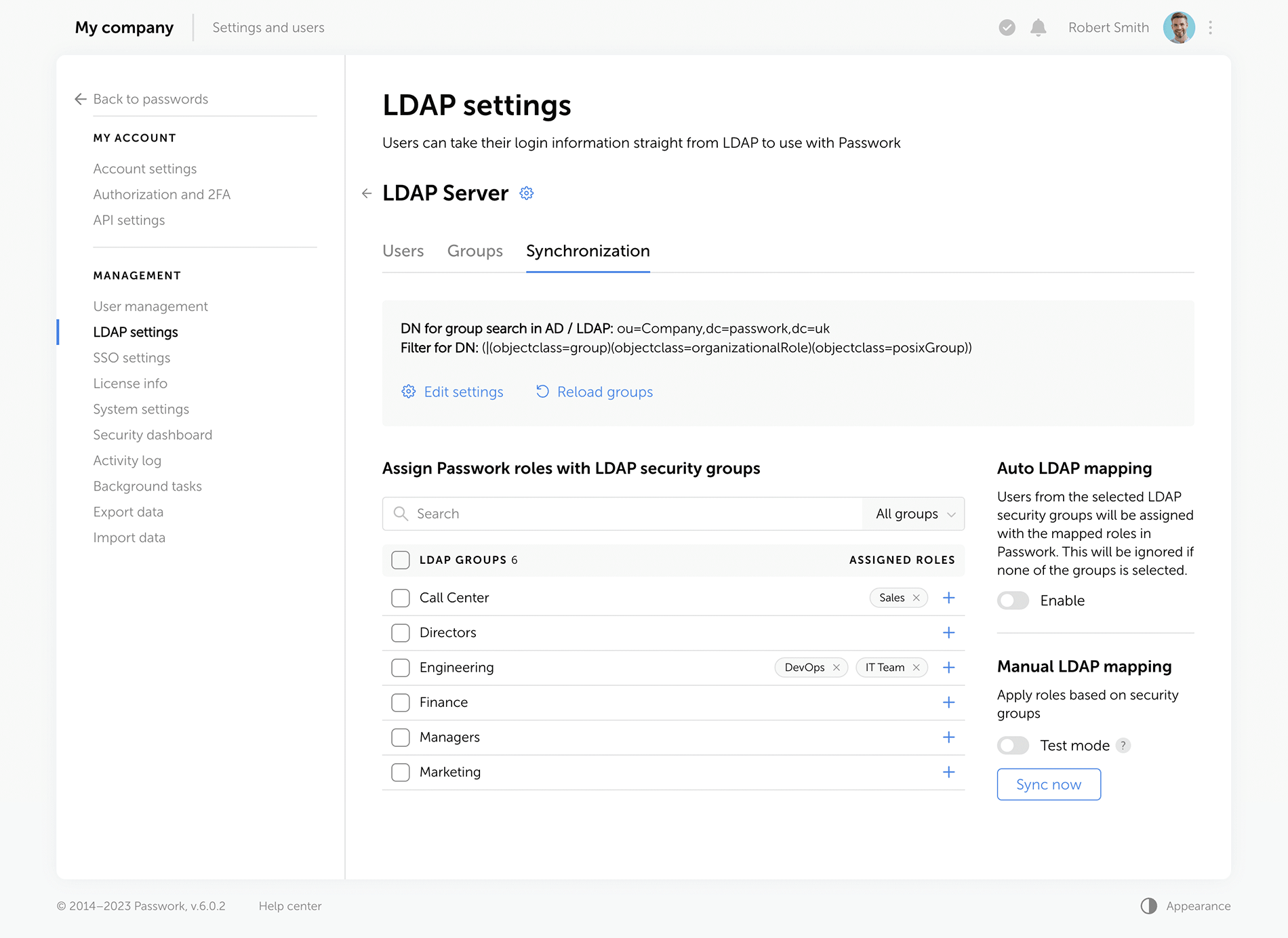
Passwork now provides more detailed security group information. The groups that are linked to roles are marked with special tags, and the groups which were not loaded from LDAP during the last update are marked as "Deleted", alerting admins to adjust the search settings or remove such groups. Also, you can now see the members of each security group.
Improved settings
We've redesigned all settings sections for a unified visual style and enhanced functionality, reimagined the logics of some settings.
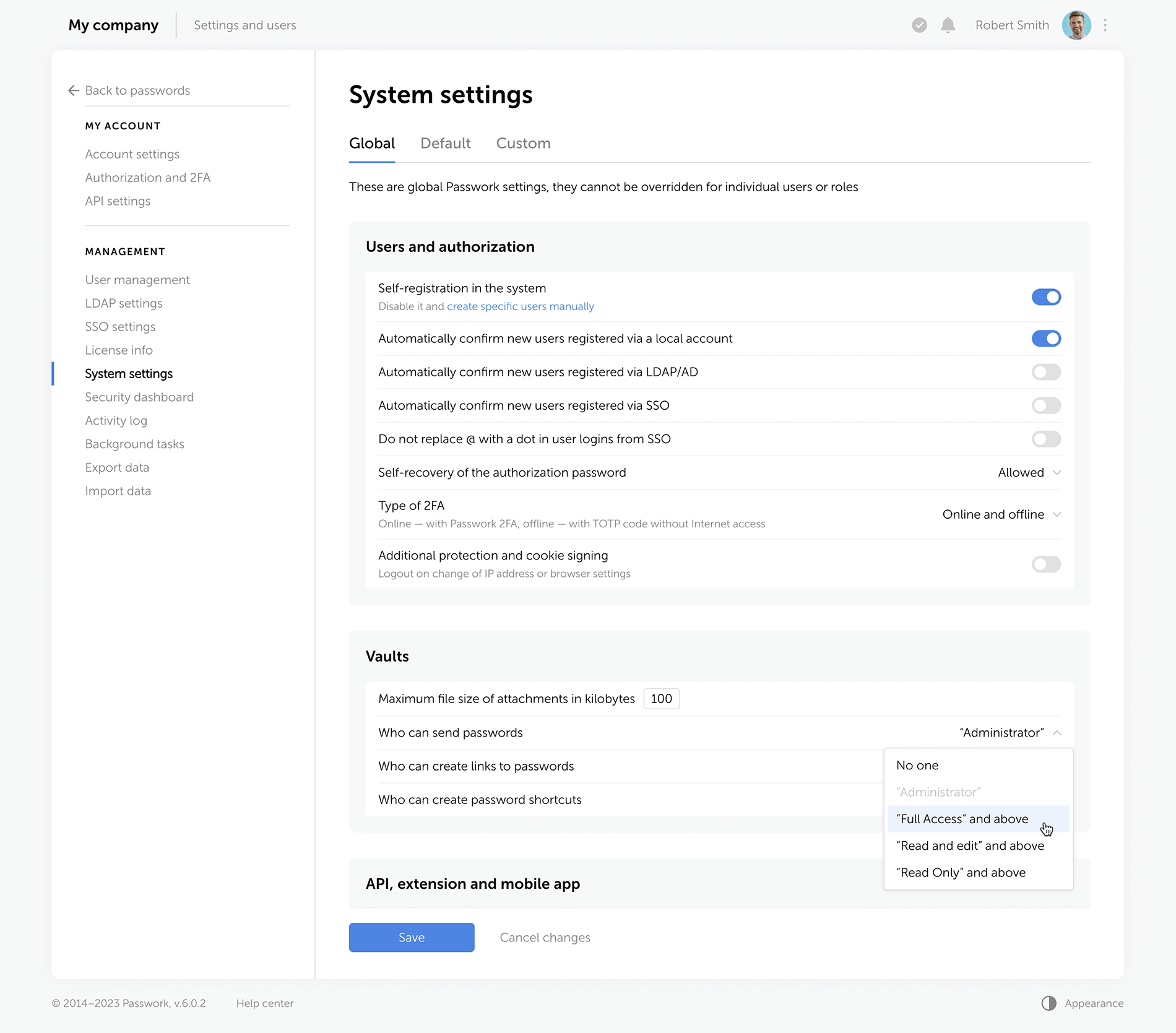
Rights for links, tags, and password sharing. Previously, these settings were applied individually to each user. Now, they are applied to everyone with a certain level of vault access. For example, anyone with the “Edit” access rights or higher can create hyperlinks to passwords. These parameters are located in the system settings under the “Global” tab.
Change confirmation. We've added “Save” and “Cancel changes” buttons in system settings. Now, any changes to settings must be confirmed — this helps to prevent accidental actions.
Custom auto-logout time. Users can now set these parameters individually, and admins specify the maximum inactivity time period before automatic logout.
Language selection. In the new version of Passwork, admins can allow employees to choose their interface language.
Interface enhancements
Improved drag and drop. Now, when dragging and dropping passwords and folders into desired directories, Passwork displays selectable actions — move, copy, or create a shortcut.
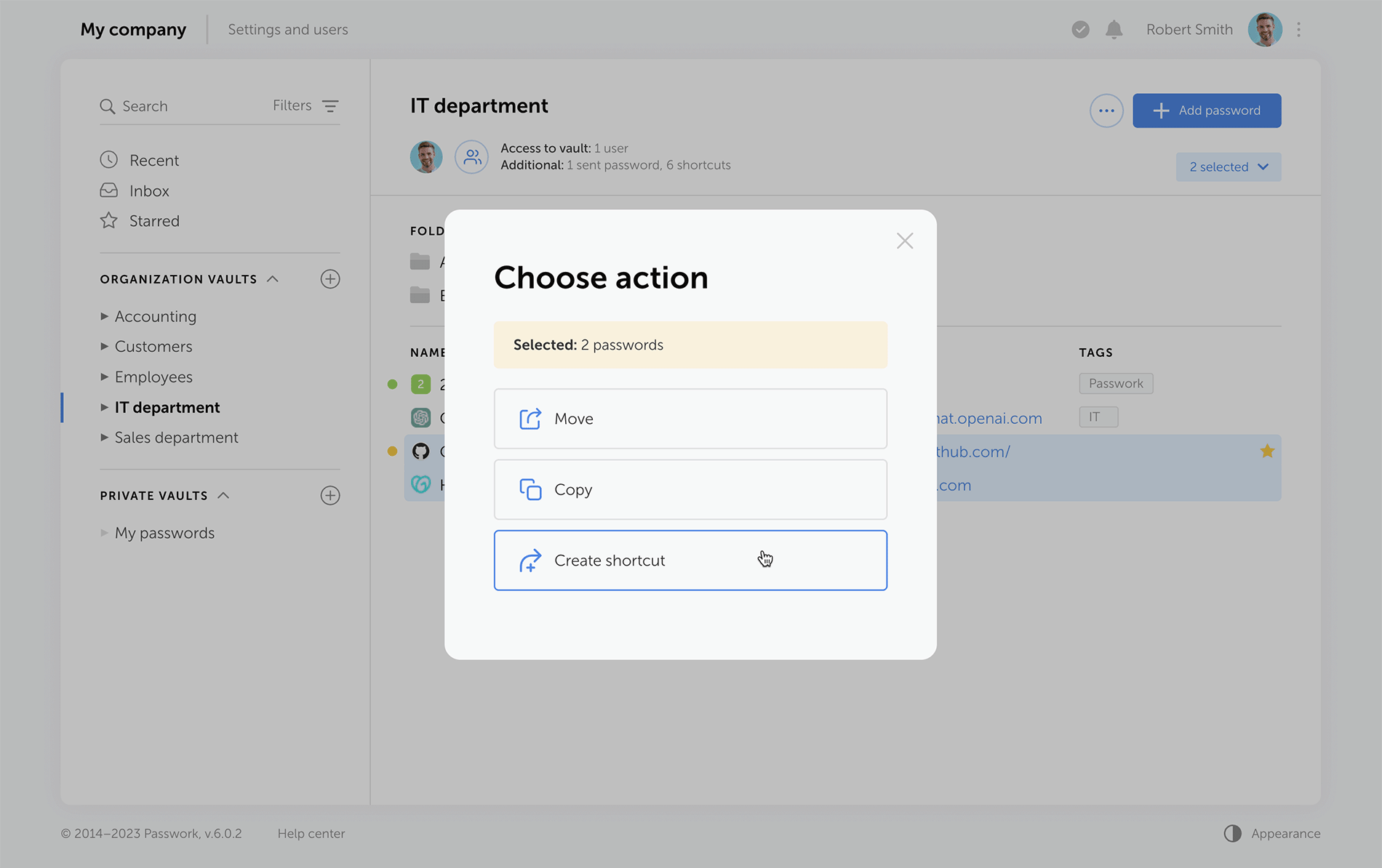
Other improvements
Separate windows for access to the safe and additional access. Vault access info is now split into two easy-to-read windows. One window shows users who has access to a specific vault, and the other displays alternative ways passwords from this vault can be accessed — shortcuts, hyperlinks, or shared passwords.
Redesigned password action buttons. On the password panel, we've added the "Edit" button and grouped together all actions for additional password access via shortcuts, links, or direct user sharing.
Additional fields for password import and export. Passwork 6.0 supports the use of custom fields, that means you can transfer not only login and password but also additional information stored within password cards.
New notifications. Administrators will receive notifications about new unconfirmed users, and employees will be notified of new passwords in the "Incoming" section.
Introducing Passwork 6.0

A Security Operations Center (SOC) is a critical hub for cybersecurity within organizations. It combines people, processes, and technologies to detect, analyze, and respond to security incidents. In this article, we will delve into the components that make up a SOC, starting with its basic systems, then moving on to heavier software tools, and finally exploring emerging technologies that hold promise for the future of SOC operations.
Basic systems
The foundation of any SOC lies in its basic systems, which provide fundamental capabilities for monitoring, analysis, and incident response. These systems include:
A Security Information and Event Management (SIEM) system: A SIEM tool collects and correlates data from various sources, such as logs, network traffic, and endpoint events. It helps identify security incidents and generates alerts for further investigation. SIEM systems provide a centralized view of security events, allowing SOC analysts to detect patterns and anomalies.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS monitor network traffic, searching for suspicious patterns or known attack signatures. IDS detects intrusions, while IPS can actively block or mitigate threats in real time. These systems play a crucial role in detecting and preventing unauthorized access and malicious activities within the network.
Vulnerability management systems: Vulnerability management systems scan and assess the organization's network, applications, and systems for vulnerabilities. They enable proactive identification and remediation of security weaknesses, reducing the risk of exploitation by attackers. These systems play a vital role in maintaining a secure infrastructure.
Log management systems: Logs are critical for forensic analysis and incident response. Log management systems collect, store, and analyze logs from various sources, providing valuable insights into security events. They help SOC teams investigate incidents, identify the root cause of security breaches, and ensure compliance with regulatory requirements.
Network Traffic Analysis (NTA) tools: NTA tools analyze network traffic at a granular level, identifying anomalies and potential threats. By monitoring and analyzing network traffic patterns, these tools help SOC teams detect and respond to suspicious activities. NTA tools enhance visibility into network behavior, allowing SOC analysts to identify sophisticated threats that traditional security systems may miss.
Heavier software
As threats become more sophisticated, SOC teams require advanced software tools to combat them effectively. Let’s take a look at some examples.
Threat intelligence platforms: Threat intelligence platforms aggregate data from various sources to provide up-to-date information about known threats, vulnerabilities, and indicators of compromise. They enhance incident detection and response capabilities by enabling SOC teams to proactively identify and mitigate potential risks. Threat intelligence platforms allow organizations to stay informed about emerging threats and adopt appropriate defense measures.
Endpoint Detection and Response (EDR): EDR solutions monitor endpoint devices for suspicious activities and potential threats. They provide real-time visibility, investigation, and response capabilities, helping SOC teams swiftly identify and contain incidents. EDR tools leverage behavioral analysis and threat intelligence to detect and respond to advanced threats, such as file-less malware and insider threats, at the endpoint level.
Security Orchestration, Automation, and Response (SOAR): SOAR platforms streamline and automate SOC processes, integrating various tools and technologies. They facilitate incident triage, investigation, and response, enabling faster and more efficient security operations. SOAR platforms automate routine tasks, allowing SOC analysts to focus on high-value activities like threat hunting and incident response.
User and Entity Behavior Analytics (UEBA): UEBA tools leverage machine learning algorithms to establish baseline behaviors for users and entities within an organization. They detect anomalous activities, such as insider threats or compromised accounts, by analyzing behavior patterns. UEBA tools provide insights into user activities, helping SOC teams identify potential security incidents and mitigate risks.
Deception technologies: Deception technologies create decoys and traps within a network, luring attackers and diverting their attention. By interacting with deception assets, SOC teams can gather valuable threat intelligence and gain insights into attackers' techniques. Deception technologies complement traditional security measures by providing early detection and response capabilities.
Looking forward
The evolving threat landscape calls for constant innovation in the field of cybersecurity. Several technologies show promise for enhancing SOC capabilities in the future. Let’s take a look at a few.
Artificial Intelligence (AI) and Machine Learning (ML): AI and ML techniques are already being utilized in various aspects of cybersecurity. They can aid in threat detection, anomaly detection, and behavior analysis, enabling more proactive and accurate identification of security incidents. AI and ML algorithms can analyze vast amounts of data and identify patterns that human analysts may miss, improving the efficiency and effectiveness of SOC operations.
Advanced analytics: Advanced analytics techniques, such as predictive analytics and behavioral analytics, can provide deeper insights into security events and help identify emerging threats. By analyzing historical and real-time data, SOC teams can uncover hidden connections and predict future attack trends. Advanced analytics empower SOC analysts to make informed decisions, prioritize threats, and allocate resources effectively.
Cloud-based security: As organizations increasingly adopt cloud infrastructure, SOC operations will need to adapt accordingly. Cloud-native security solutions, including Cloud Access Security Brokers (CASBs) and Cloud Security Posture Management (CSPM) tools, are emerging to address the unique challenges of cloud environments. These solutions provide visibility, control, and compliance assurance across cloud services, ensuring that organizations can protect their data and applications effectively.
Internet of Things (IoT) security: With the proliferation of IoT devices, SOC teams will face the challenge of securing these endpoints. Future SOC technologies should incorporate specialized IoT security solutions that monitor and protect connected devices. IoT security platforms can detect and mitigate IoT-specific threats, such as device tampering, unauthorized access, and data exfiltration. These technologies enable SOC teams to secure the expanding landscape of IoT devices within organizations.
Quantum computing: Quantum computing has the potential to revolutionize cryptography and threat intelligence analysis. With its immense computational power, quantum computers may help SOC teams tackle complex cryptographic algorithms and facilitate faster threat analysis. Quantum-resistant encryption algorithms and quantum-enabled threat detection techniques may become crucial components of future SOC operations.
Conclusion
A well-equipped SOC comprises basic systems, advanced software, and future technologies. The basic systems form the foundation, providing essential monitoring and analysis capabilities. Heavier software tools enhance incident response and detection, allowing SOC teams to stay ahead of evolving threats. Looking ahead, emerging technologies like AI, advanced analytics, cloud-based security, IoT security solutions, and quantum computing hold the potential to revolutionize SOC operations, enabling organizations to protect their assets and data more effectively in an ever-changing cybersecurity landscape.
Exploring the components of a Security Operations Center (SOC): Basic systems, advanced software, and future technologies

Symmetric algorithms, forming the backbone of modern cryptography, offer a secure method of encrypting and decrypting data utilizing a single shared key. They have been widely adopted for their unmatched speed and efficiency. Like any other technology, symmetric algorithms come with their own set of benefits and drawbacks. This article seeks to offer a comprehensive review of the pros and cons of symmetric algorithms, providing a deeper understanding of their integral role in data security and the potential challenges they entail.
Pros of symmetric algorithms
Unrivaled efficiency
Symmetric algorithms are best known for their superior efficiency in handling large volumes of data for encryption and decryption. The use of a single key significantly reduces the demand for computational resources, setting symmetric algorithms apart from their asymmetric counterparts. This makes them an excellent fit for applications that demand high-speed data processing, including secure communication channels and real-time data transfers.
Impressive speed
Symmetric algorithms, by virtue of their simplicity, can process data at a much faster rate than asymmetric algorithms. Without the need for complex mathematical operations, such as prime factorization or modular arithmetic, symmetric algorithms can encrypt and decrypt data rapidly, reducing latency. This speed advantage is particularly beneficial for applications requiring swift data encryption, including secure cloud storage and virtual private networks (VPNs).
Key distribution
Symmetric algorithms simplify the key distribution process. Given that both the sender and receiver utilize the same key, they only need to execute a secure key exchange once. This offers increased convenience in scenarios where multiple parties need to communicate securely, such as within large organizations, military operations, or corporate communications.
Computational simplicity
Symmetric algorithms are relatively straightforward to implement due to their computational simplicity. This allows for efficient coding, making them ideally suited for resource-constrained devices that possess limited computational capabilities, such as embedded systems or Internet of Things (IoT) devices. This simplicity also contributes to easier maintenance and debugging, reducing the potential for implementation errors that could compromise security.
Cons of symmetric algorithms
Complex key management
The management and distribution of shared keys are significant challenges inherent to symmetric algorithms. The security of these algorithms is closely tied to the confidentiality of the key. Any unauthorized access or compromise of the key can lead to a total breach of data security. Consequently, robust key management protocols are essential, including secure storage, key rotation, and secure key exchange mechanisms, to mitigate this risk.
Lack of authentication
Symmetric algorithms do not inherently provide authentication mechanisms. The absence of additional measures, such as digital signatures or message authentication codes, can make it challenging to verify the integrity and authenticity of the encrypted data. This opens the door for potential data tampering or unauthorized modifications, posing a considerable security risk.
Scalability
Symmetric algorithms face challenges when it comes to scalability. Since each pair of communicating entities requires a unique shared key, the number of required keys increases exponentially with the number of participants. This can be impractical for large-scale networks or systems that involve numerous users, as managing a vast number of keys becomes complex and resource-intensive.
Lack of perfect forward secrecy
Symmetric algorithms lack perfect forward secrecy, meaning that if the shared key is compromised, all previous and future communications encrypted with that key become vulnerable. This limitation makes symmetric algorithms less suitable for scenarios where long-term confidentiality of data is crucial, such as secure messaging applications.
An in-depth analysis of symmetric algorithms
Symmetric algorithms, including the widely adopted AES, DES, and Blowfish, are favored for their speed and efficiency. However, their robustness is largely dependent on the size of the key and the security of the key during transmission and storage. While larger keys can enhance security, they also increase the computational load. Thus, selecting the appropriate key size is a critical decision that requires a careful balance between security and performance requirements.
One of the standout strengths of symmetric encryption is its application in bulk data encryption. Because of their speed, symmetric algorithms are ideally suited for scenarios where large amounts of data need to be encrypted quickly. However, they may not always be the best solution. In many cases, asymmetric encryption algorithms, despite their higher computational demands, are preferred because of their additional security benefits.
It's also crucial to note that cryptographic needs often go beyond just encryption and decryption. Other security aspects, such as data integrity, authentication, and non-repudiation, are not inherently provided by symmetric algorithms. Therefore, a comprehensive security scheme often uses symmetric algorithms in conjunction with other cryptographic mechanisms, such as hash functions and digital signatures, to provide a full suite of security services.
Final thoughts
Symmetric algorithms occupy a pivotal place in the realm of cryptography. Their efficiency and speed make them an invaluable asset for many applications, especially those involving large-scale data encryption. However, the limitations inherent in symmetric algorithms, including key management complexities, lack of authentication, and absence of perfect forward secrecy, necessitate meticulous implementation and the incorporation of additional security measures. Therefore, the decision to utilize symmetric algorithms should be made based on a thorough understanding of these pros and cons, as well as the specific requirements of the system in question.
Pros and cons of symmetric algorithms: Ensuring security and efficiency

The marvels of modern computing are, in part, thanks to advances in artificial intelligence. Specific breakthroughs in large language models, such as OpenAI's GPT-4 and Google's BERT, have transformed our understanding of data processing and manipulation. These sophisticated models masterfully convert input data—whether it be text, numbers, or more—into a form that machines can understand. This intricate process, known as data encoding, serves as the foundation for these models to comprehend and generate human-like text. Let's delve deeper into the intricacies of data encoding and how it powers the magic of AI language models.
The secret code of machines
The beginning of the journey involves comprehending how GPT-4 or BERT processes sentences typed into them. Contrary to human processing capabilities, these models can't directly interpret words. Instead, they employ something known as word embeddings. This complex yet efficient technique transforms each word into a unique mathematical form—akin to a secret code decipherable only by machines. Each encoding is meticulously performed to ensure that semantically similar words receive comparable codes. The aim is to create a rich, multidimensional landscape where each word's meaning is determined by its location relative to other words.
The role of positional encoding in context understanding
While individual words carry their importance, the structure of language extends beyond isolated entities. The sequence of words, the context, can drastically alter the meaning of a sentence. To illustrate, consider the phrases "Dog bites man" and "Man bites dog." The same words are used, but their arrangement creates entirely different narratives. That's where positional encoding enters the picture. By assigning each word an additional code indicating its position in the sentence, positional encoding provides models with a vital understanding of language structure and syntax.
The attention process: making words context-aware
After word and positional encoding, these mathematical representations, or word embeddings, undergo an 'attention' mechanism. Here, each word embarks on a figurative group discussion with all the other words in the sentence. During this interaction, each word decides the importance it should attribute to the others. For instance, in the sentence "Jane, who just moved here, loves the city," the word "Jane" would assign significant attention to "loves."
These 'attention' weights are then used to compute a new representation for each word that is acutely aware of its context within the sentence. This batch of context-aware embeddings journeys through multiple layers within the model, each designed to refine the model's understanding of the sentence. This systematic processing prepares the model to generate responses or predictions that accurately reflect the intended meaning of the sentence.
GPT-4: writing text one word at a time
GPT-4 has adopted a unique approach when it comes to generating text. It operates on a "one word at a time" principle. Beginning with an input, it predicts the next word based on the preceding context. This predicted word is then included in the context for predicting the following word, and the process repeats. This strategy allows GPT-4 to produce text that is not just grammatically coherent, but also semantically relevant, mirroring the way humans write one sentence after another.
BERT: a 360-degree view of sentence context
BERT, on the other hand, possesses a distinct capability that sets it apart from other models. It can process and understand text in both directions simultaneously. BERT does not limit itself to considering words before or after a given word. Instead, it absorbs the entire context at once, effectively offering a 360-degree view of the sentence. This bidirectional understanding enables BERT to comprehend the meaning of words based on their complete context, significantly enhancing the model's ability to interpret and generate nuanced responses.
The versatility of data encoding
While language forms a significant chunk of these models' use cases, they aren't confined to it. An exciting feature of models like GPT-4 and BERT is their ability to work with any kind of sequential data. This characteristic opens up a universe of possibilities for diverse fields, from composing harmonic music to decoding complex genetic sequences, predicting stock market trends, or even simulating game strategies. By analyzing patterns in the sequential data, these models can unearth hidden insights and produce creative outcomes, making them an invaluable asset in numerous areas beyond language processing.
Expanding horizons: applications and future prospects
The wonders of data encoding do not stop with text generation. In fact, the potential applications of these AI models are continually expanding. They can be used to aid human decision-making in complex scenarios, such as medical diagnosis or legal analysis, by digesting massive amounts of textual data and making informed suggestions. In the field of research, they can help summarize lengthy academic papers or generate new hypotheses based on existing literature. The entertainment industry isn't left out either, as these models can create engaging content, ranging from writing captivating stories to generating dialogues for video games.
Moreover, GPT-4 and BERT's remarkable abilities to understand and manipulate language are catalyzing research into other AI models. Researchers are exploring ways to combine the strengths of various models and reduce their limitations, which promises an even more exciting future for AI.
Conclusion
In conclusion, data encoding in AI models like GPT-4 and BERT can be likened to watching a symphony of processes working in perfect harmony. From word embeddings and positional encoding to attention mechanisms, these models leverage a series of intricate techniques to decode the hidden patterns in data, transforming it into meaningful information. The incredible capability of these models to understand context, generate human-like text, and adapt to diverse data types is revolutionizing the field of artificial intelligence, paving the way for a future brimming with AI innovations.
How large language models encode data

The intricate dance between spies and encryption has been played out over thousands of years, and its rhythm continues to quicken. As we delve deeper into this dance, we see a confluence of technology, secrecy, and intelligence that has shaped the course of history and continues to impact our world today.
A brief history of encryption
Encryption, in its essence, is about transforming information into a code that is unreadable to anyone except the intended recipient. The Ancient Greeks and Romans were among the first to understand this concept. They used simple substitution ciphers, where each letter in a message would be replaced by another letter. The Caesar Cipher, used by Julius Caesar for secure military communications, is a classic example. This cipher was a simple shift of the alphabet, and while it was easy to break, it underscored the vital principle of encryption: the ability to shield information from prying eyes.
Fast forward to the World Wars, and we see the stakes rising. Encryption technology became more advanced and intertwined with the art of espionage. The Enigma machine, utilized by the Germans during World War II, is a well-known example of this progression. The Enigma was an electromechanical device that used a set of rotating disks to scramble plaintext messages into complex ciphertext. The machine's complexity made it a powerful tool for clandestine communication, and cracking its code was a task that required immense intellectual prowess.
The British cryptanalysts at Bletchley Park, led by Alan Turing, took on this monumental challenge. Their efforts to break the Enigma code were not just a victory for cryptography but also a critical factor that contributed to the Allied victory. It was espionage and counter-espionage at its finest, with encryption at the heart of the battle.
The Cold War saw the battleground shift, but the importance of encryption remained the same.
Cryptic case studies
In the last few years, we've seen several noteworthy instances where spies have used encryption and other covert tactics to achieve their goals. Let's explore five recent cases:
- Walter Glenn Primrose and Gwynn Darle Morrison were apprehended for a most unusual crime: the theft of deceased infants' identities. The case took a peculiar twist when a photograph was discovered featuring the duo dressed in what was purportedly KGB uniforms. The objective behind this odd photograph remains shrouded in ambiguity. However, this case casts a spotlight on the extraordinary lengths to which spies will resort to obfuscate their true selves, potentially utilizing encryption as a tool to further conceal their covert activities.
- In another instance, the veneer of Russian intelligence's machinations to sway U.S. elections was peeled back with the indictment of Alexandr Viktorovich Ionov. This indictment served as a window into the operational mechanics of the Russian FSB, divulging their deployment of an array of stratagems, including the use of encryption and disinformation campaigns, to sow seeds of chaos within the United States and undermine the foundations of global democracy.
- A narrative involving U.S. nuclear engineer Jonathan Toebbe and his spouse, Diana, unfolded as the pair tried to profit from selling purloined U.S. Navy nuclear documents and designs in exchange for cryptocurrency. Their surreptitious operation was derailed by an FBI sting operation, underscoring the pivotal role of counterintelligence mechanisms and encryption in the intricate world of modern espionage.
- In 2022, European nations initiated a large-scale crackdown on Russian intelligence operations that resulted in the expulsion of 556 Russian intelligence officers and diplomats. This widespread ejection served to hinder Russia's influence operations on European soil and stifle their capacity to manage and support their spy networks. This incident underscores the concerted global efforts being taken to neutralize encrypted espionage activities.
- China remains a prominent figure on the stage of global espionage, relentlessly targeting Western technological knowledge and silencing dissent within the Chinese diaspora. One particularly significant case involved Yanjun Xu, an intelligence officer who set his sights on the U.S. aerospace sector. Xu's subsequent 20-year prison sentence serves as a sobering testament to China's long-haul espionage strategy, the role of encryption in facilitating covert operations, and the international cooperative efforts required to counteract such threats.
Reflecting upon both historical and contemporary instances, one can see the intricate duality that encryption presents in espionage. As a tool, it simultaneously serves as a means for covert agents to veil their communications, maintaining the secrecy that their roles require. Simultaneously, it is the shield that protects sensitive data from falling into the wrong hands, acting as a safeguard against the very spies who would employ it for their own purposes.
As technology surges forward, the tactics and techniques of spies and cryptographers mirror this progression. This perpetual cycle of action and counteraction — the relentless pursuit to devise impenetrable codes on one hand, and the counter-effort to decode them on the other — encapsulates the ongoing relationship between espionage and encryption. This dance, marked by strategic maneuvering, continuous adaptation, and intellectual rigor, escalates in intensity with each passing moment, as each side ceaselessly strives to outsmart the other.
Summing up
In conclusion, the interplay between espionage and encryption is a nuanced ballet of complexity and evolution. Encryption serves dual roles in this dance: as a tool that facilitates the clandestine operations of spies, and as a defense mechanism against such covert activities. As we continue to ride the wave of technological advancement, the ties between espionage and encryption will undoubtedly become more intricate, more convoluted, and more pivotal. Whether the scenario involves state-sponsored cyber-espionage aiming to disrupt nations or individuals attempting to monetize state secrets, encryption remains a critical element in these engagements, forming the core of this ongoing battle.
Spies and encryption: Dance of secrecy and technology

The globe has become profoundly reliant on technology, information, and the web. Although this has optimized and made business processes more efficient, it has also given rise to severe issues like cyber threats. The frequency of cyber attacks is escalating at a distressing pace.
Studies indicate that globally, every organization is subjected to over nine hundred cyber assaults on a weekly basis. This has culminated in a plethora of both concrete and abstract losses for organizations.
With the surge in cyber attacks, there is a corresponding rise in the need for experts in cyber security. Organizations are in dire need of specialists who can shield them from these onslaughts. Consequently, career opportunities in cybersecurity are burgeoning at an unprecedented rate in the United States.
As time has passed, cybersecurity has burgeoned into a sector replete with highly specialized roles that offer lucrative remuneration. Each role comes with its own set of requirements, competencies, and perspectives. Let’s delve into an overview of the eight most remunerative careers in the realm of cybersecurity.
Information security analyst
Information security analysts play a pivotal role in instituting cyber security protocols within a company or organization. A prime example of their responsibilities is the installation of firewalls. These firewalls act as a critical bulwark, providing an augmented shield to safeguard the organization's network.
In addition to installing firewalls, information security analysts wear multiple hats. They are involved in perpetually monitoring the organization’s networks for any security breaches and investigating violations when they occur. They are also tasked with creating and executing plans to combat potential security incidents and bolster the organization's security posture.
Moreover, they frequently need to stay abreast with the latest trends and developments in information security to ensure that the organization's security measures are up-to-date. This includes not only understanding the technical aspects but also the regulatory compliance and best practices to safeguard sensitive information.
When it comes to remuneration, the average baseline salary for an information security analyst in the United States is approximately $93,861 annually. However, this figure can vary based on factors such as location, level of experience, education, and the size and industry of the employer. Experienced analysts or those working in sectors with higher security demands may command higher salaries.
Cloud consultant
In the United States, a cloud consultant typically earns an average annual salary of around $127,105. Their role is primarily centered on working with cloud storage systems. Their responsibilities encompass the development, deployment, and maintenance of cloud applications, workflows, and services. Moreover, they rigorously analyze the organization’s data.
Through meticulous scrutiny of the data and understanding of the business requirements, they deduce the most appropriate cloud solution tailored to the organization’s needs. In addition to identifying the optimal cloud solutions, they also serve as advisers in the domain of cloud security. They meticulously evaluate the array of cloud services leveraged by the organization and proceed to suggest solutions that can bolster the security framework.
Furthermore, cloud consultants often engage in facilitating the migration of an organization's data and applications to the cloud. They are instrumental in ensuring a seamless transition while minimizing downtime and mitigating risks.
Given their expertise, they also provide insights and recommendations on cost management strategies, scalability, and disaster recovery plans within the cloud environment. Their role is essential for organizations to capitalize on the benefits of cloud computing while ensuring data integrity and security.
Penetration tester
Penetration testers serve as invaluable assets to organizations by pinpointing and rectifying security vulnerabilities through the execution of simulated cyberattacks. These professionals, often termed “ethical hackers,” mimic the tactics of malicious hackers in a controlled environment to evaluate the security infrastructure. In the United States, they typically earn an average annual salary of approximately $127,170.
Post the simulated attacks, penetration testers meticulously analyze the data to identify potential weak points in the system. Based on their assessments, they recommend and implement robust security measures designed to thwart actual cyberattacks. Their insights are crucial in fortifying the organization’s defense mechanisms.
Organizations that handle sensitive, personal, or classified information regard penetration testers as indispensable. Industries such as healthcare, finance, and government, which are especially sensitive to data breaches due to the nature of the information they manage, are more likely to employ penetration testers. These professionals might be hired for a specific project or be an integral part of the in-house cybersecurity team.
Network security architect
In the United States, a network security architect typically garners an average annual income of around $130,028. These professionals shoulder the critical responsibility of safeguarding an organization's network infrastructure.
A network security architect’s role encompasses designing, deploying, and rigorously testing networks to ascertain that they are impervious to cyberattacks and that security protocols are adhered to. This involves crafting network structures that are resilient and implementing cutting-edge security technologies to mitigate risks.
Additionally, network security architects play a vital role in the evolution of the organization's Local Area Network (LAN), Wide Area Network (WAN), and other data communication networks. They make sure these networks are not only secure but also efficient and scalable to accommodate the organization’s evolving needs.
Application security engineer
In the United States, application security engineers typically earn an average annual salary of around $126,391. These professionals play an integral role in guaranteeing that an organization’s software products function securely and dependably. Additionally, they extend their expertise to safeguard the organization's network and data repositories.
Collaboration is at the heart of the role of an application security engineer. They work hand-in-hand with software developers and product managers in a concerted effort to plan, enable, and bolster security implementations aimed at fortifying applications and software products. This involves integrating security measures throughout the software development lifecycle.
Their responsibilities include performing code reviews to identify vulnerabilities, implementing encryption and other security features, and ensuring compliance with industry security standards. They also design and conduct security tests to evaluate the resilience of applications against various attack scenarios.
Director of information security
The Director of Information Security holds a high-ranking position within an organization. In the United States, individuals in this role can expect an average base salary of approximately $206,475 annually. Additionally, they often receive yearly bonuses, which further enhance their earnings. The primary responsibility of a Director of Information Security is to devise and cultivate strategies aimed at bolstering the organization’s cybersecurity posture.
In their capacity, they assume a leadership role in managing and supervising a multitude of elements that make up the organization’s cybersecurity blueprint. This encompasses the creation and enforcement of security policies, conducting risk assessments, and ensuring compliance with regulatory standards.
Beyond developing strategies, they often have a bird's-eye view of the organization's security landscape and work closely with other departments to integrate cybersecurity measures into the broader organizational objectives. This sometimes involves communicating with the board of directors or other stakeholders to ensure they are aware of the security risks and measures in place.
Final words
It is evident that the cybersecurity field boasts an array of lucrative career opportunities, with even entry-level positions commanding attractive compensation. As one gains experience and demonstrates proficiency, there is a commensurate escalation in remuneration. If you’re seeking a rewarding and thriving career, the cybersecurity domain is ripe with possibilities, making the present moment an ideal time to venture into this sector.
To gain a foothold in the cybersecurity industry, it is imperative to possess relevant certifications or a degree in cybersecurity. Numerous educational institutions, including colleges and universities, offer a range of programs in this field. It is advisable to explore and enroll in a program that aligns well with your career aspirations and preferences.
The 6 highest-paid professions in cybersecurity

Biometric data refers to physical or behavioral characteristics that can be used to recognize a person. Indeed, in today's world, biometric data has become a widely used method of identifying individuals. Some examples of biometric data include fingerprints, facial recognition, and iris scans. Biometric data is now being used in a variety of applications, including in passports. Passports with biometric data are now the norm in many countries, and they offer several advantages over traditional passports. However, they also come with their own set of risks, including the possibility of being hacked.
The primary purpose of biometric data on a passport is to improve security and reduce the likelihood of identity fraud. The biometric data on a passport is unique to each individual and is difficult to replicate or forge. This makes it much harder for someone to use a fake passport or assume someone else's identity. In addition, biometric data can be used to speed up the passport control process, reducing wait times at airports and border crossings.
However, biometric data on passports is not foolproof. Hackers can potentially access this data and use it for their own purposes. For example, they may be able to use the data to create fake passports or to steal someone's identity. This is a major concern for many governments and individuals, as the consequences of identity theft can be severe.
Ways in which the biometric data on passports can be hacked
There are several ways in which biometric data on passports can be hacked. One method is through the use of skimming devices. Skimming devices can be used to steal the data on a passport's RFID chip, which contains biometric data. These devices can be hidden in public places, such as airports or train stations, and can be used to steal data from unsuspecting individuals. Once the data has been stolen, it can be used to create fake passports or to steal someone's identity.
Another way in which biometric data can be hacked is through cyberattacks. Cybercriminals can use various methods to gain access to a passport database and steal the biometric data contained within it. This data can then be sold on the dark web to other criminals or used to create fake passports. Cyberattacks can also be used to alter or delete data in the passport database, which can cause chaos and confusion for governments and individuals alike.
One example of biometric data being hacked is the 2014 breach of the US Office of Personnel Management. In this breach, hackers were able to steal sensitive data, including the biometric data of millions of government employees. This data included fingerprints, which can be used to identify individuals. The breach was a significant blow to US national security, and it highlighted the vulnerability of biometric data.
Another example of biometric data being hacked is the 2019 breach of Suprema, a biometric security company. In this breach, hackers were able to access the biometric data of millions of people, including fingerprint and facial recognition data. This data was being used by various organizations for security purposes, and the breach was a major concern for those who had entrusted their biometric data to Suprema.
The risks of biometric data being hacked are significant, as the consequences can be severe. For example, if a criminal gains access to someone's biometric data, they can potentially use it to create fake passports, steal their identity, or commit other crimes. This can result in financial loss, legal troubles, and damage to one's reputation.
How to protect biometric data on passports
To protect biometric data on passports, individuals and governments need to take steps to minimize the risk of it being hacked. One key step is to use encryption to protect the data while it is being transmitted and stored. Indeed, Encryption is a process of encoding data so that it can only be accessed by authorized parties with the appropriate decryption key. By encrypting biometric data on passports, the risk of it being intercepted or stolen by unauthorized parties is reduced.
Another important step is to improve cybersecurity measures to prevent cyberattacks. This includes implementing firewalls, using secure passwords, and regularly updating software and security protocols. It is also important to educate individuals about the risks of biometric data being hacked and how to protect themselves.
In addition, individuals can take steps to protect their own biometric data. This includes being vigilant about suspicious activity, such as phishing emails or phone calls that ask for personal information. It is also important to keep passports and other sensitive documents in a safe place and to report any lost or stolen passports immediately.
Despite the risks associated with biometric data on passports, it is important to note that it remains one of the most secure methods of identification available. While no security system is foolproof, the use of biometric data can significantly reduce the risk of identity fraud and improve security at airports and border crossings. By taking steps to protect biometric data, individuals and governments can minimize the risks of it being hacked and ensure that it remains a secure method of identification for years to come.
Conclusion
Biometric data on passports offers several advantages over traditional passports, including improved security and faster passport control. However, it also comes with its own set of risks, including the possibility of being hacked. Hackers can use various methods to access biometric data, including skimming devices and cyberattacks. Governments and individuals need to be aware of these risks and take steps to protect their biometric data. This may include using encryption, improving cybersecurity measures, and being vigilant about suspicious activity. The consequences of biometric data being hacked can be severe, and it is up to all of us to take steps to prevent it from happening.
